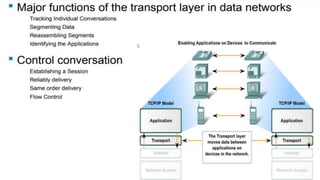
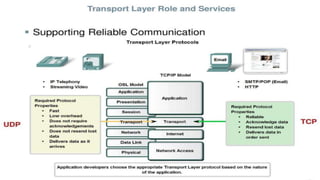
The document provides a comprehensive overview of transport layer protocols in networking, focusing on the functions, roles, and services of the transport layer, particularly Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). TCP is explained as a reliable, connection-oriented protocol that ensures data integrity and ordered delivery, while UDP is described as a simpler, unreliable protocol suitable for applications where speed is crucial. Key concepts such as segmentation, port numbers, error control mechanisms, and connection management, including TCP's three-way handshake, are elaborated upon.