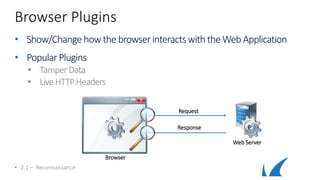
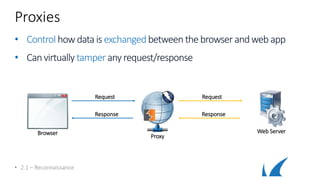
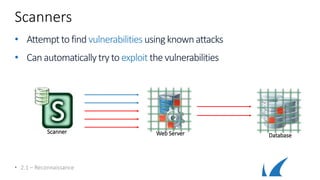
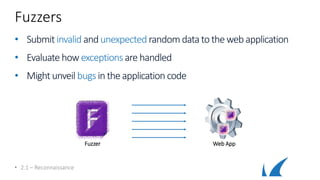
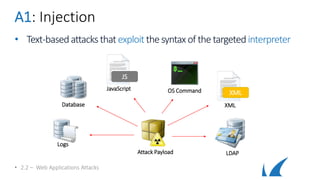
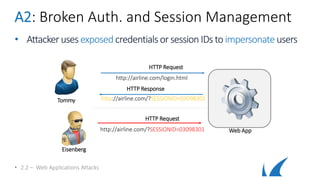
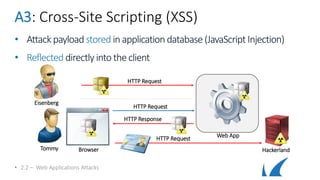
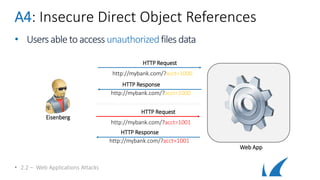
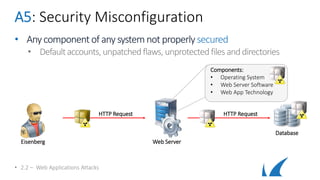
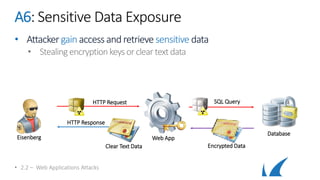
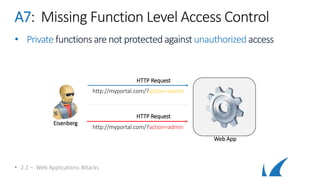
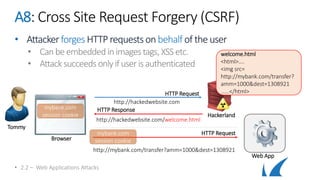
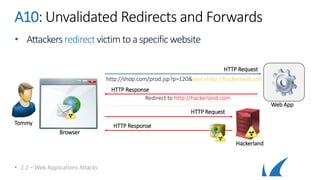
This document provides an overview of topics related to analyzing and attacking web applications. It discusses techniques for reconnaissance like using Wireshark, browser plugins, proxies, scanners and fuzzers to gather information. It also covers mapping applications, identifying vulnerabilities outlined in the OWASP Top 10 like injection, XSS and insecure authentication, and additional risks like clickjacking, denial of service and information leakage.