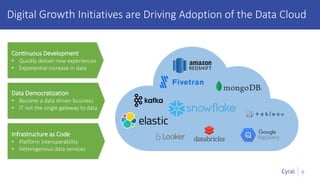
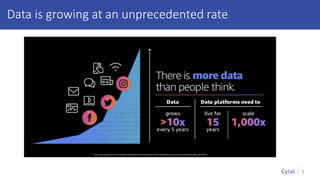
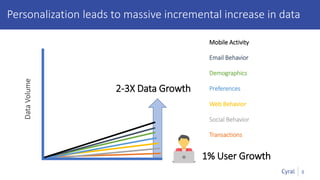
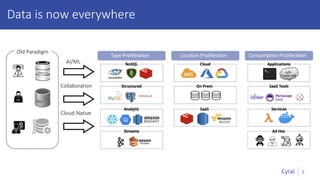
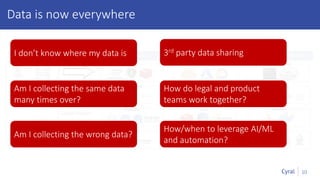
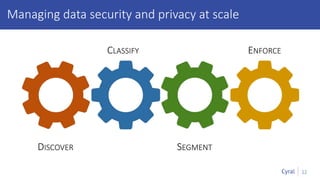
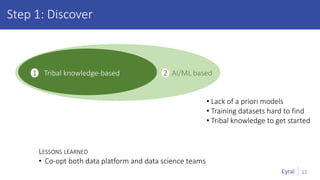
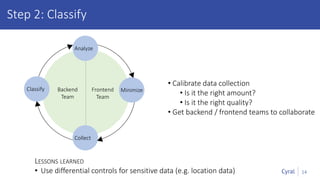
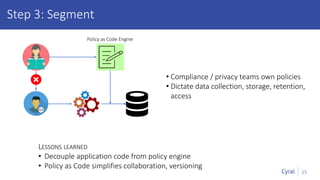
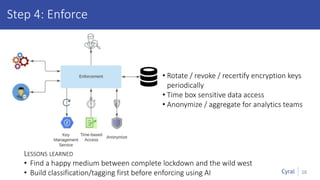
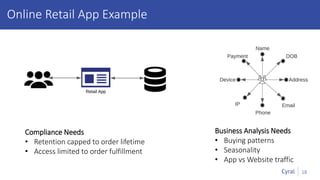
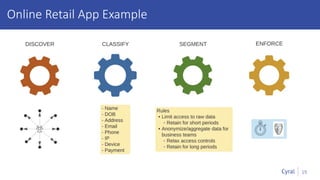
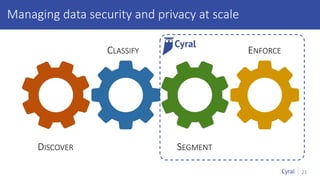
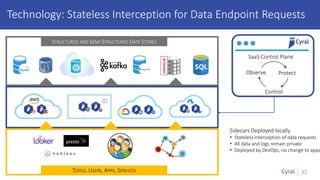
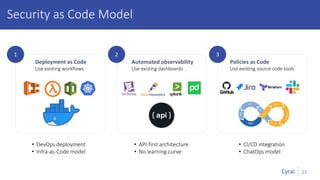
The document introduces a new framework for managing data privacy and security, emphasizing discovery, classification, segmentation, and enforcement. It discusses the challenges of data security at scale in the context of rapid digital growth and increasing data volumes, and how organizations can implement this framework effectively. Additionally, it provides an example of an online retail app to illustrate compliance and business analysis needs, along with how Cyral can assist in managing these data security challenges.