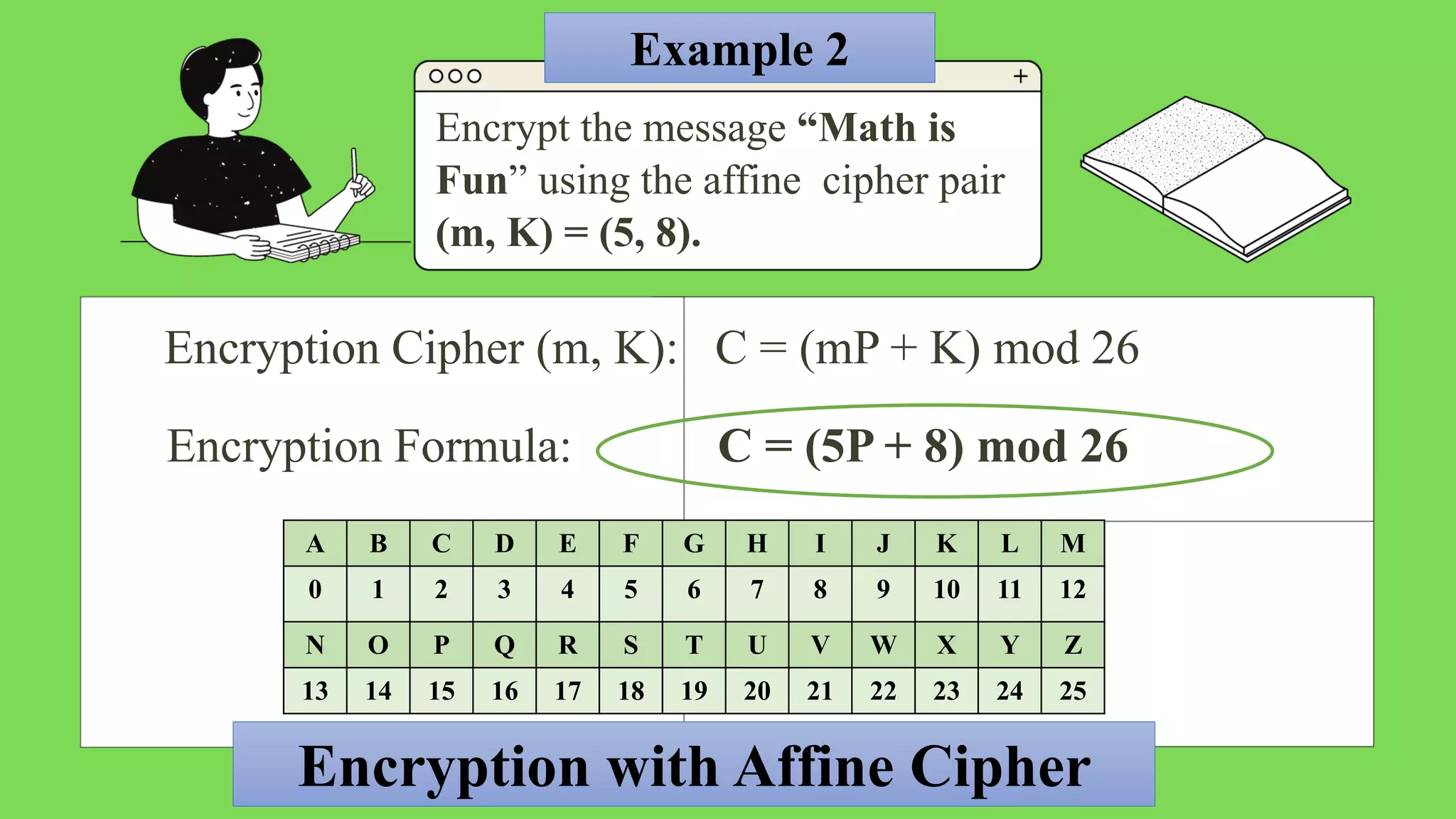
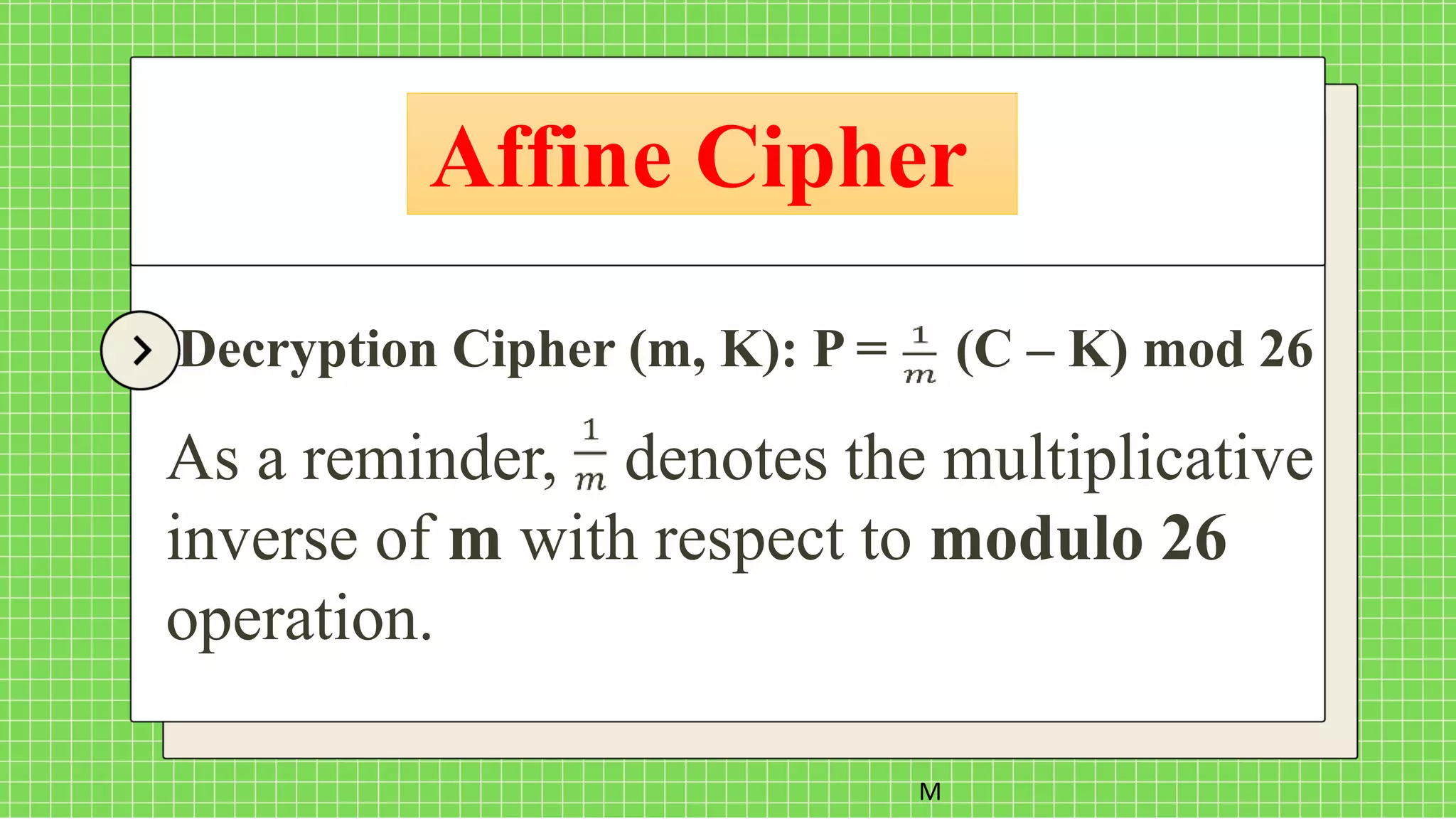
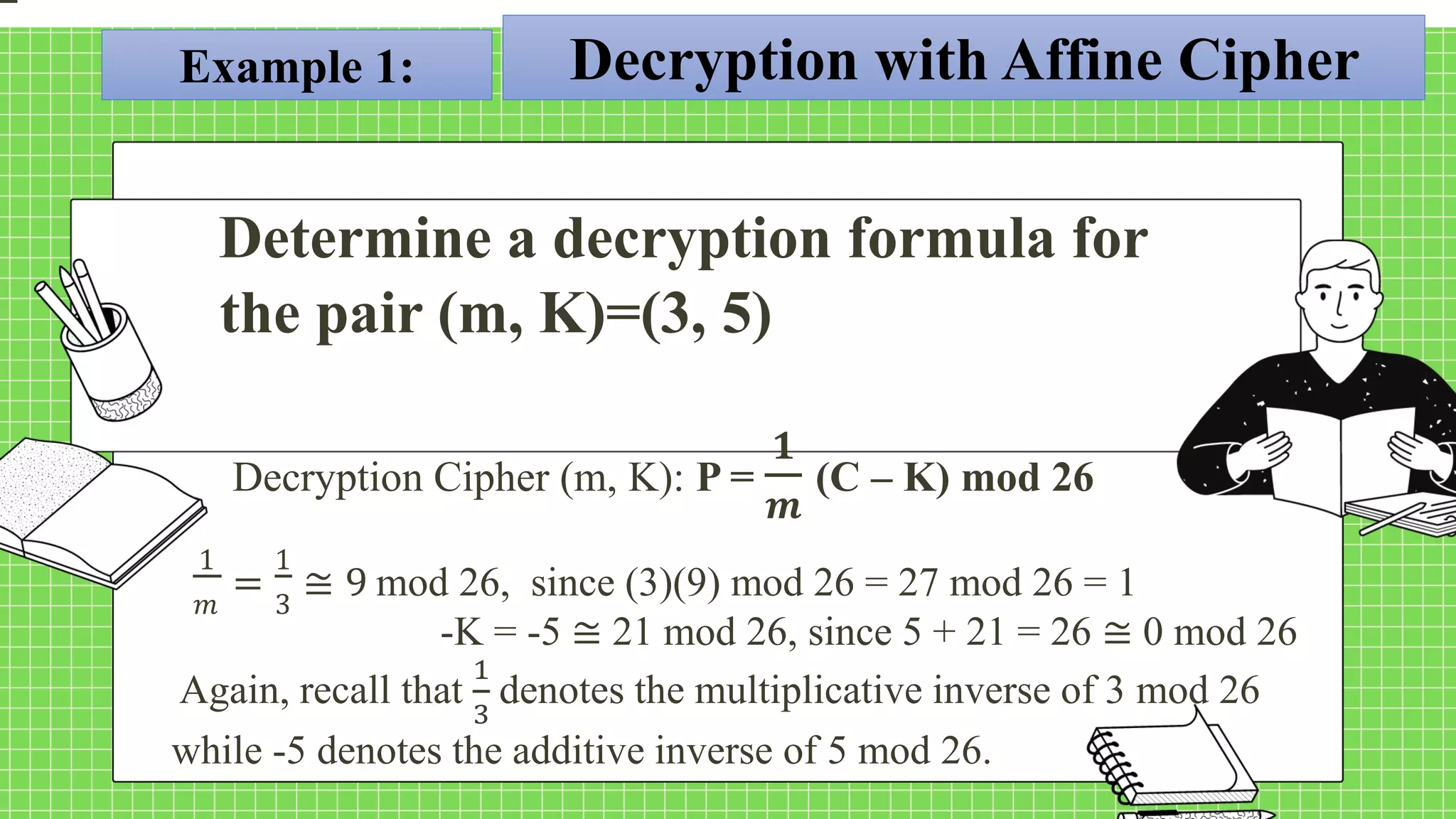
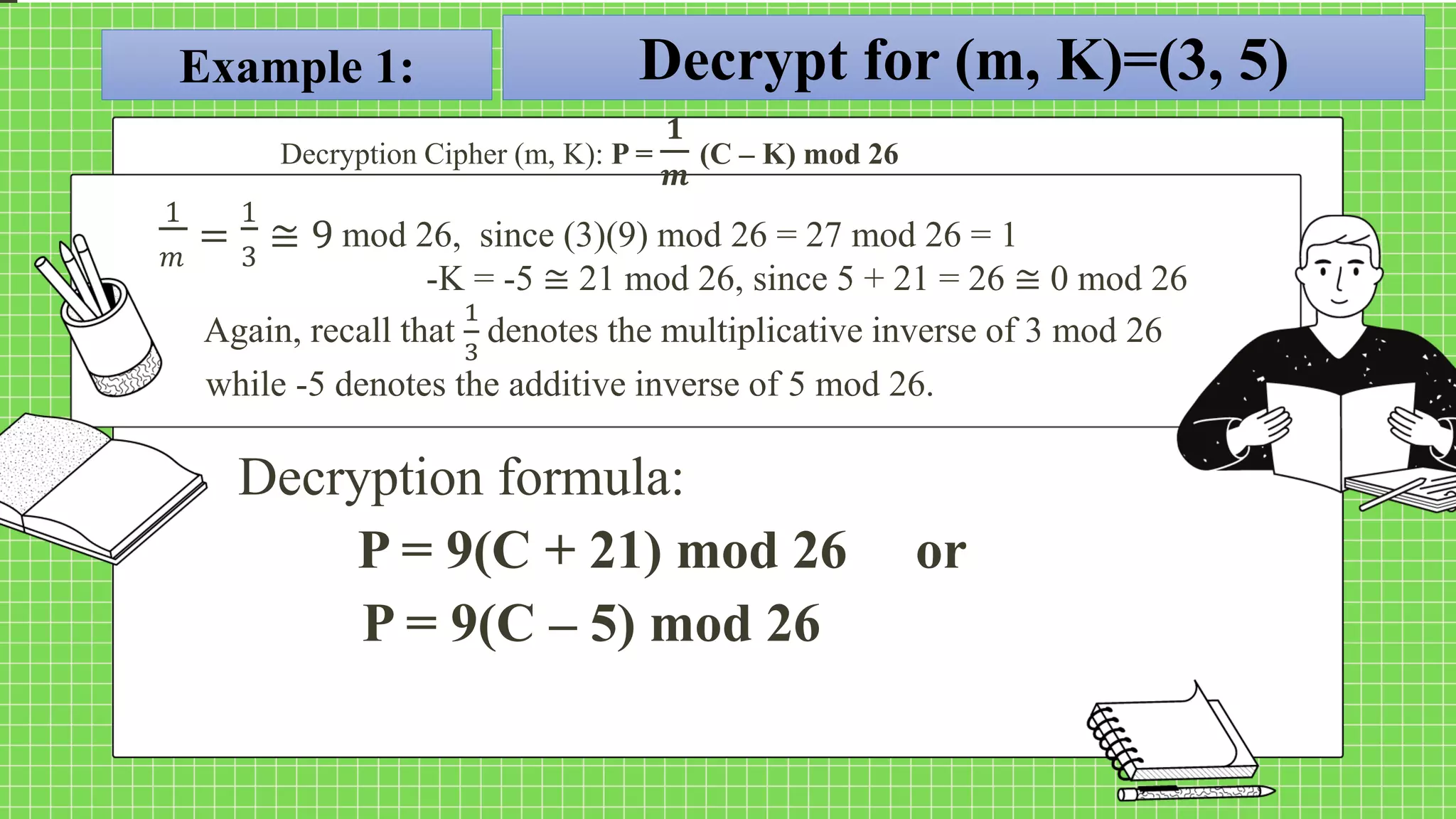
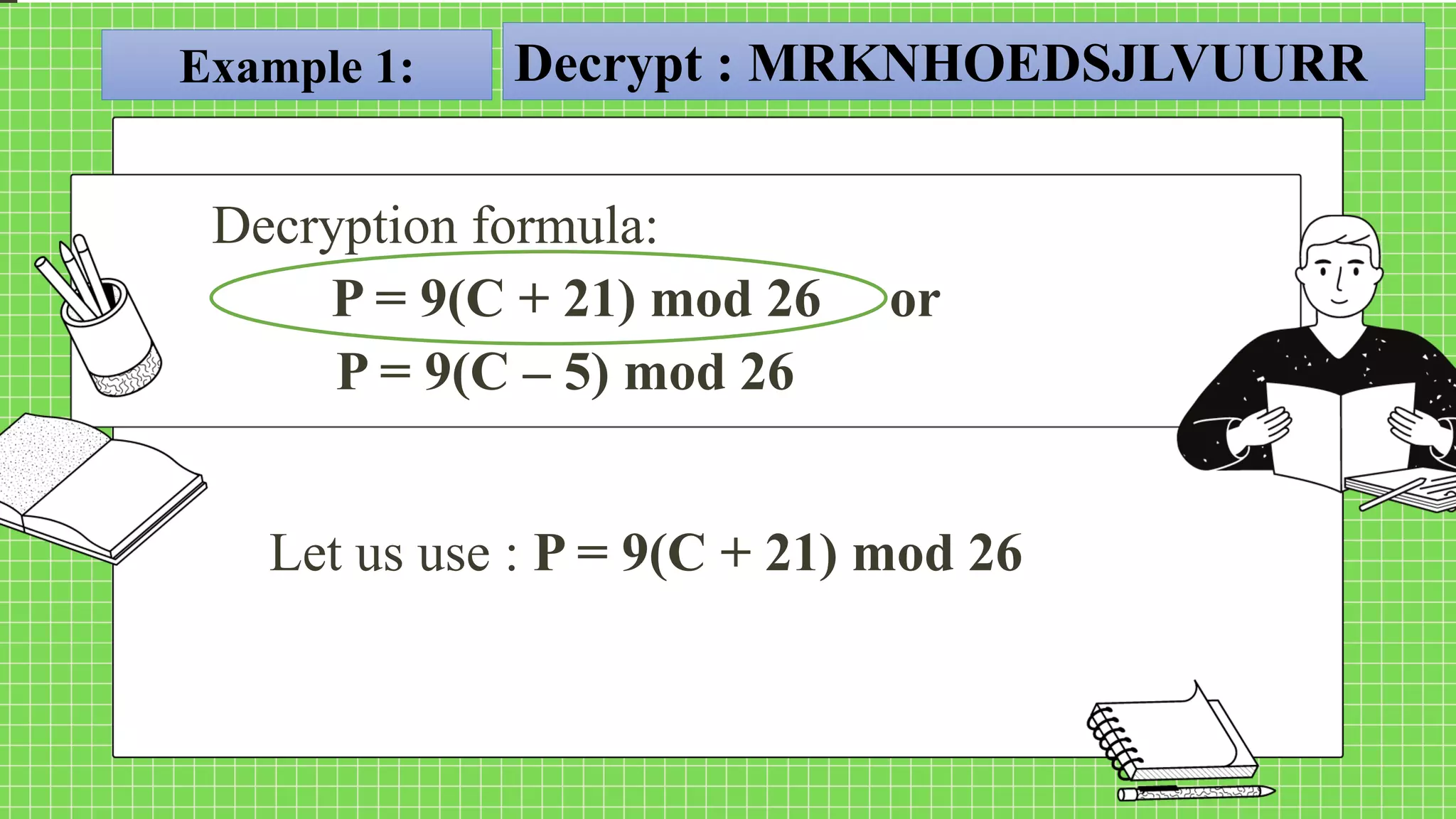
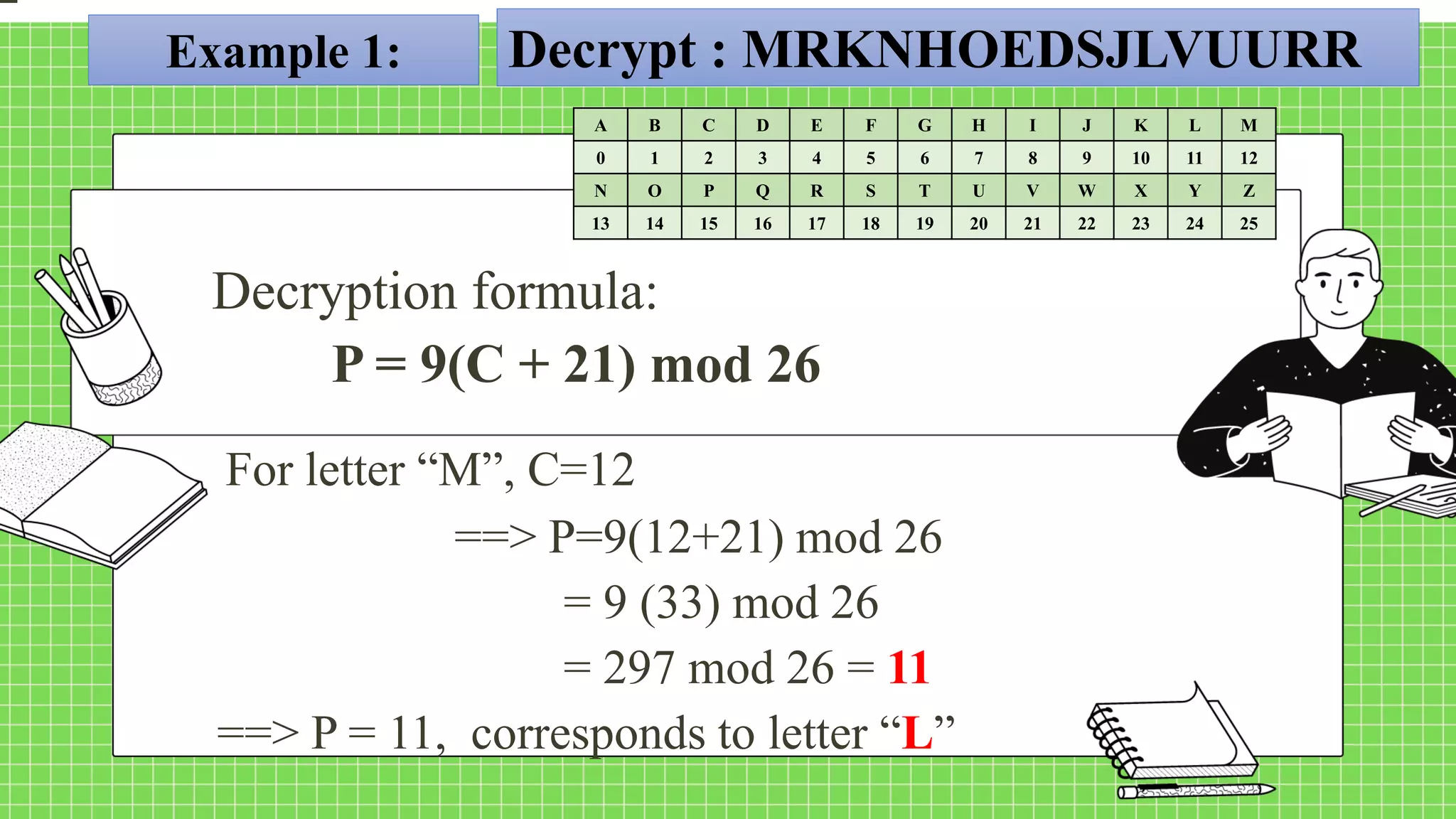
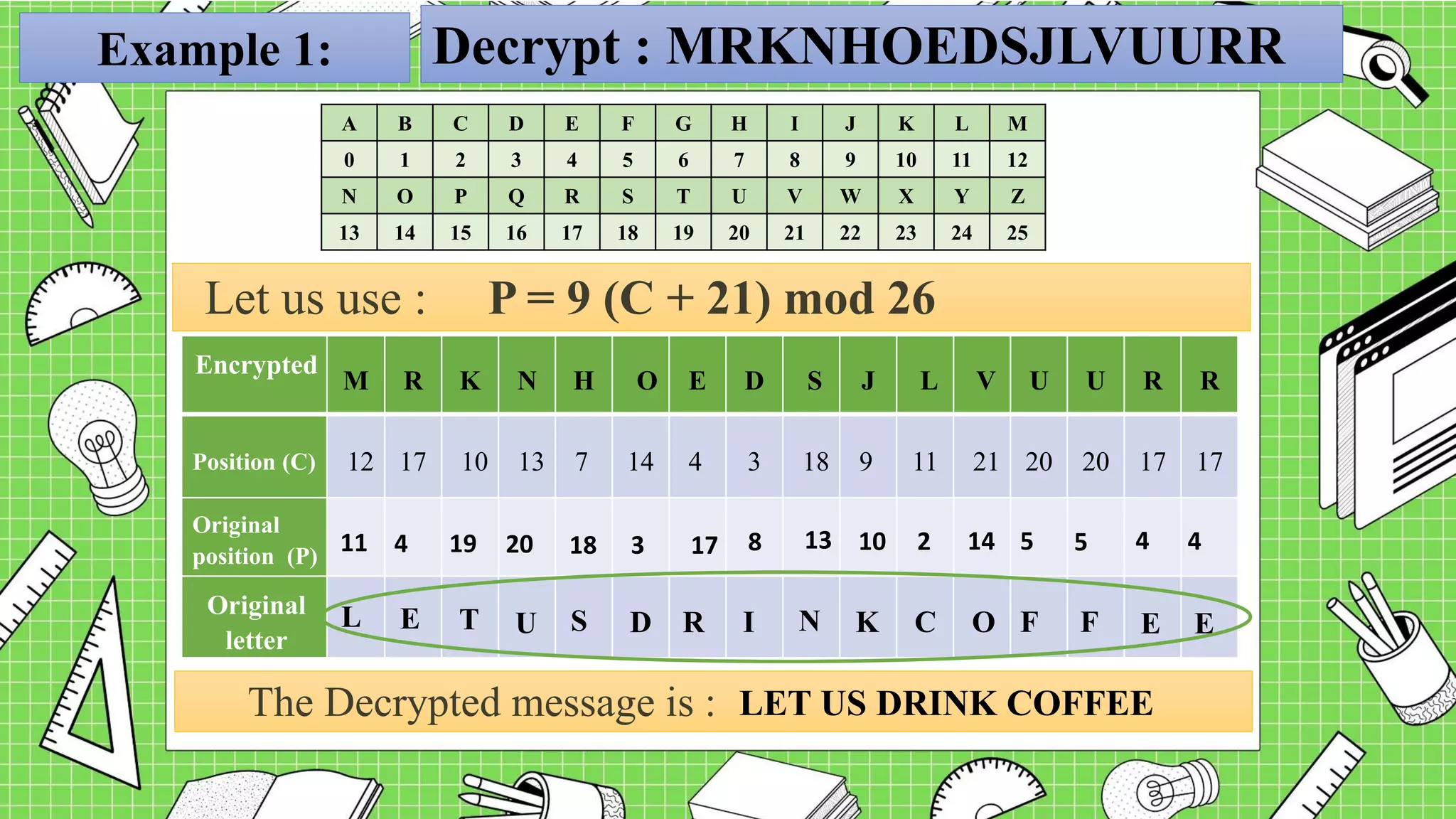
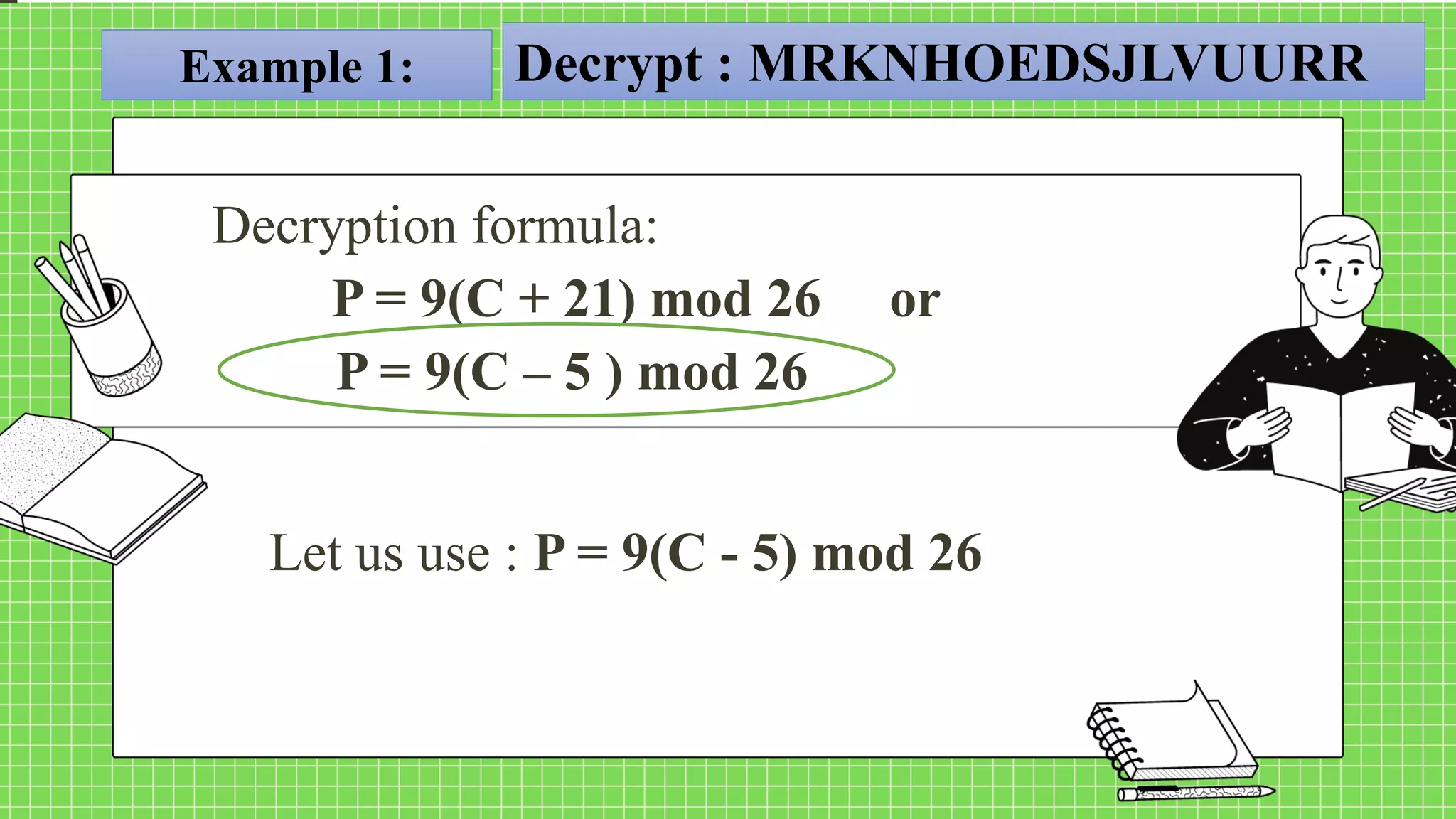
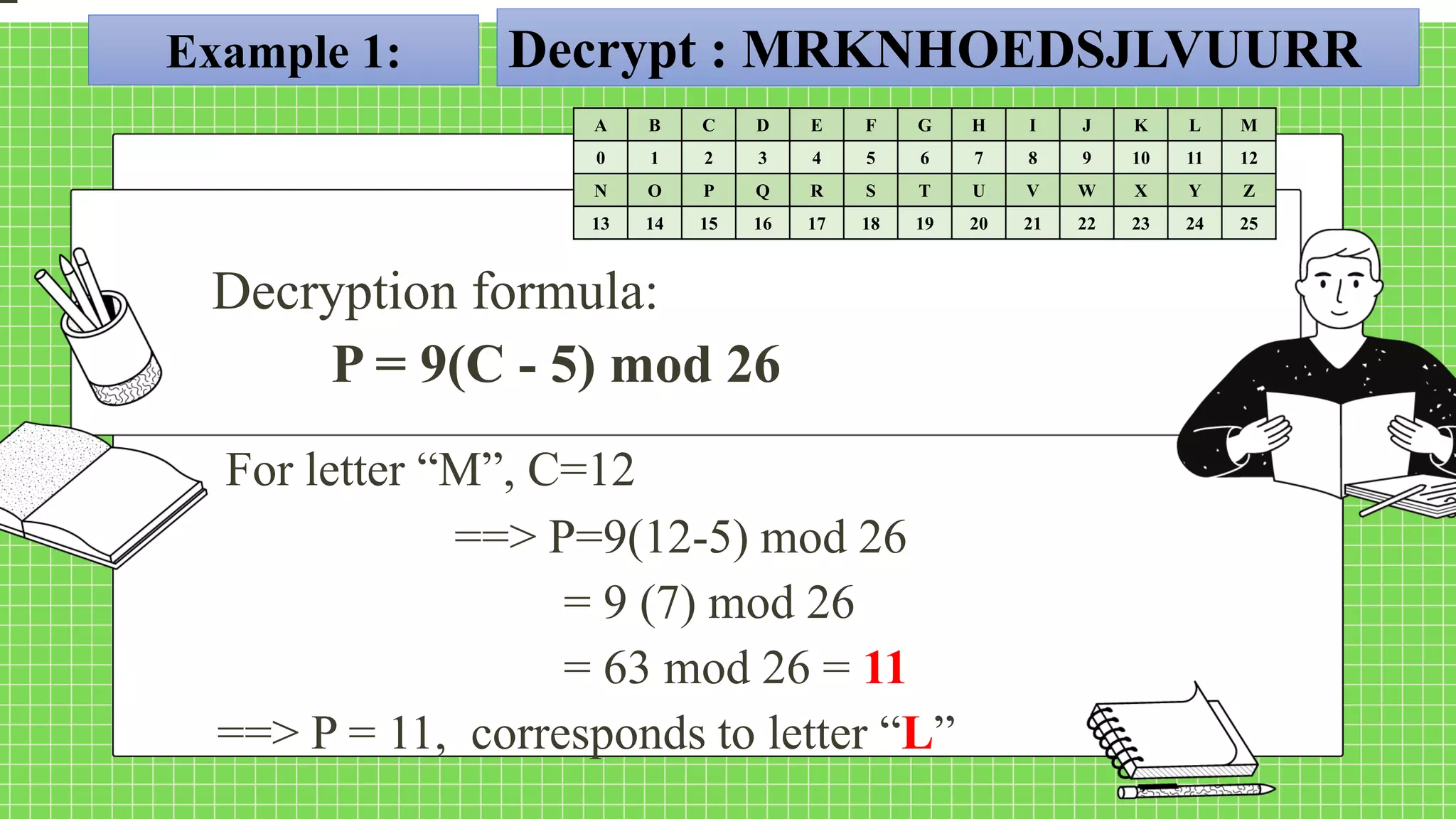
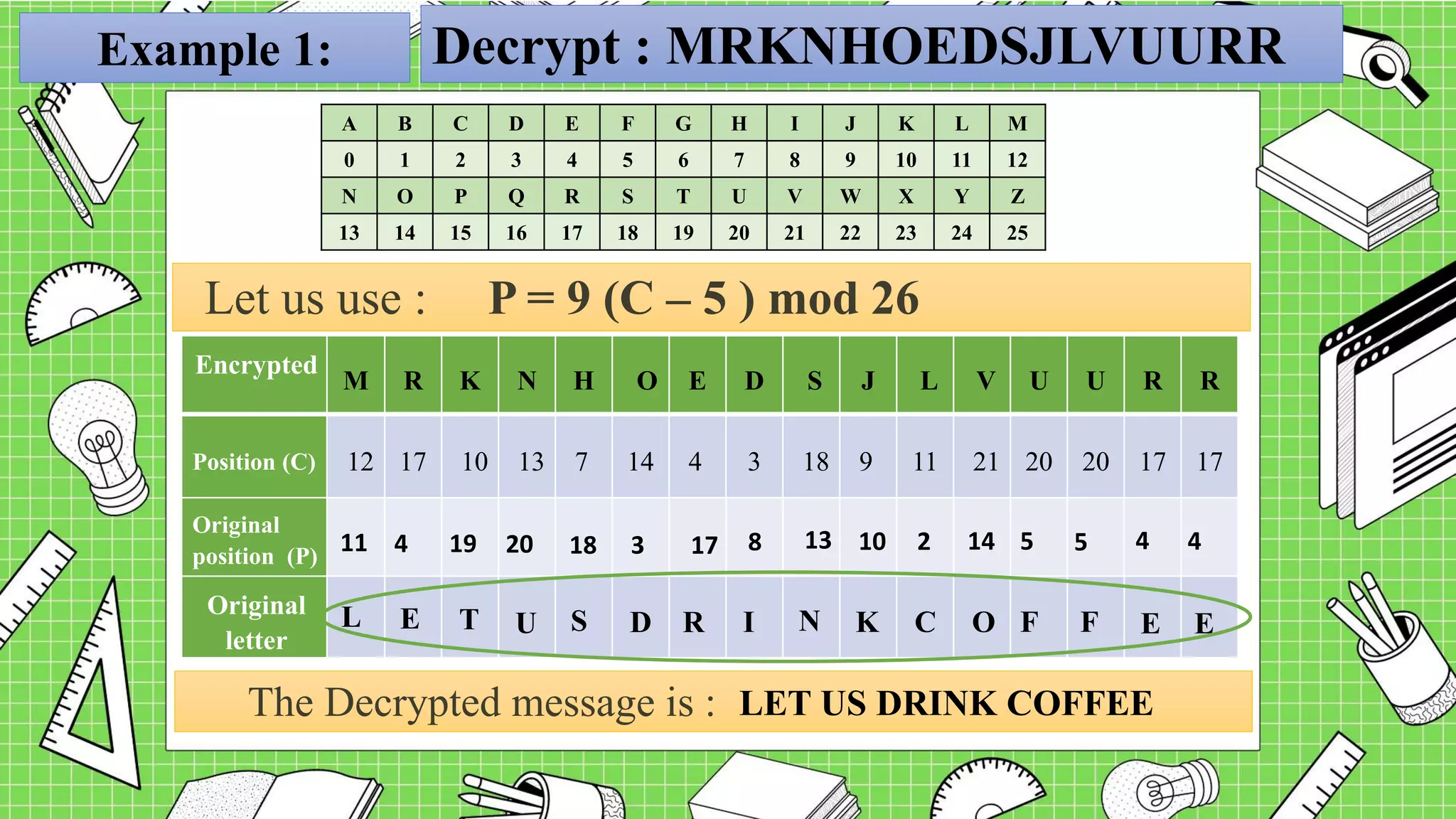
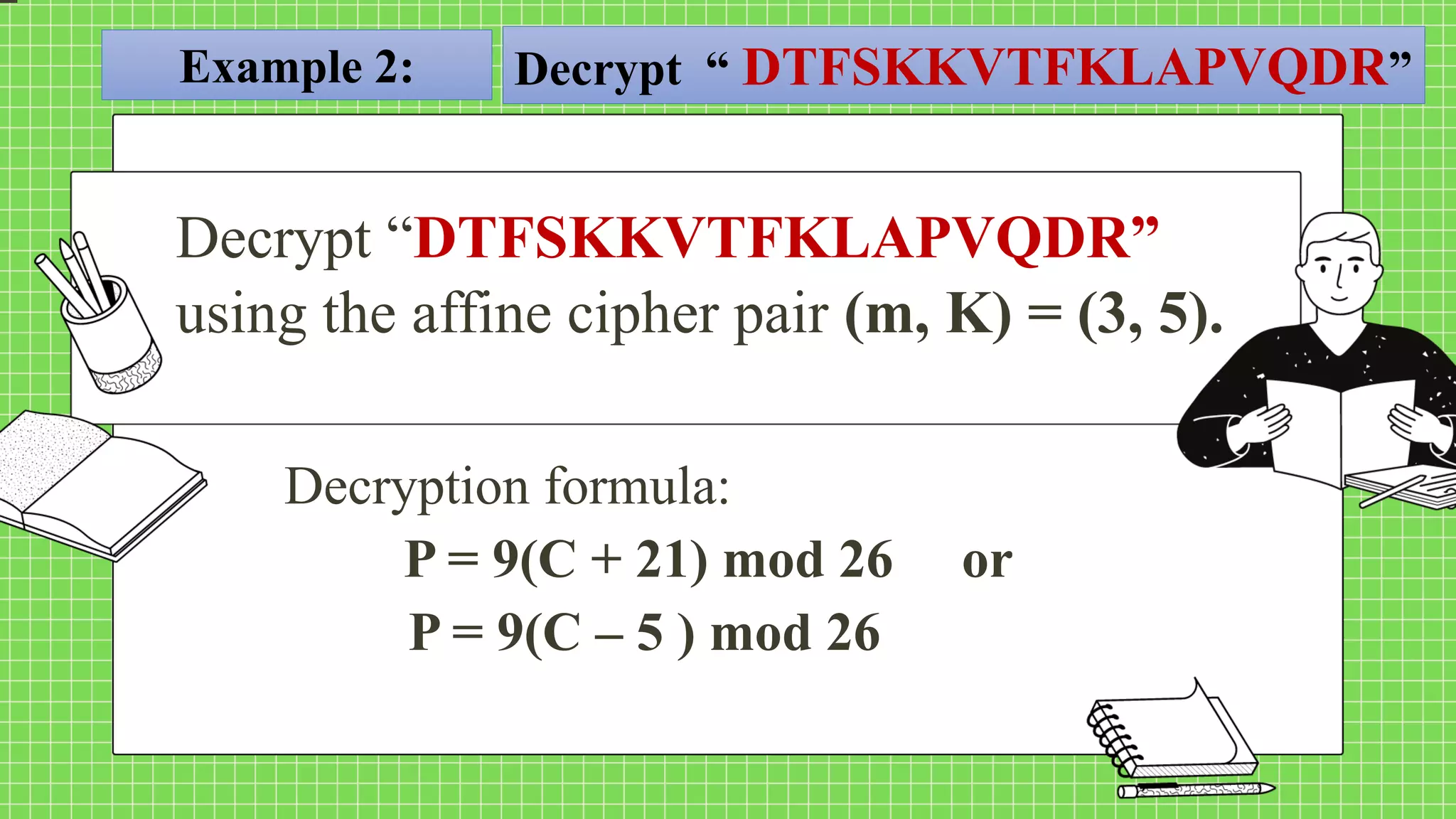
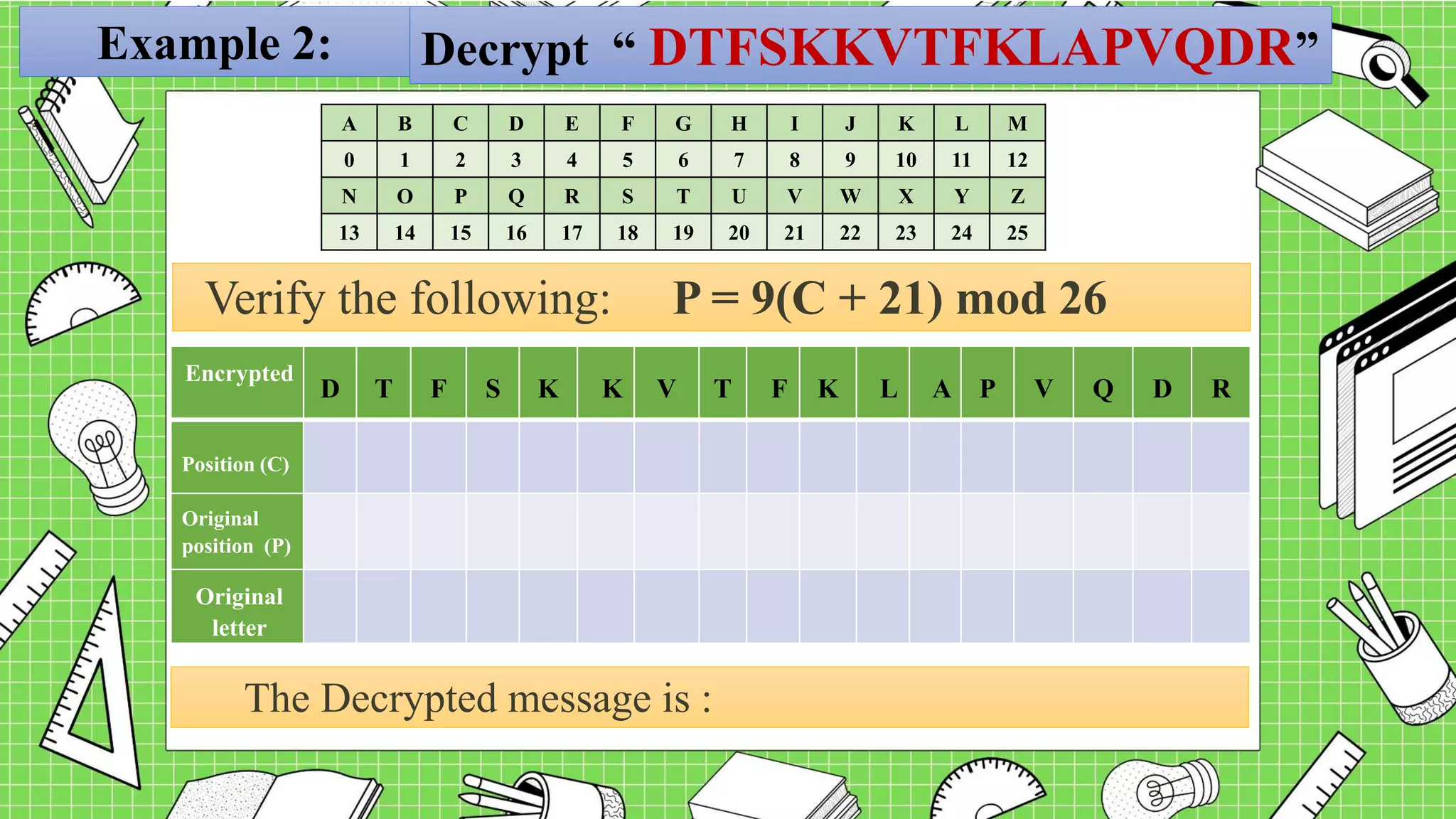
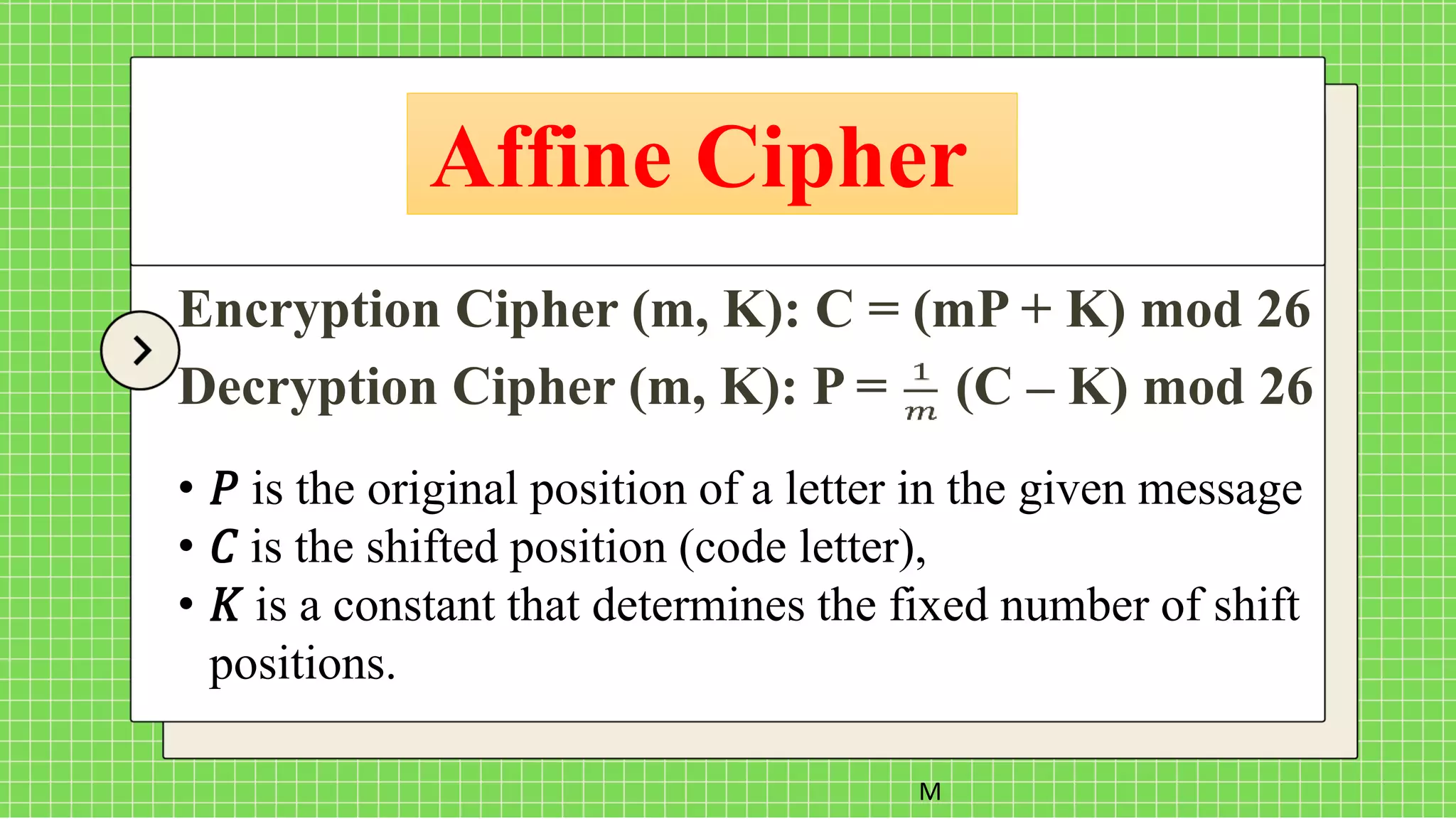
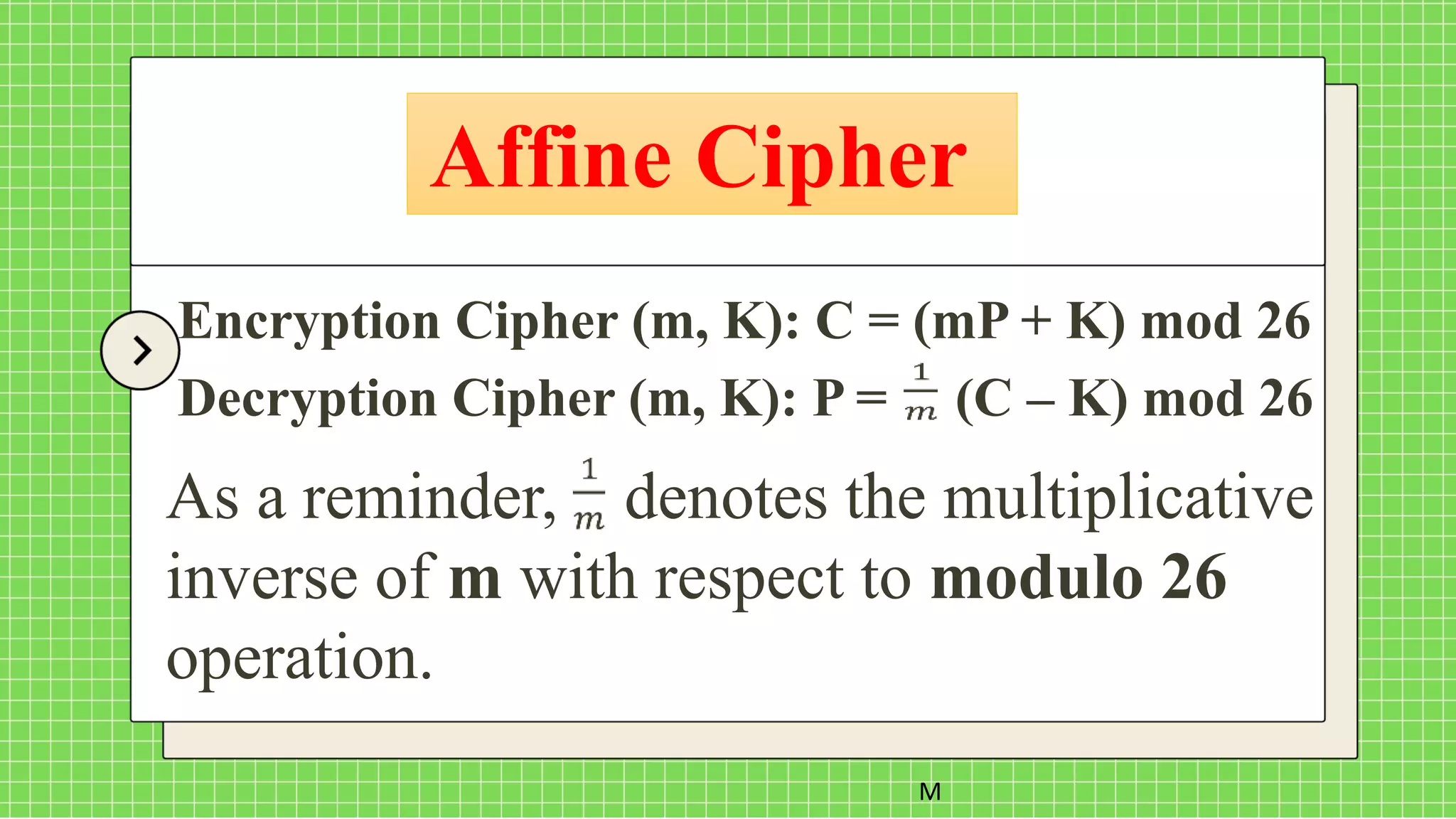
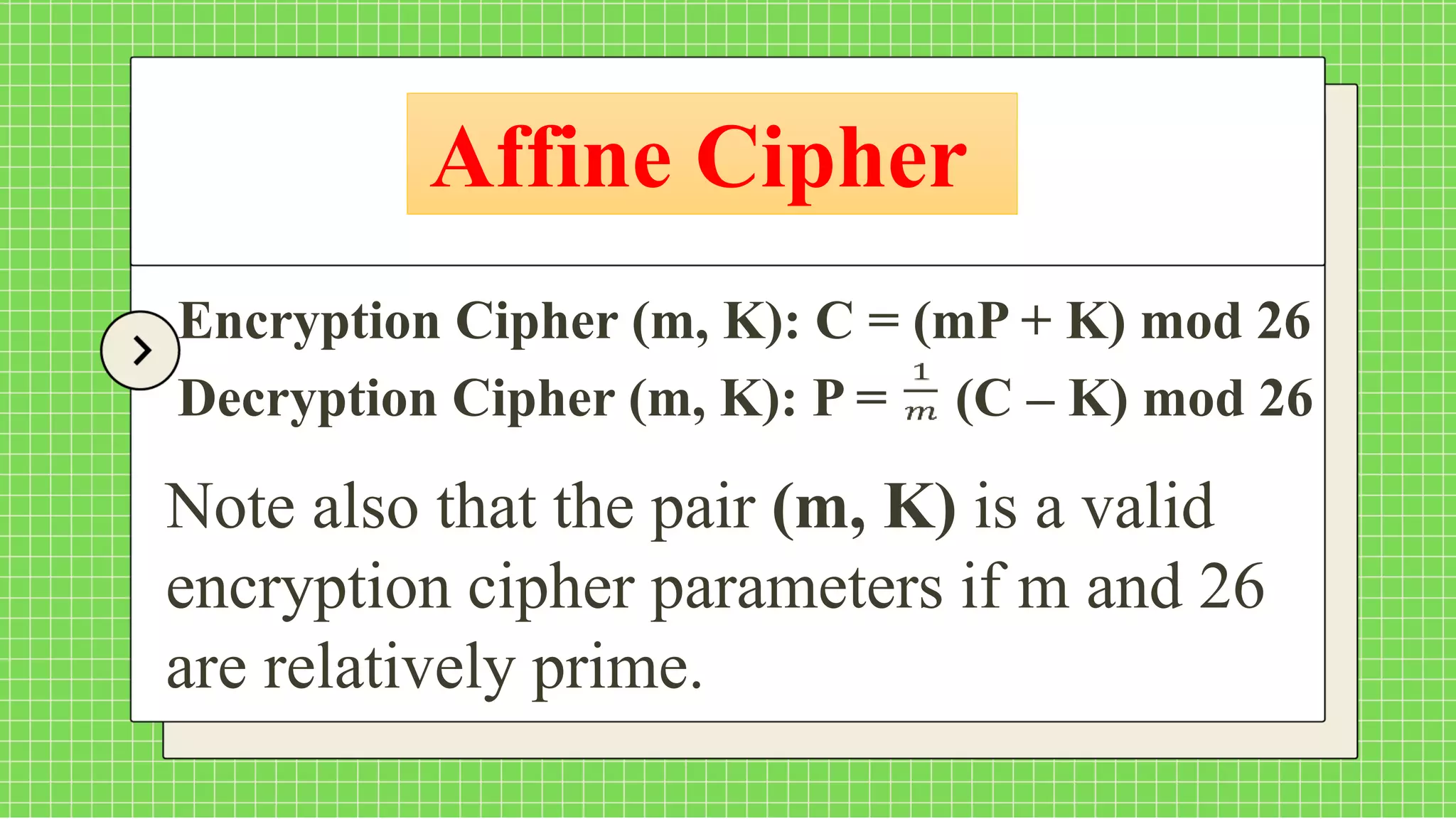
The document describes the affine cipher, which is a more complex cipher than the shift cipher. The affine cipher involves multiplying the cipher value of each letter by a value m, plus adding a constant value K, and taking the result modulo 26. It provides the encryption and decryption formulas for the affine cipher, which use m, K, and the original and ciphered positions of each letter. Examples are given to demonstrate encrypting and decrypting messages using specific m and K values with the affine cipher.


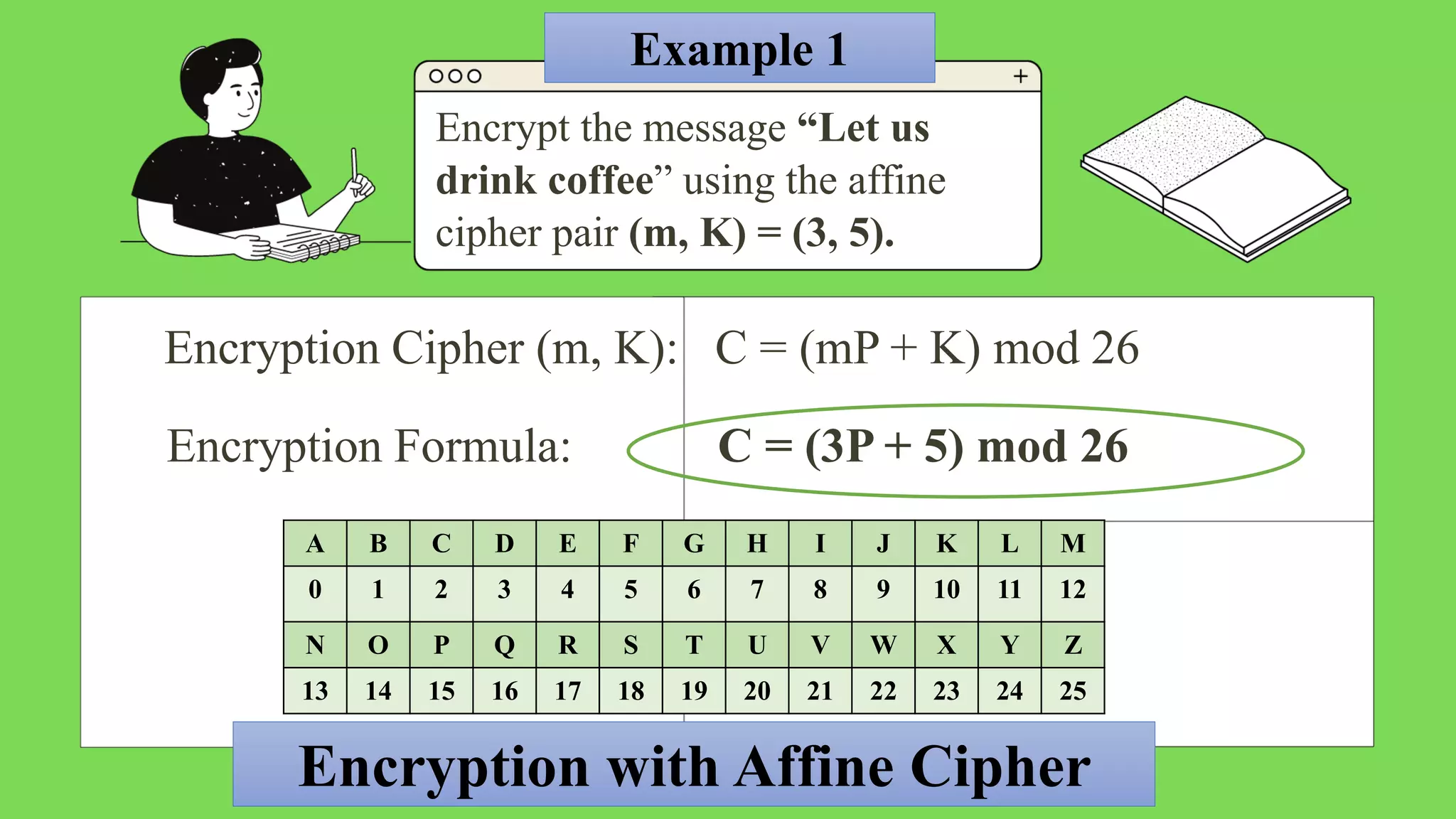
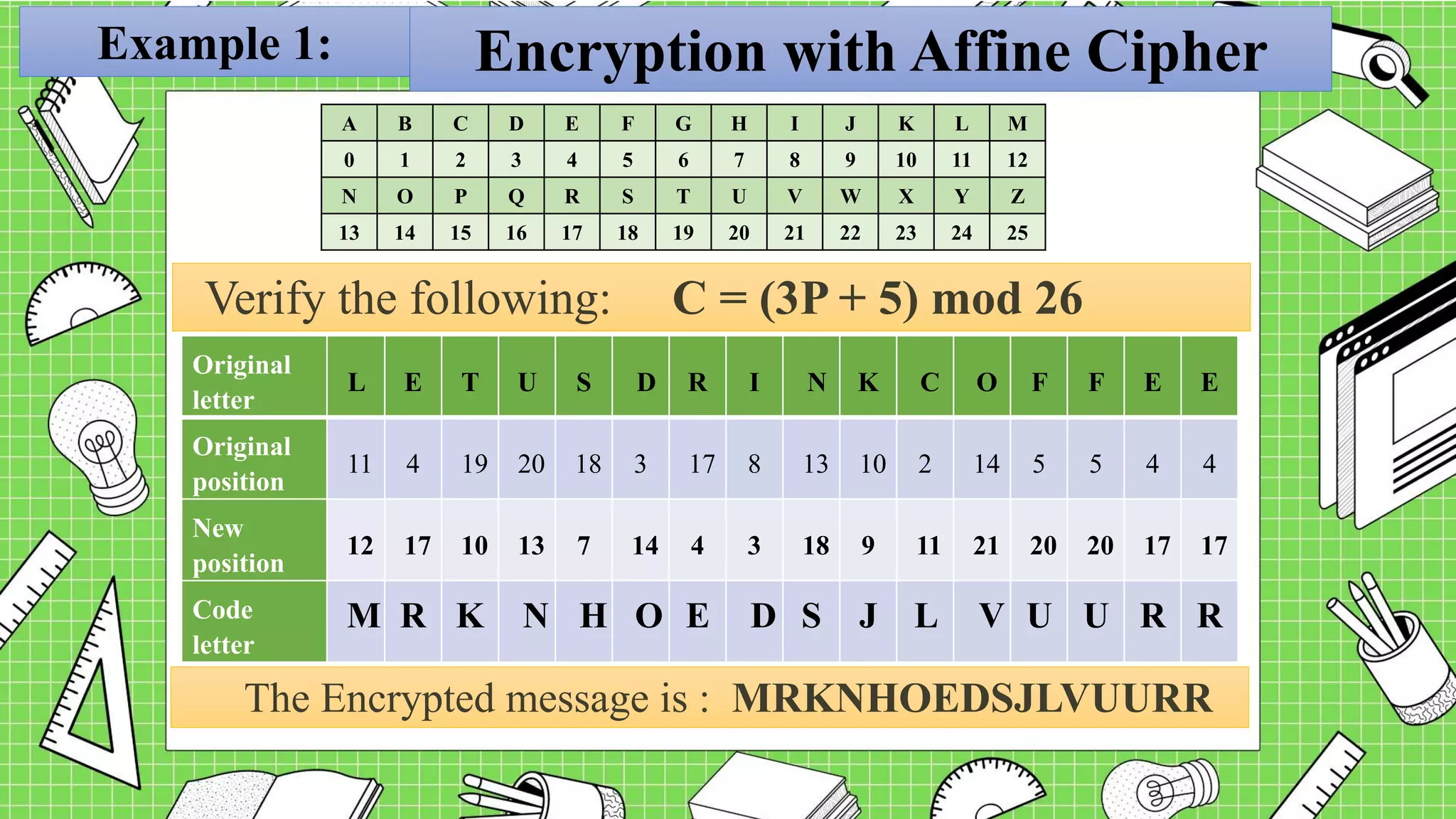
![Example 1:
Encrypt the message “Let us drink coffee” using
the affine cipher pair (m, K) = (3, 5).
Encryption with Affine Cipher
Encryption Formula:
C = (3P + 5) mod 26
• For letter “L”, P=11
• C=[(3)(11)+5] mod 26
= 38 mod 26 = 12 the code letter for “L” is “M”
A B C D E F G H I J K L M
0 1 2 3 4 5 6 7 8 9 10 11 12
N O P Q R S T U V W X Y Z
13 14 15 16 17 18 19 20 21 22 23 24 25](https://image.slidesharecdn.com/cryptographyaffinecipherianchristinemario-221111141008-2fd4dd59/75/Cryptography-Affine-Cipher-Ian-Christine-Mario-pptx-7-2048.jpg)