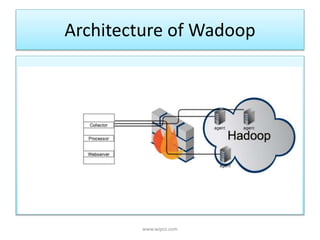
Wadoop is an extensible security framework for Hadoop developed by Wipro that aims to address common security issues in big data administration. It delivers authentication, authorization, and auditing capabilities and provides a unified view of user access and reporting across Hadoop components. The architecture of Wadoop includes components for user management, access control, data zoning for logical data grouping, and dashboards for security reporting and resource utilization.