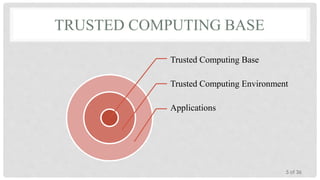
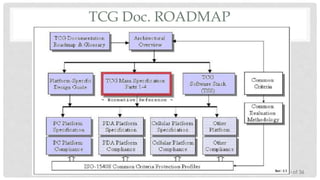
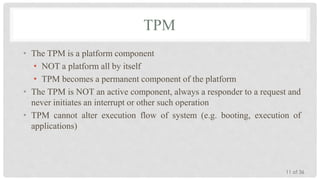
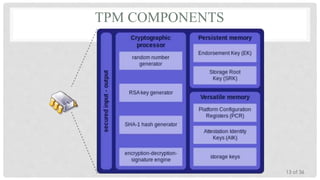
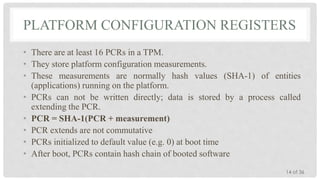
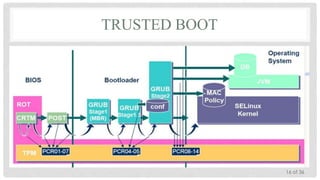
The Trusted Platform Module (TPM) is an international standard for a secure cryptoprocessor developed by the Trusted Computing Group to provide hardware-based security related features. It measures the boot process and software running on a device to ensure integrity and allows for remote attestation of the device's state. The TPM provides roots of trust for measurement, reporting, and storage and utilizes platform configuration registers, sealed storage, and keys to securely store and report information based on the device's configuration.