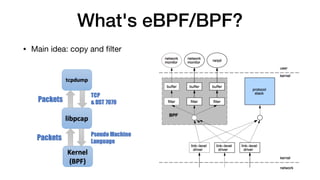
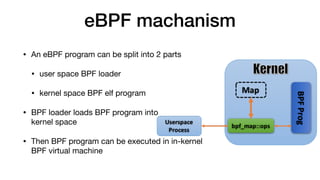
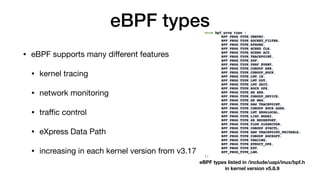
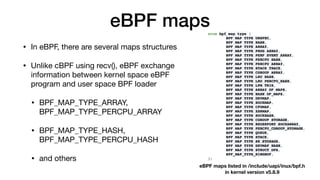
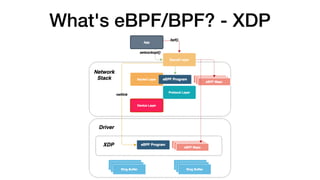
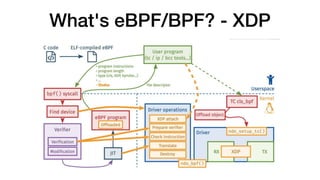
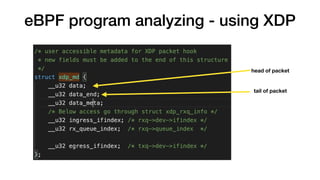
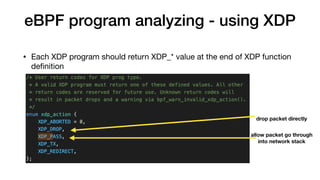
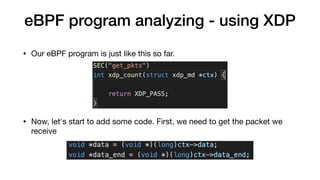
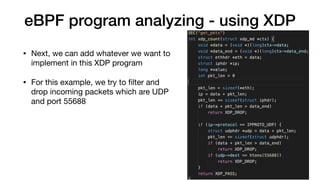
This document provides an overview of eBPF/BPF and instructions for creating an eBPF program from scratch. It begins with explaining what eBPF/BPF is, its history and main ideas. It then covers how to build an eBPF program from the Linux kernel source code, including prerequisites, compilation steps, and modifying the makefile. The document also discusses how to program an eBPF program manually, analyzing the eBPF program and loader. It concludes with a promise of a quick demo.