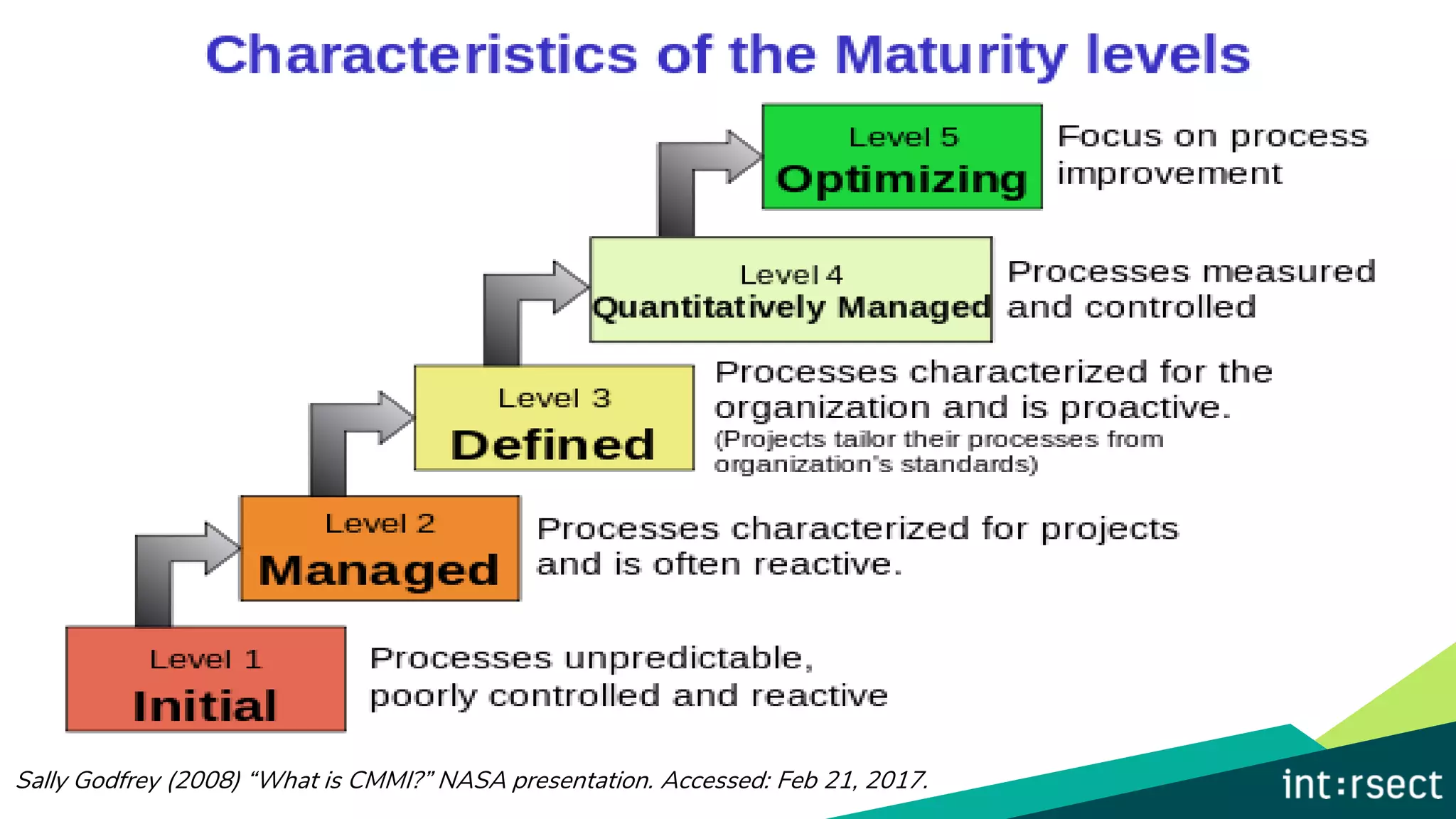
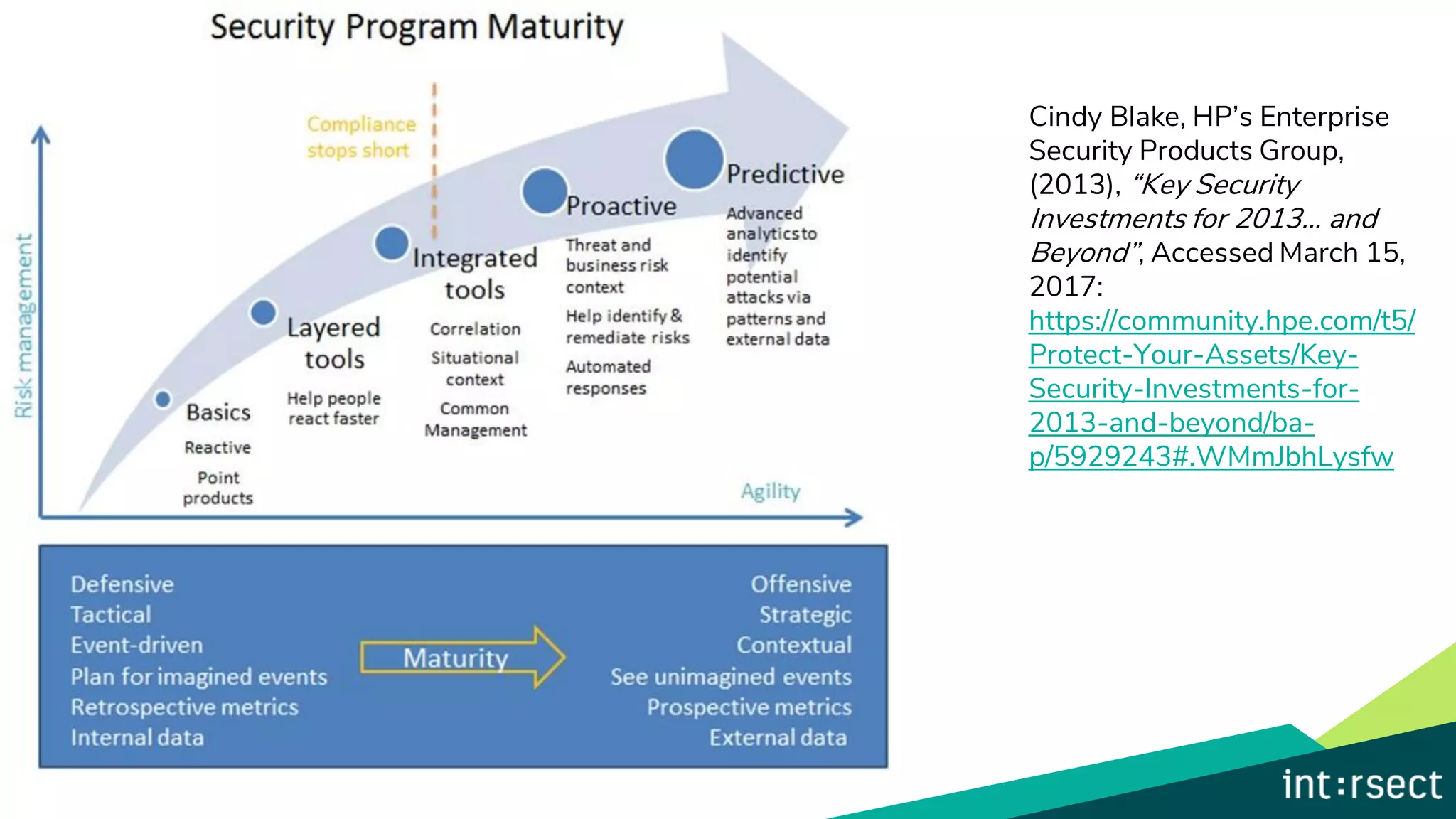
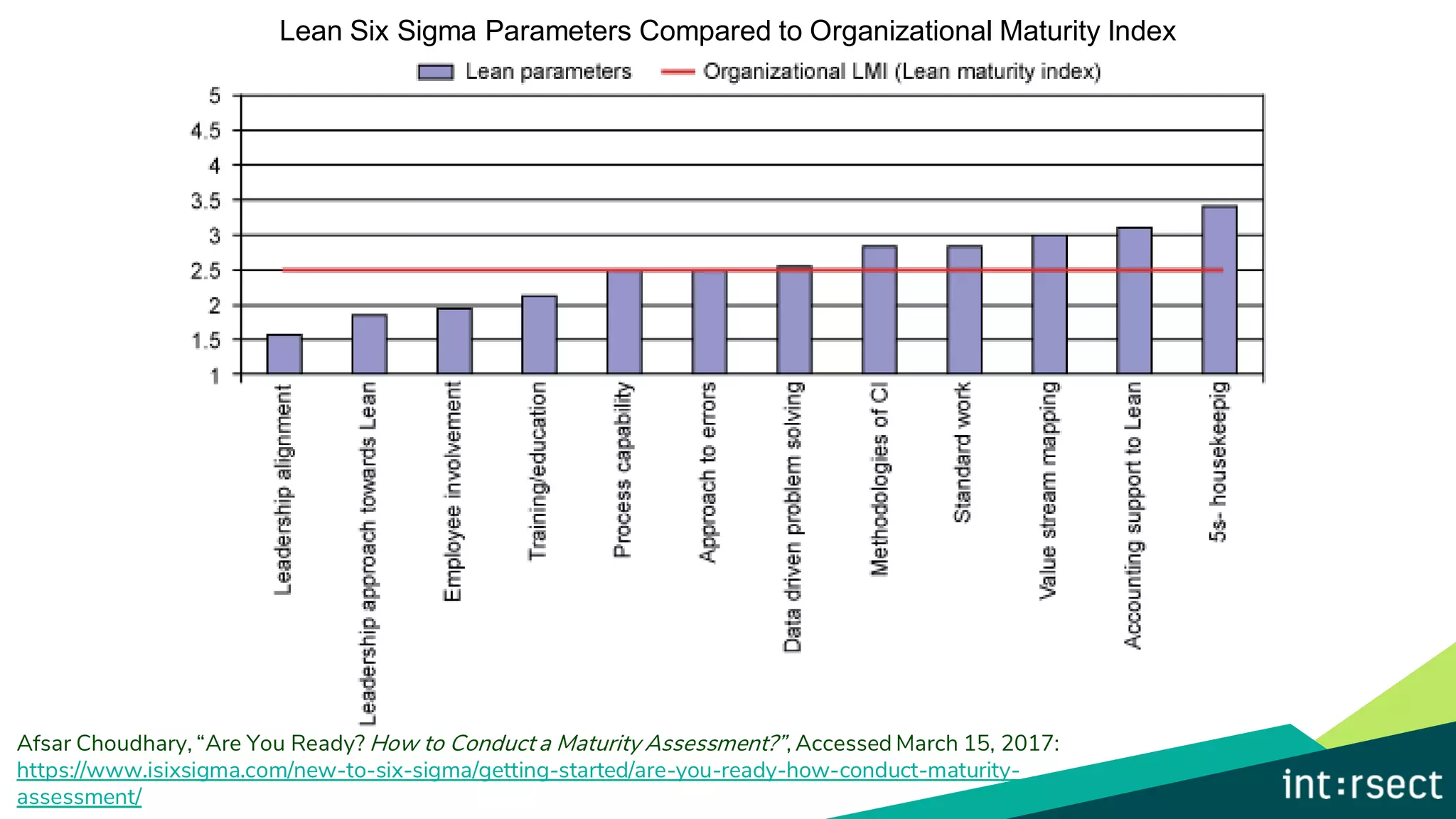
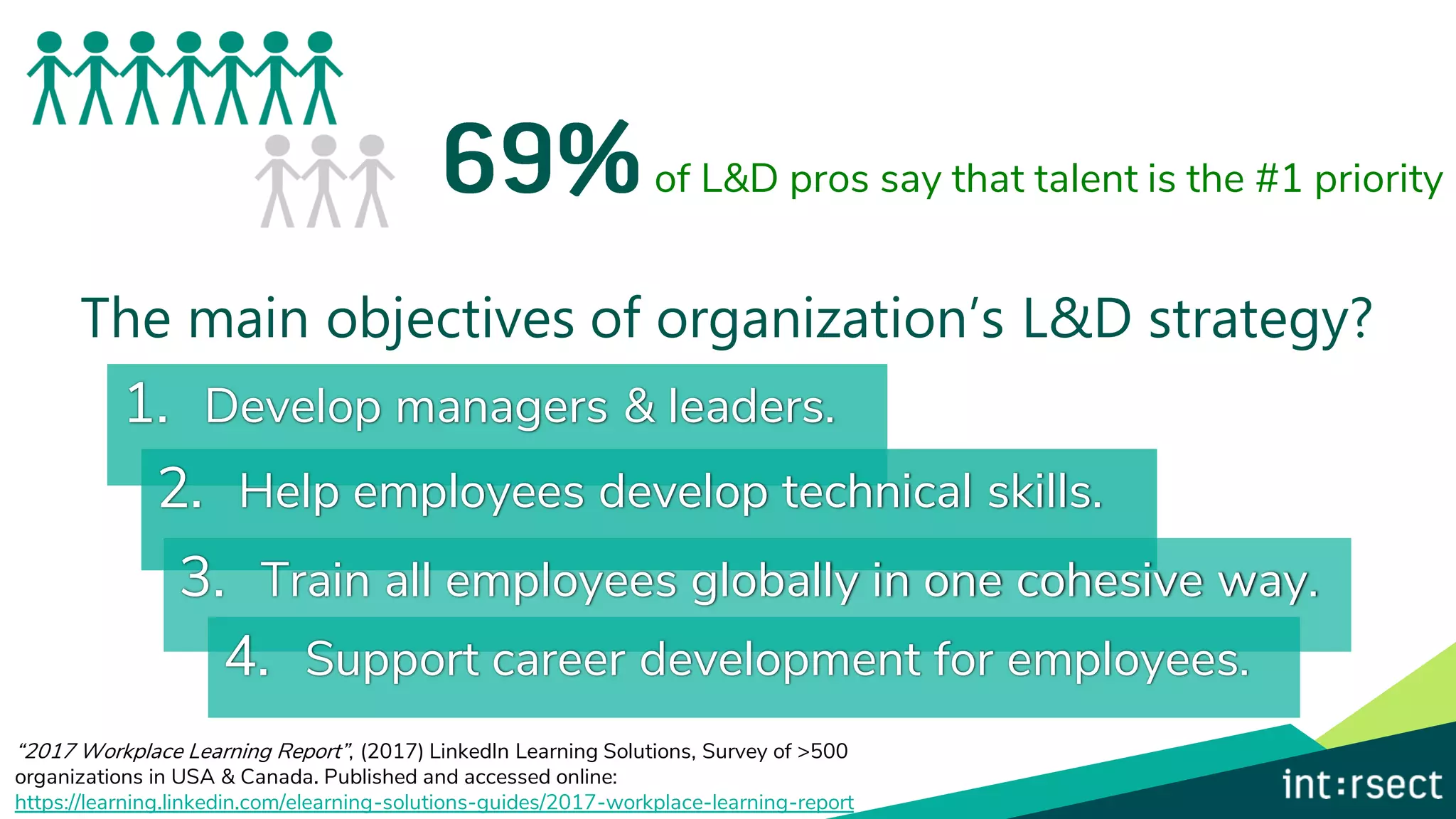
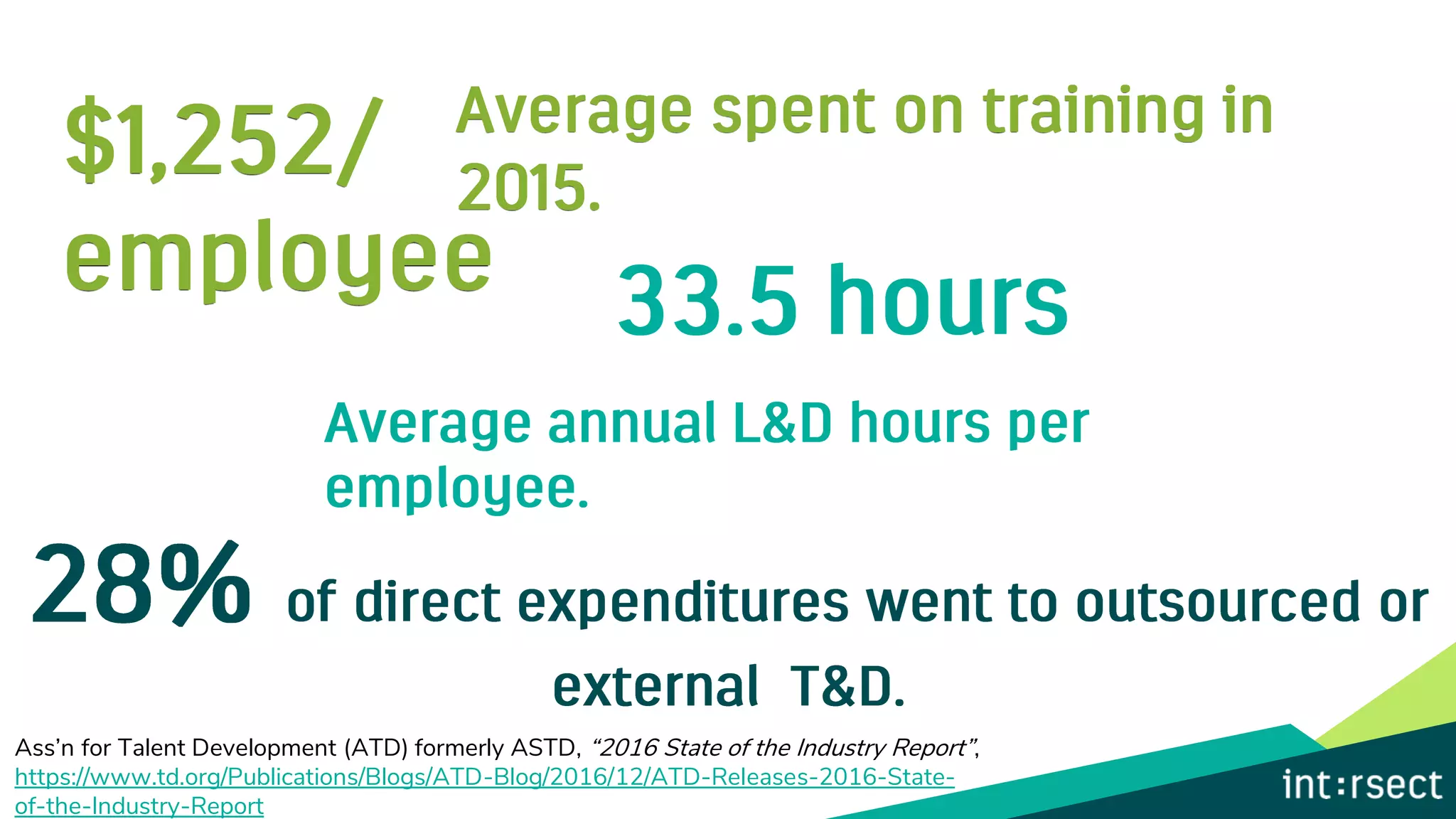
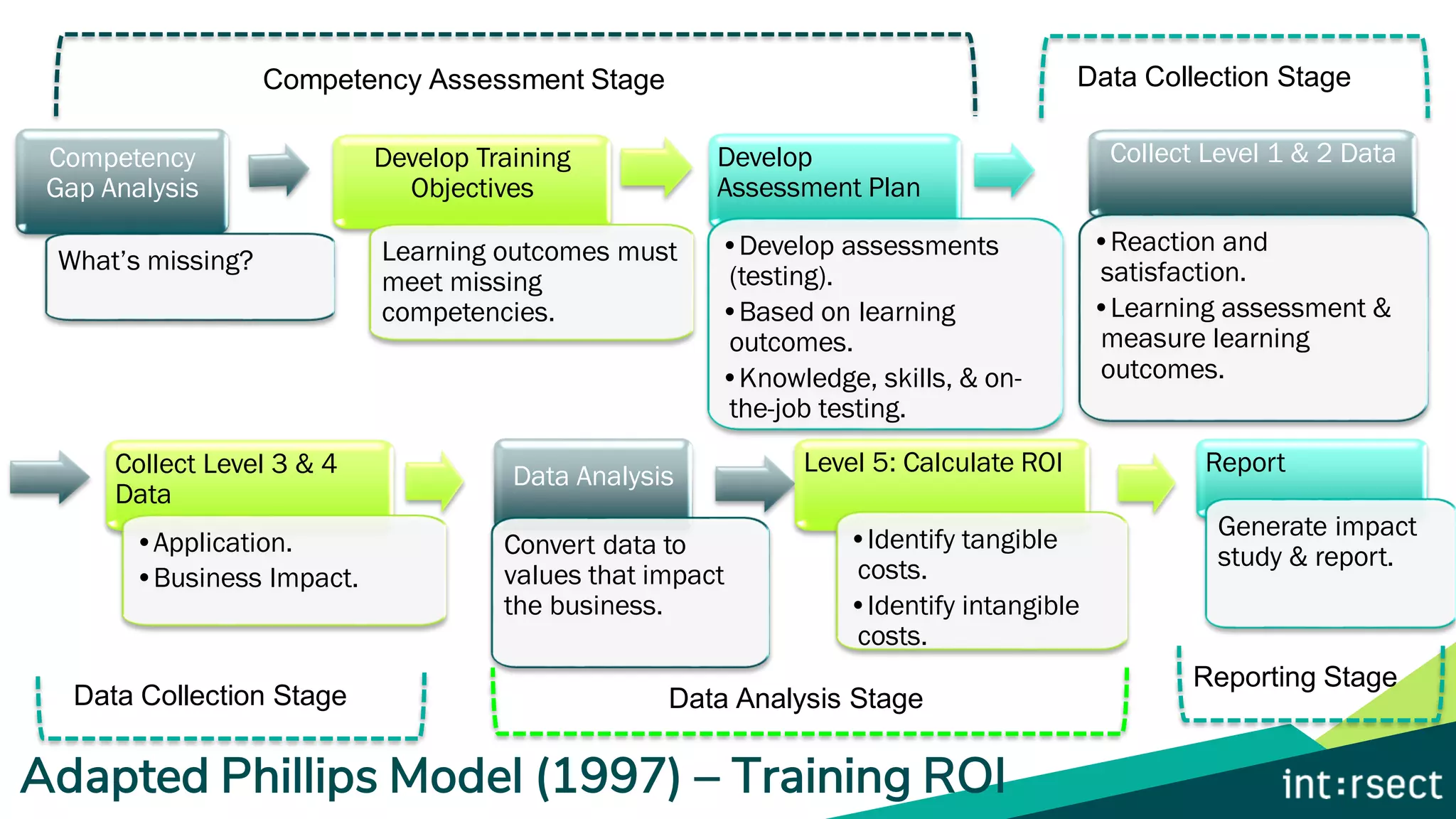
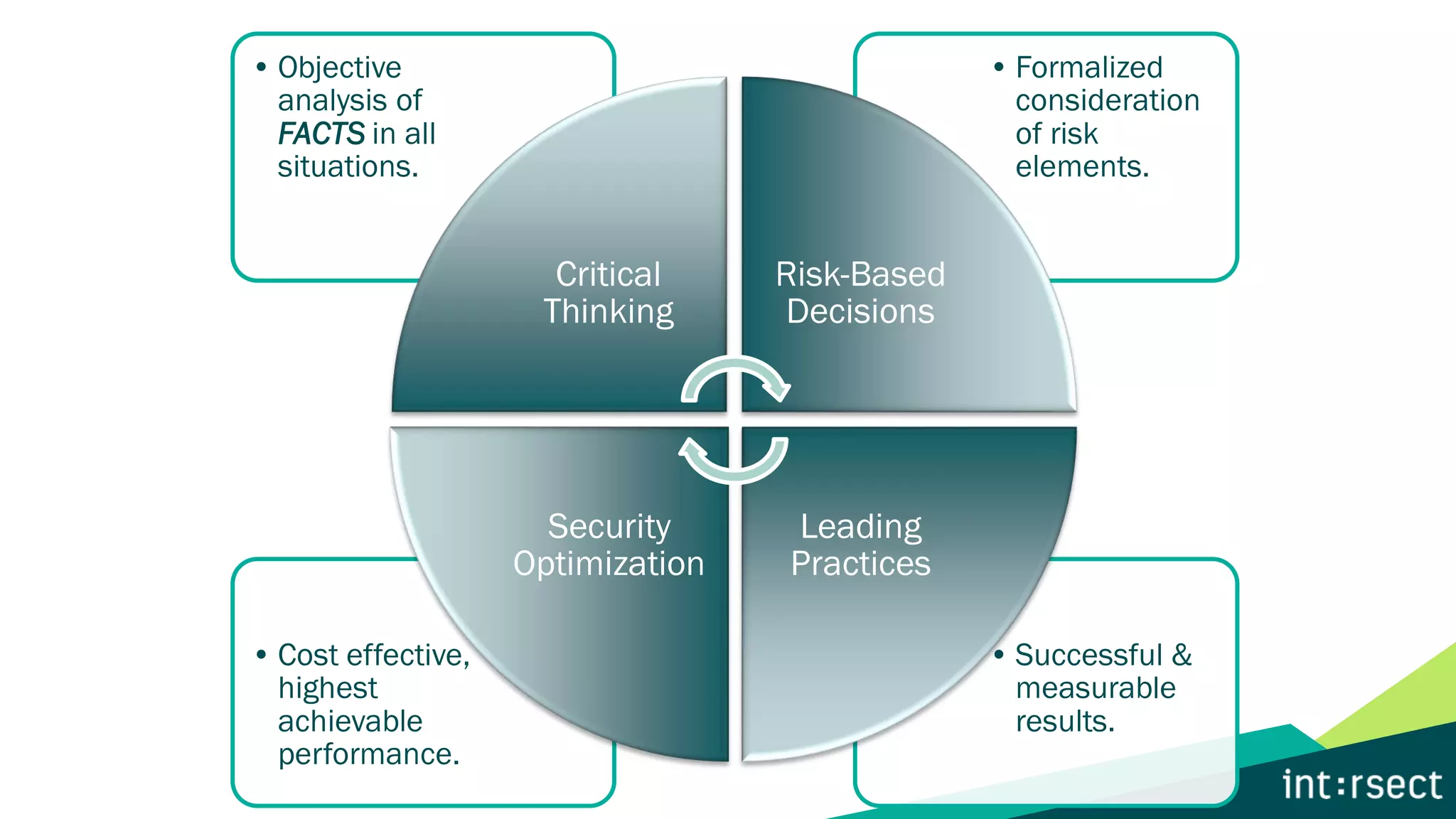
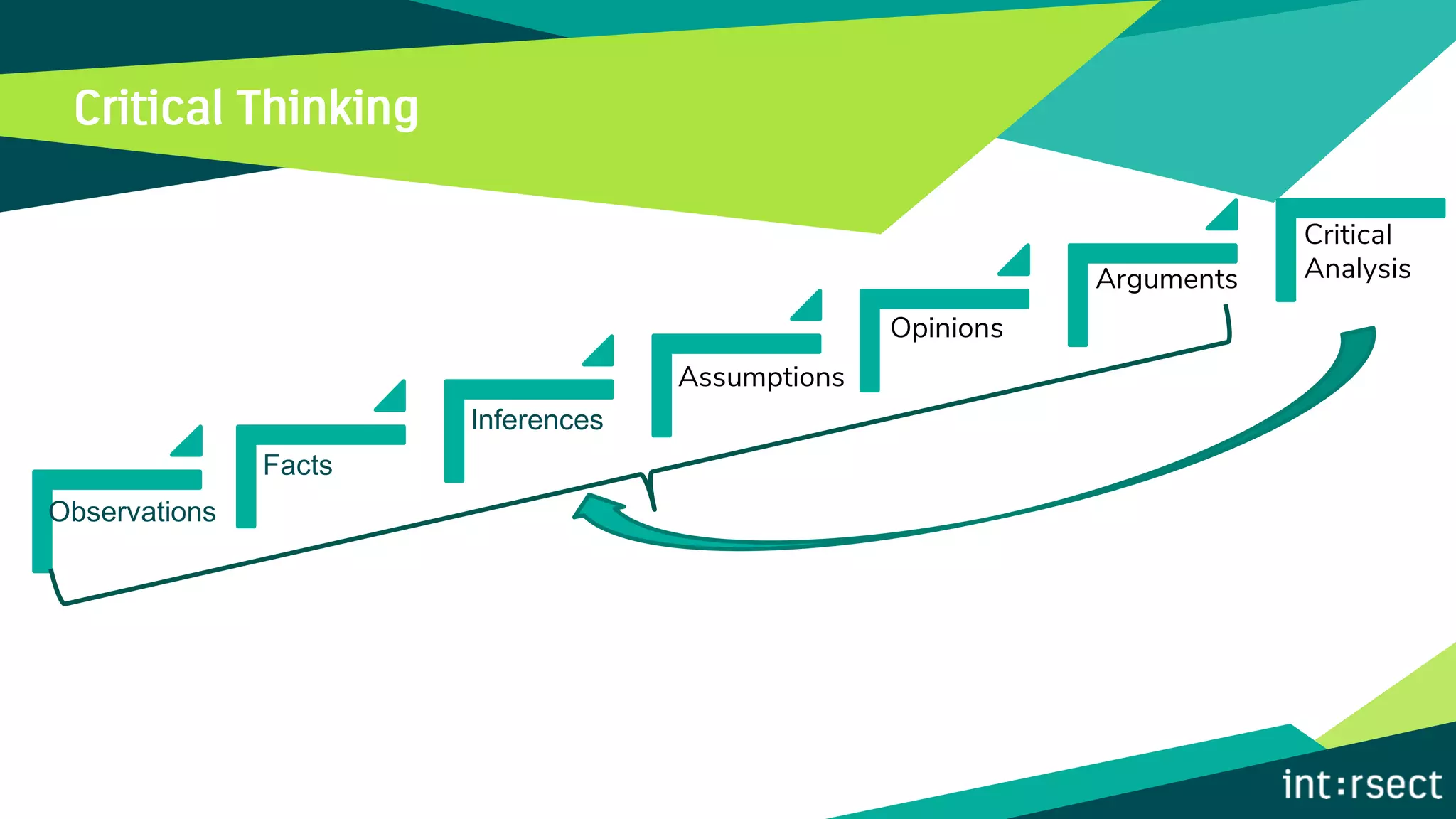
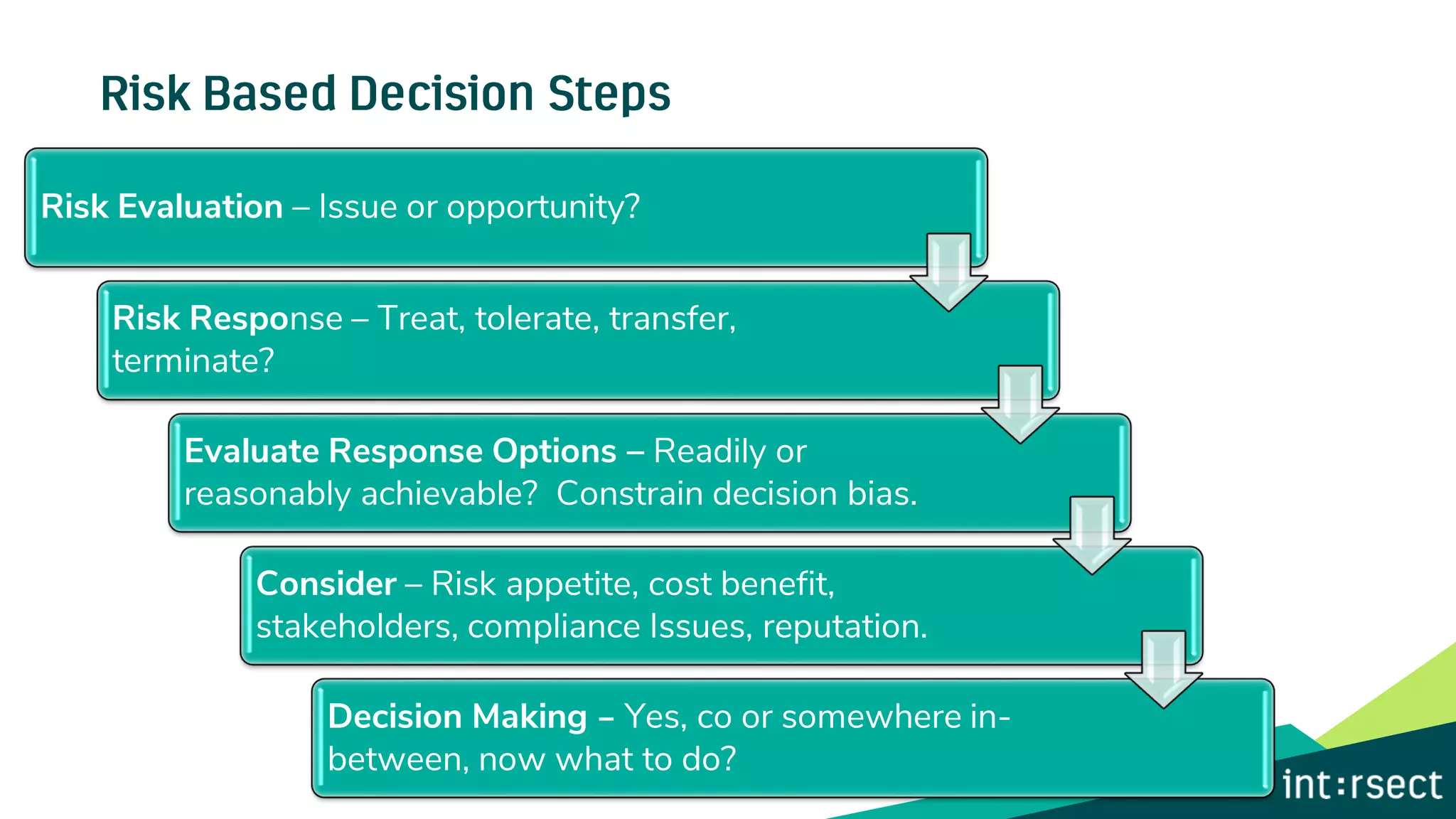
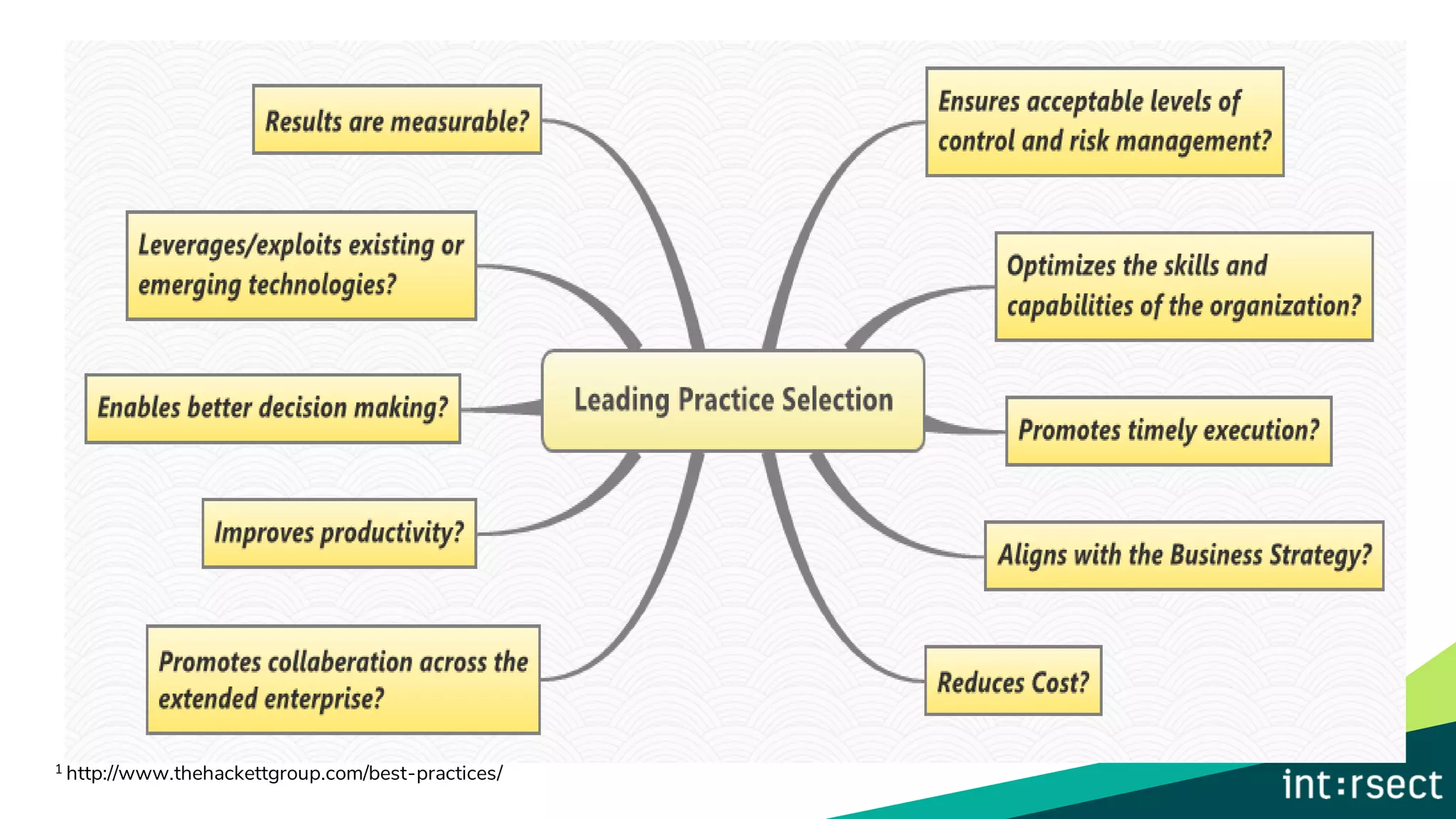
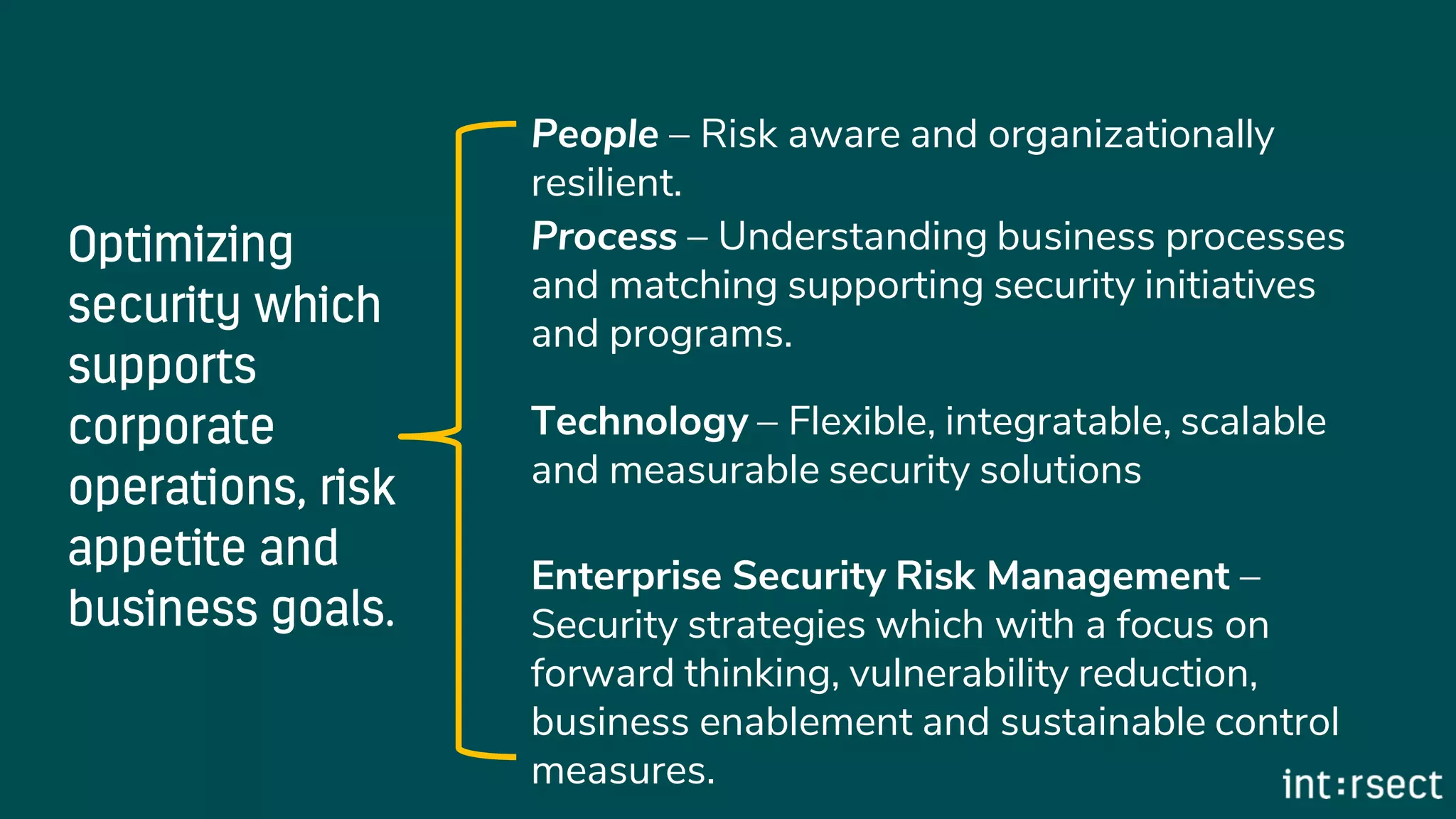
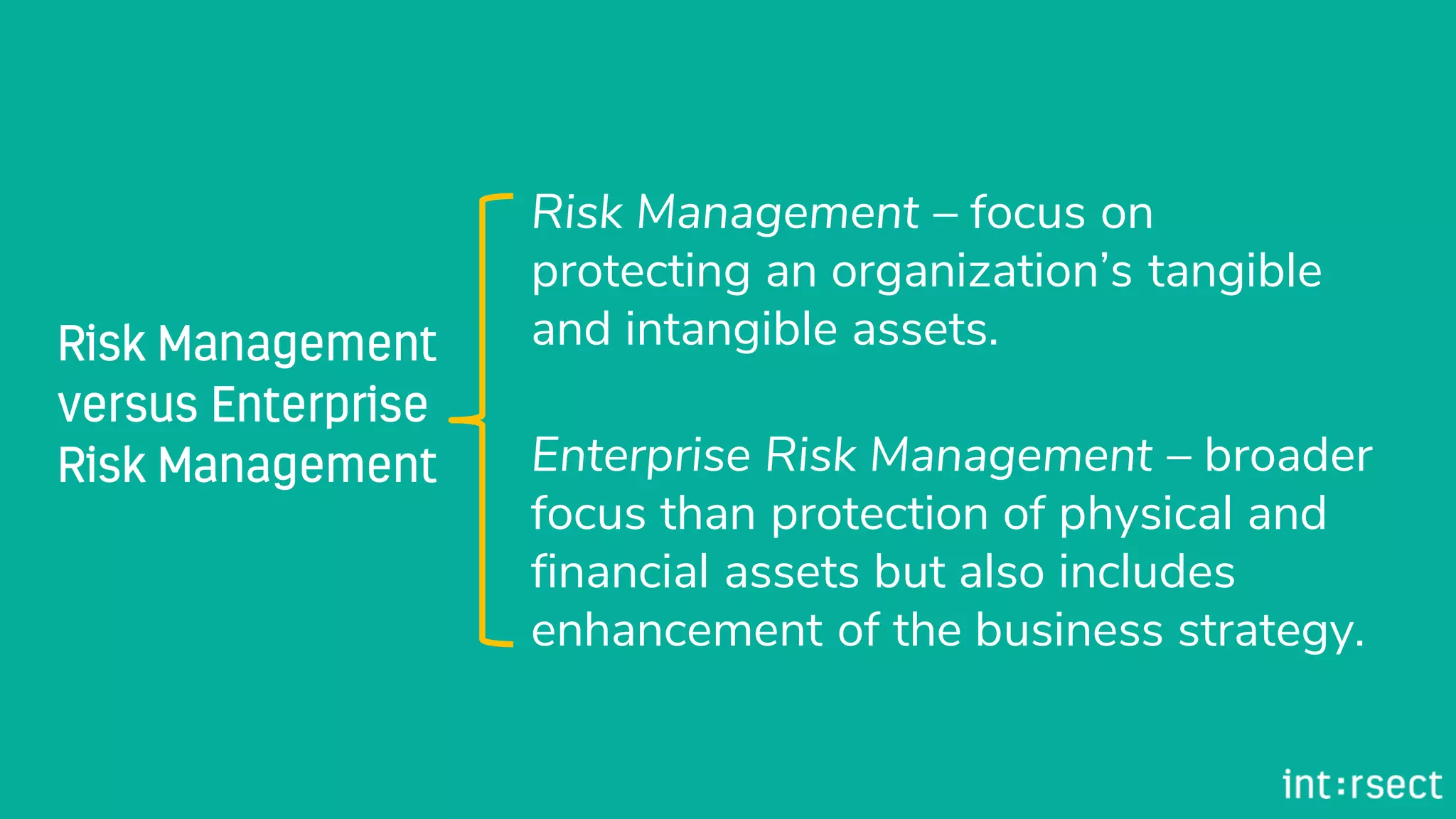
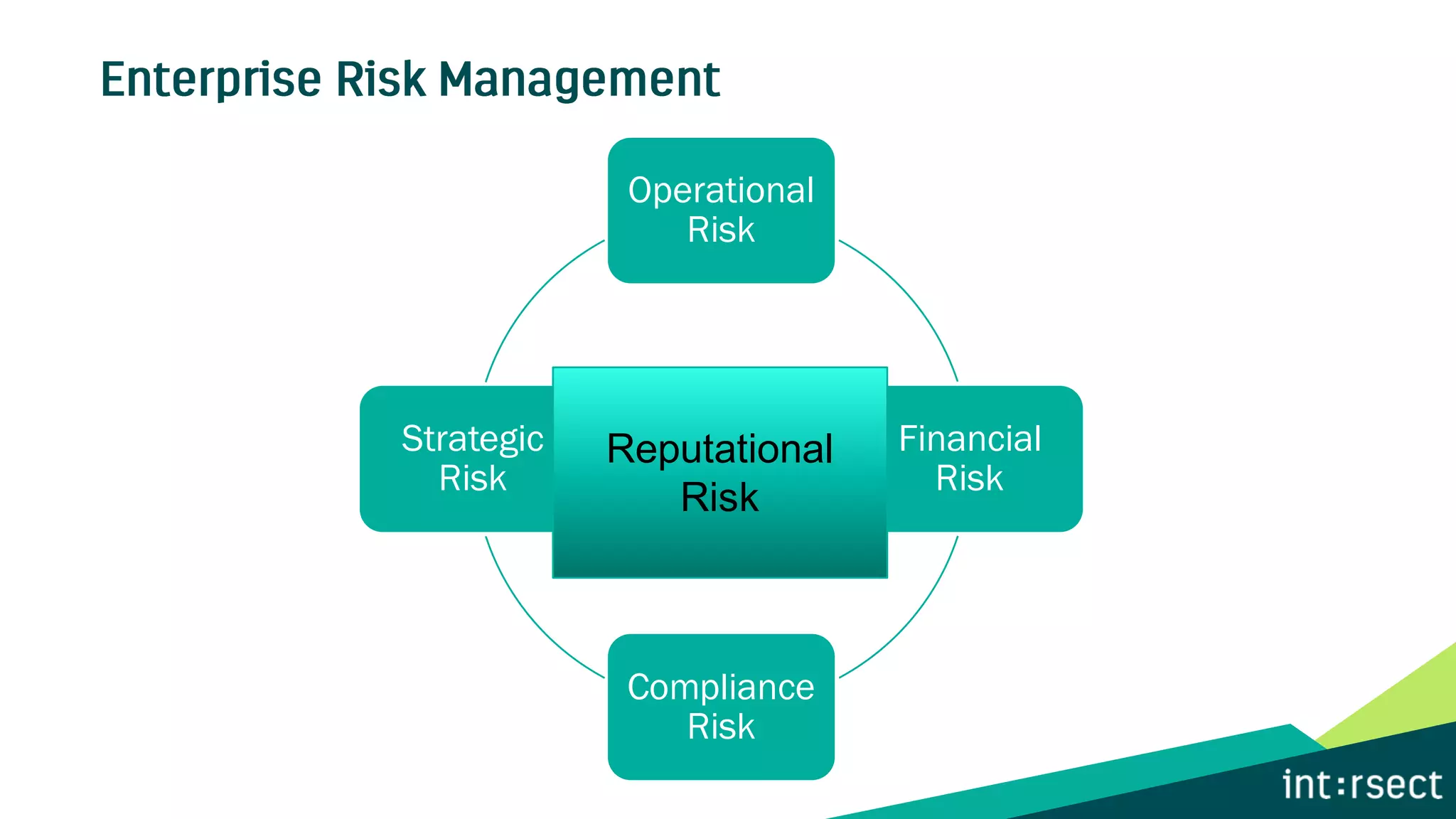
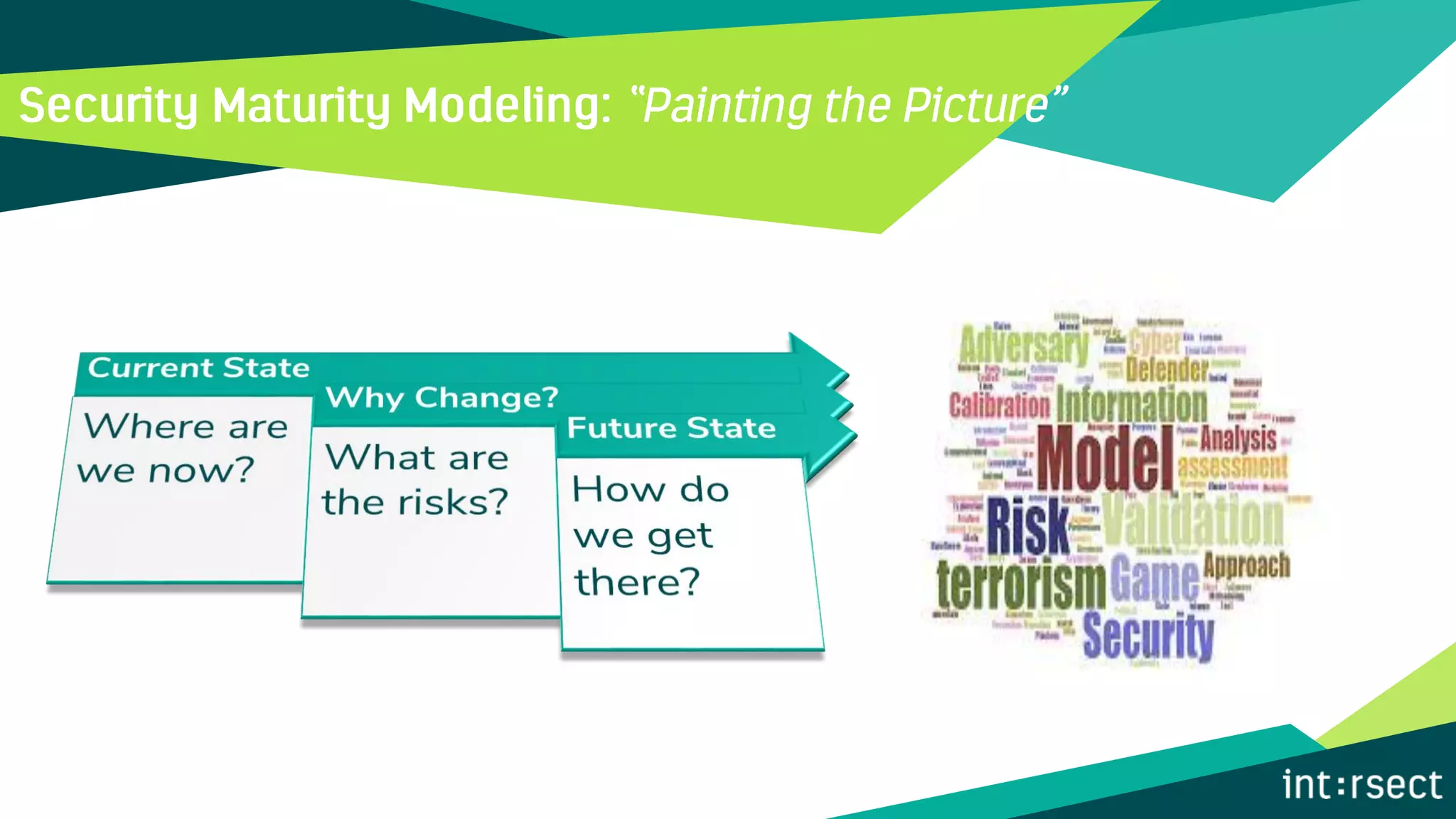
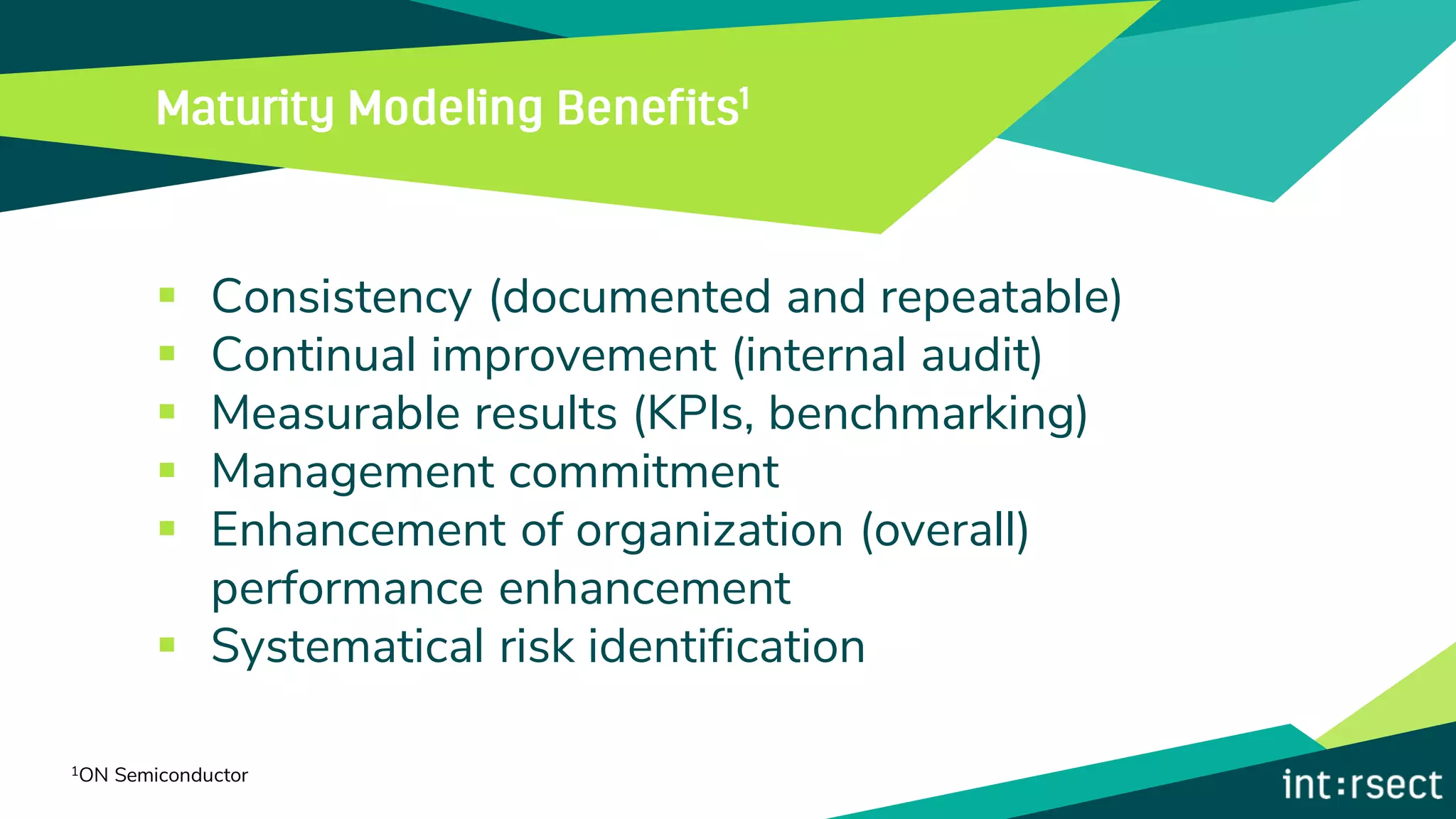
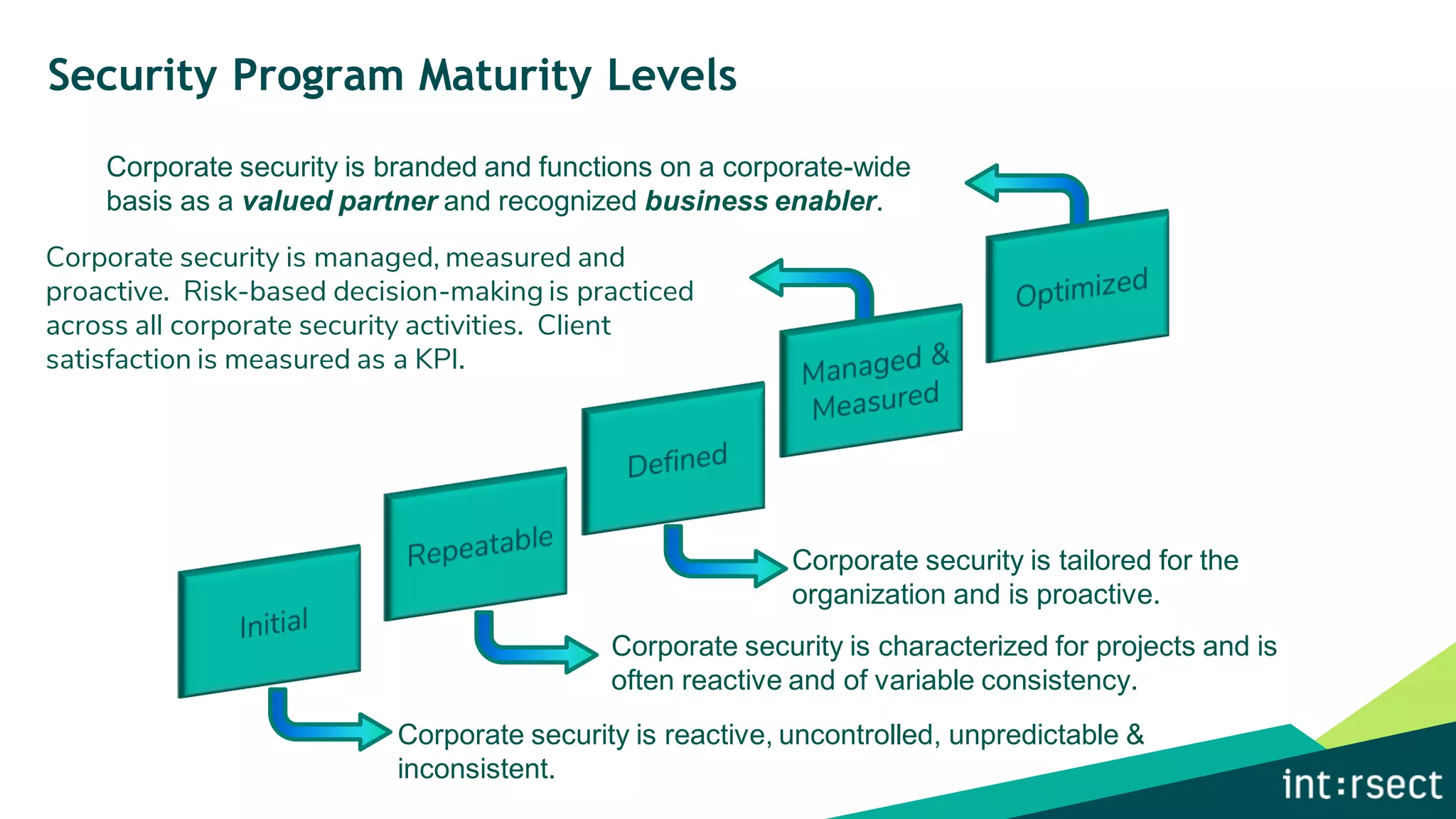
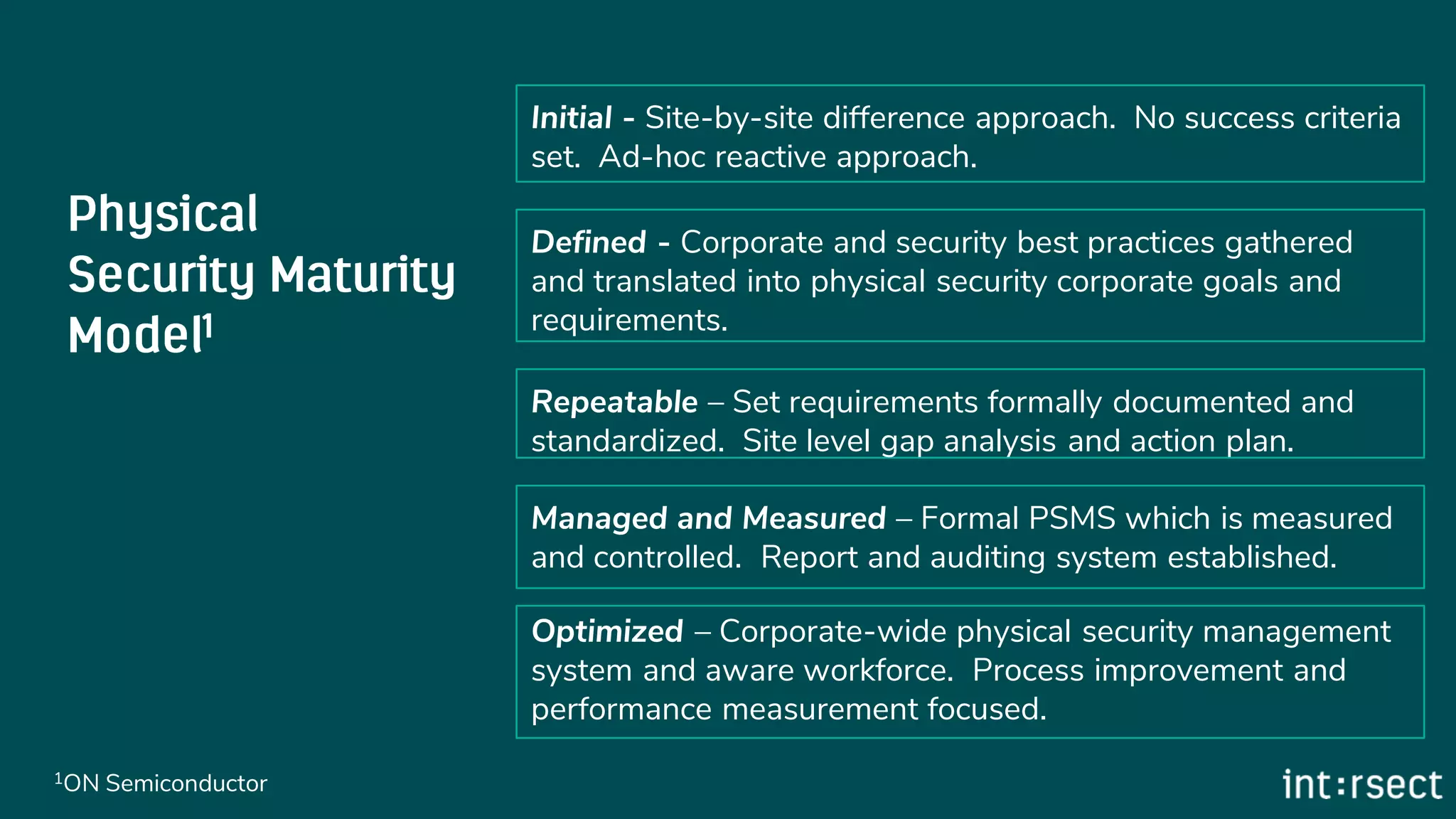
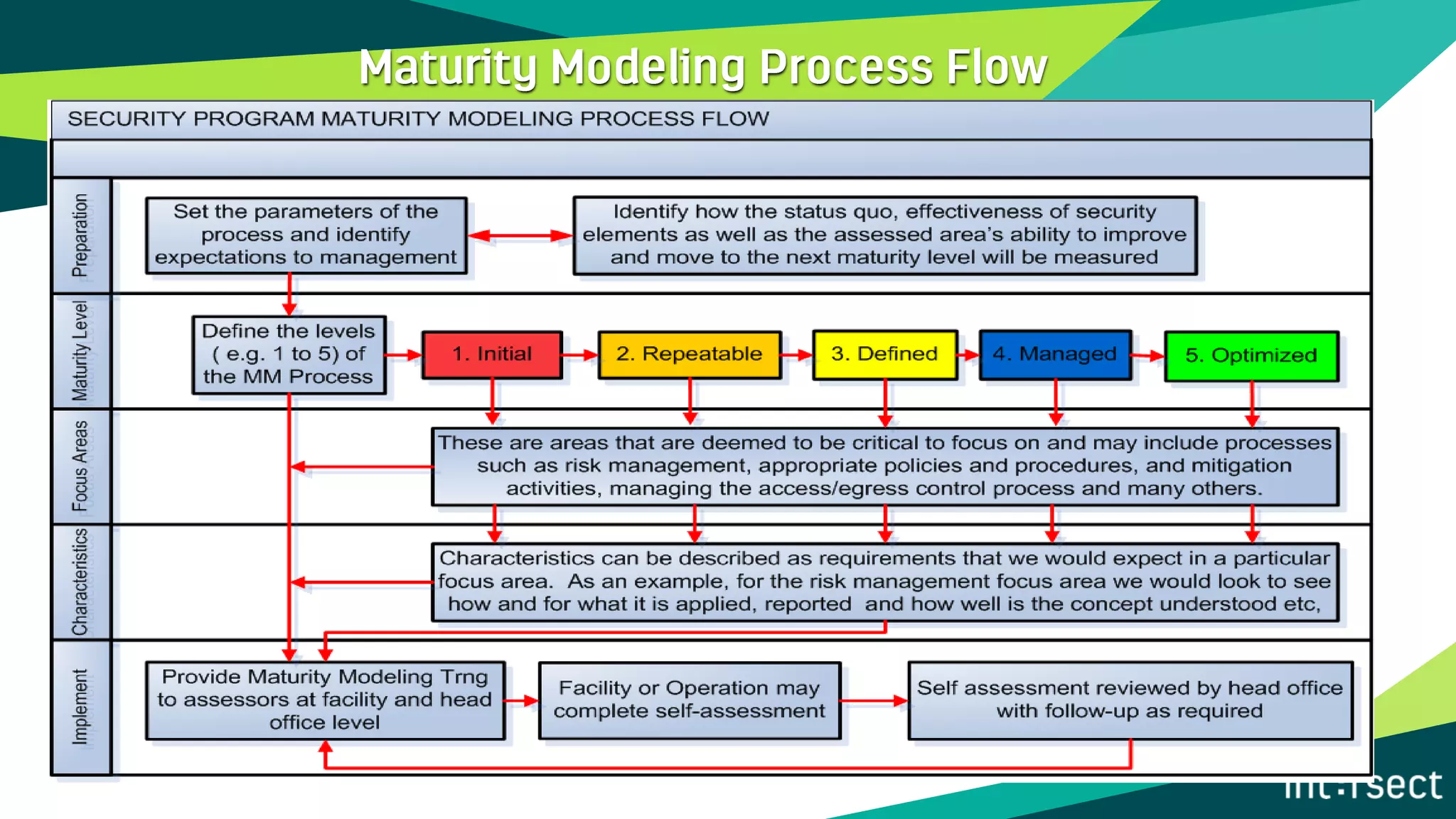
The document discusses Enterprise Security Risk Management (ESRM) as a holistic approach to managing security threats within an organization, emphasizing continuous improvement and leadership in the maturity assessment process. It outlines key objectives for learning and development in organizations, focusing on developing technical skills and supporting employee career growth while also measuring the impact of training on business outcomes. Additionally, it addresses risk-based decision-making and the importance of aligning security initiatives with organizational goals for effective risk management.