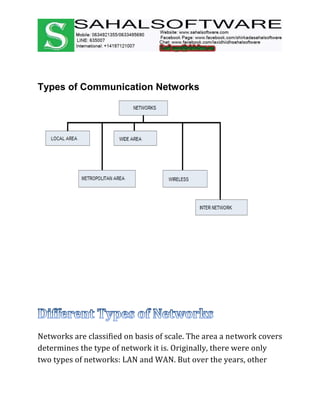
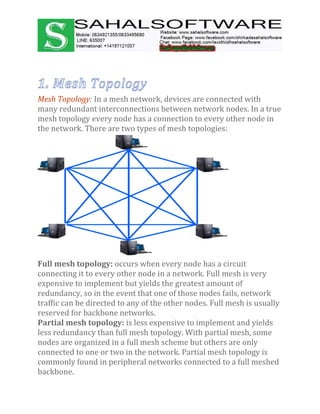
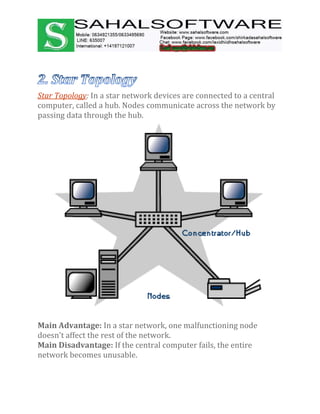
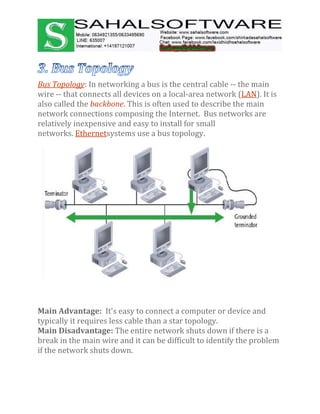
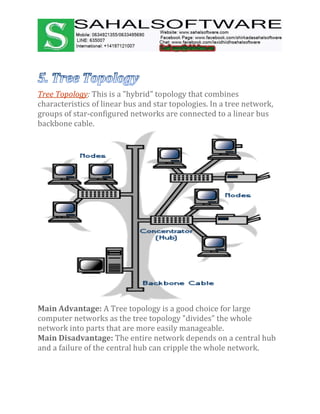
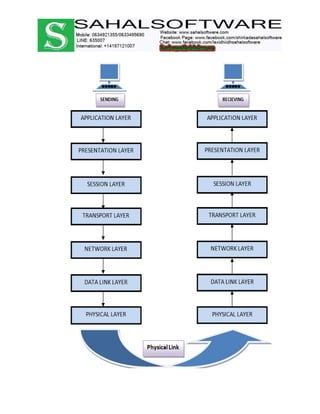
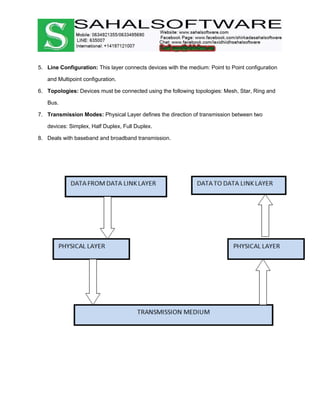
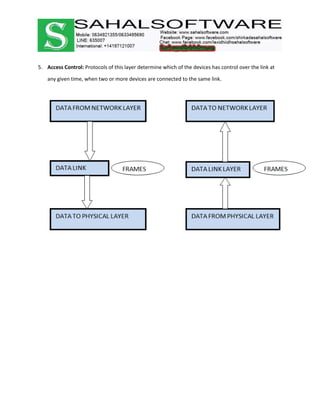
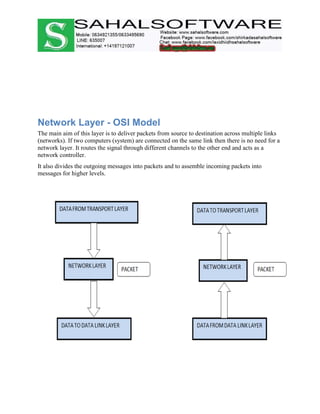
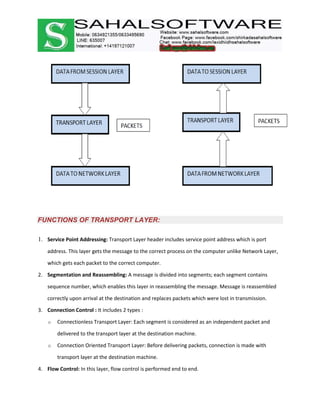
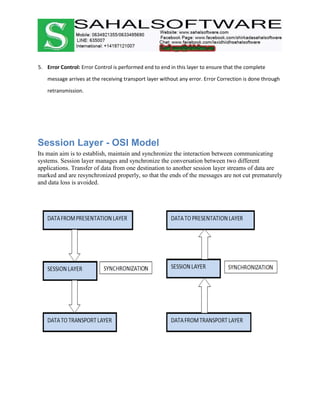
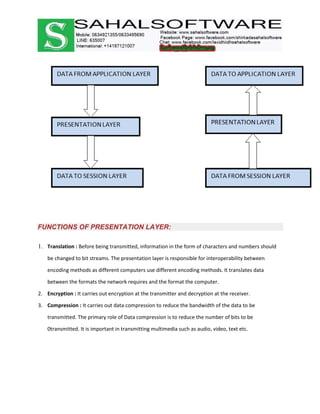
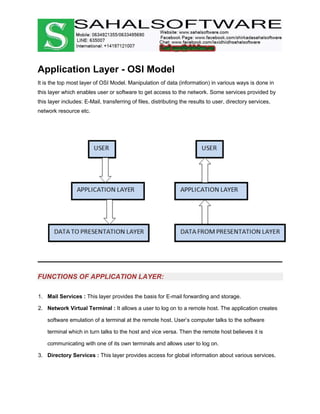
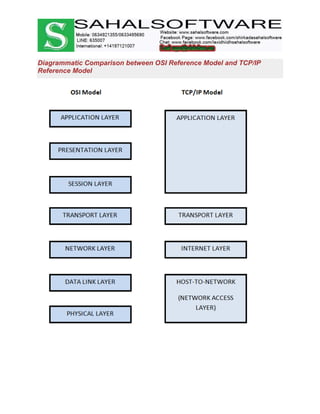
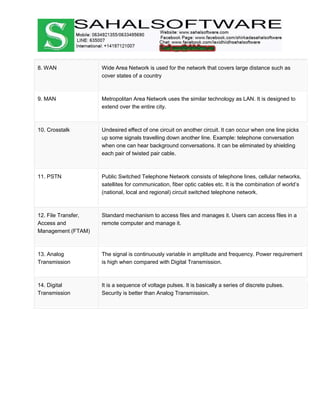
The document discusses the history and evolution of computer networks from early standalone computers in the 1970s-80s to today's internet-connected world. It describes how the ARPANET in 1969 first linked two computers, pioneering network technology. Over time, networks expanded to connect people globally through the internet. The document then defines what a computer network is, describing the basic requirements of at least two connected computers, servers, clients, networking hardware and software. It also outlines common network types including LAN, WAN, VPN, MAN and CAN, as well as network topologies like star, bus, ring and tree configurations. Finally, it introduces the ISO/OSI 7-layer model for standardizing network communication.