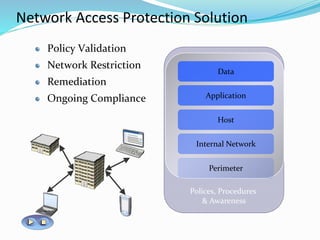
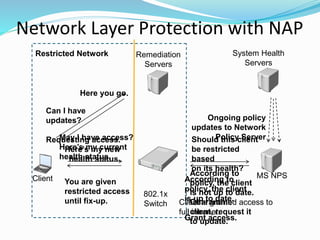
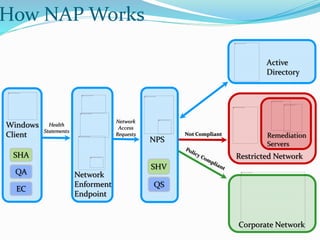
Network Access Protection (NAP) is a Windows Server 2008 feature that allows network administrators to control client access to network resources based on the client's compliance with health policies. NAP validates clients, enforces compliance through limited network access if needed, and facilitates automatic remediation to help clients meet policy requirements. NAP components work together to validate client health, restrict non-compliant clients, and provide updates to remedy issues and maintain ongoing compliance.