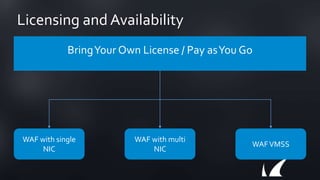
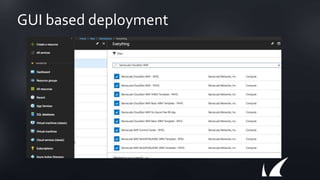
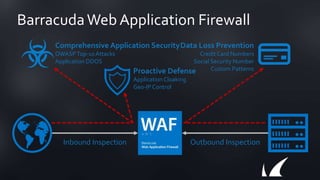
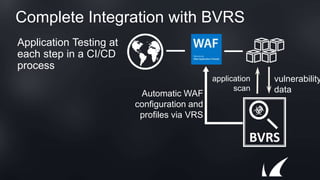
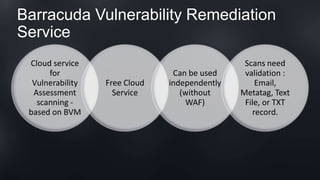
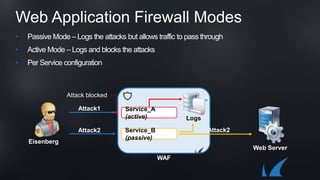
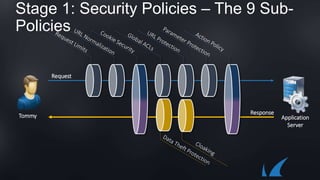
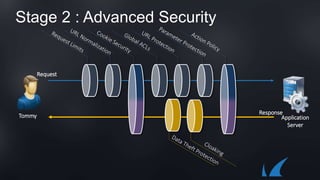
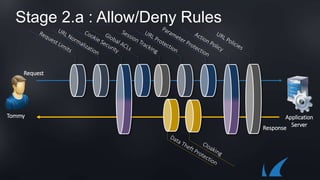
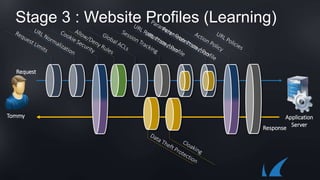
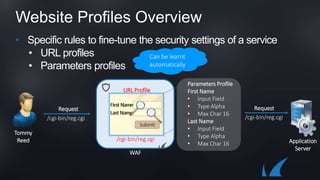
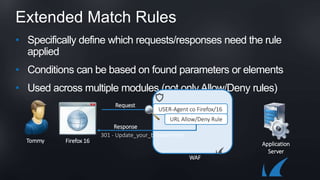
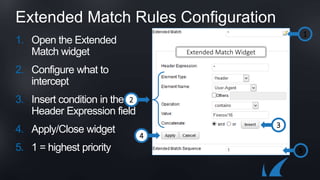
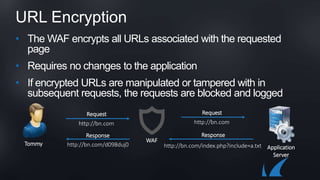
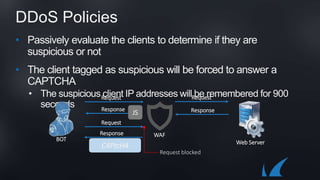
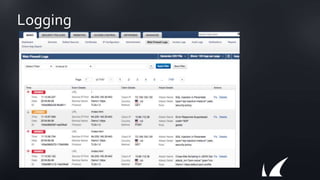
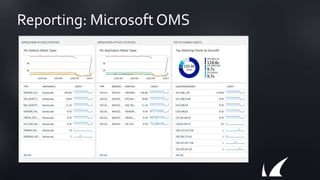
The document discusses Barracuda's Web Application Firewall product. It covers deployment options including bringing your own license and pay-as-you-go models. It also discusses security features such as inbound and outbound inspection, application DDoS protection, and integration with the Barracuda Vulnerability Remediation Service. Configuration and management options using the GUI and Puppet are also summarized.