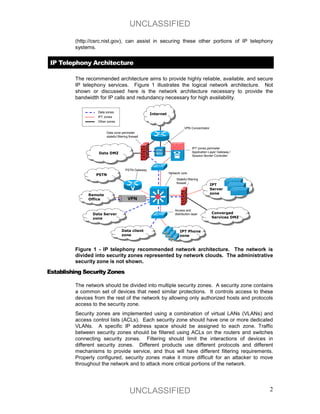
The document provides recommendations for securing IP telephony systems, including:
- Establishing separate security zones and controlling traffic between zones
- Using firewalls and application layer gateways to control external connections
- Implementing layer 2 protections, authentication, encryption, and availability measures
- Protecting against denial of service attacks and securing physical infrastructure
- Recommending practices like device management, testing, and physical access controls