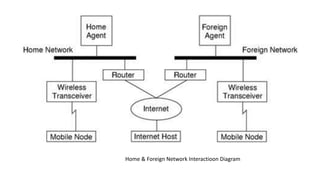
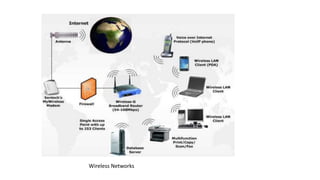
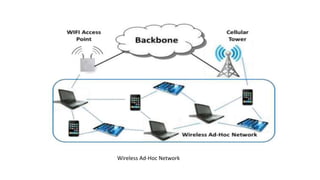
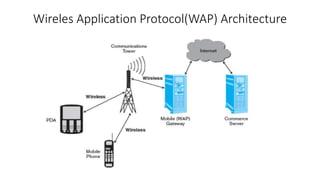
Mobile computing allows wireless transmission of data, video, and audio through portable devices. It enables portable connectivity through computer networks. Key challenges include limited resources, dynamic network environments, and security issues when transmitting over radio interfaces.
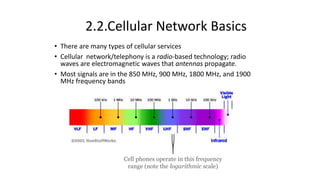
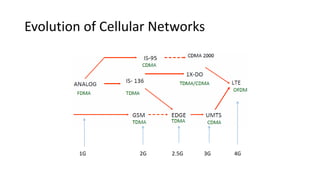
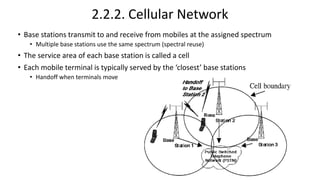
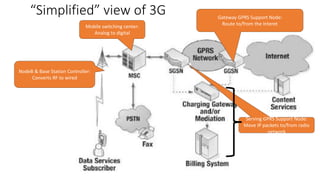
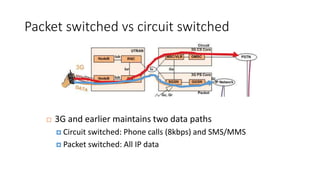
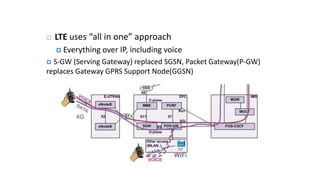
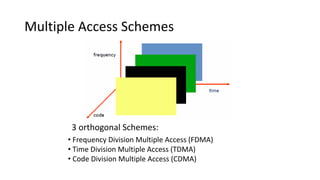
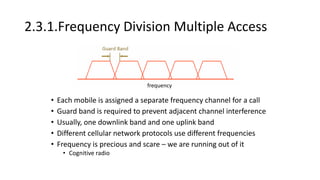
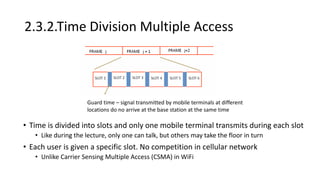
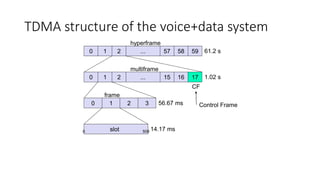
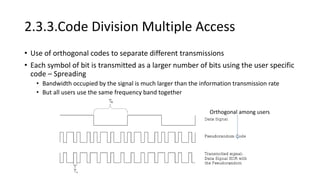
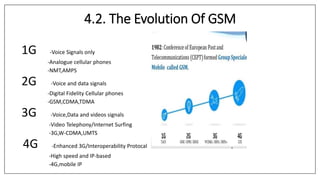
Various wireless networks exist for mobile computing including personal area networks, Wi-Fi, and cellular networks. Cellular networks have evolved through generations from analog to digital transmission and now support high-speed data through LTE. They address the multiple access problem of many devices transmitting through the use of frequency division, time division, or code division multiple access schemes.