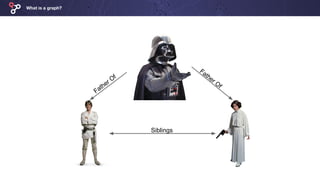
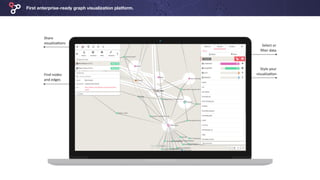
The document discusses the use of graph technologies to combat fraud, highlighting the limitations of traditional relational databases in modeling complex relationships. It emphasizes the increasing importance of graph databases for fraud detection, offering tools to visualize and analyze connections among data entities. Linkurious provides a graph visualization platform aimed at enhancing fraud detection capabilities and accelerating investigations.