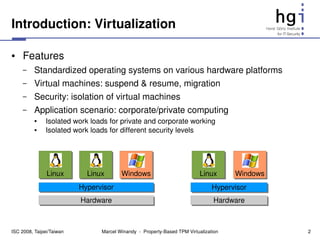
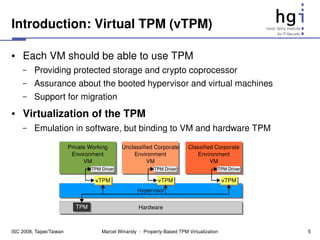
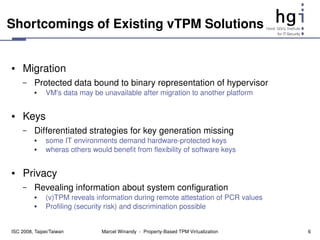
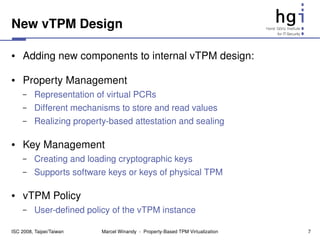
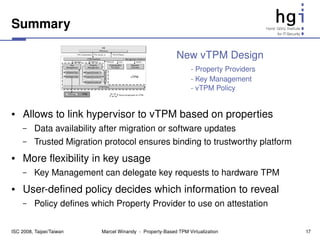
The document proposes a new design for virtual Trusted Platform Modules (vTPMs) that addresses shortcomings of existing solutions. The key aspects of the new design are:
1) It uses property providers that store vTPM measurements differently, allowing flexible attestation and migration.
2) It includes key and property management components for flexible key handling and attestation.
3) Each vTPM has a user-defined policy that determines which property provider to use for different operations.
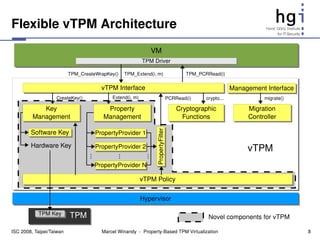
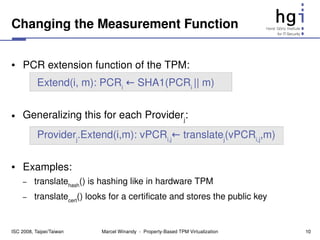
![Property Providers
● Each property provider has its own PCR vector
– How to store values is up to each implementation
– This results in a matrix of vPCRs
– vTPM Policy decides which vector to use on which operation
vTPM Instance
PropertyProvider 1 PropertyProvider j PropertyProvider N
vPCR[0] ... ...
vPCR[1] ... ... Mapping
...
...
...
vPCR[n] ... ...
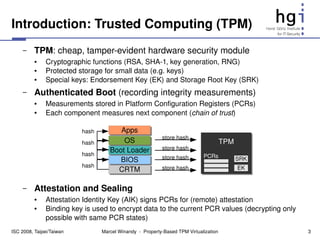
– Initialization TPM
● Applying all property providers to build the vPCR matrix PCRs
● Each Property Provider can implement a different mapping
ISC 2008, Taipei/Taiwan Marcel Winandy PropertyBased TPM Virtualization 9](https://image.slidesharecdn.com/winandyvtpm-12801832056835-phpapp02/85/Property-Based-TPM-Virtualization-9-320.jpg)
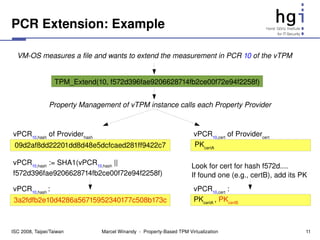

ISC 2008, Taipei/Taiwan Marcel Winandy PropertyBased TPM Virtualization 12](https://image.slidesharecdn.com/winandyvtpm-12801832056835-phpapp02/85/Property-Based-TPM-Virtualization-12-320.jpg)
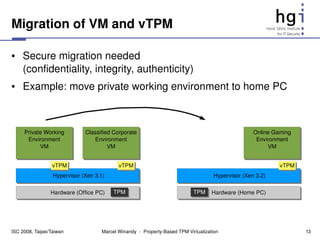
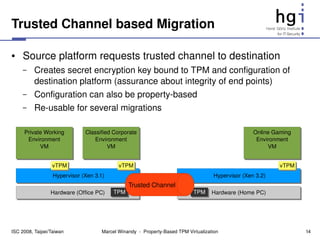


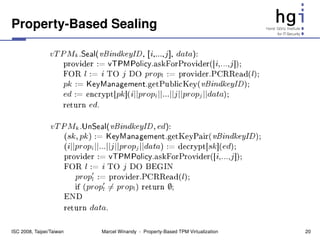

s := getState()
es := encrypt[sk](s)
deleteKey(sk), deleteState()
transfer(es,esk)
destroy() sk := unbind[PKBind](esk)
s := decrypt[sk](es)
X
setState(s)
ISC 2008, Taipei/Taiwan Marcel Winandy PropertyBased TPM Virtualization 21](https://image.slidesharecdn.com/winandyvtpm-12801832056835-phpapp02/85/Property-Based-TPM-Virtualization-21-320.jpg)