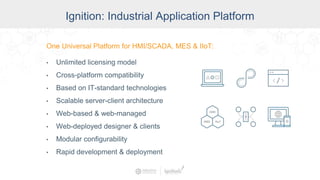
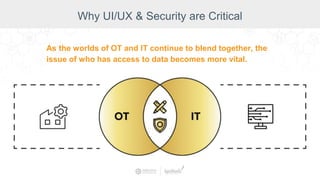
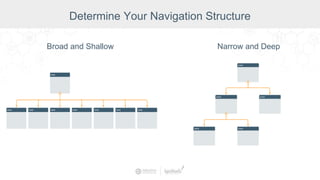
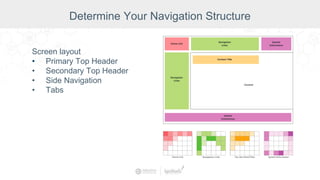
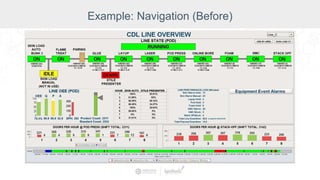
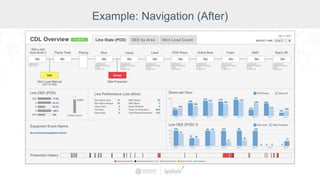
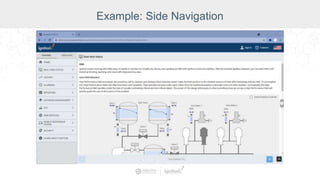
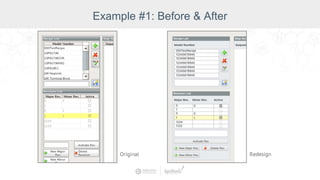
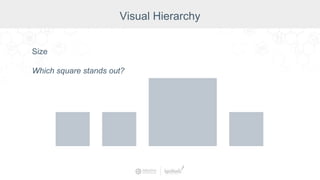
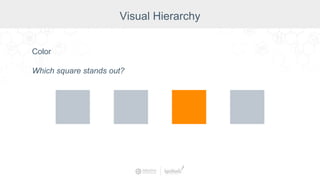
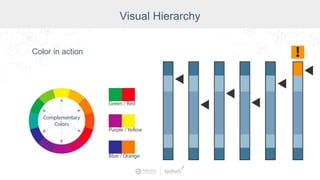
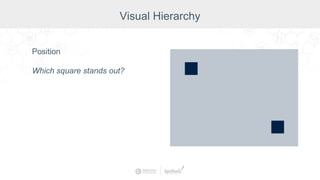
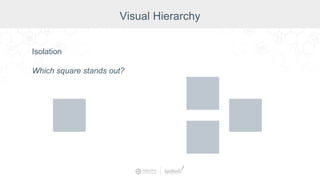
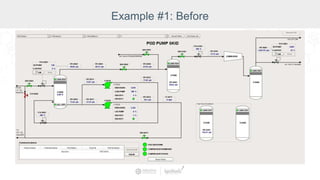
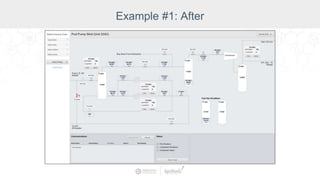
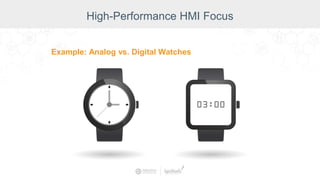
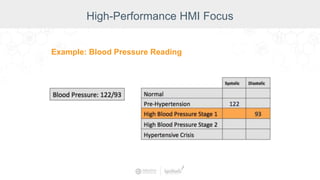
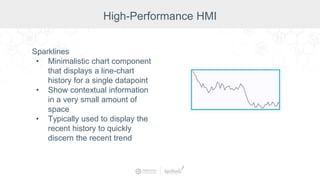
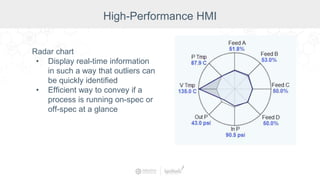
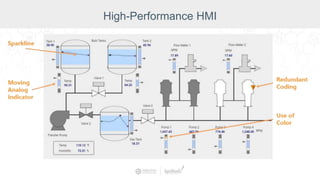
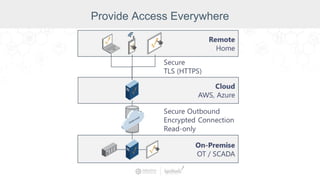
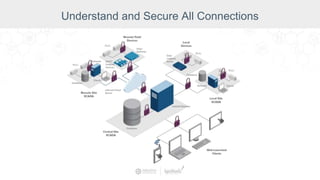
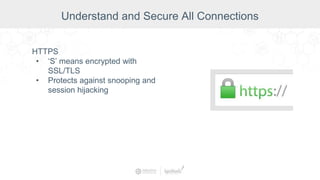
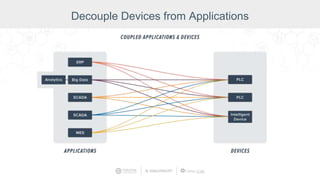
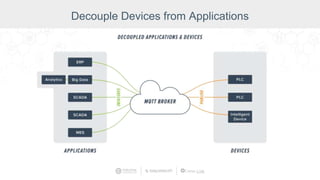
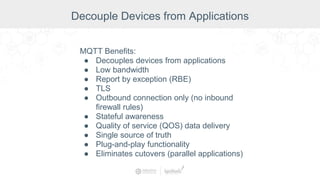
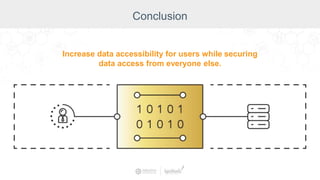
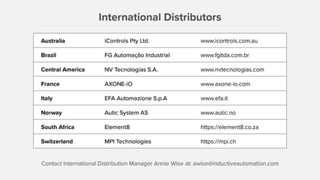
The document summarizes a presentation by Inductive Automation on the importance of UI/UX and security in industrial control systems, focusing on ten essential tips for enhancing design and security. It highlights key aspects of the Ignition industrial application platform, which supports scalable architecture and cross-platform compatibility. The presentation emphasizes improving user experience and securing data access while providing practical advice on navigation, cognitive load management, and leveraging modern technologies.