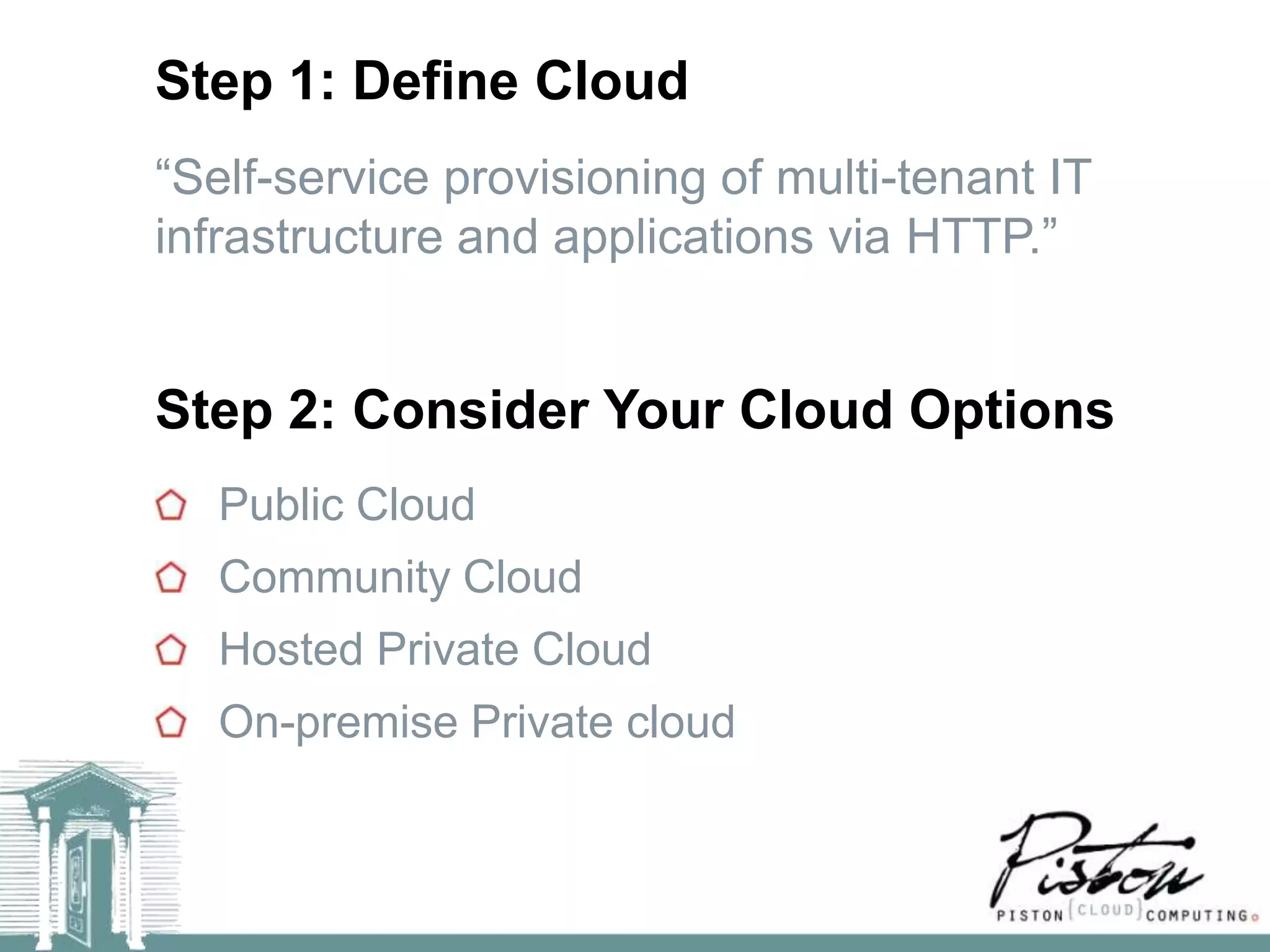
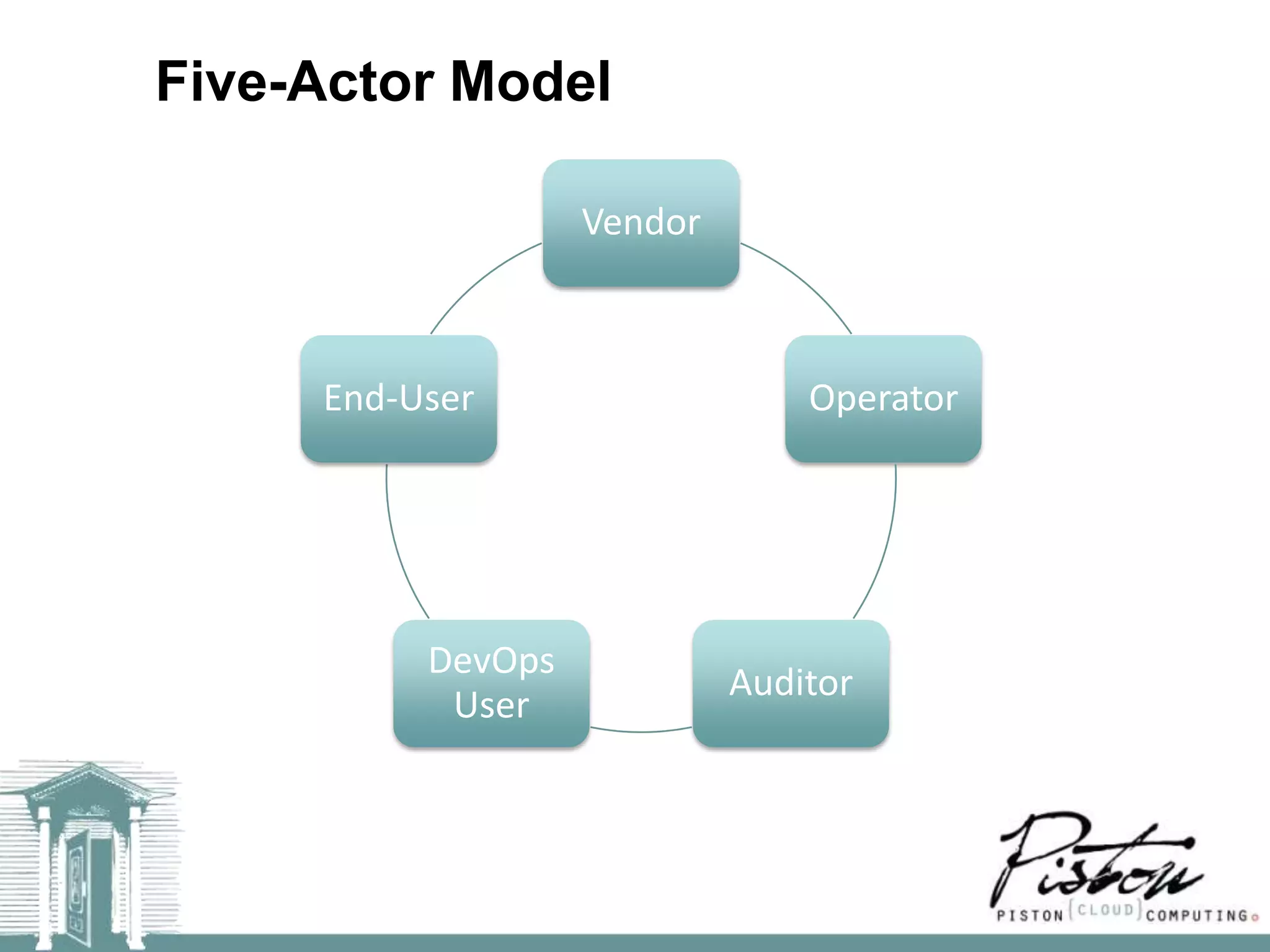
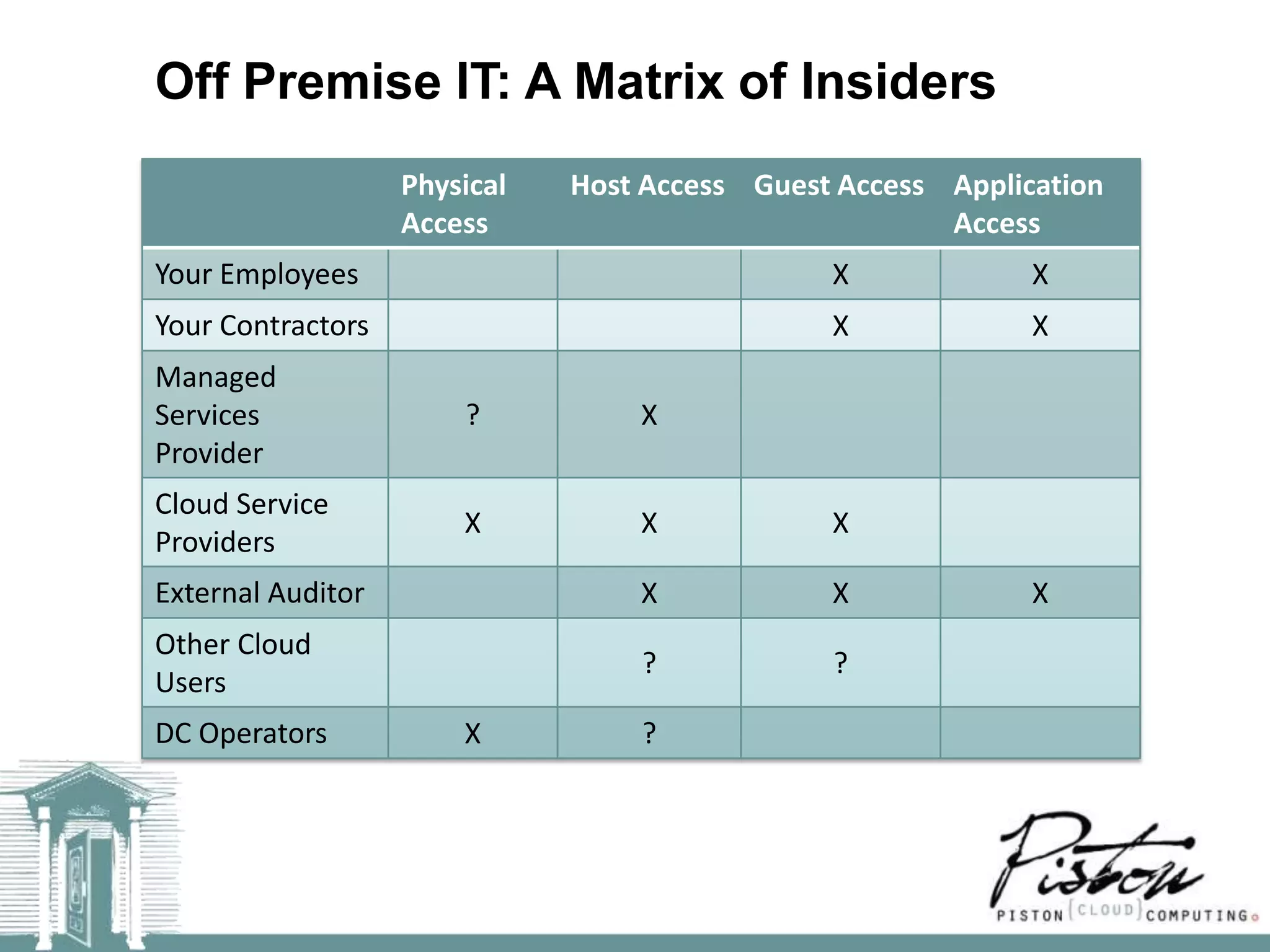
The document discusses the risks of technology and complexity in cloud computing. It argues that adding more technology alone cannot solve security problems, and may increase other risks around complexity and compliance. The key takeaways are that complexity is the enemy, adding "rootkits" is not the solution, automation should be used to limit access, and services should be simplified using Pareto's Law.