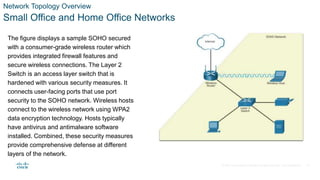
The document provides an overview of network security topics including the current security landscape, network topologies, and objectives. It describes how networks are routinely under attack and reasons it is important to secure networks. It also outlines how different network types like campus area networks, small office/home networks, wide area networks, and data centers need security measures at various layers to protect the network, data, and resources. Physical security for data centers is also highlighted as critical to protect equipment and sensitive data stored in these facilities.