Embed presentation
Downloaded 10 times


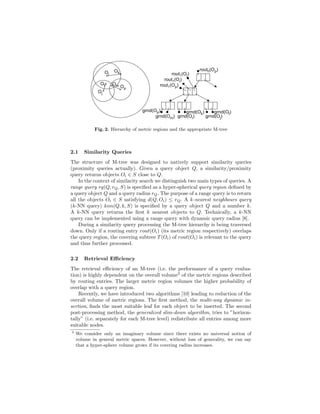

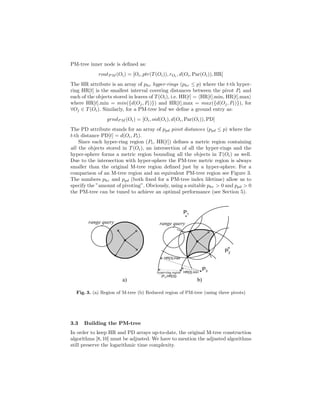

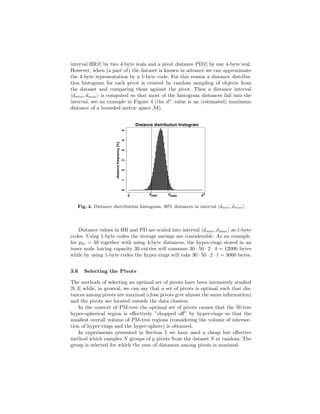


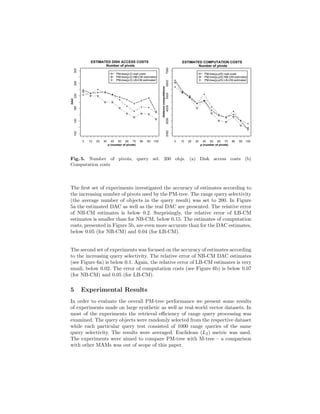

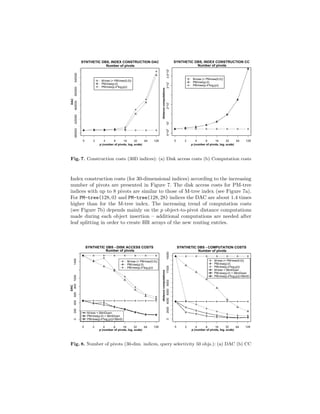





The document describes the PM-tree, a new metric access method that combines the M-tree with pivot-based approaches to improve efficiency of similarity search in multimedia databases. The PM-tree enhances M-tree routing and ground entries by including pivot-based information like hyper-ring regions defined by pivot objects and distances. This reduces the volume of metric regions described by entries, tightly bounding indexed objects and improving retrieval performance. Algorithms for building and querying the PM-tree are presented, showing how pivot distances are used to prune irrelevant regions during search.















