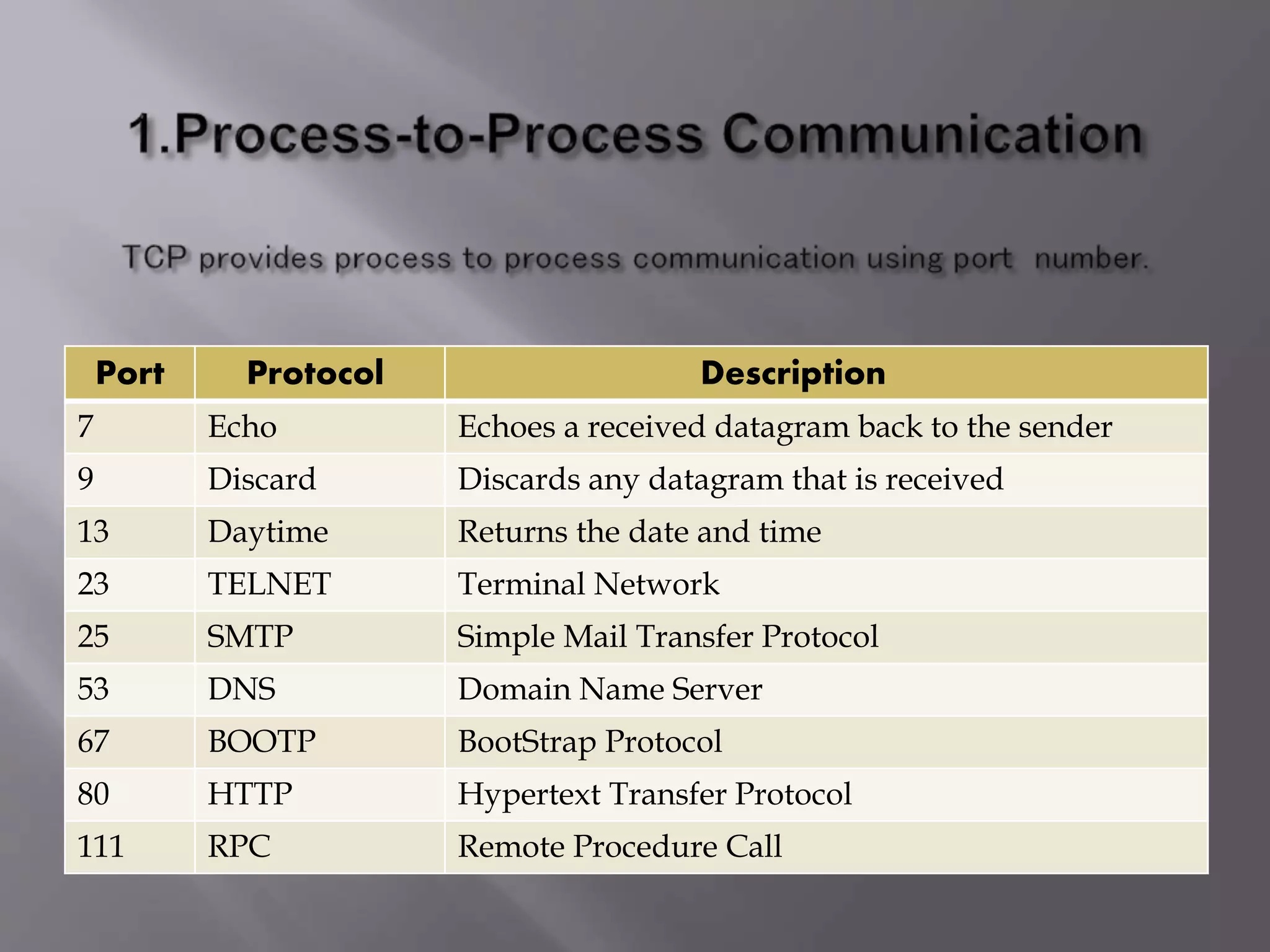
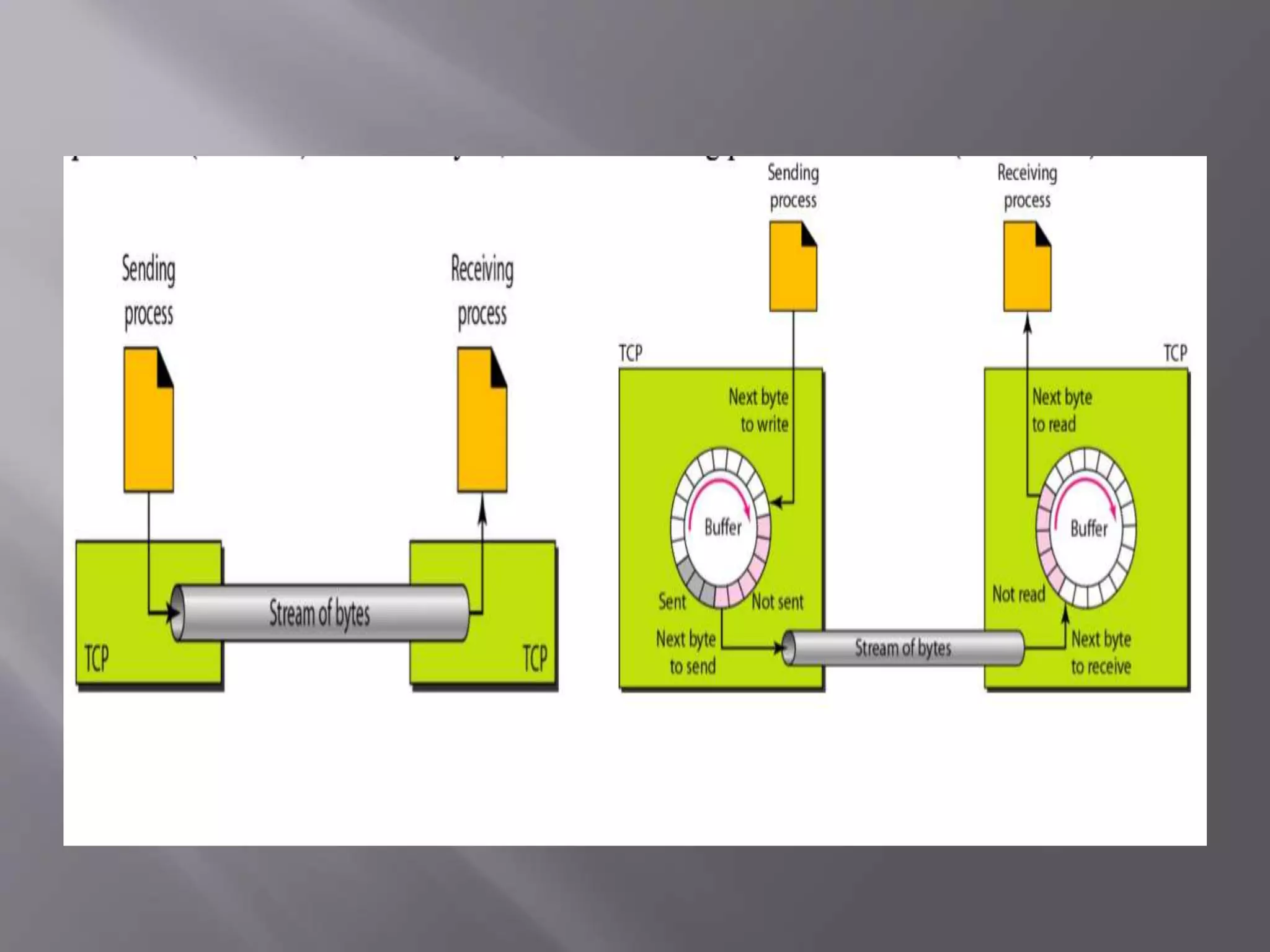
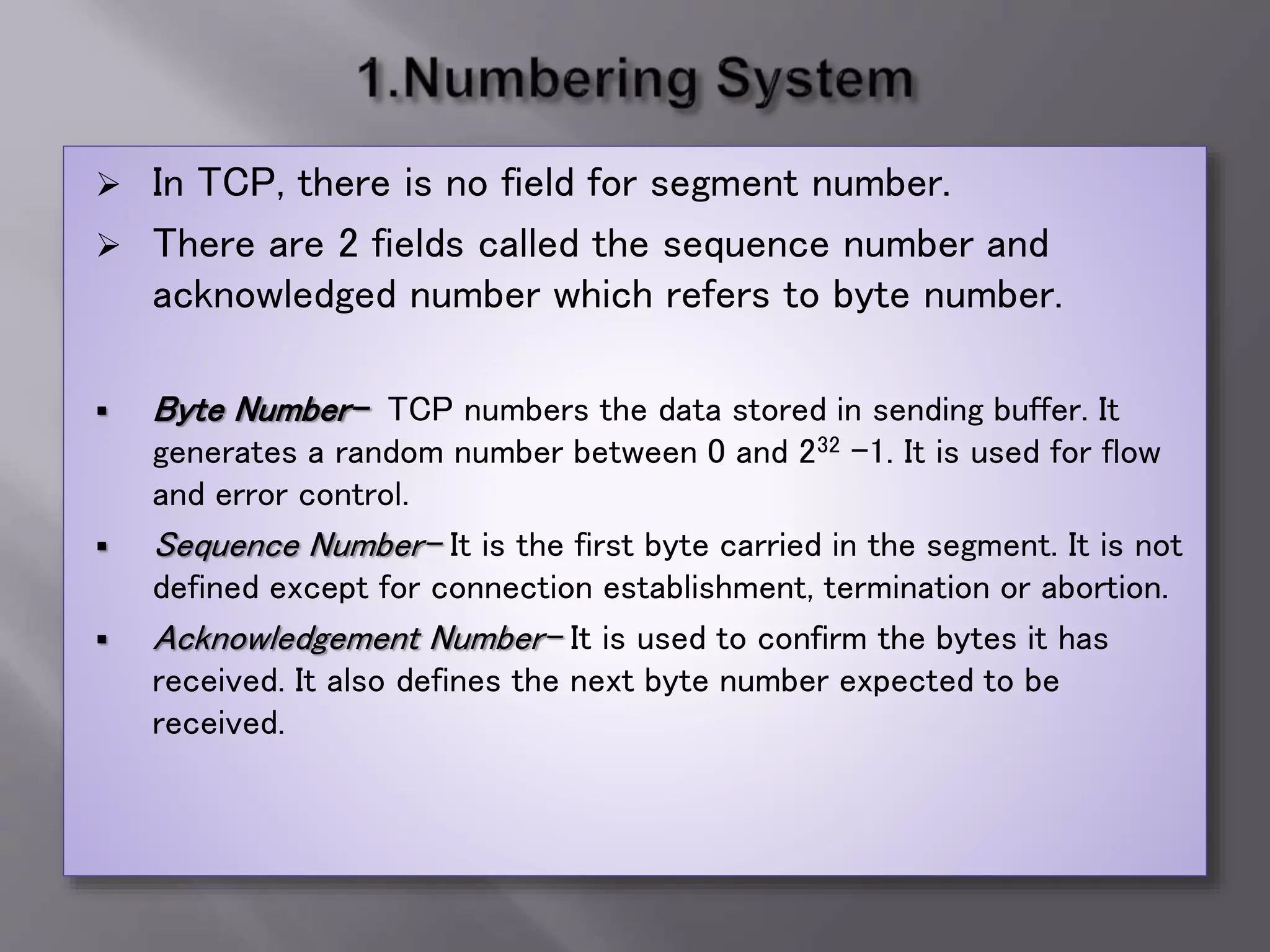
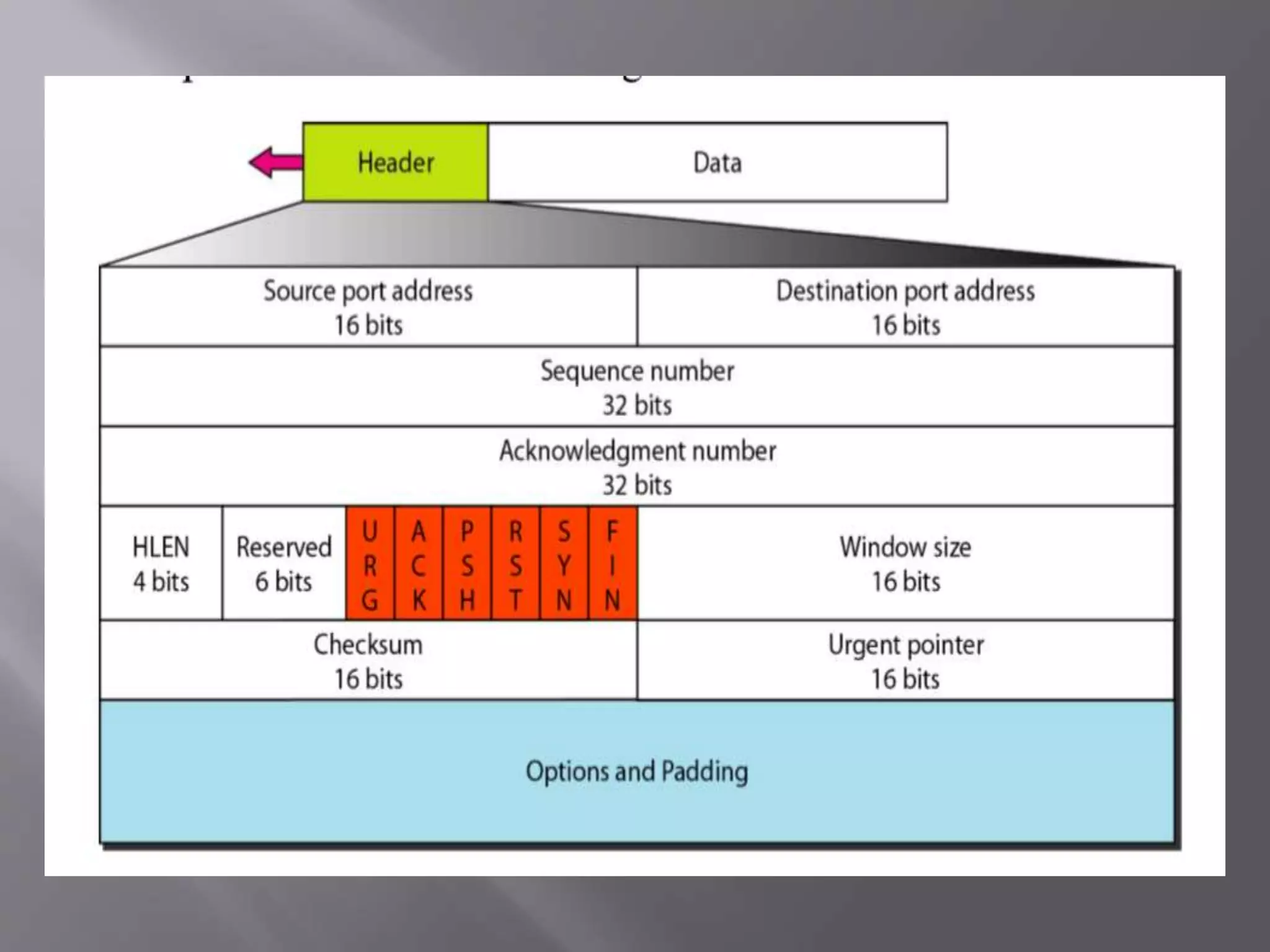
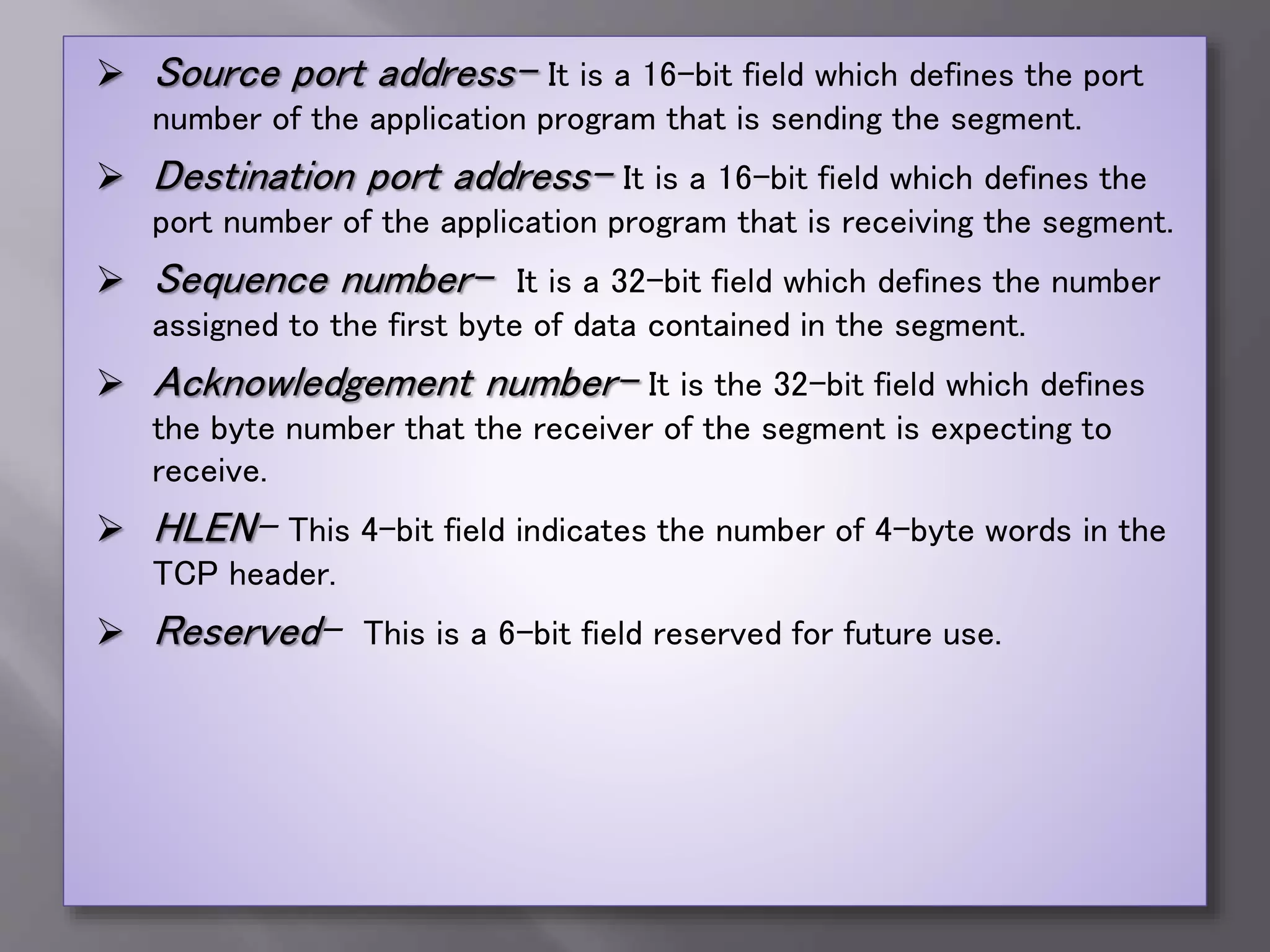
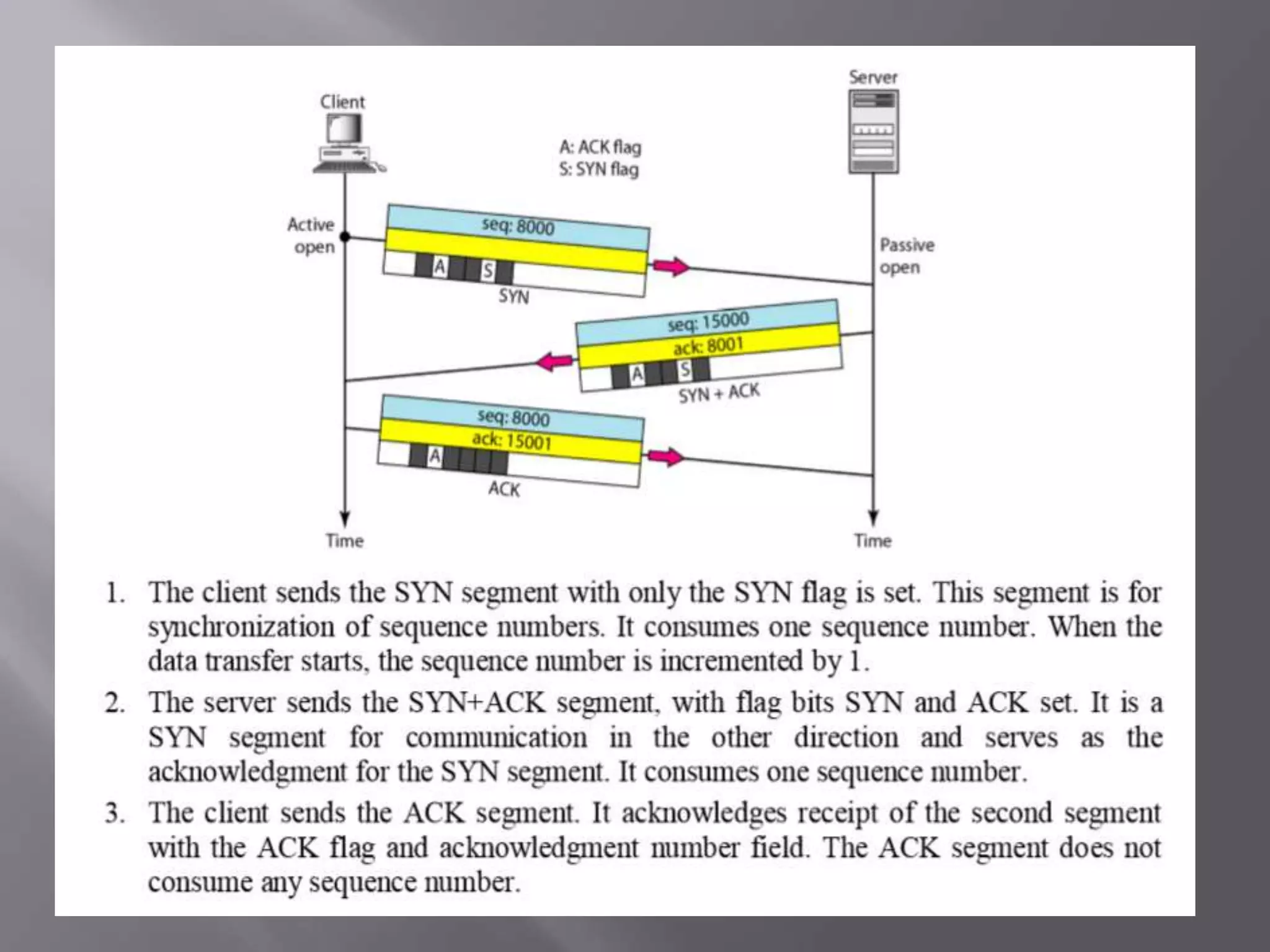
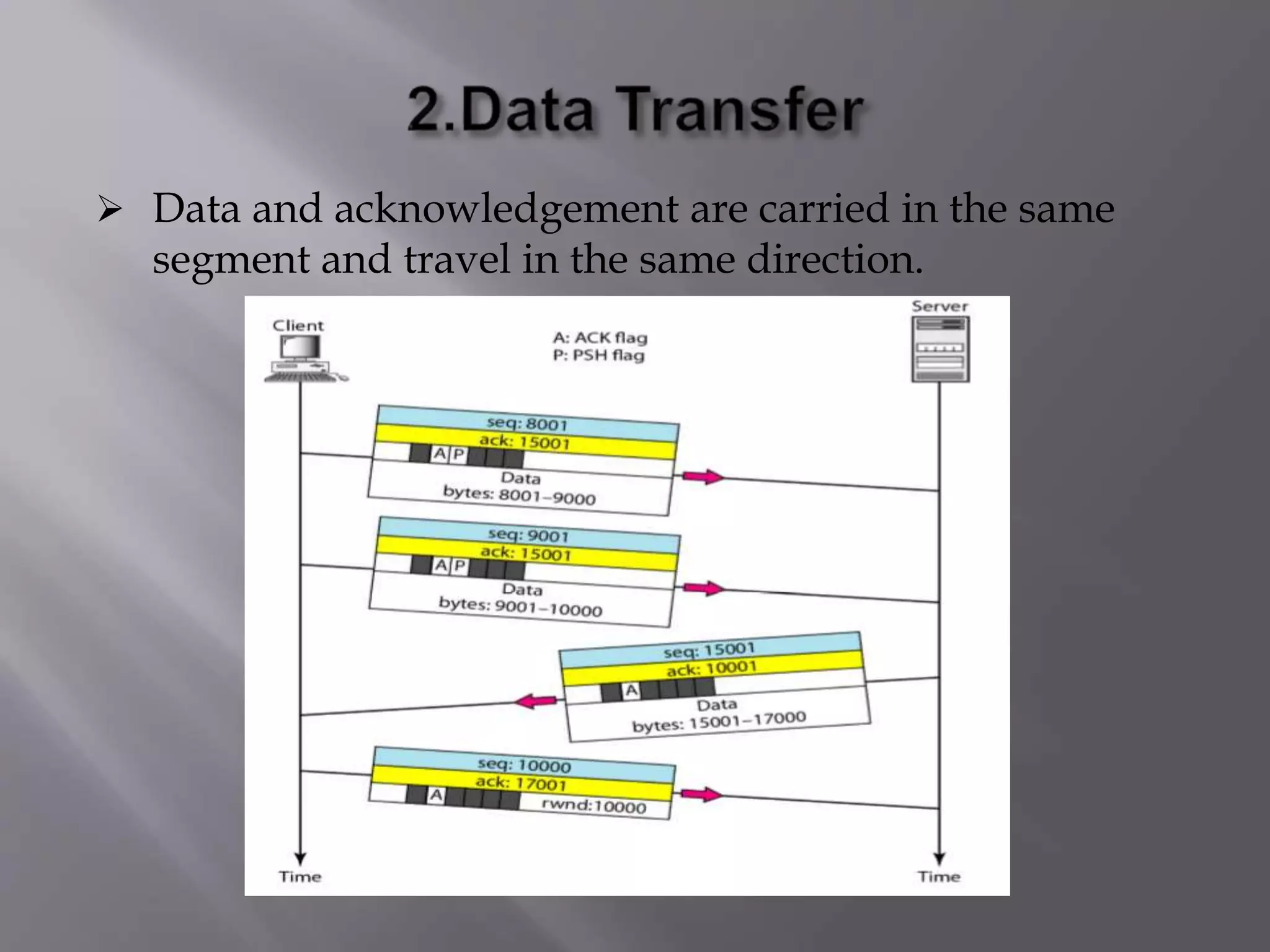
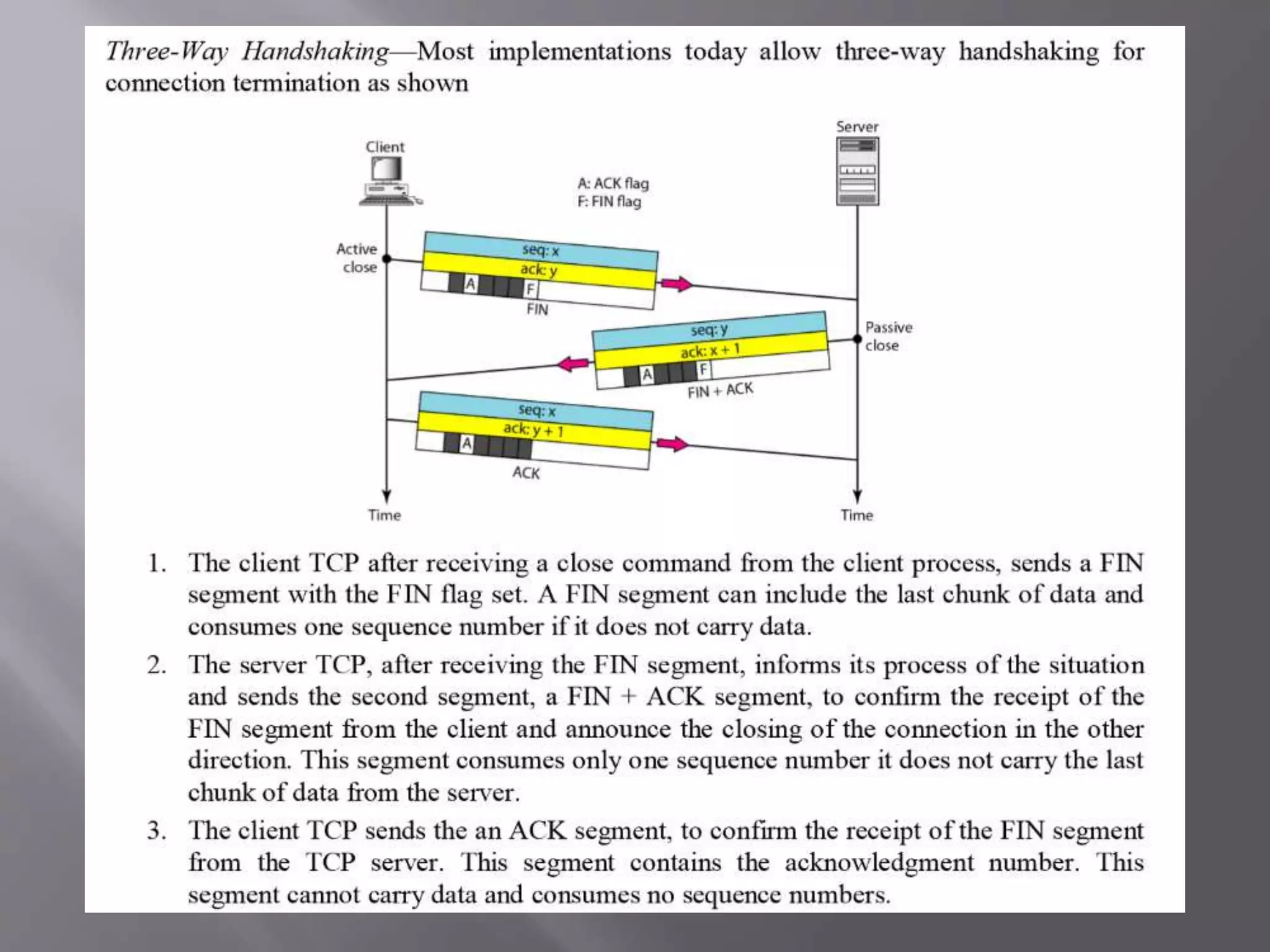
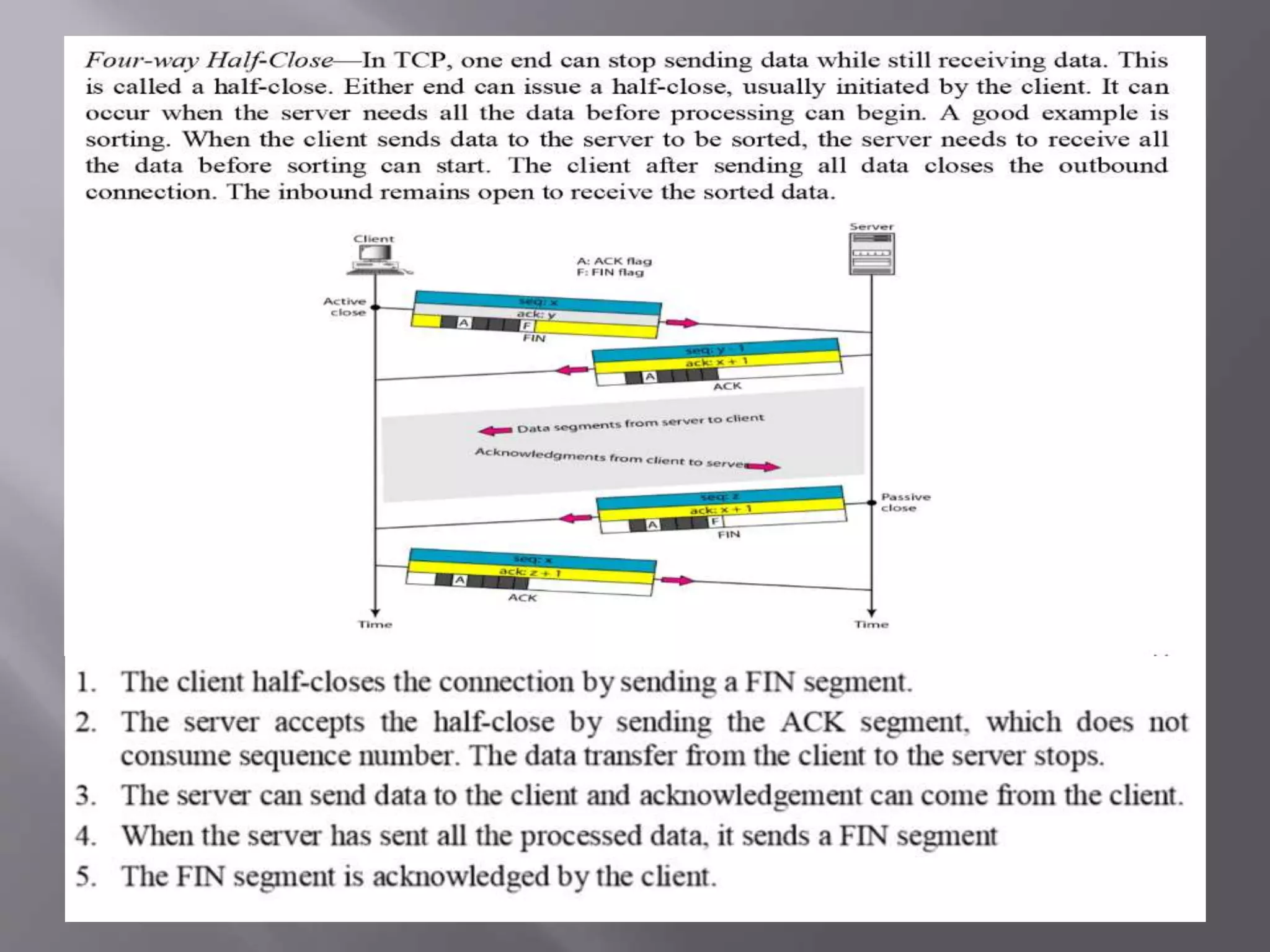
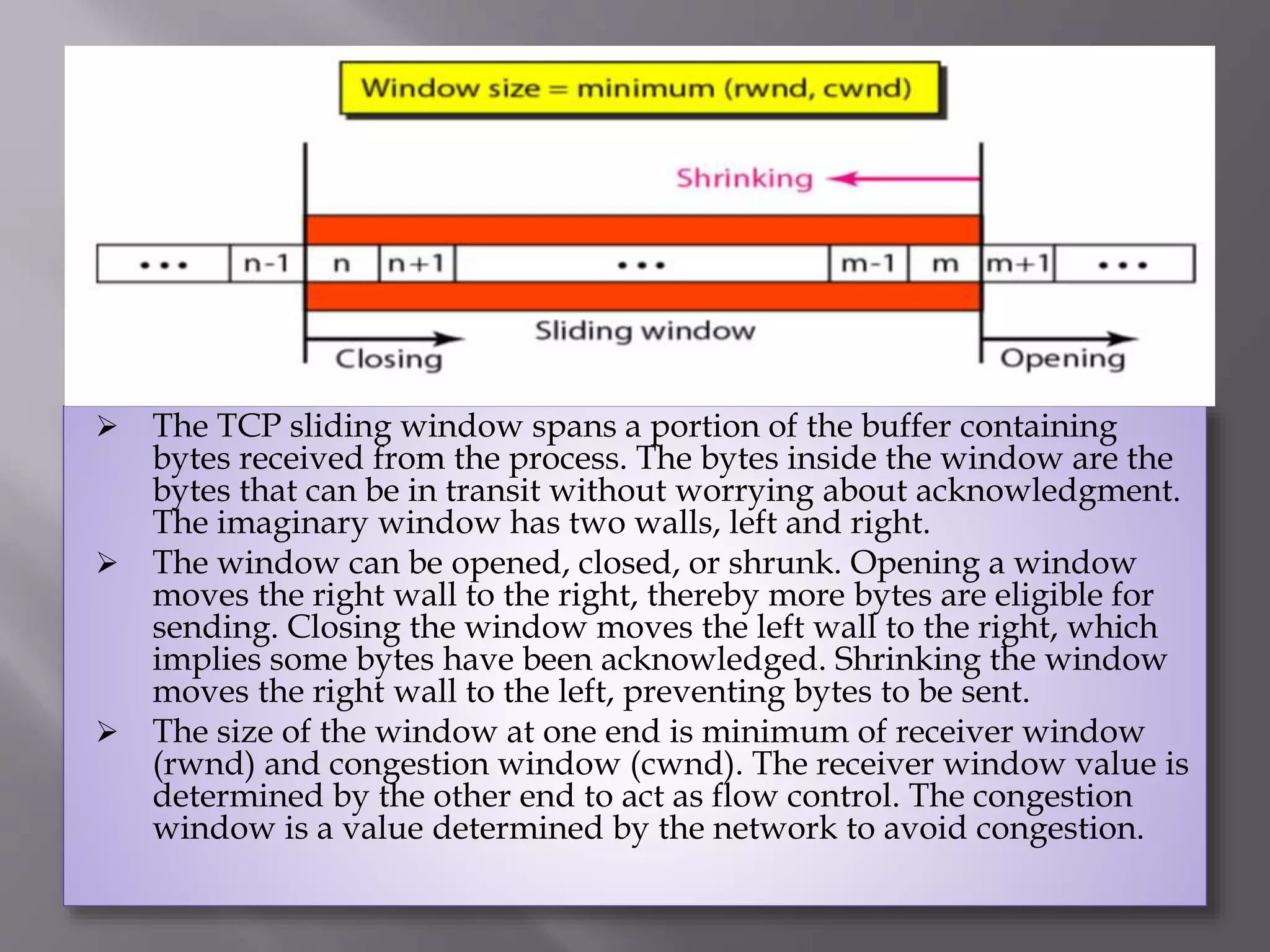
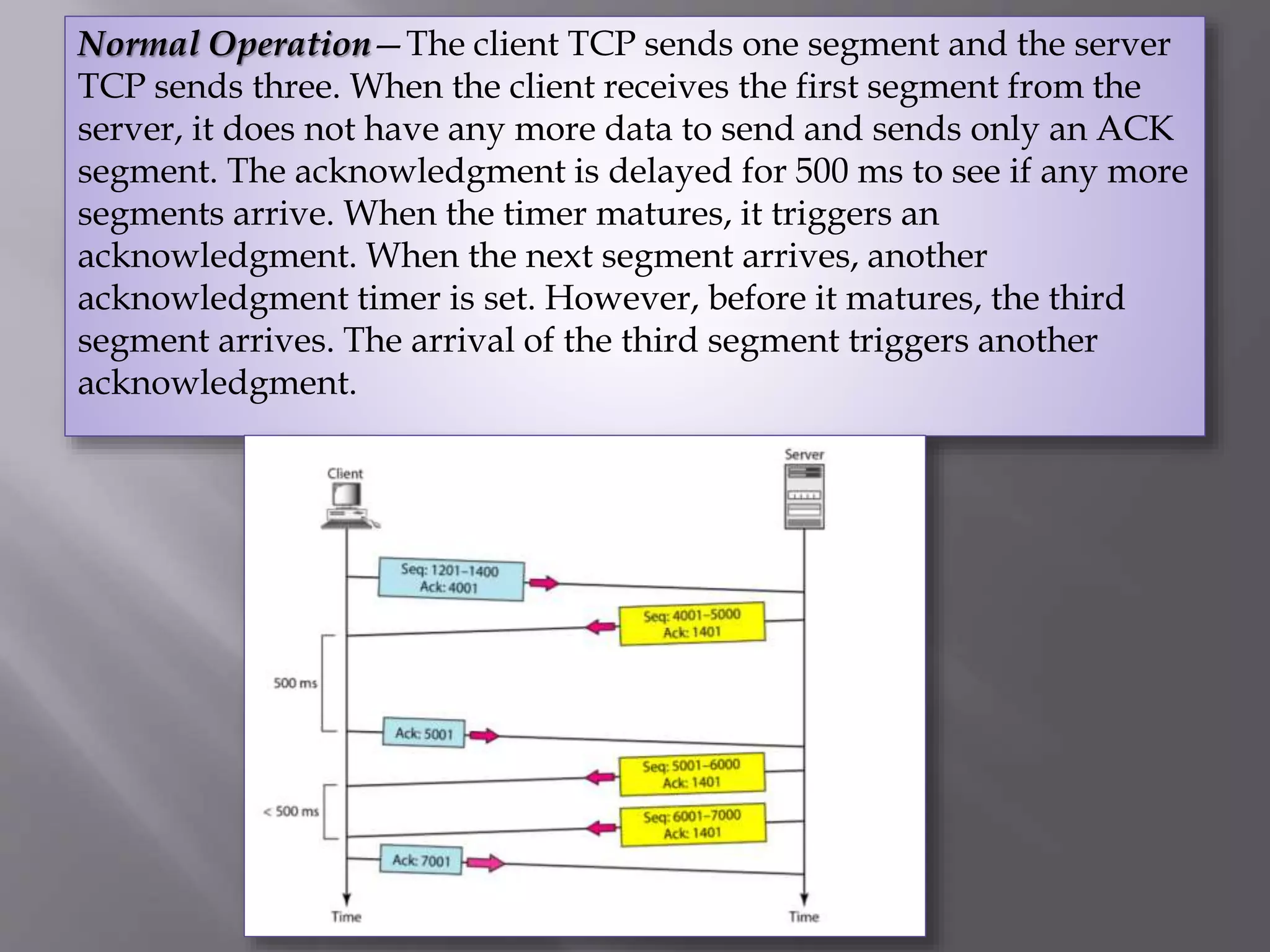
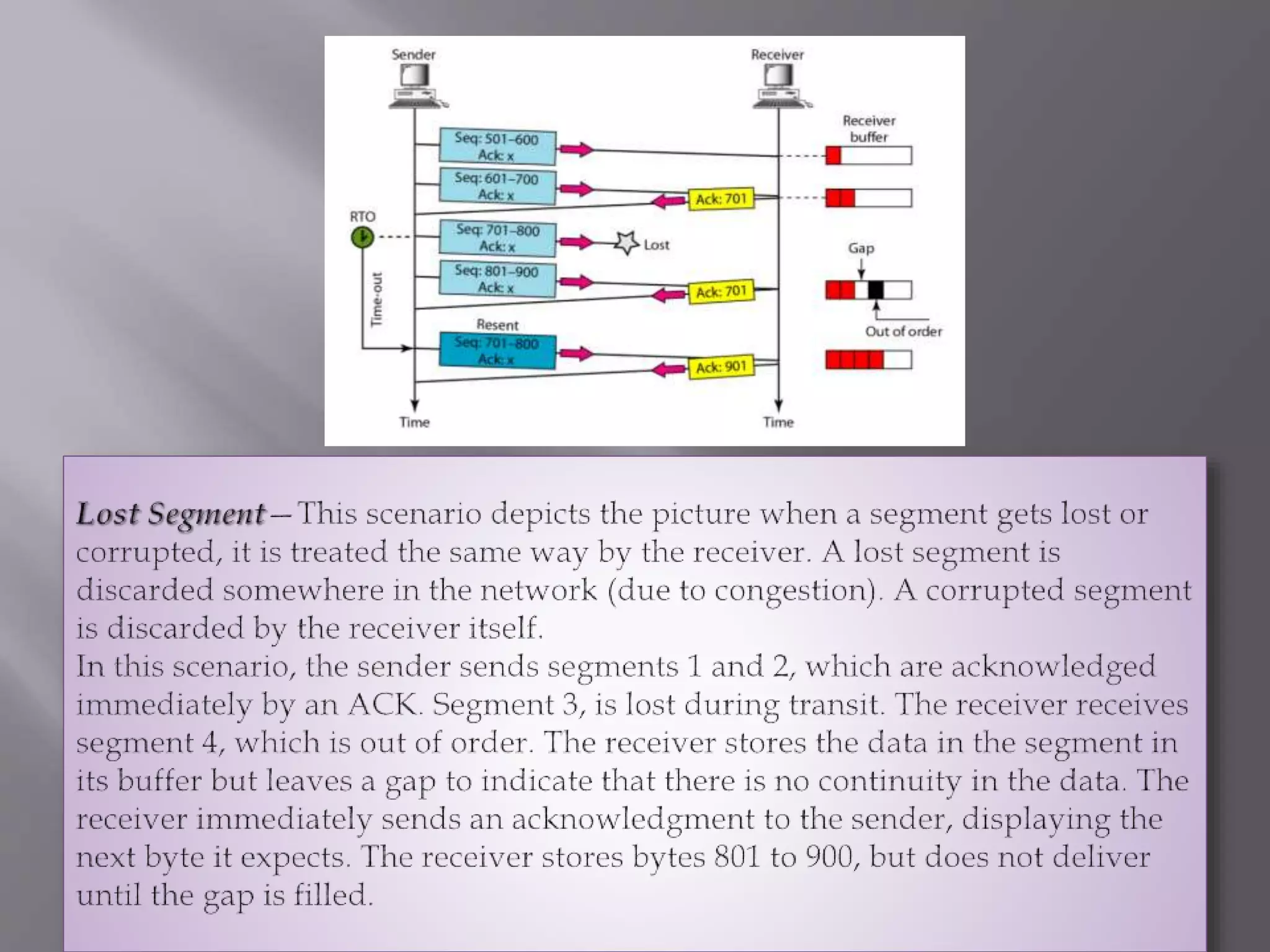
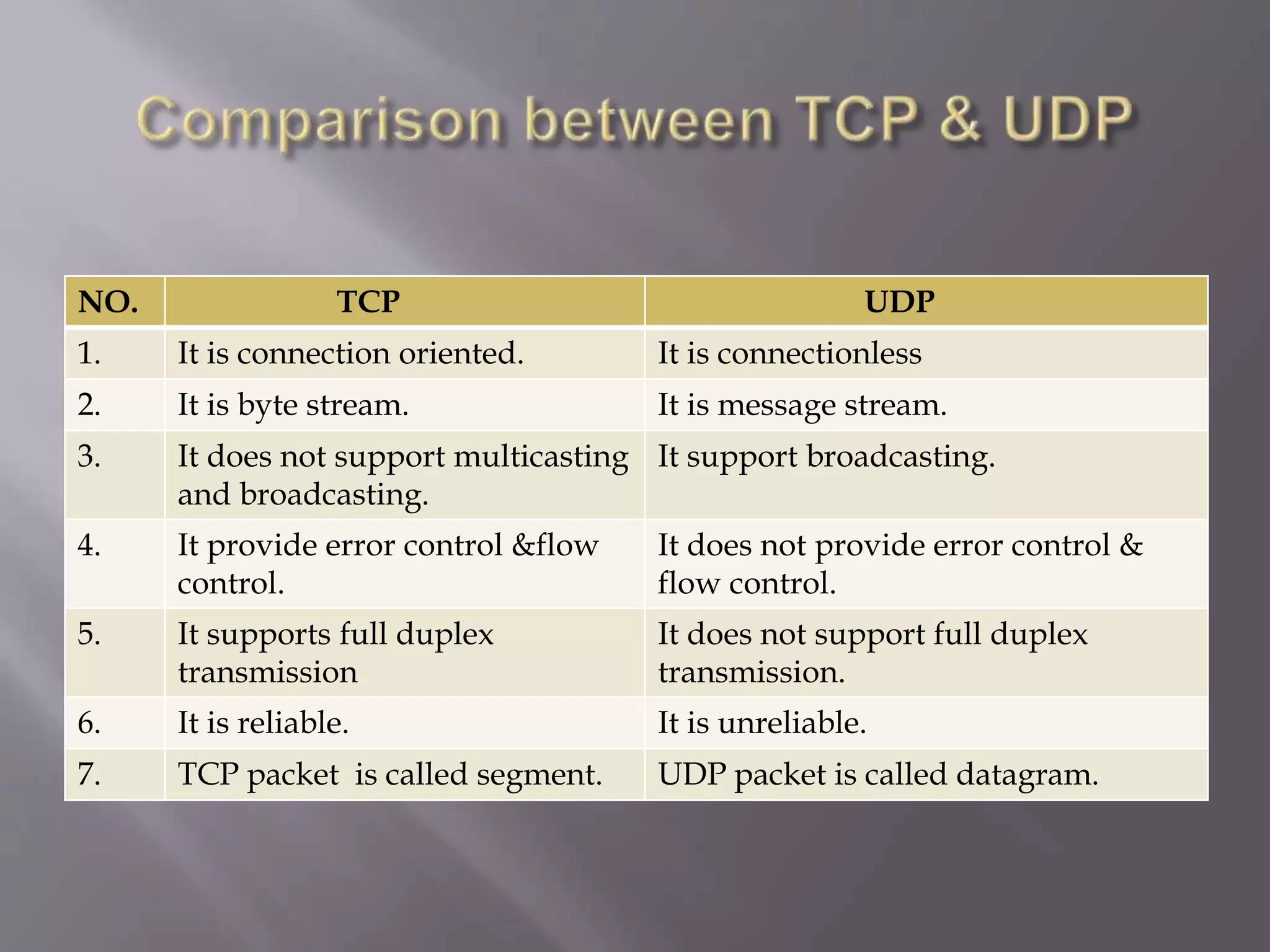
The document outlines the Transmission Control Protocol (TCP) as a connection-oriented protocol that ensures reliable data transmission using flow and error control mechanisms. It emphasizes TCP's features such as stream delivery, the use of acknowledgment for data integrity, and the three-way handshake process for establishing connections. Additionally, it compares TCP with User Datagram Protocol (UDP), highlighting TCP's reliability and full-duplex communication capabilities.