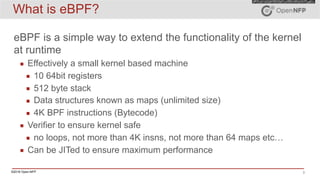
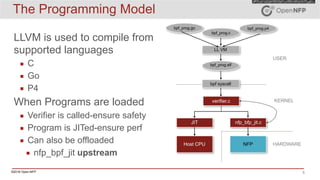
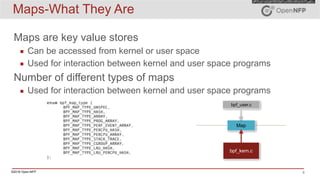
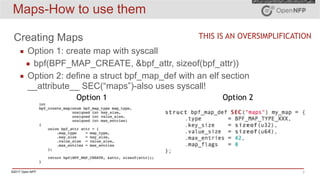
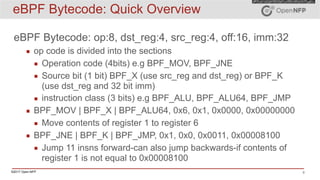
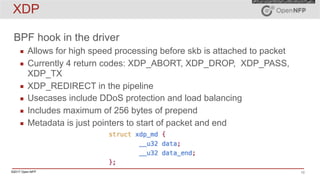
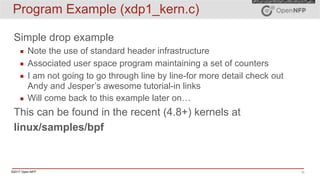
The document provides an overview of eBPF (extended Berkeley Packet Filter) and XDP (express data path), including their architecture, programming model, and use cases in enhancing kernel functionality and network performance. eBPF allows developers to run sandboxed programs in the kernel for tasks like load balancing and security, while XDP enables high-speed packet processing before they are attached to sockets. It also discusses the programming model, how to create maps for data interaction, and various hooks available in the kernel for BPF.