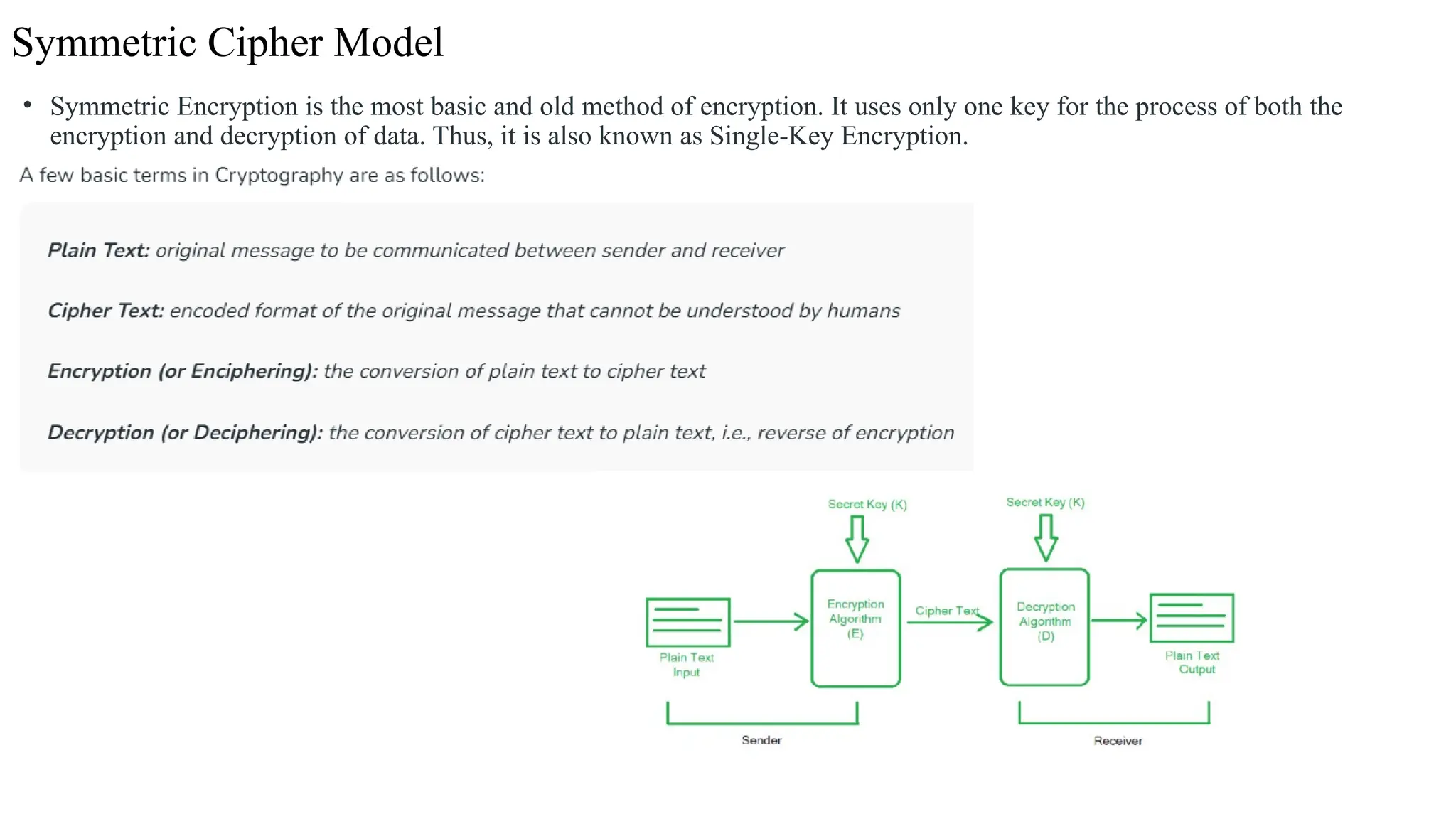
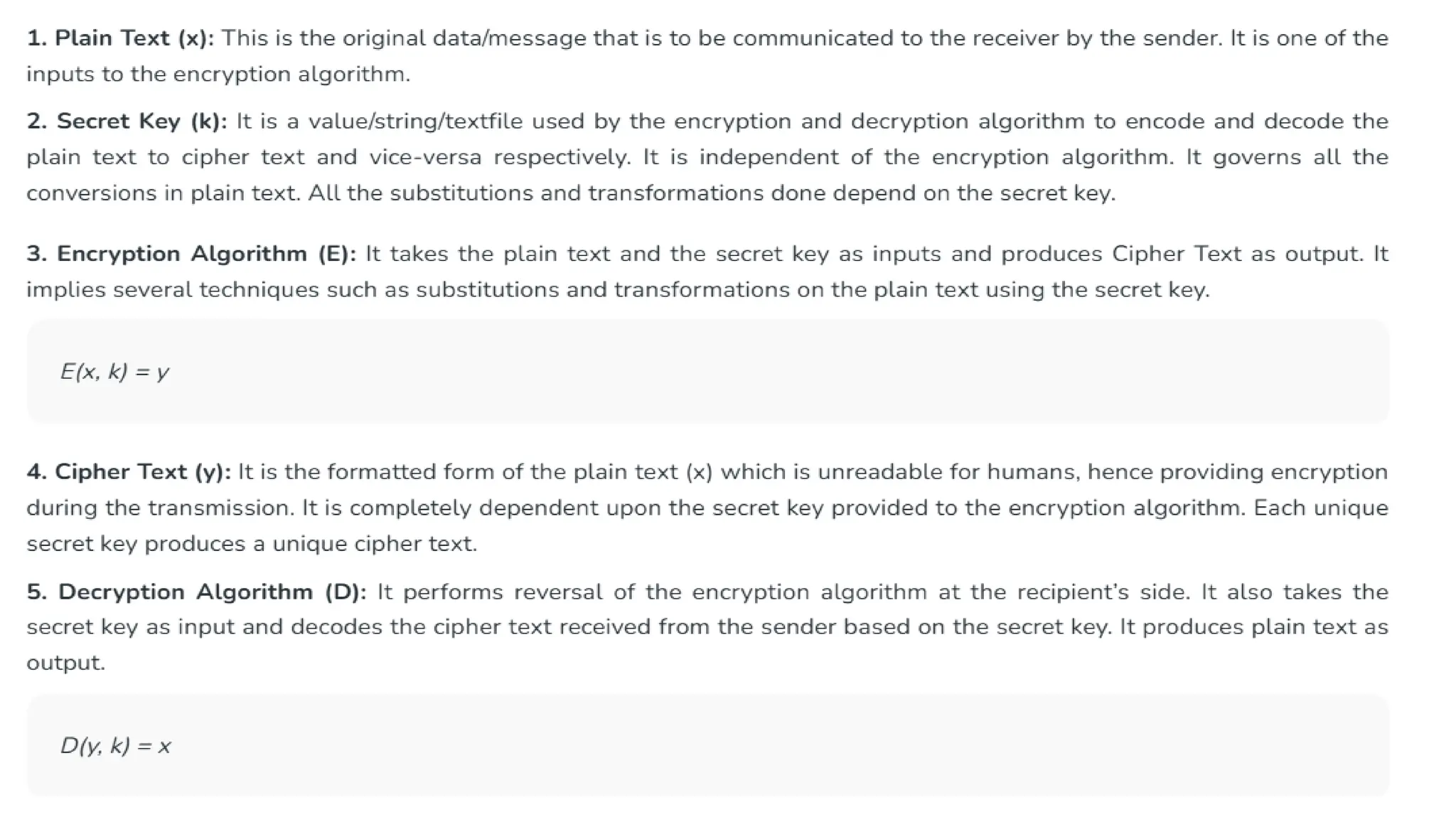
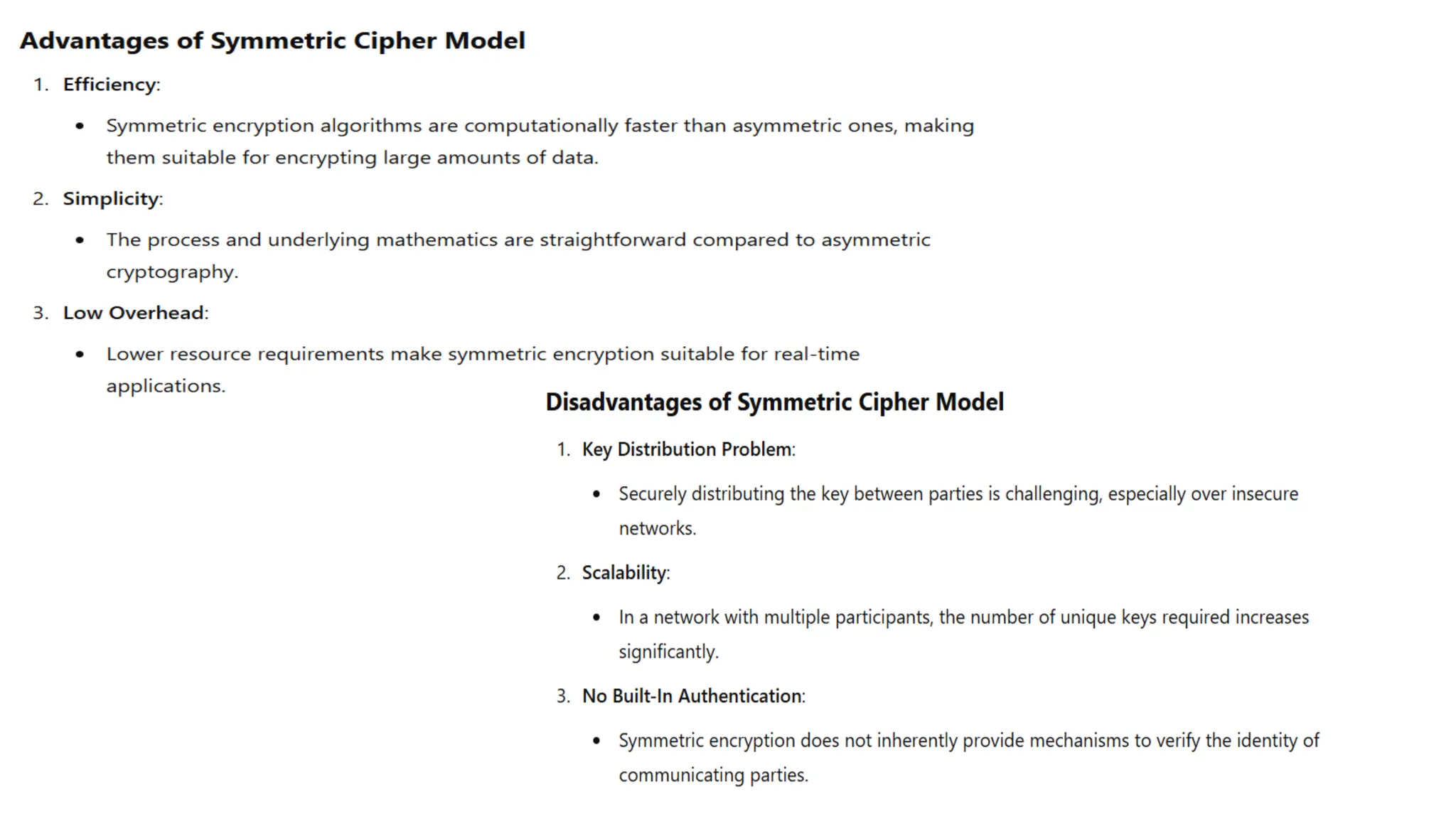
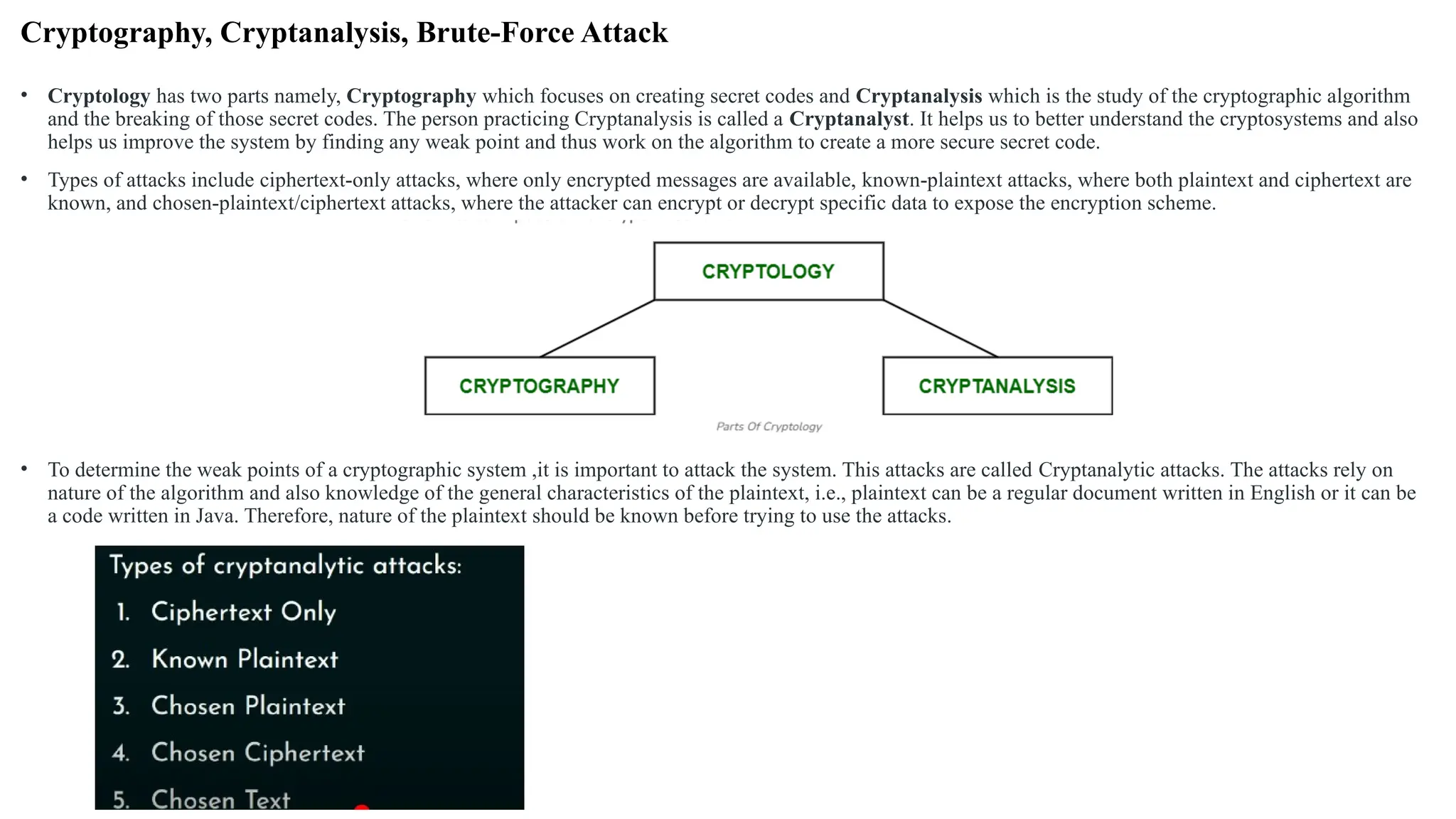
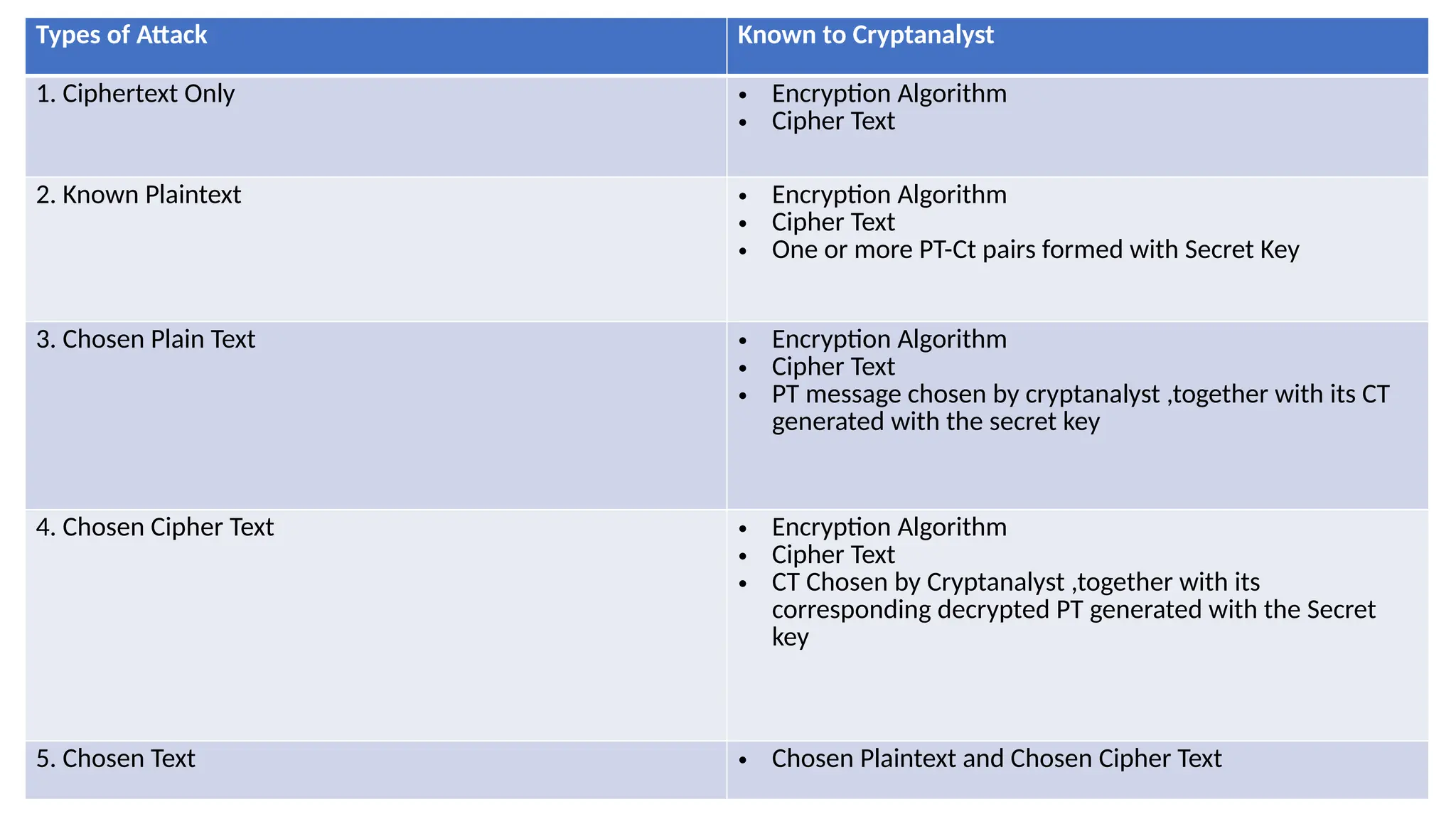
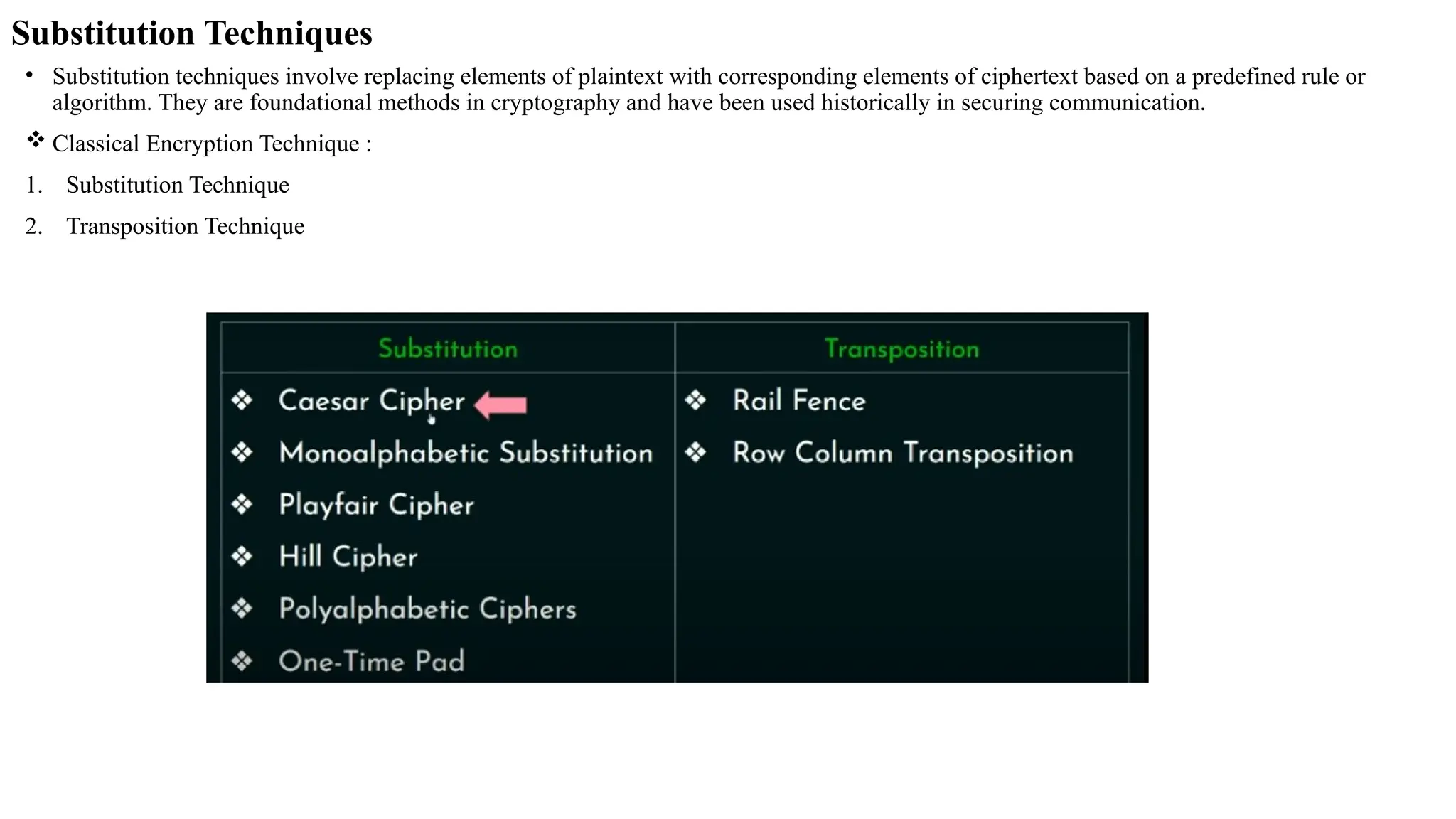
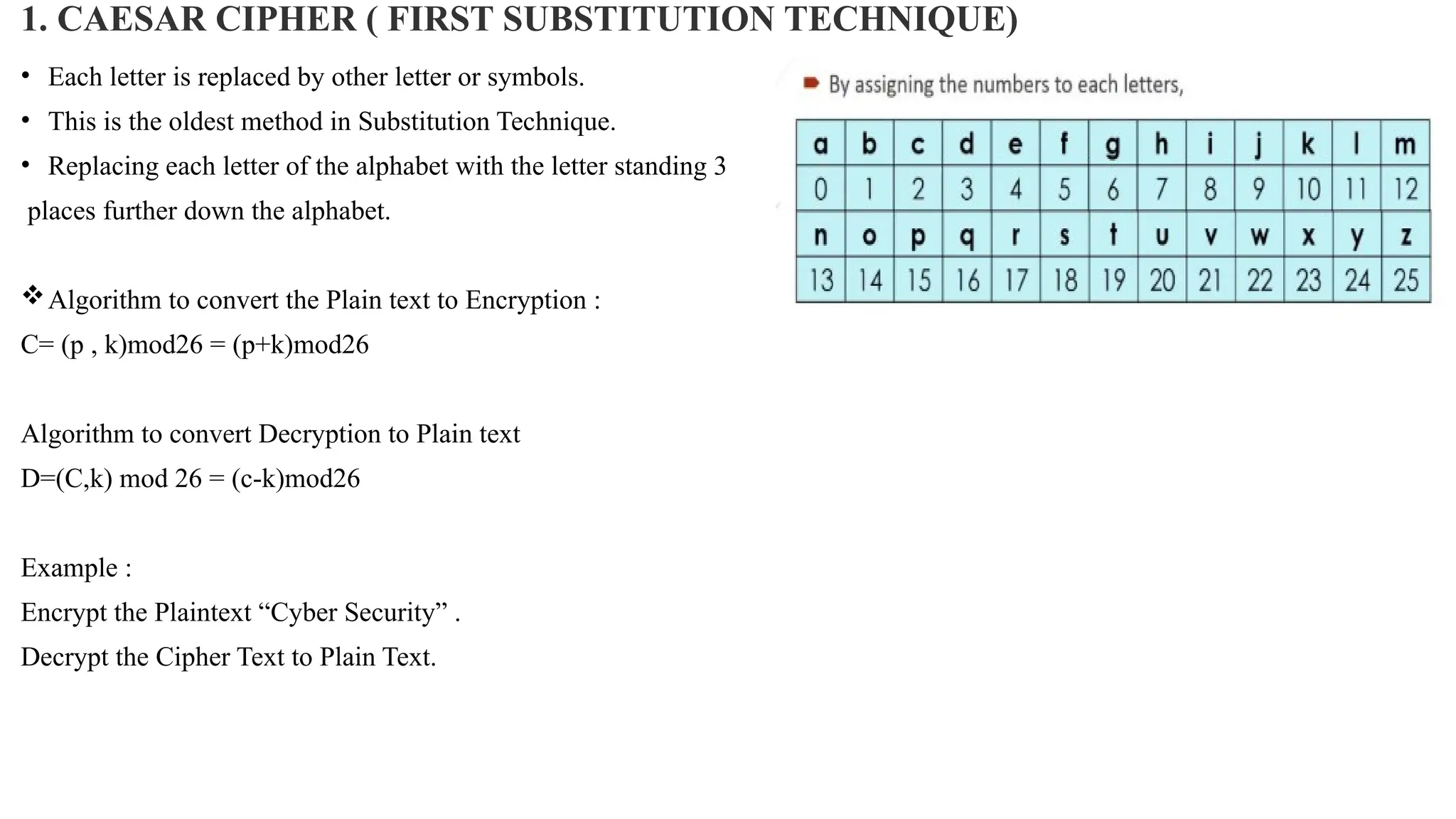
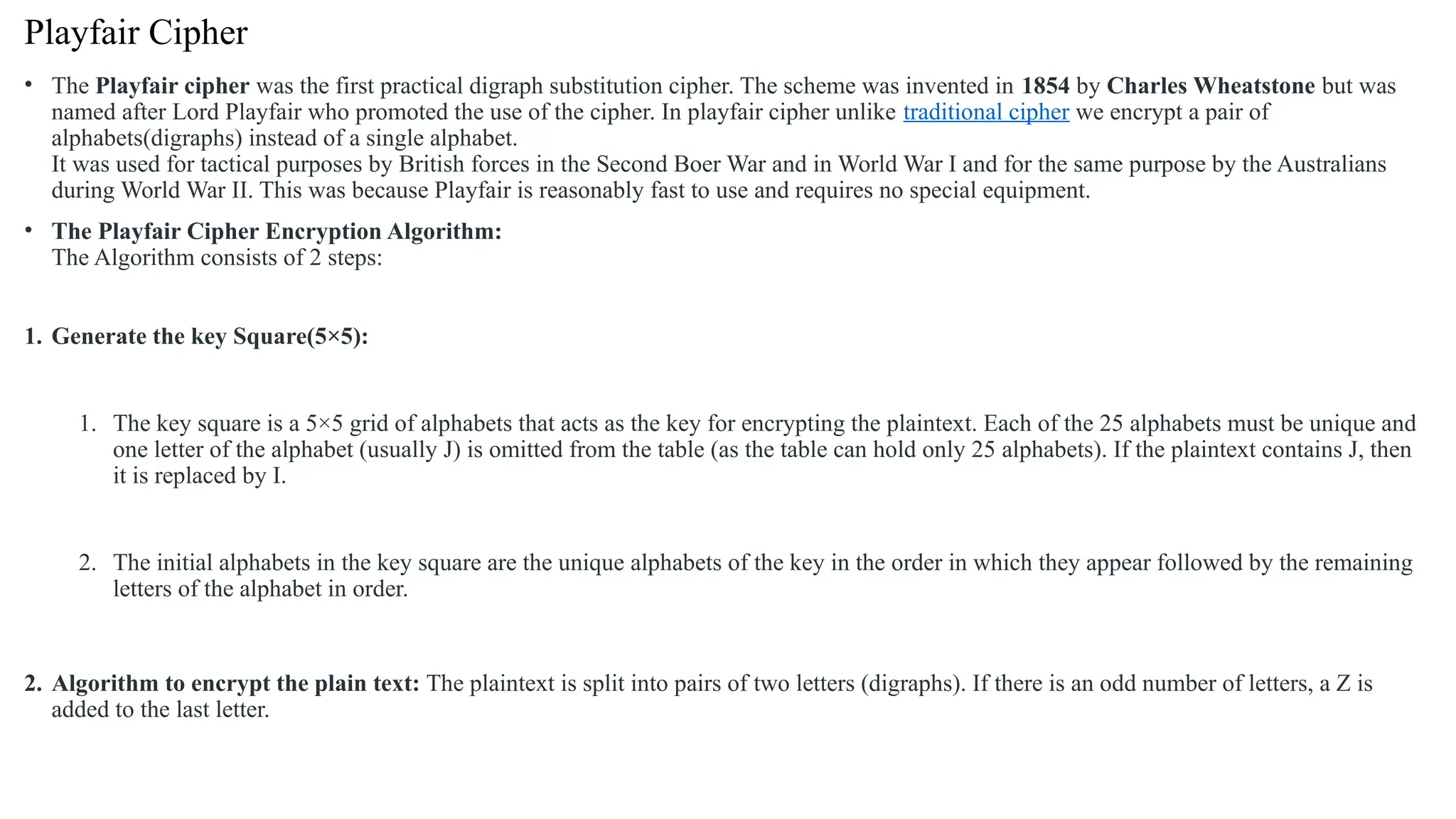
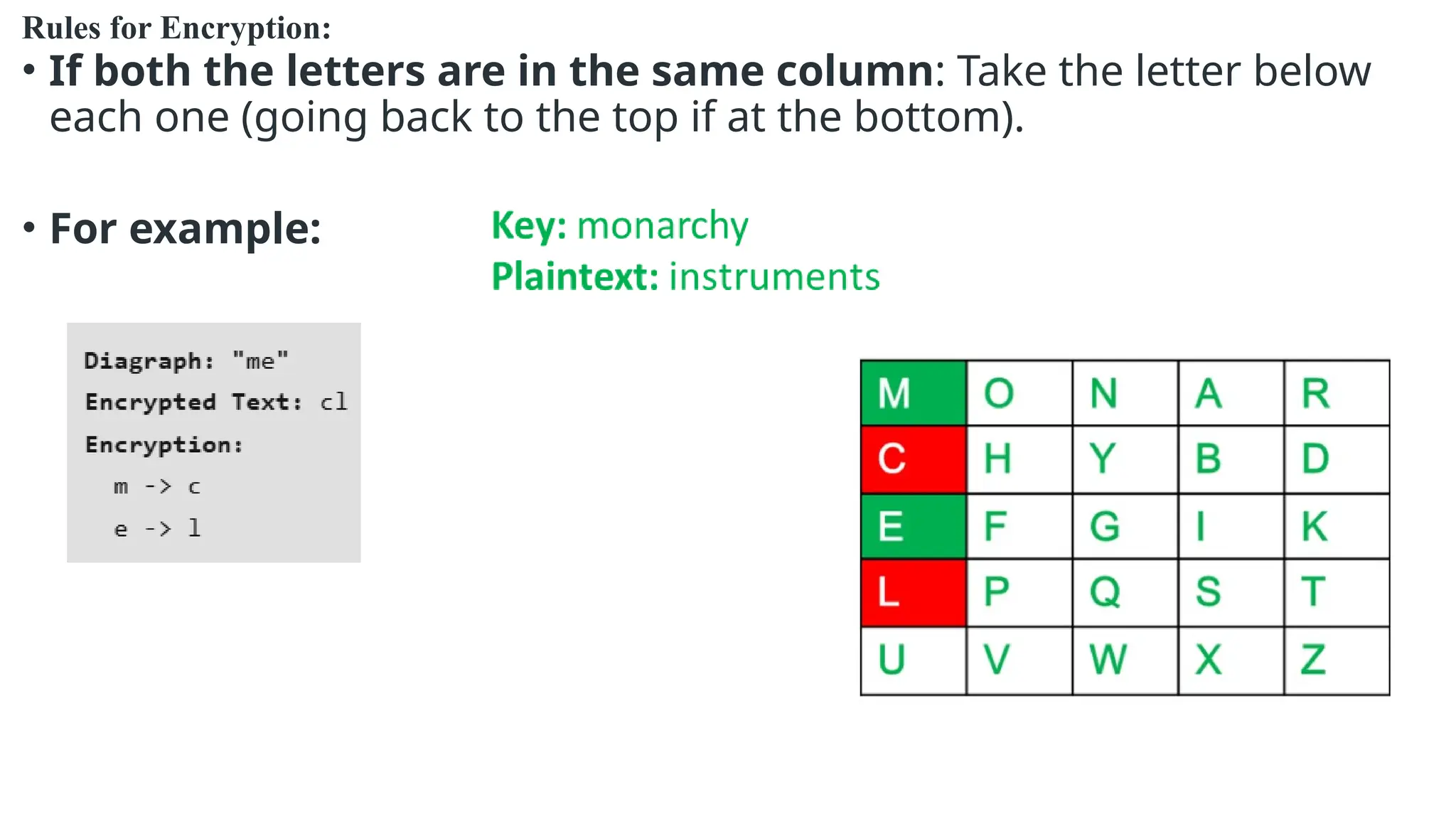
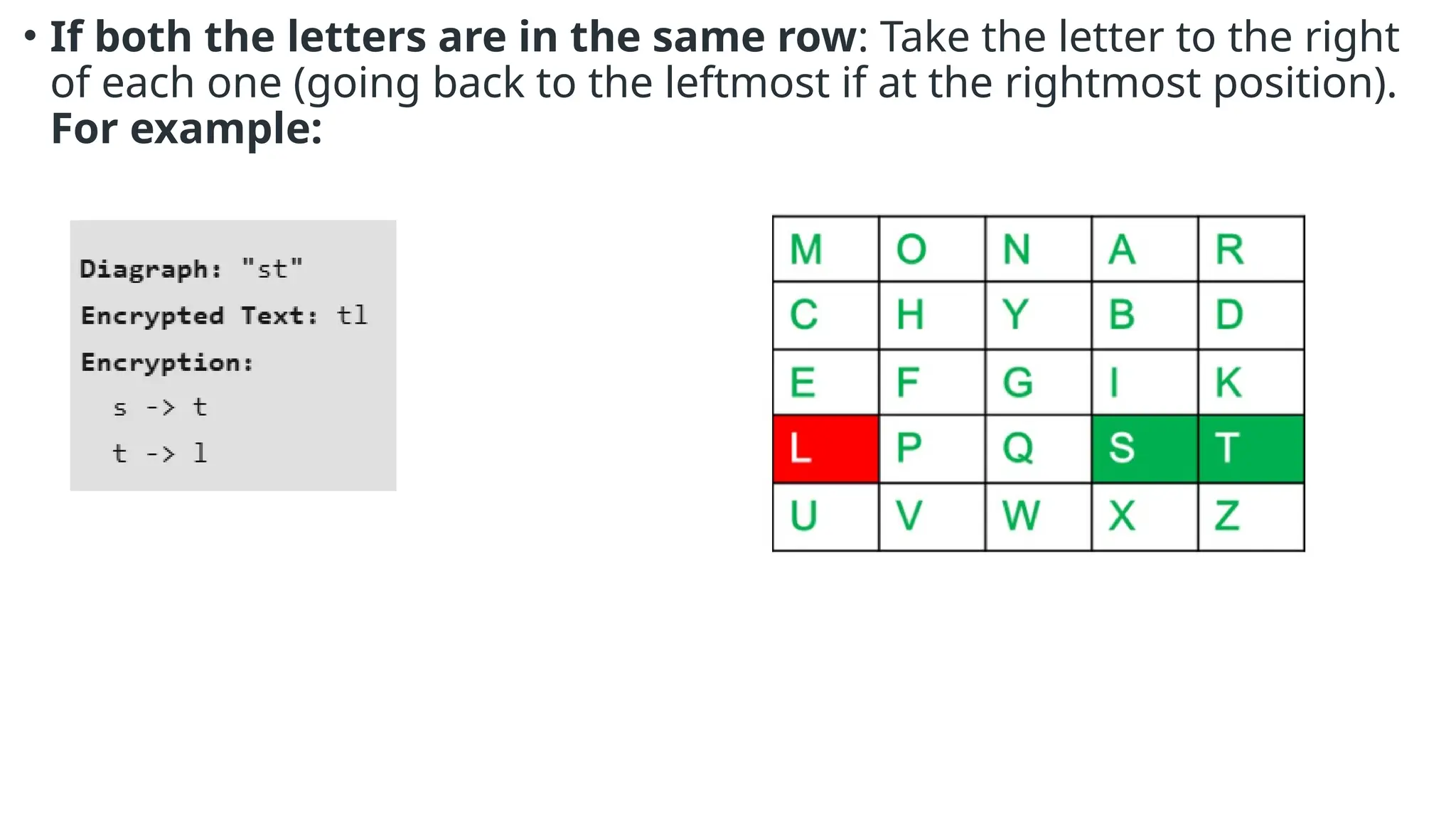
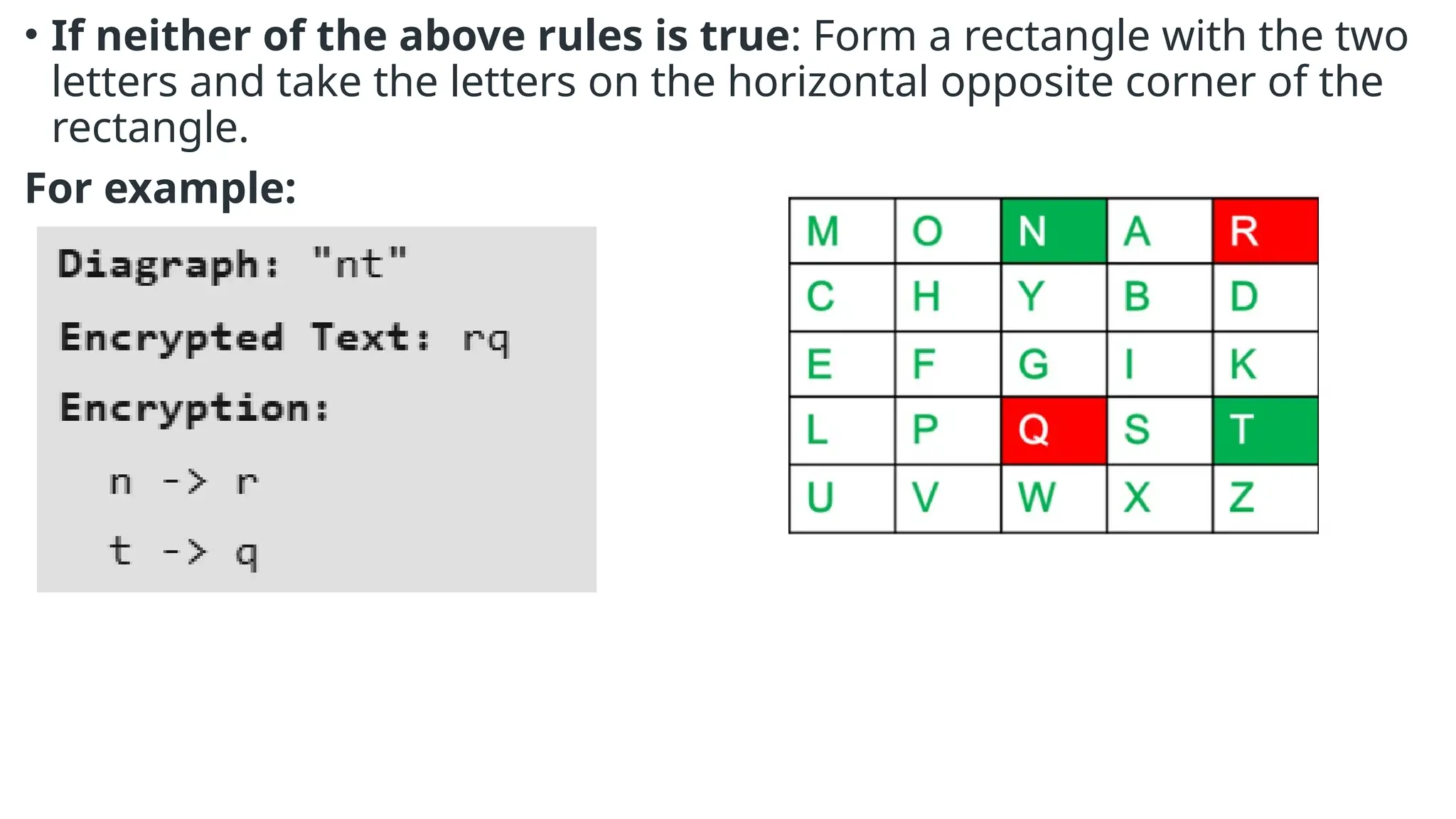
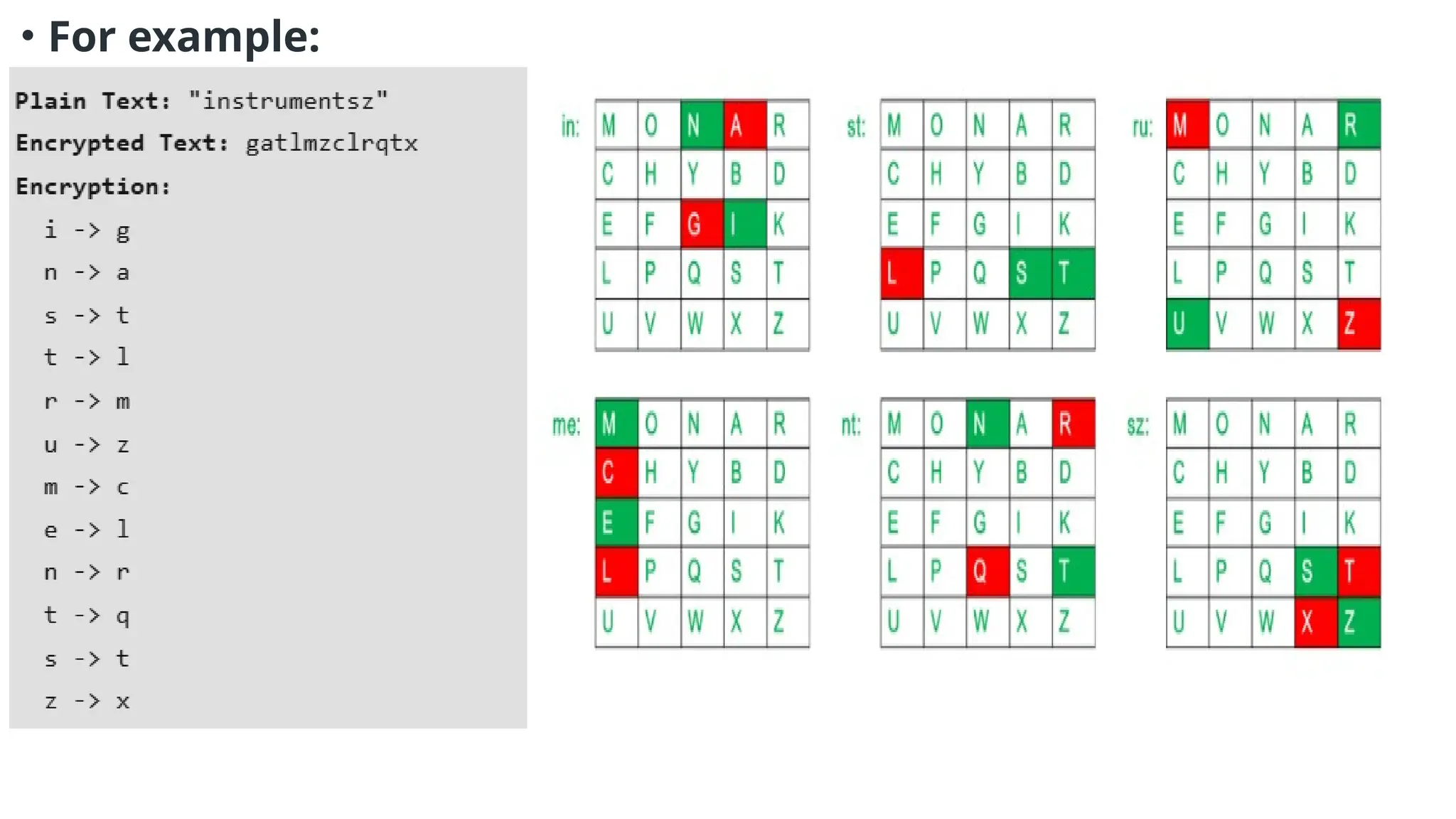
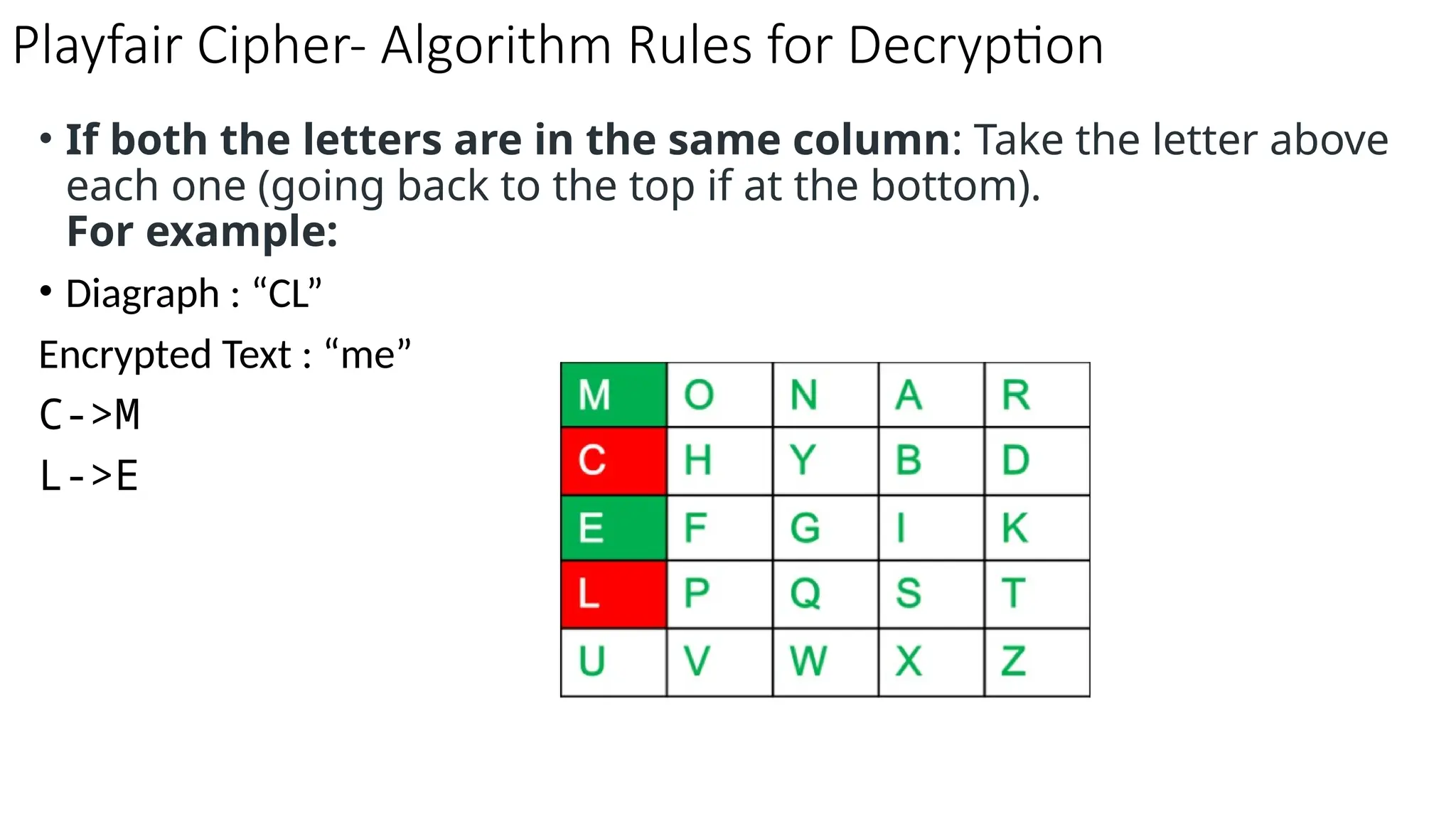
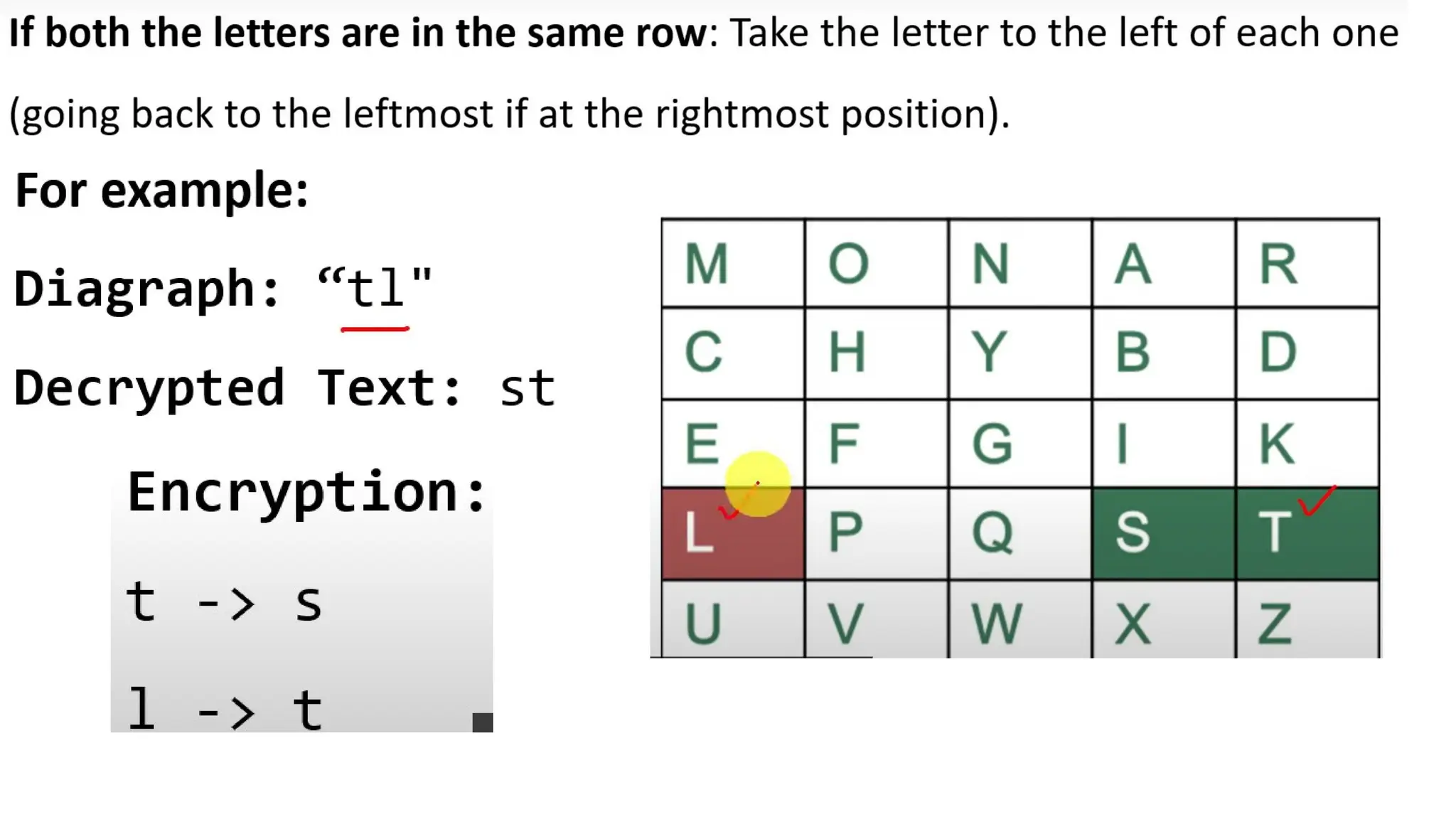
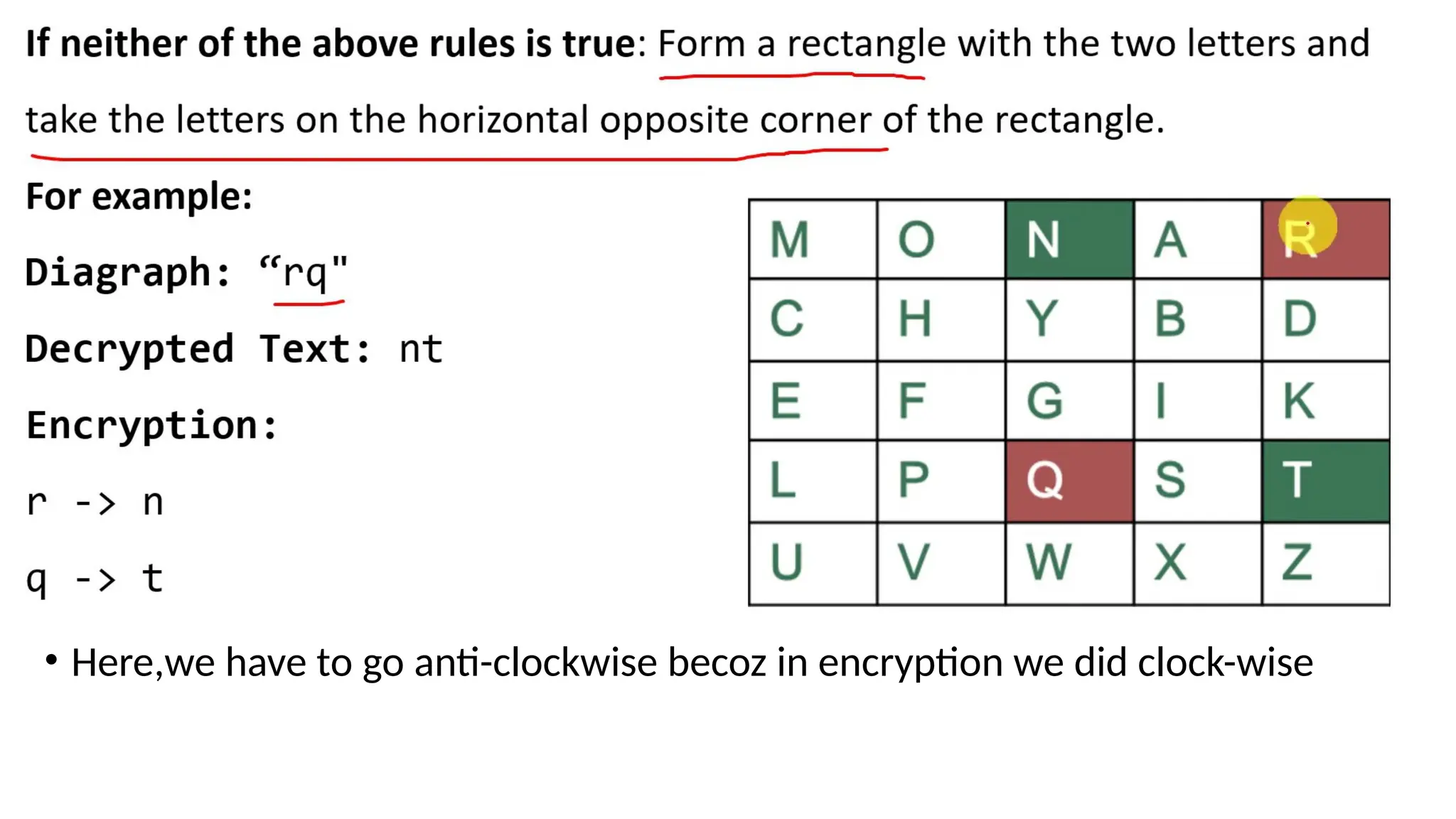
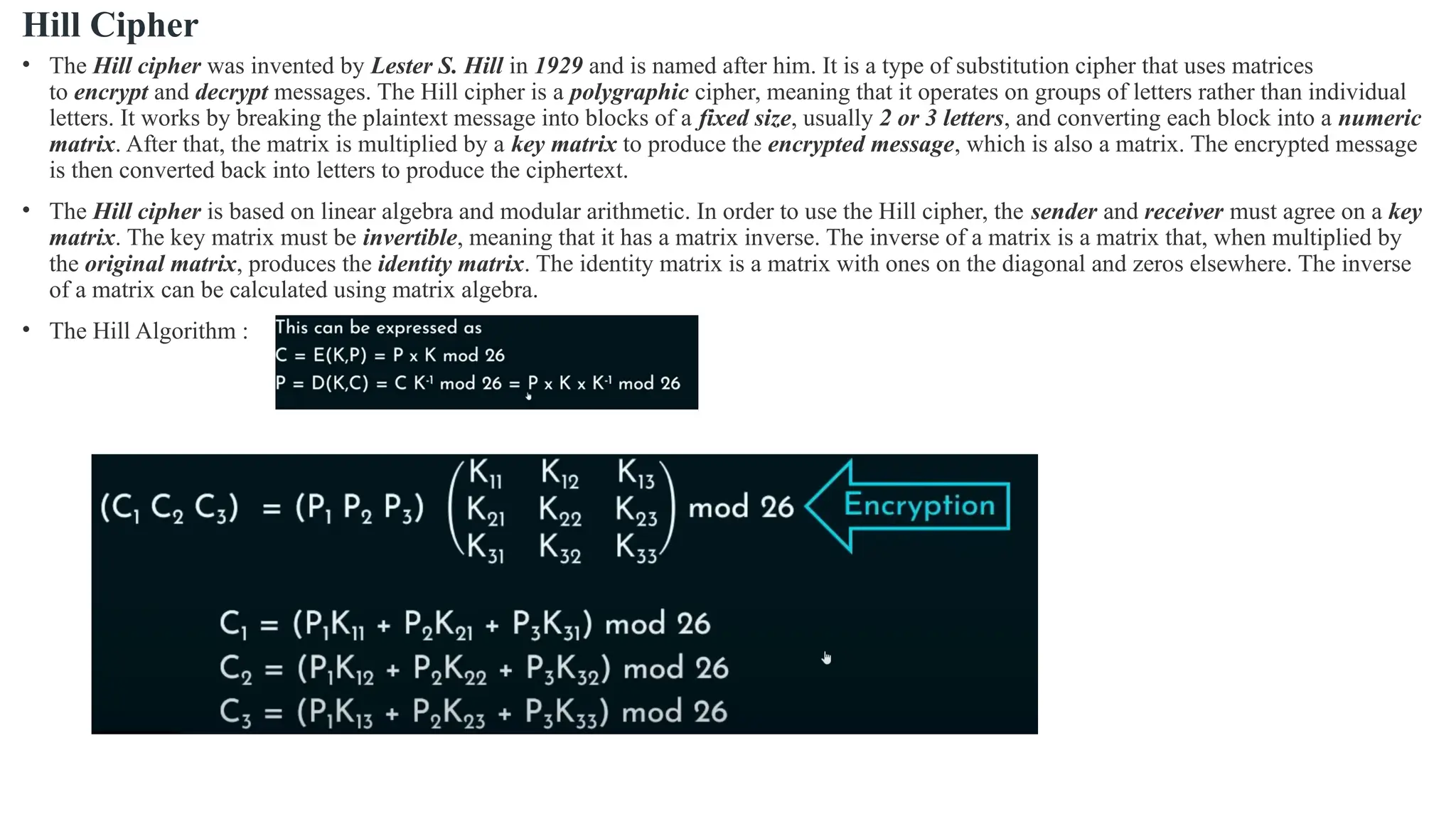
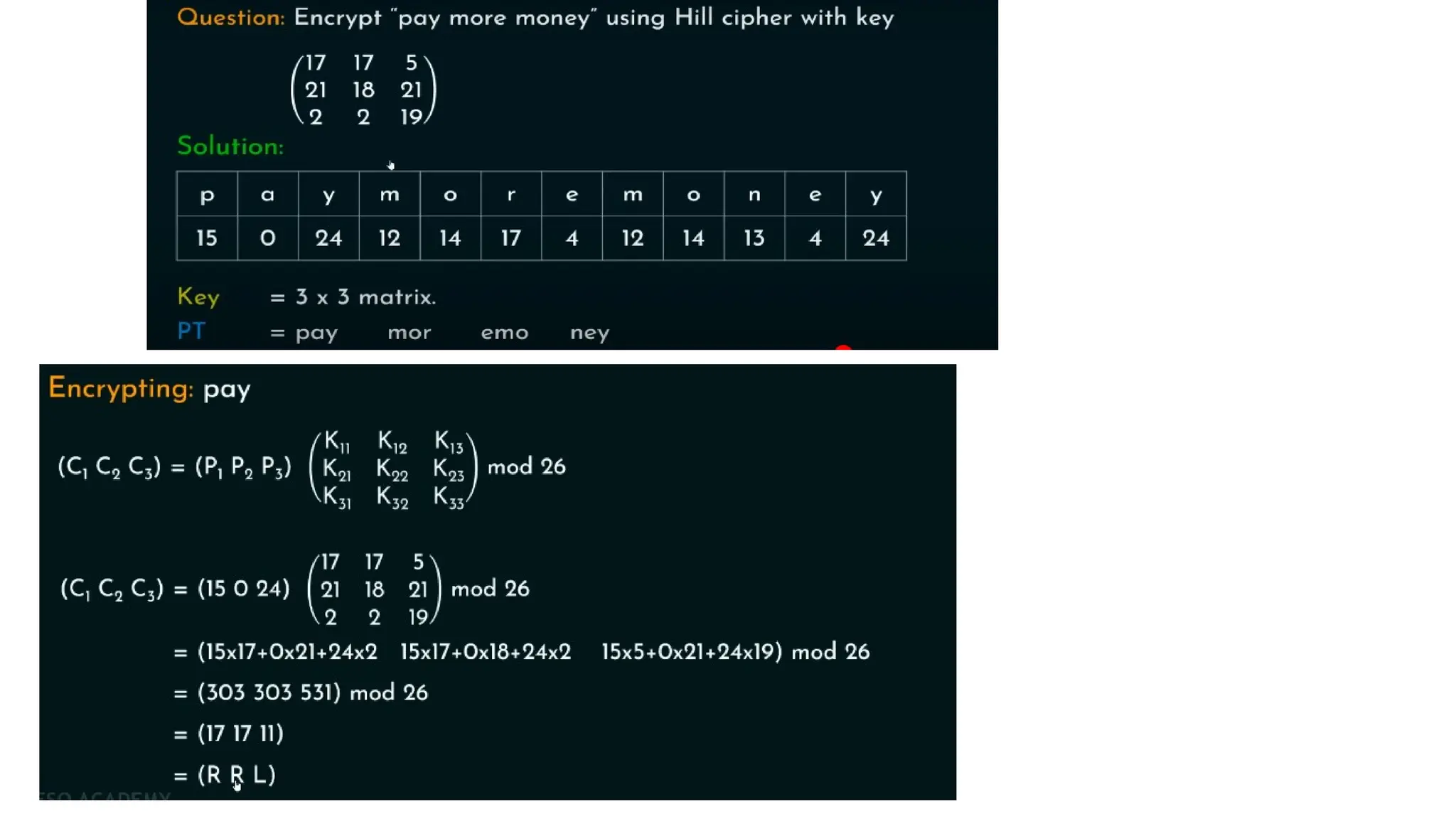
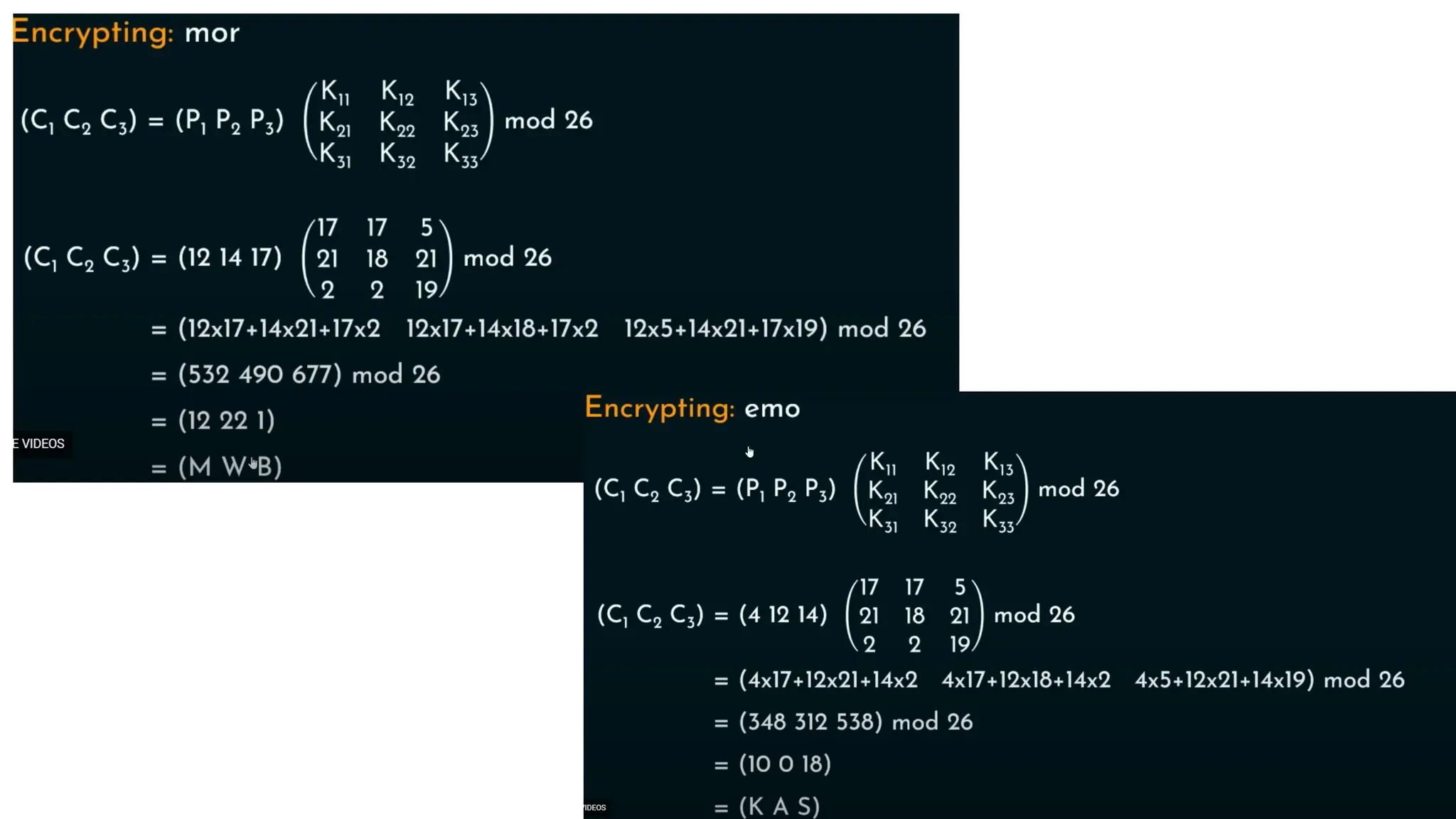
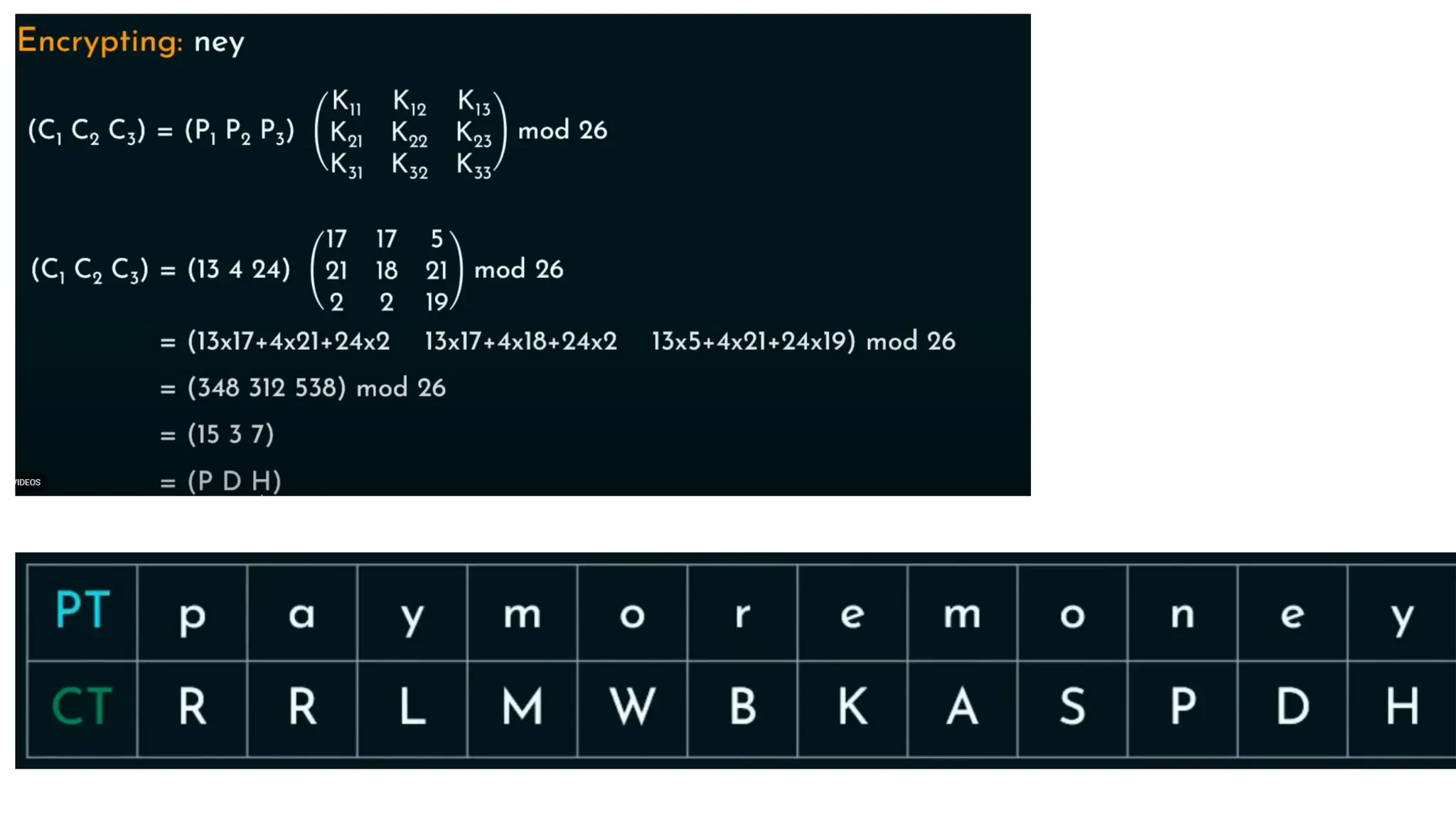
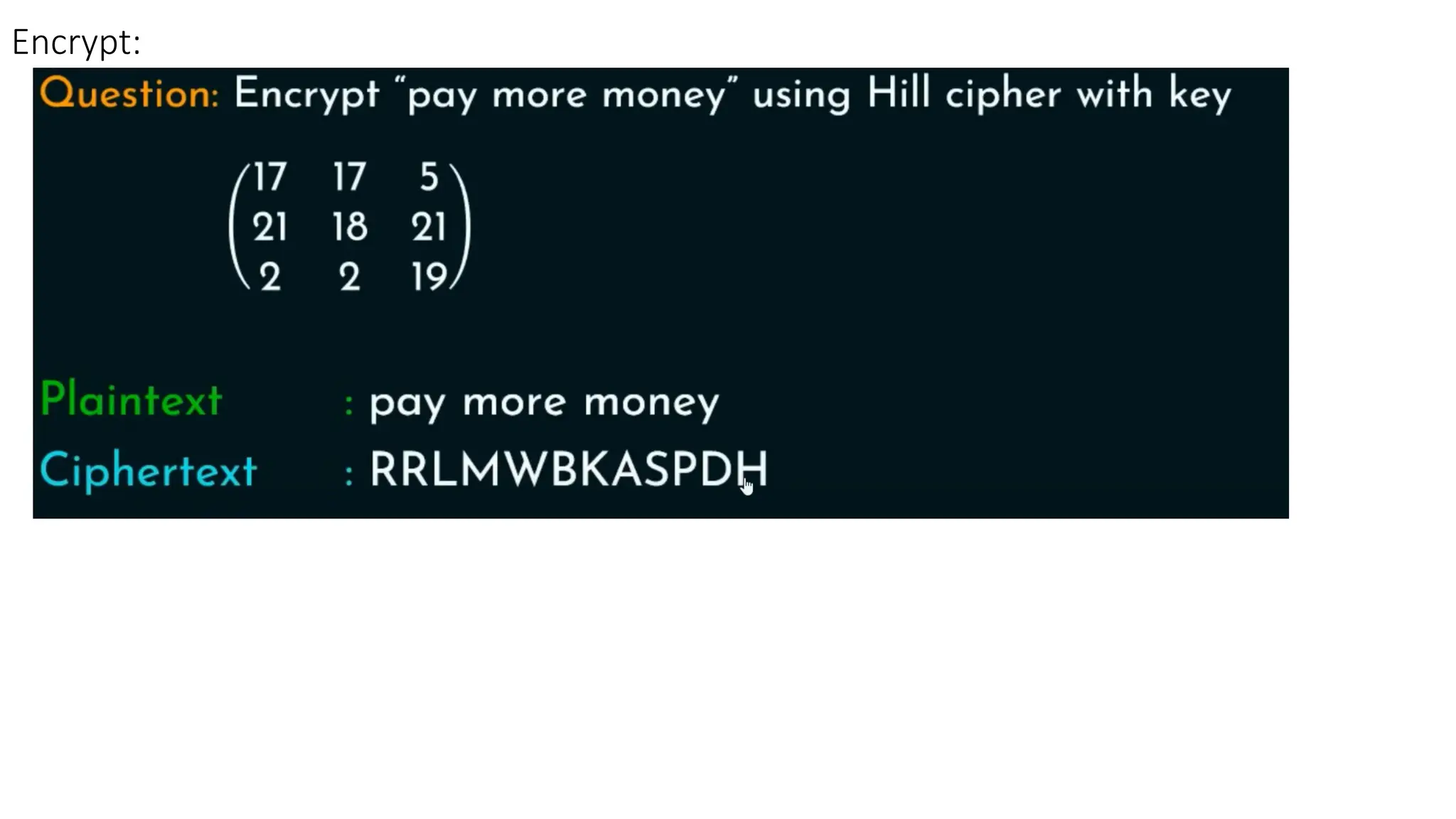
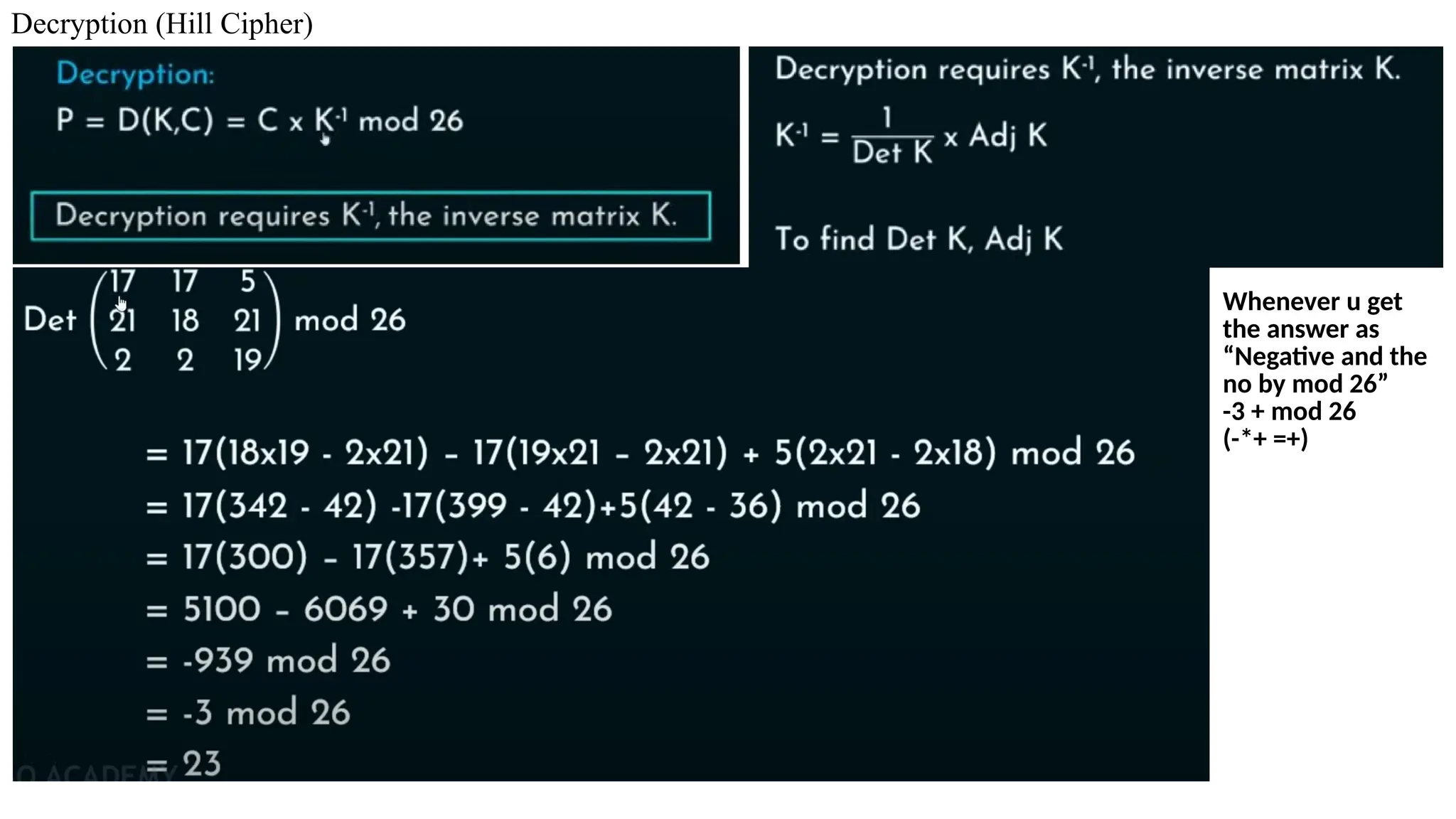
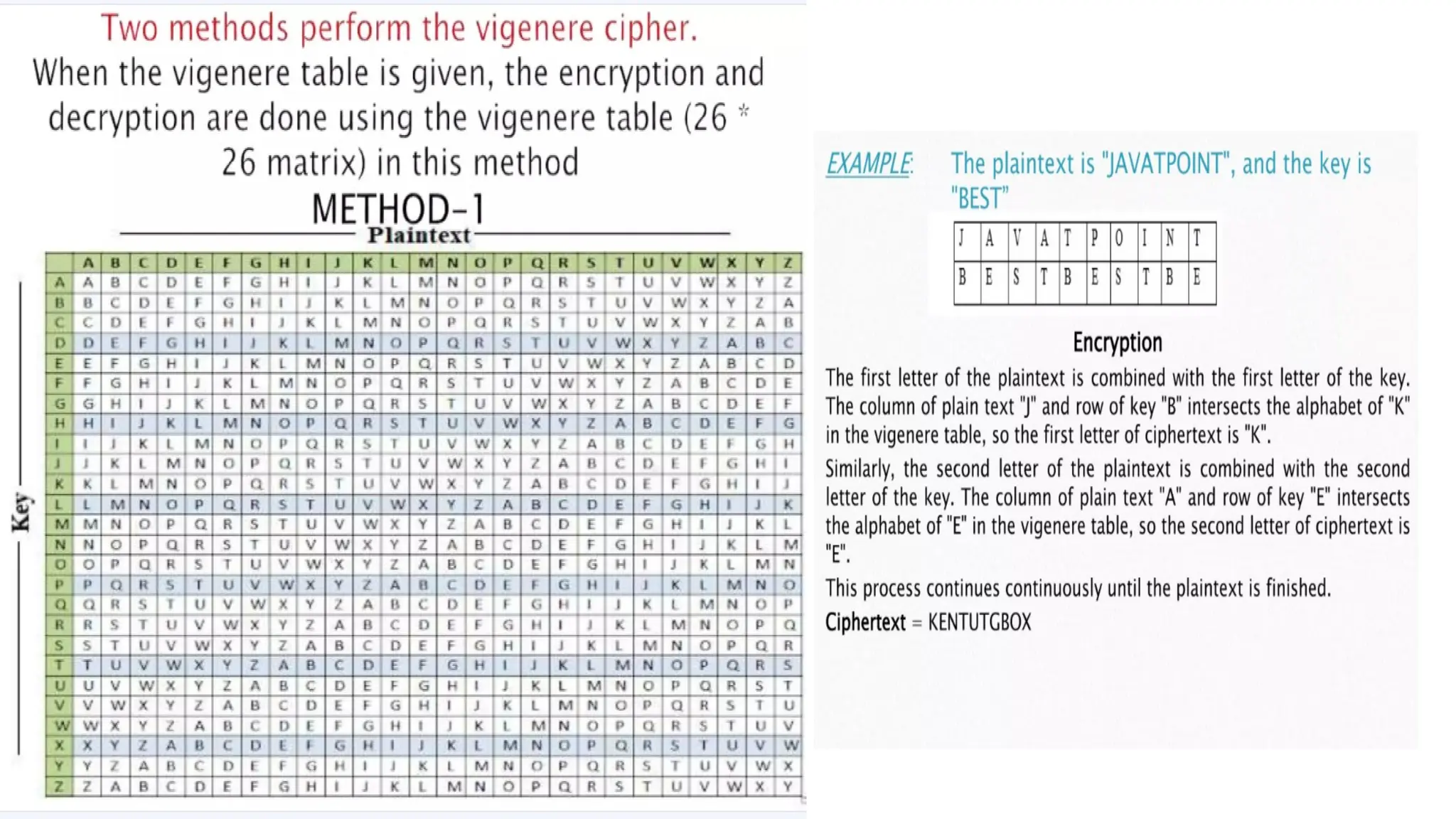
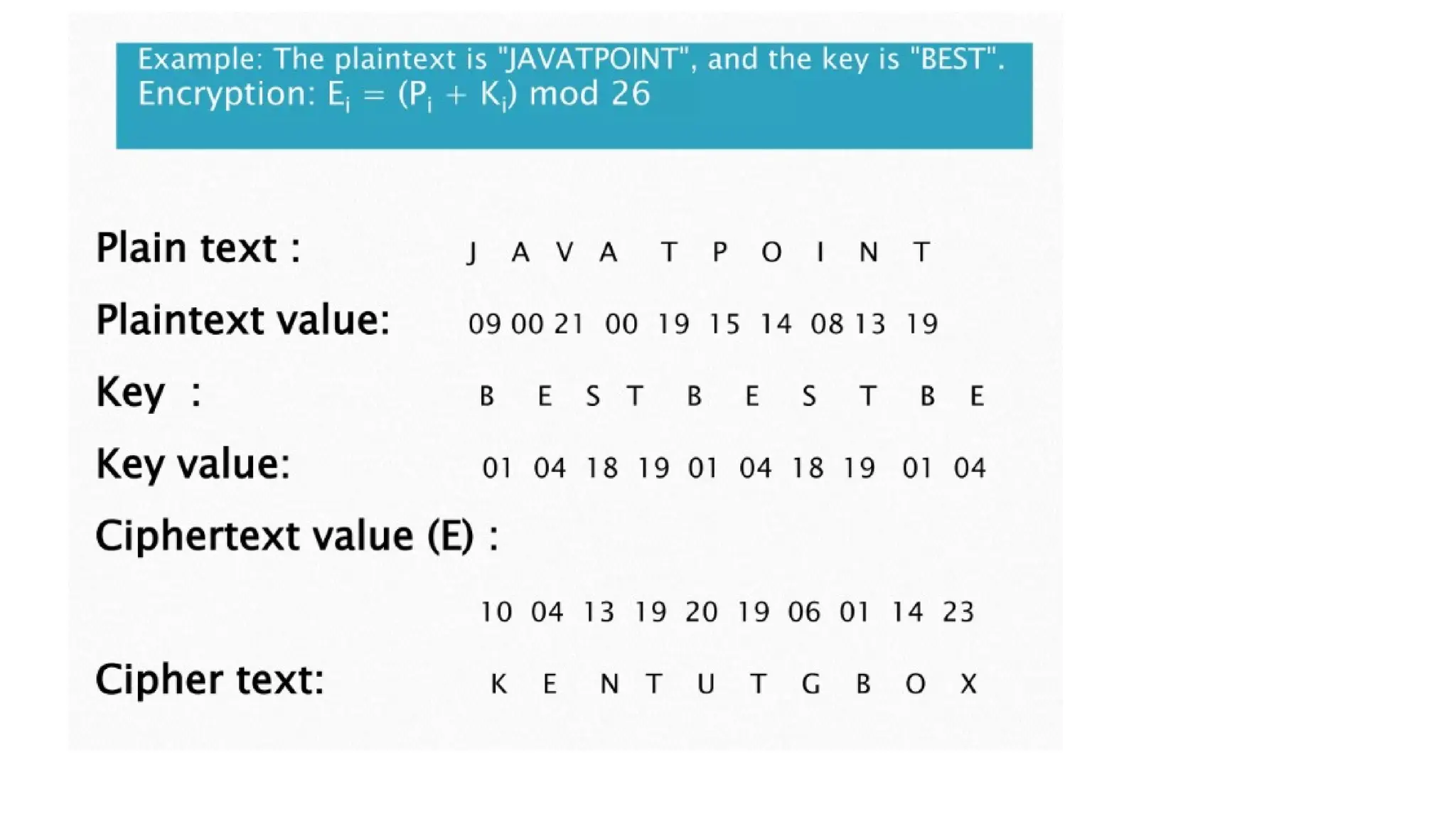
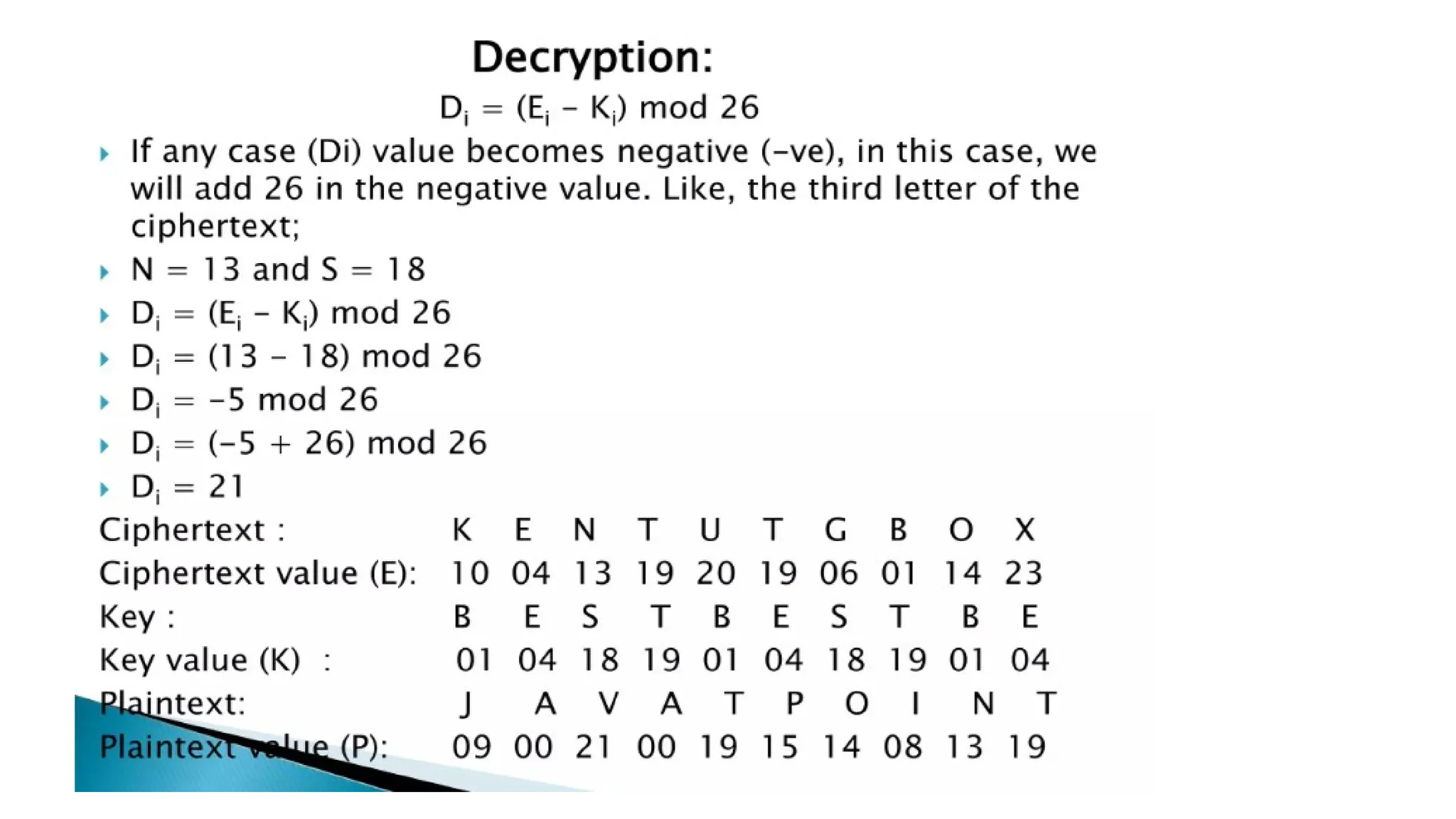
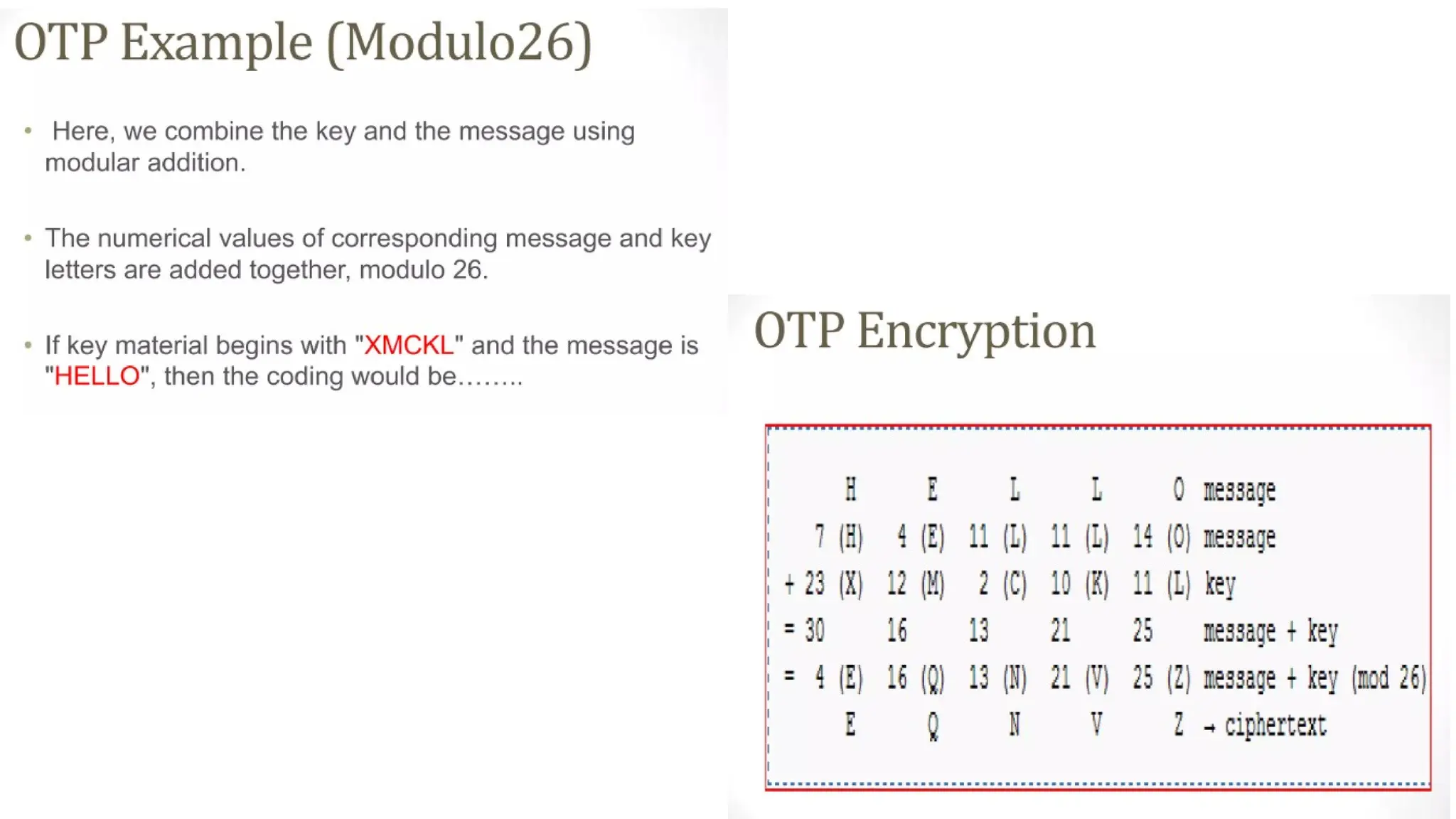
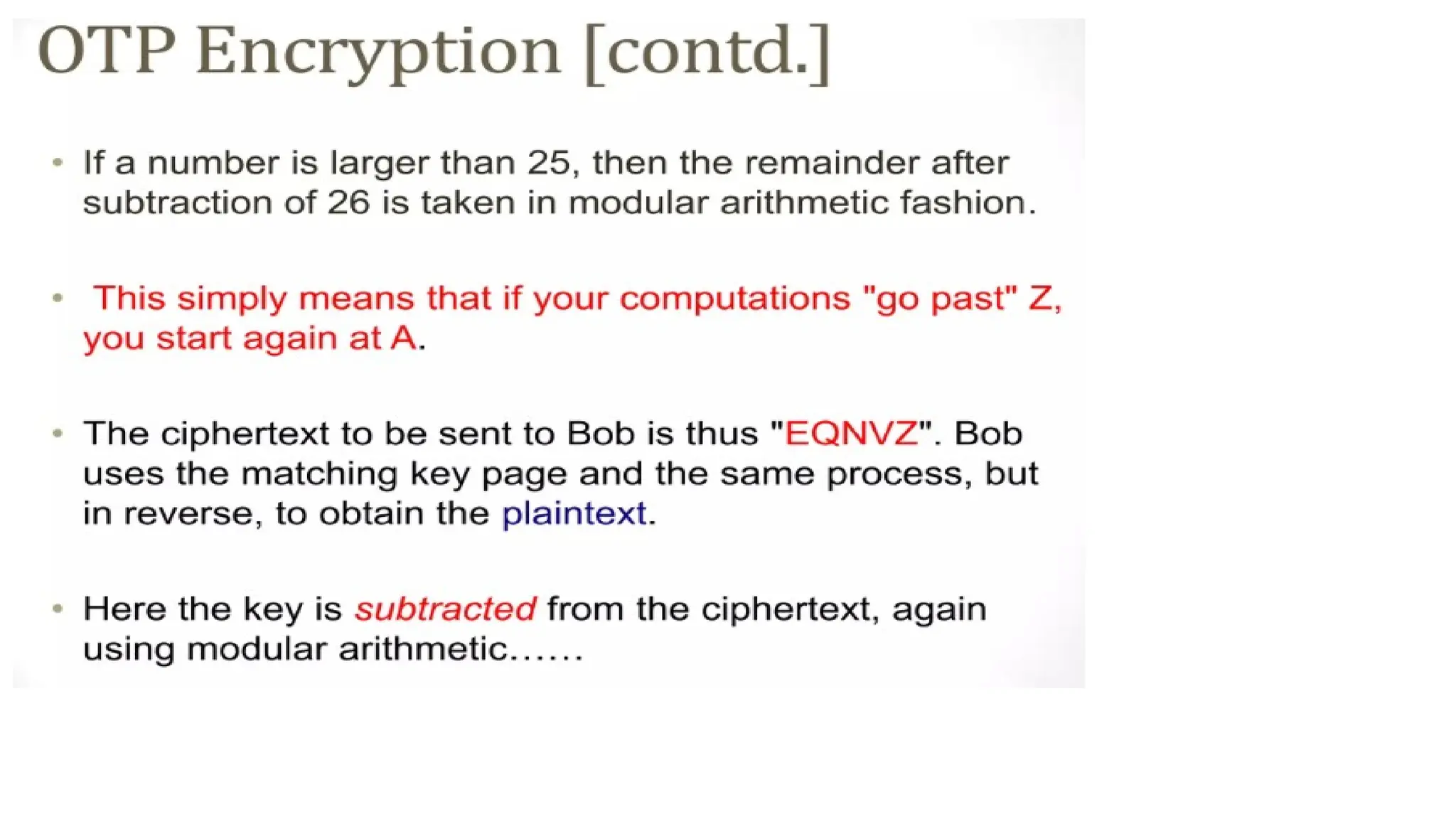
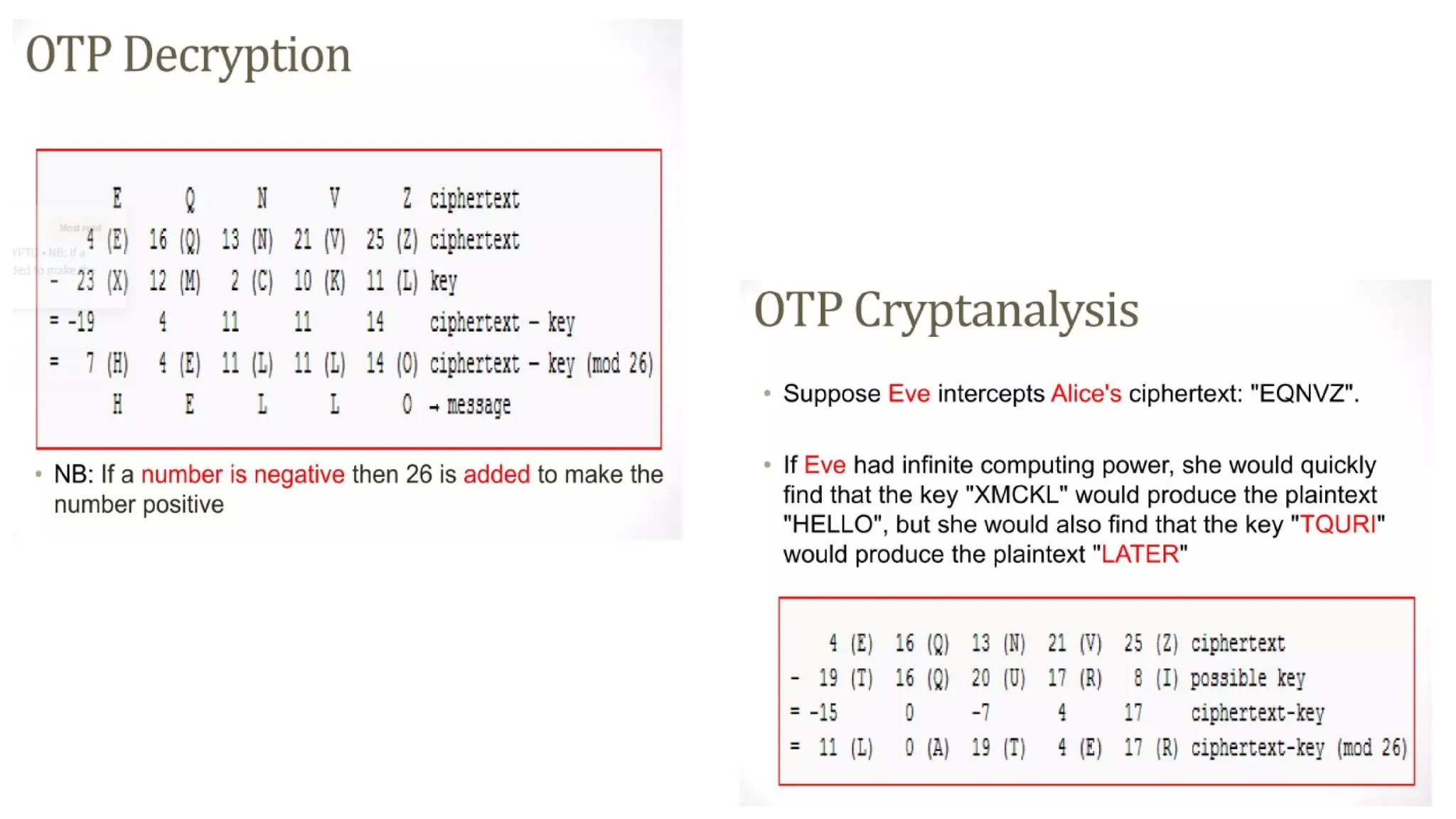
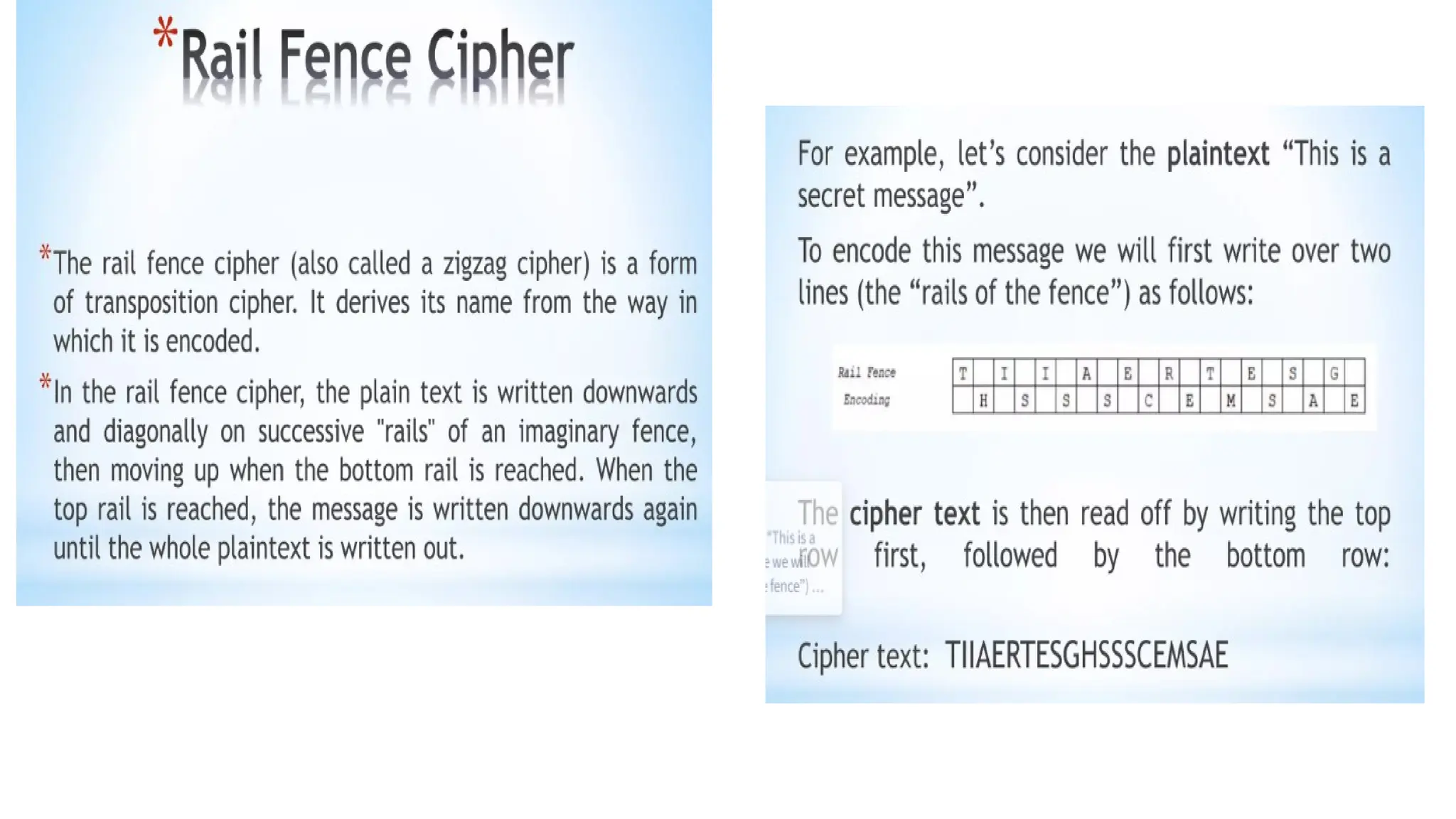
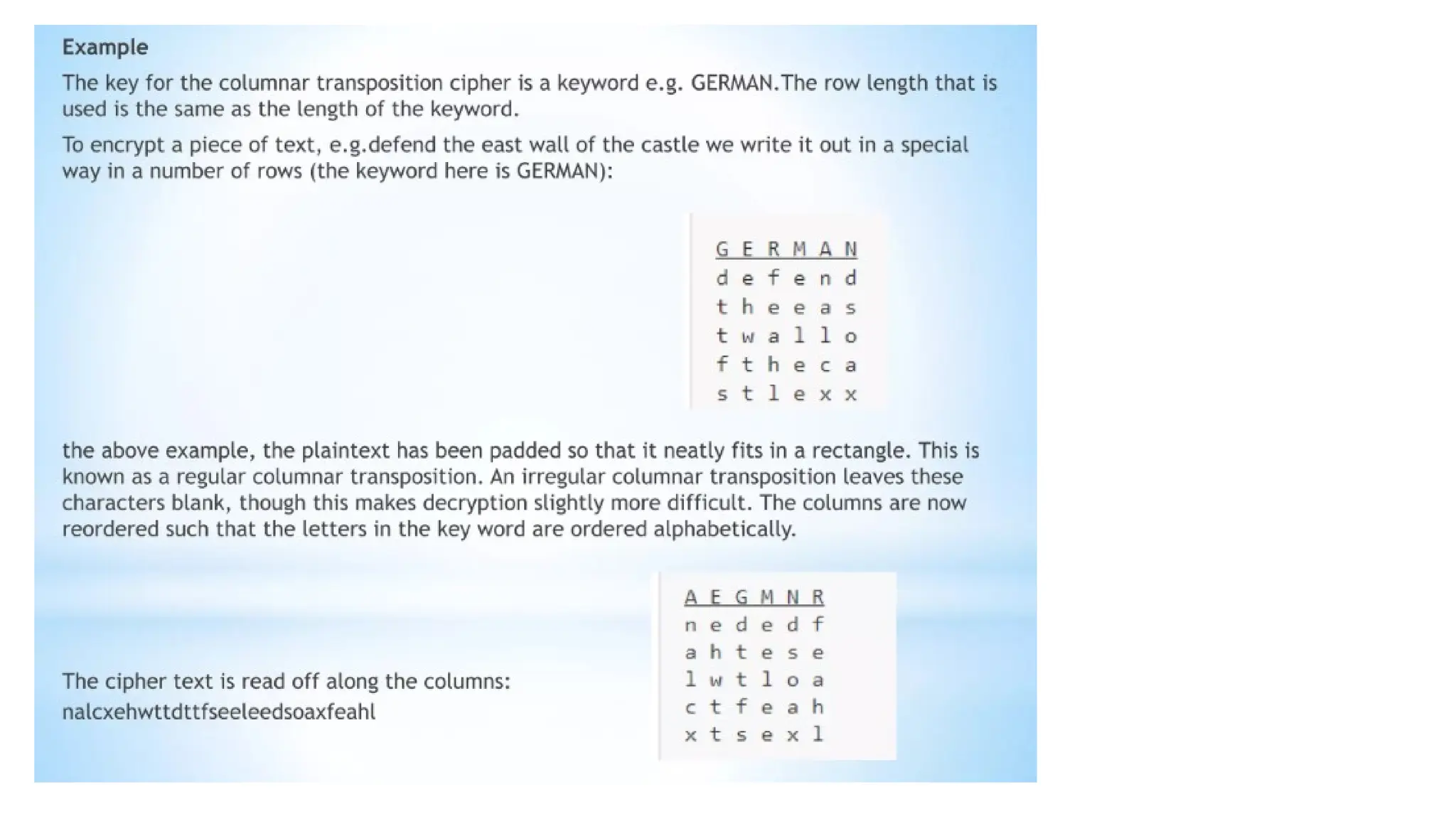
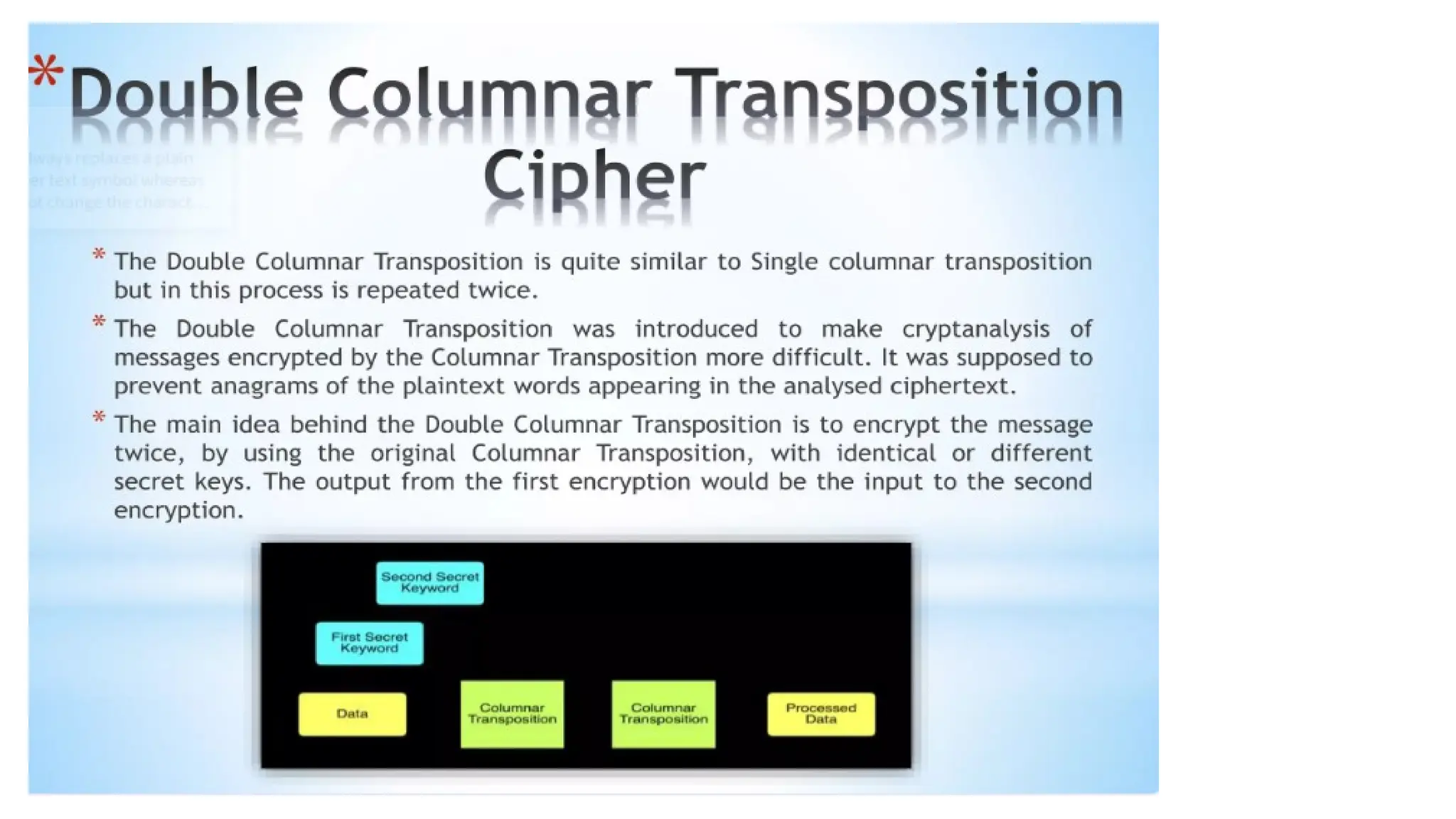
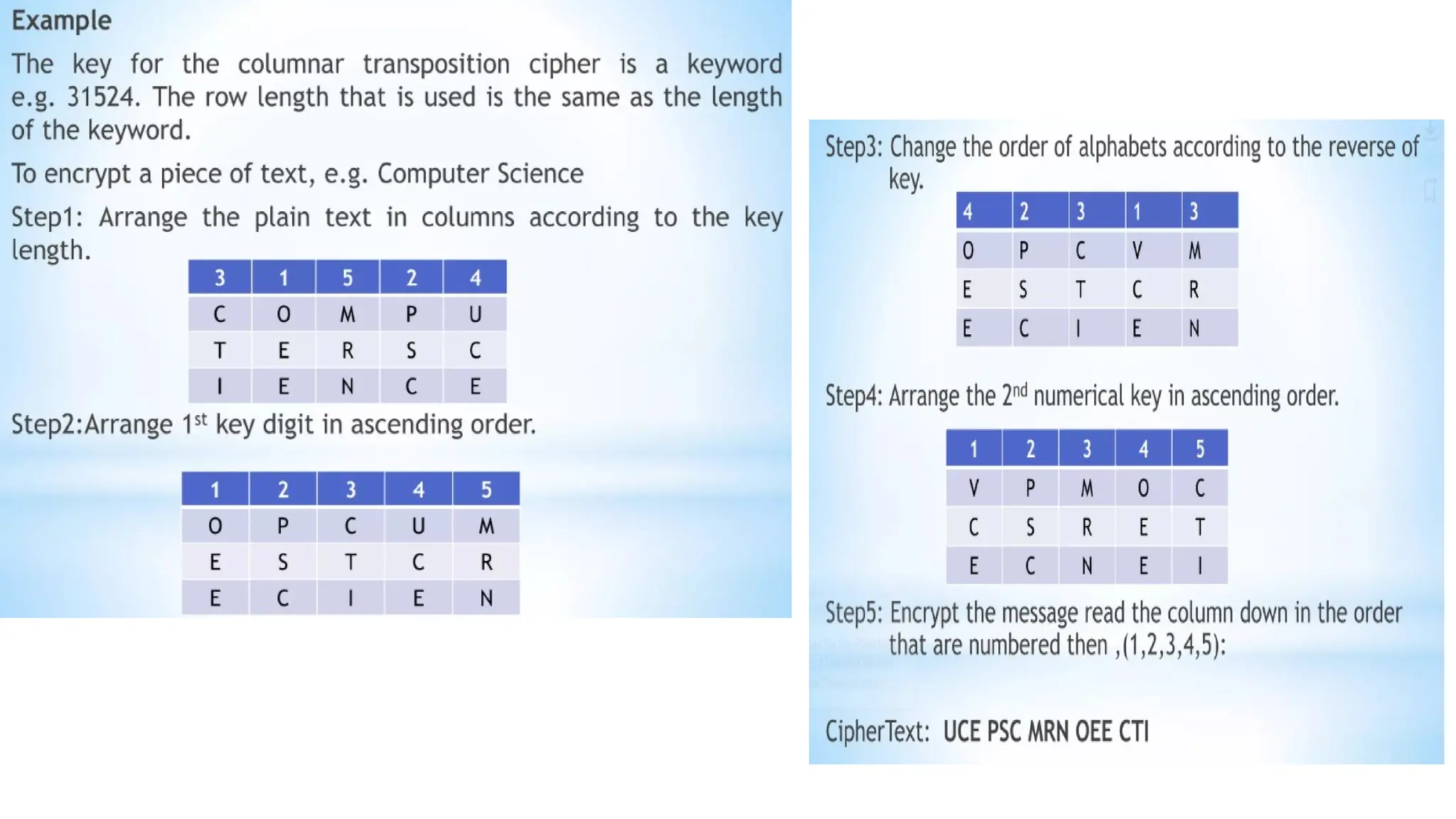
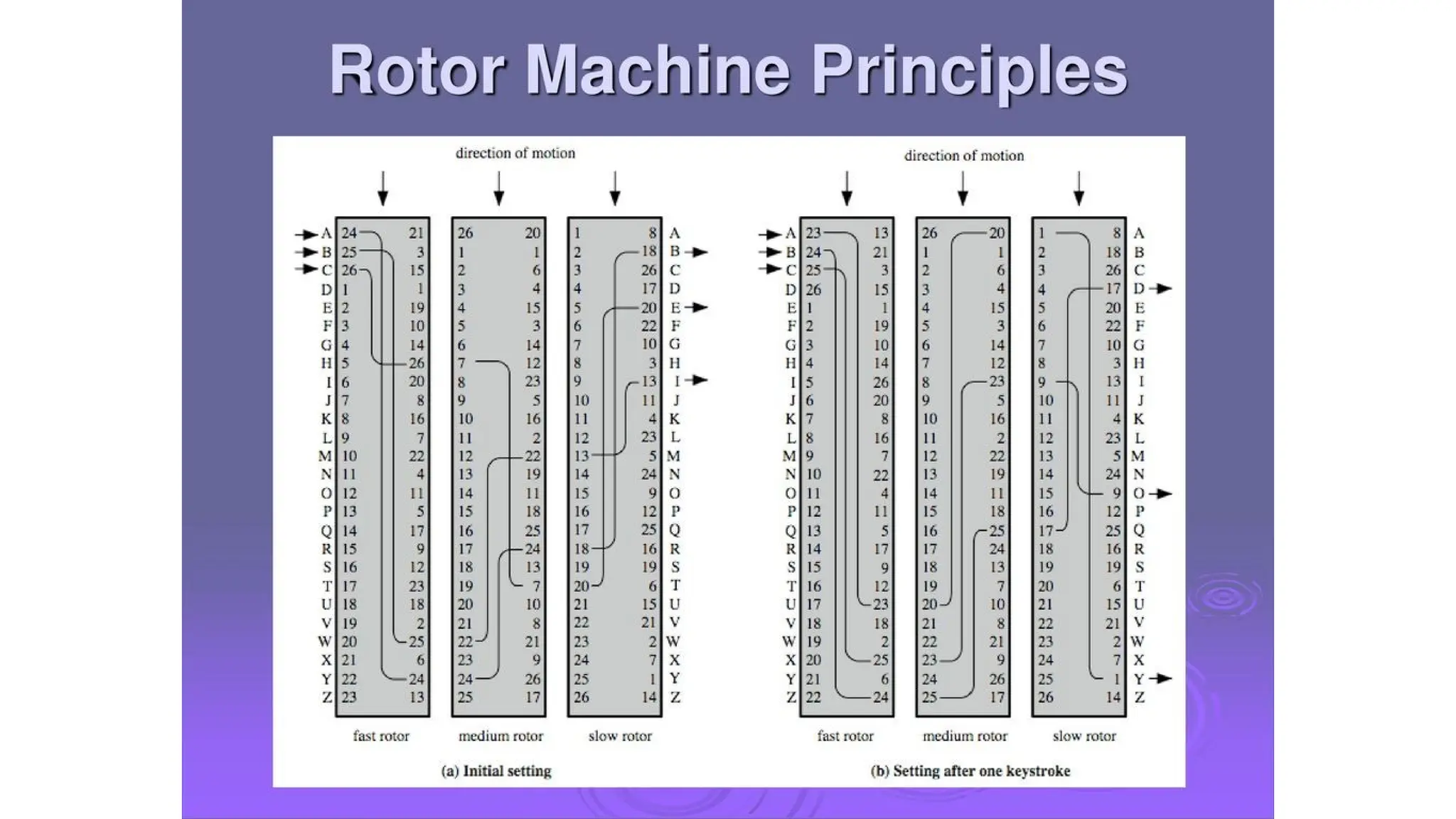
The document discusses symmetric key cryptographic algorithms, primarily focusing on symmetric encryption which uses a single key for both encryption and decryption. It highlights various algorithms like DES, AES, Blowfish, and 3DES, along with their applications and security measures needed for key sharing. Additionally, the document explores cryptanalysis methods, types of attacks on cryptographic systems, and classical encryption techniques including substitution and transposition methods.