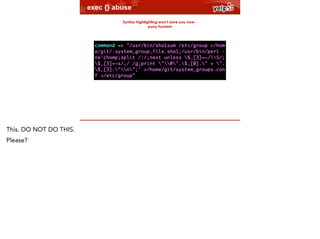
The document discusses the key lessons learned from writing poor Puppet code, focusing on the misuse of functions, inline templating, and exec abuse. It highlights the challenges of managing SSH keys, particularly in integrating Gitolite authentication into legacy user management systems. The author emphasizes the importance of maintainability and reusable functions while cautioning against common coding pitfalls.











![Prepend instance name
!
Add user to every instance
– [“${username} ${restofkey}”]
– [“${instance} “]
– [“${instance} ${username} ${restofkey}”]
– Use this as $name in a define to iterate
– ssh/authorized_keys.d/${instance}.pub
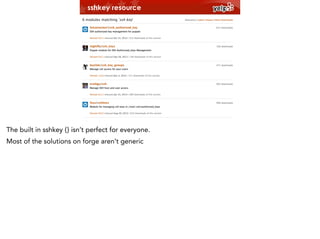
We then have an array of instances, and an array of users/keys.
Our array_prefix function makes the product of both lists.
Complexity due to iterating over two lists $key_lines and $instances](https://image.slidesharecdn.com/theworstcodeieverwrote-puppetberlin-131115191444-phpapp02/85/The-worst-code-I-ever-wrote-14-320.jpg)
![Prepend instance name
!
Add user to every instance
– [“${username} ${restofkey}”]
– [“${instance} “]
– [“${instance} ${username} ${restofkey}”]
– Use this as $name in a define to iterate
– ssh/authorized_keys.d/${instance}.pub
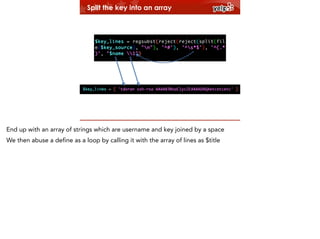
We then have an array of instances, and an array of users/keys.
Our array_prefix function makes the product of both lists.
Complexity due to iterating over two lists $key_lines and $instances](https://image.slidesharecdn.com/theworstcodeieverwrote-puppetberlin-131115191444-phpapp02/85/The-worst-code-I-ever-wrote-15-320.jpg)
![Prepend instance name
!
Add user to every instance
– [“${username} ${restofkey}”]
– [“${instance} “]
– [“${instance} ${username} ${restofkey}”]
– Use this as $name in a define to iterate
– ssh/authorized_keys.d/${instance}.pub
We then have an array of instances, and an array of users/keys.
Our array_prefix function makes the product of both lists.
Complexity due to iterating over two lists $key_lines and $instances](https://image.slidesharecdn.com/theworstcodeieverwrote-puppetberlin-131115191444-phpapp02/85/The-worst-code-I-ever-wrote-16-320.jpg)
![Prepend instance name
!
Add user to every instance
– [“${username} ${restofkey}”]
– [“${instance} “]
– [“${instance} ${username} ${restofkey}”]
– Use this as $name in a define to iterate
– ssh/authorized_keys.d/${instance}.pub
We then have an array of instances, and an array of users/keys.
Our array_prefix function makes the product of both lists.
Complexity due to iterating over two lists $key_lines and $instances](https://image.slidesharecdn.com/theworstcodeieverwrote-puppetberlin-131115191444-phpapp02/85/The-worst-code-I-ever-wrote-17-320.jpg)
![Prepend instance name
!
Add user to every instance
– [“${username} ${restofkey}”]
– [“${instance} “]
– [“${instance} ${username} ${restofkey}”]
– Use this as $name in a define to iterate
– ssh/authorized_keys.d/${instance}.pub
This is gross
We then have an array of instances, and an array of users/keys.
Our array_prefix function makes the product of both lists.
Complexity due to iterating over two lists $key_lines and $instances](https://image.slidesharecdn.com/theworstcodeieverwrote-puppetberlin-131115191444-phpapp02/85/The-worst-code-I-ever-wrote-18-320.jpg)