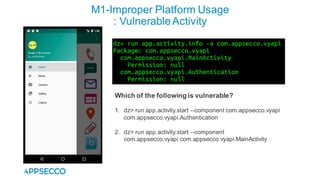
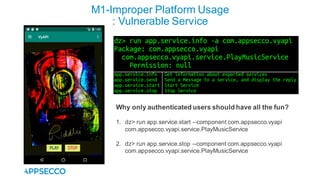
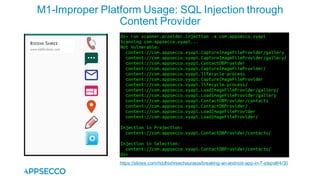
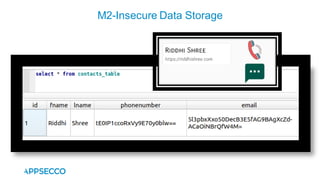
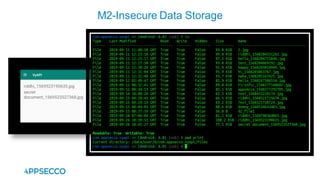
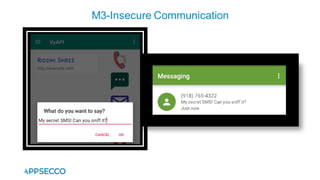
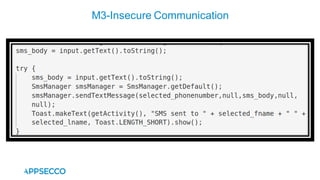
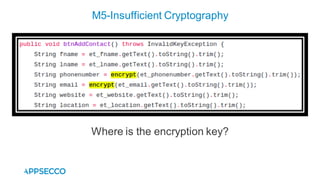
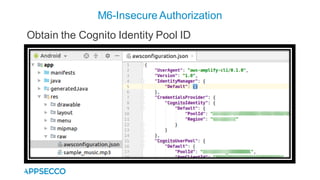
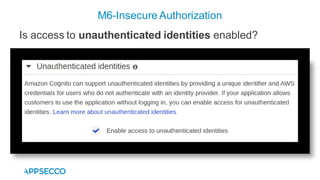
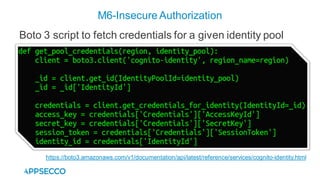
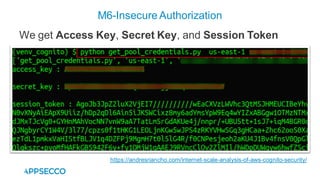
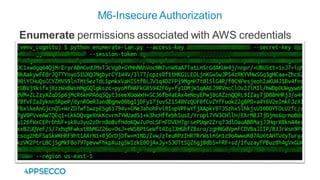
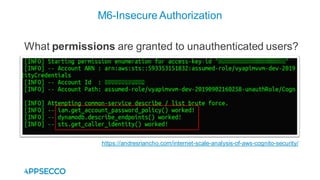
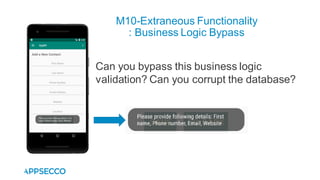
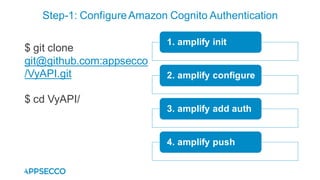
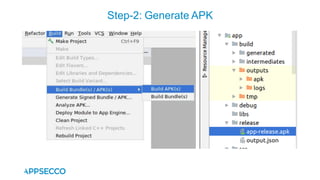
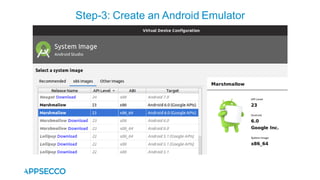
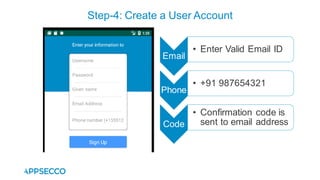
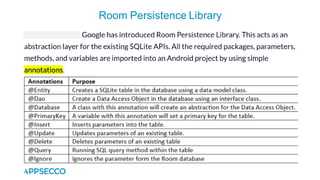
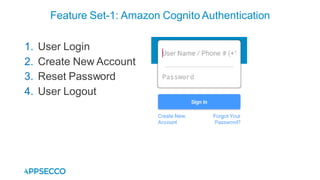
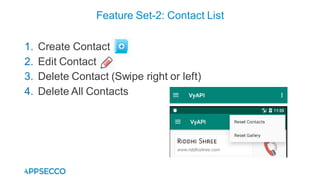
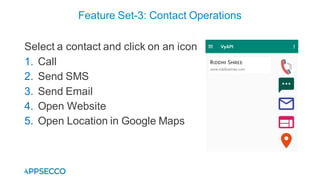
Vyapi 1.0 is a cloud-based vulnerable Android app designed for security enthusiasts to practice hacking and explore various Android vulnerabilities as outlined by OWASP's Mobile Top 10. The app includes features such as user authentication, contact management, and background music play, while also demonstrating issues like insecure data storage and improper platform usage. Users can set up a testing environment using AWS services and industry tools, with detailed setup instructions and a repository available on GitHub.