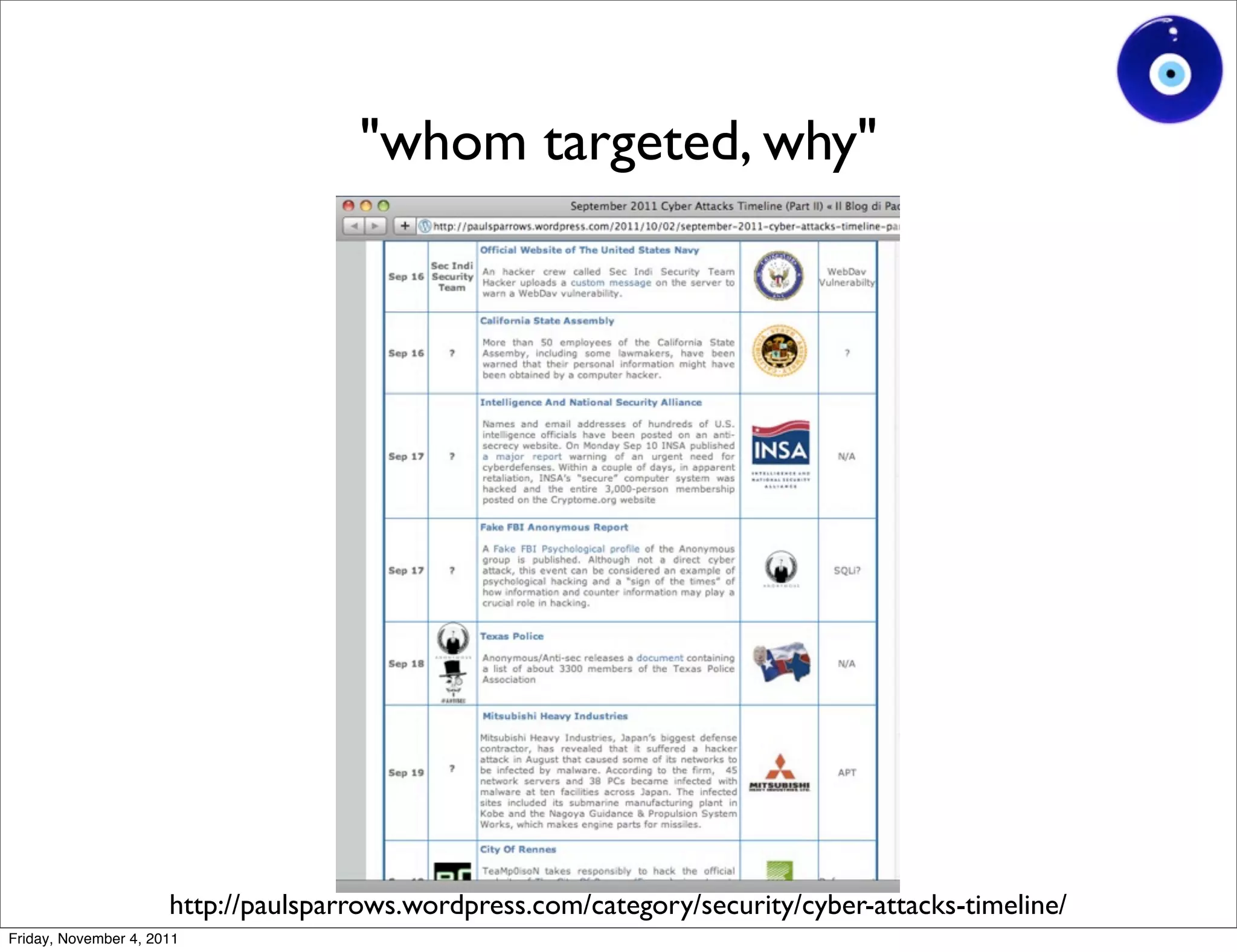
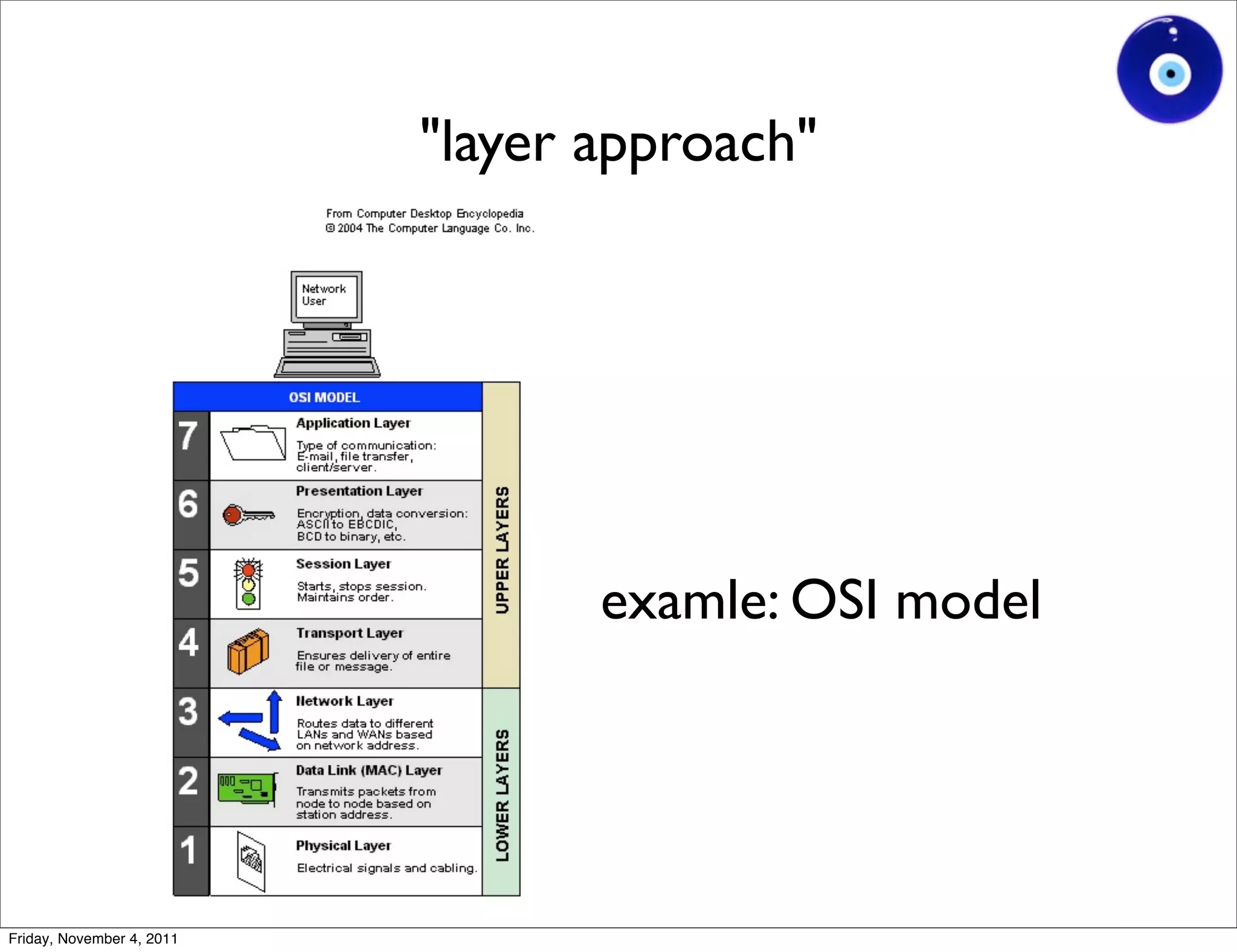
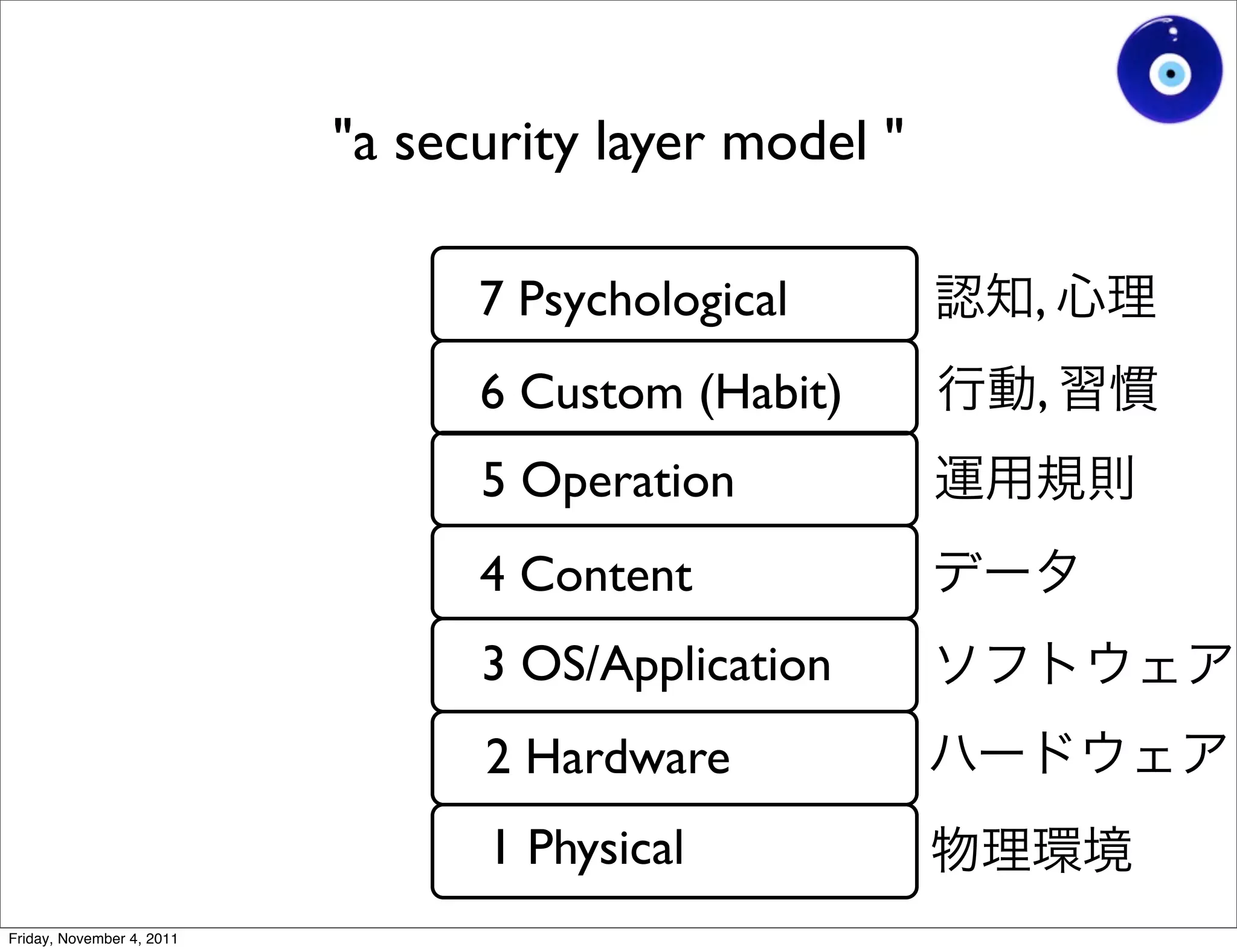
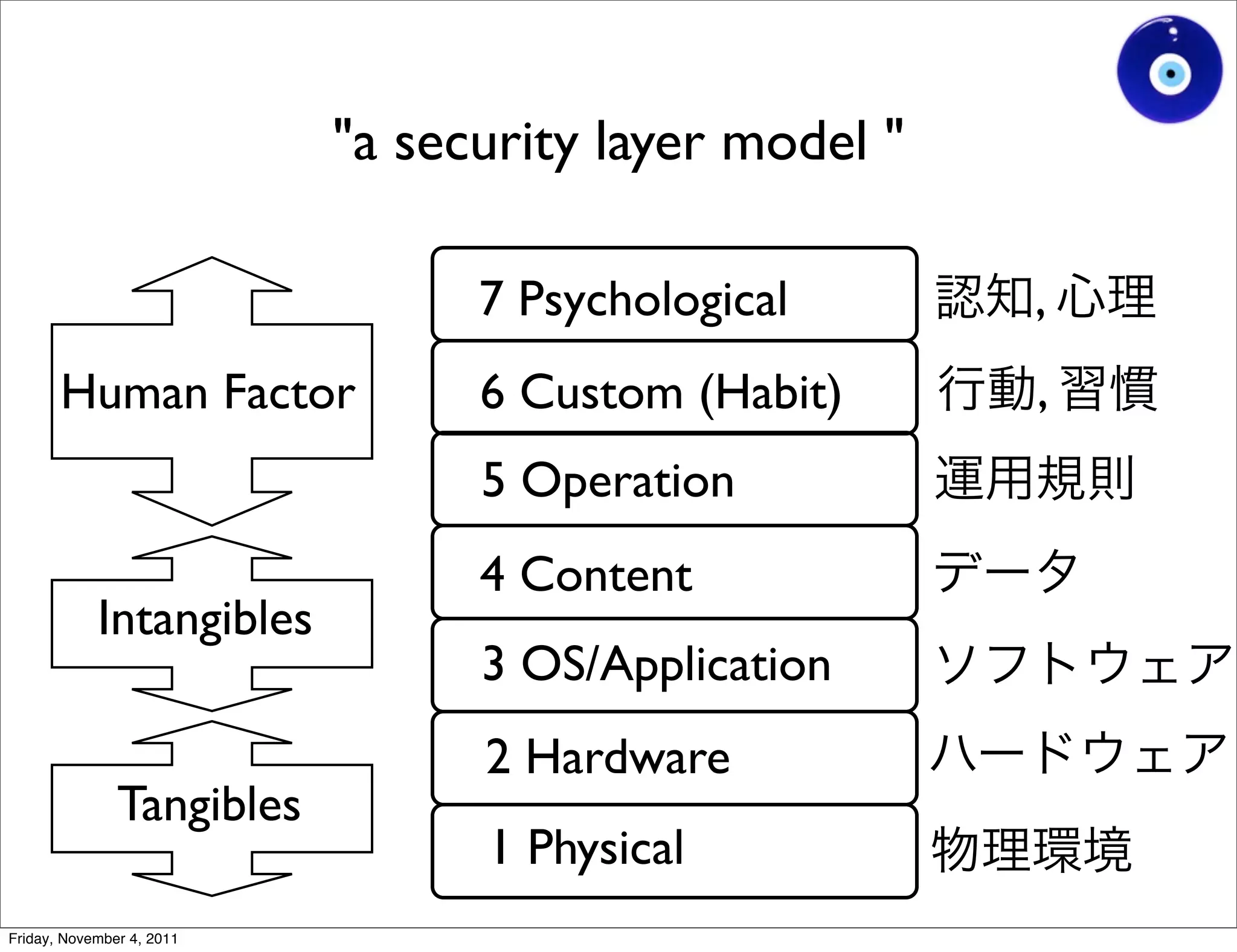
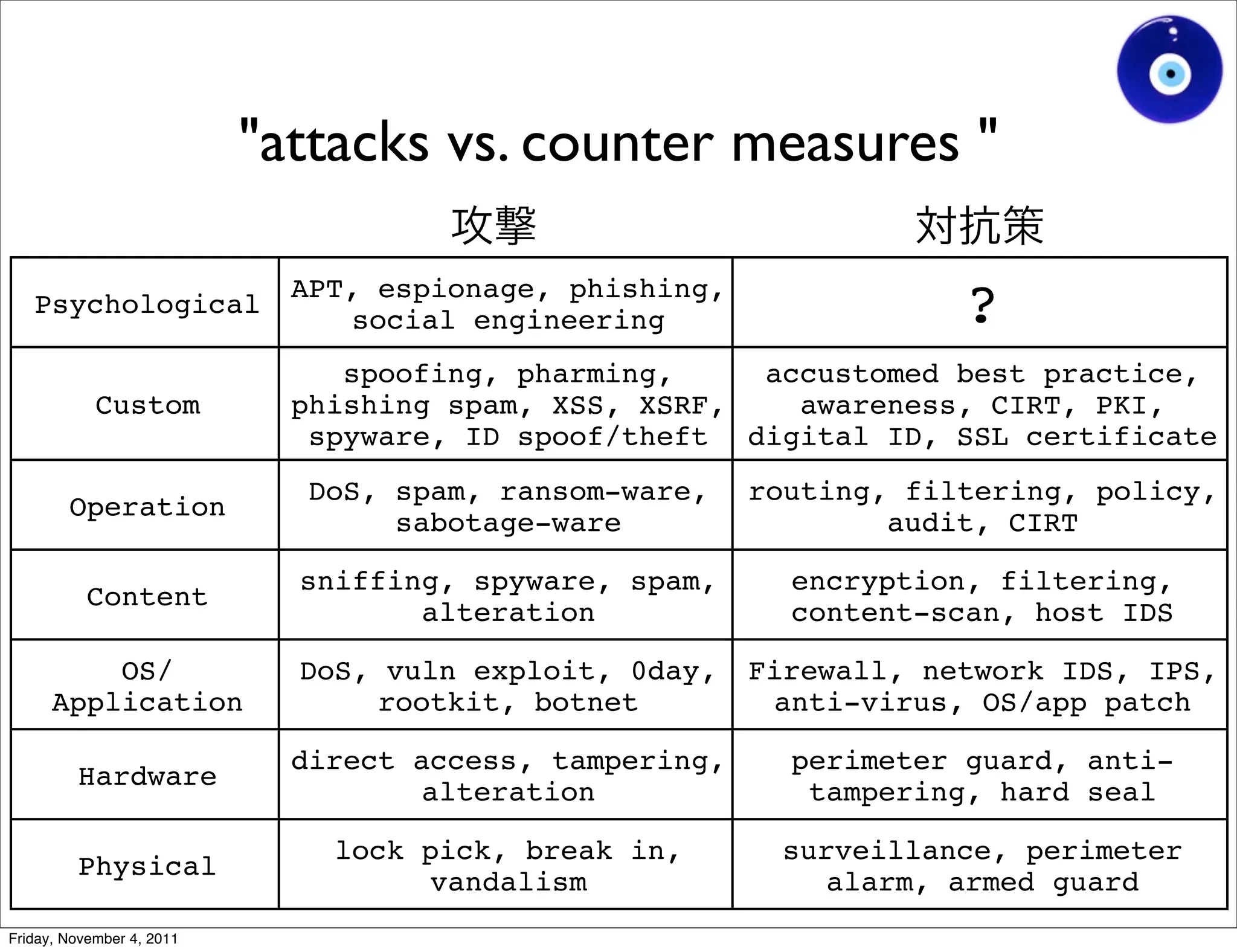
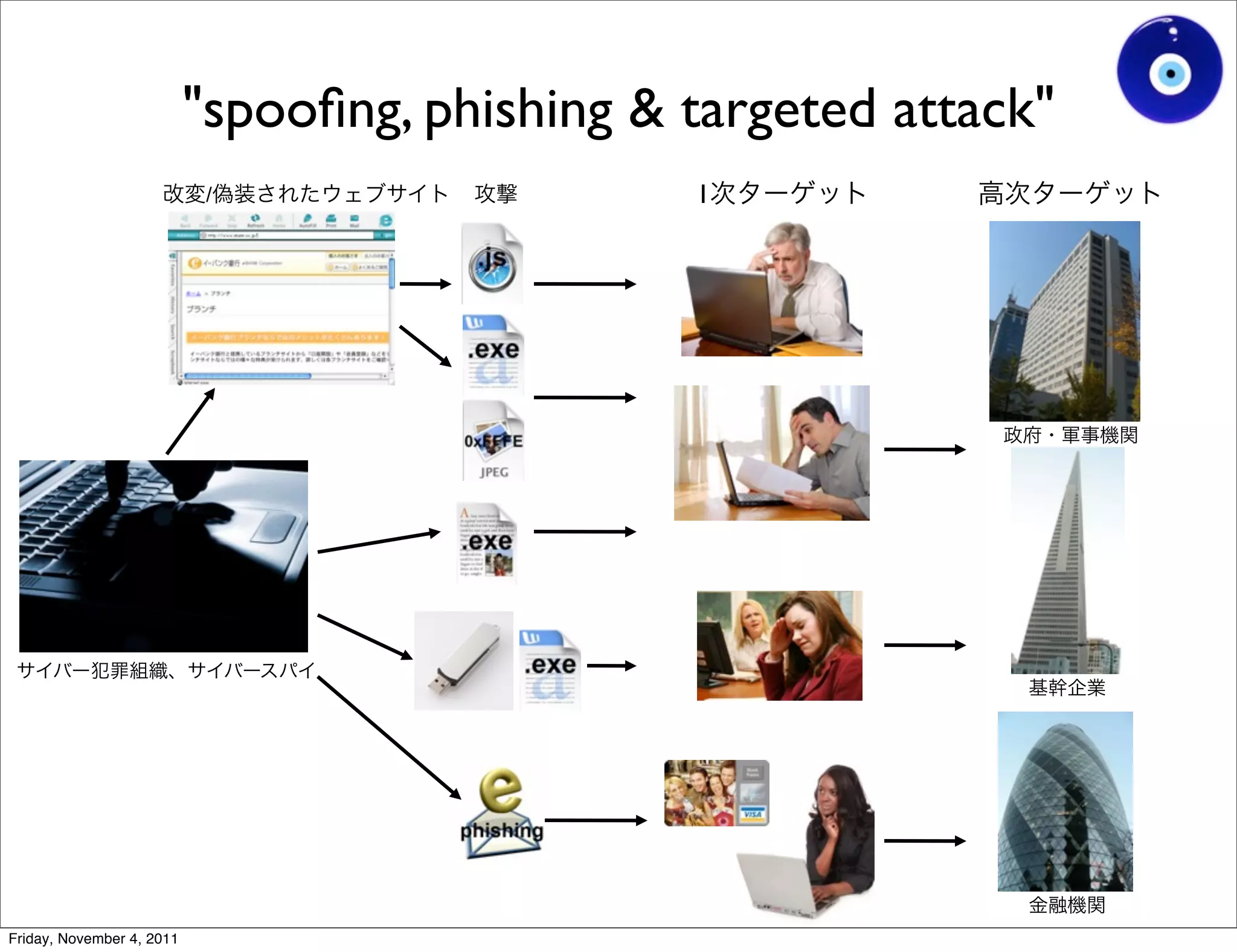
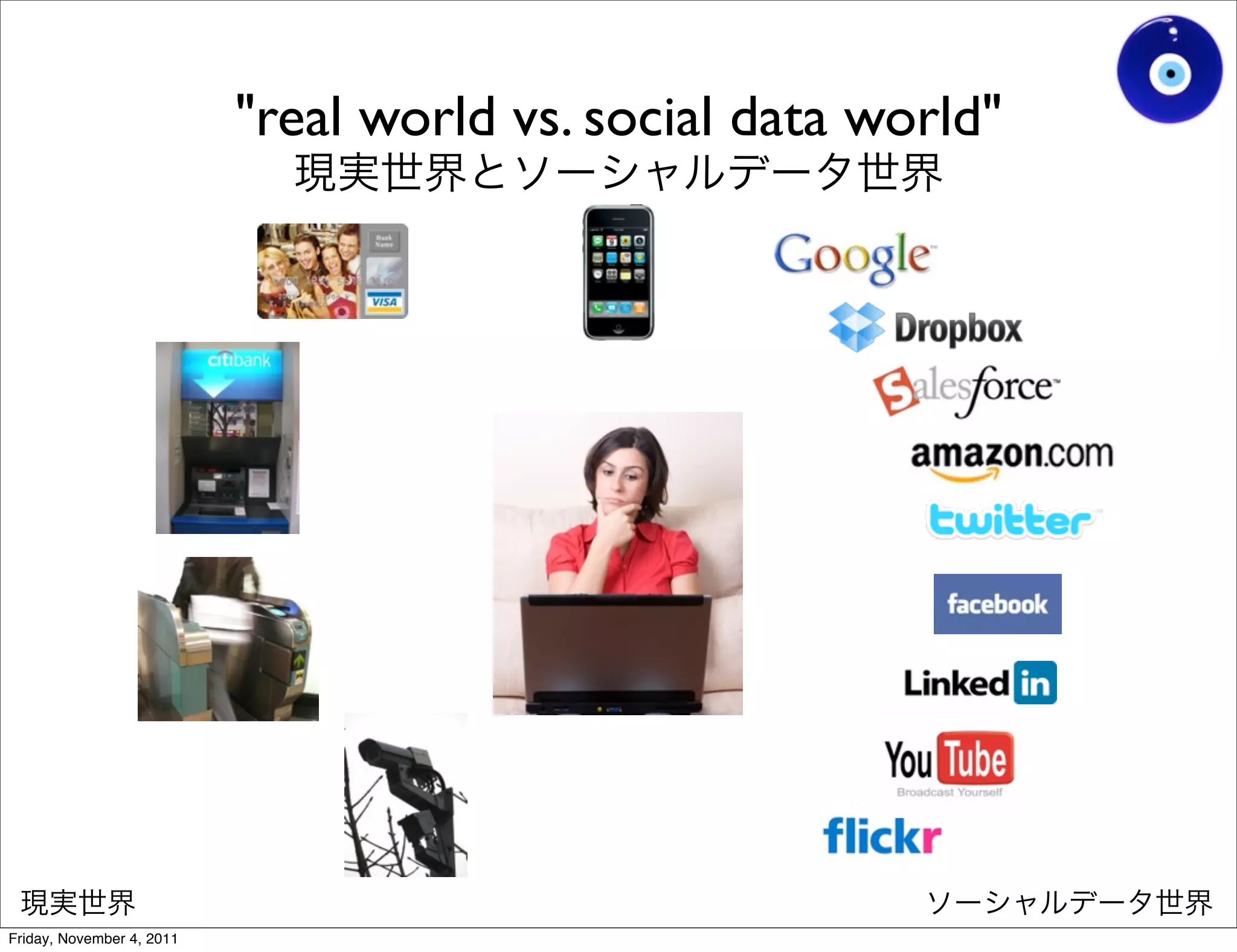
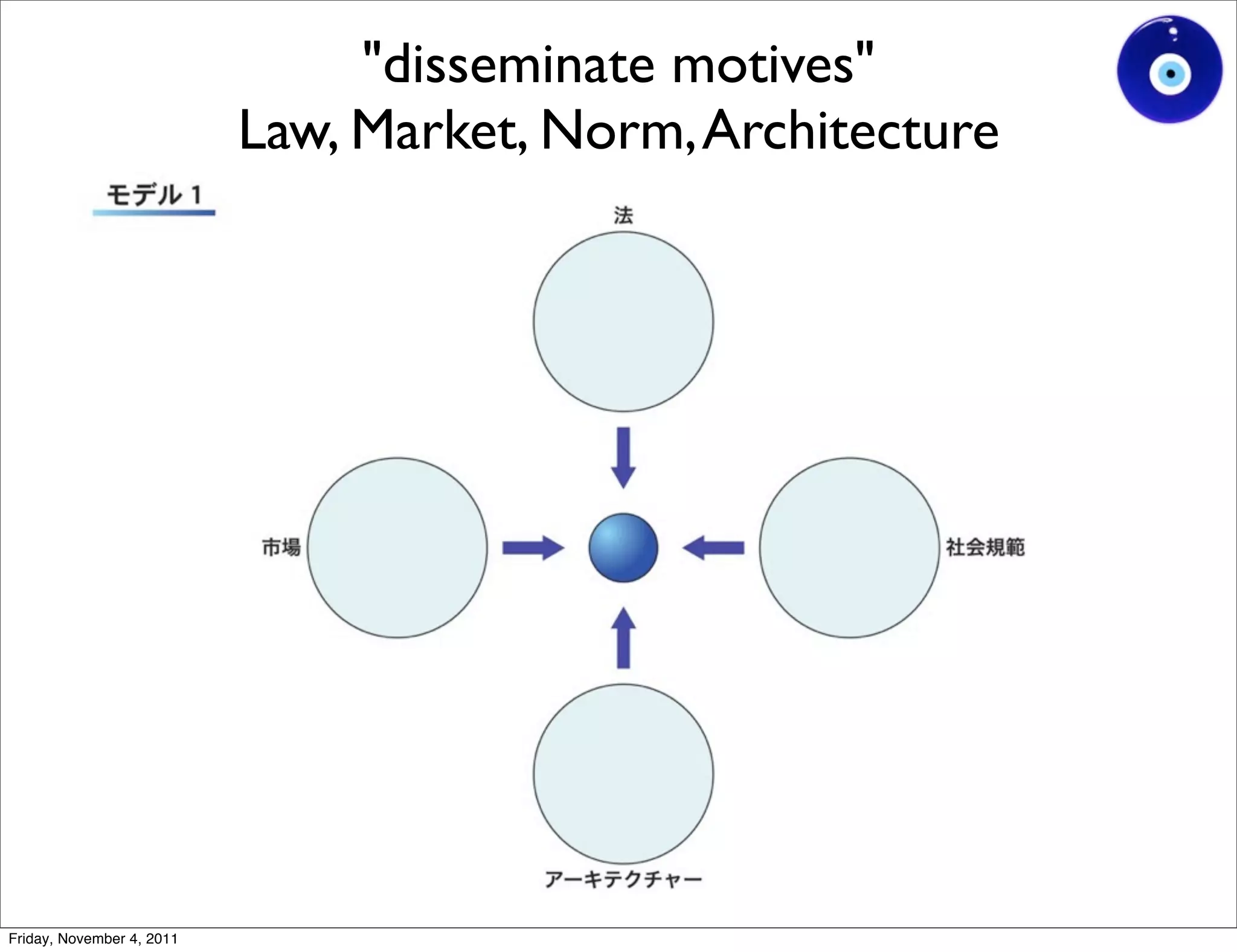
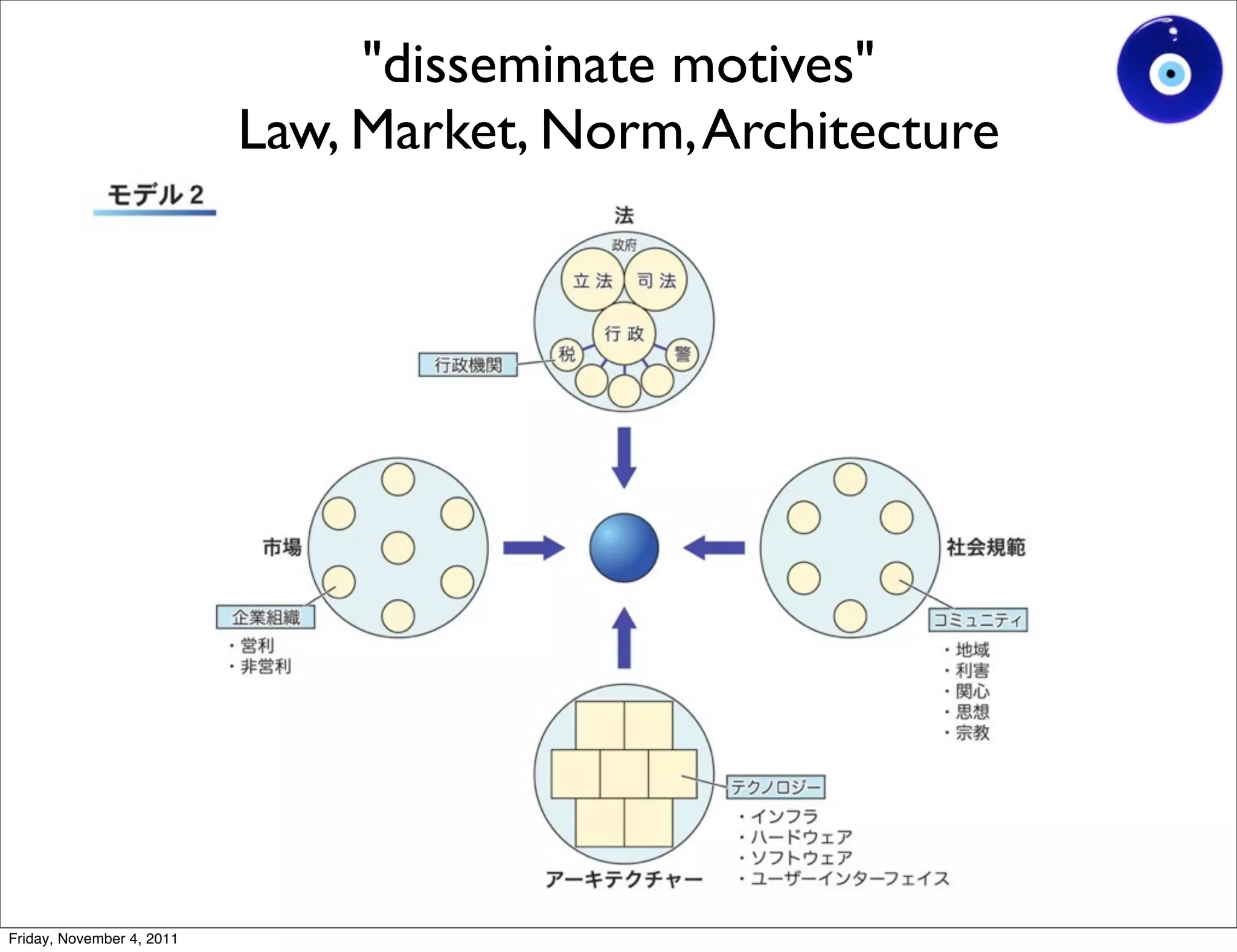
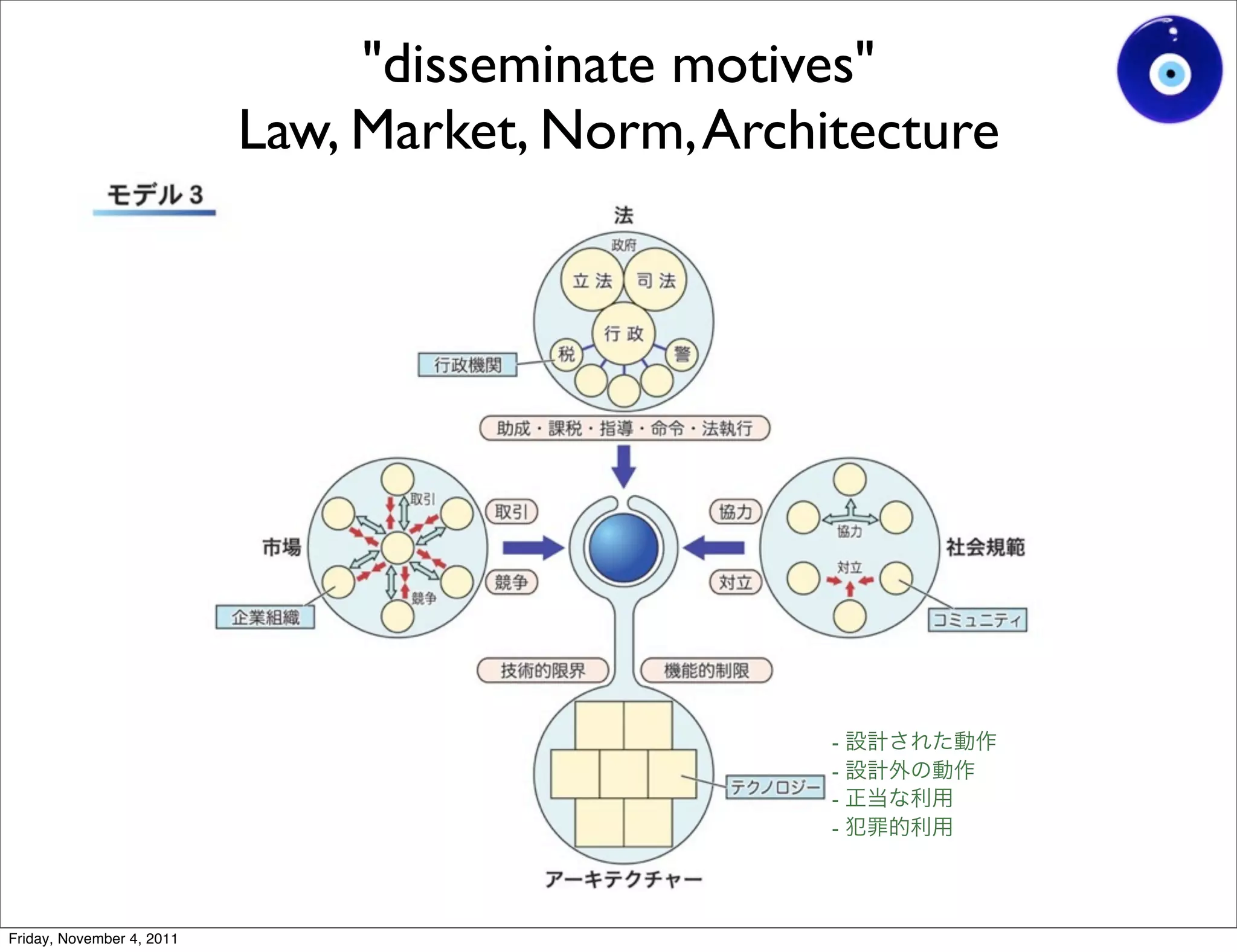
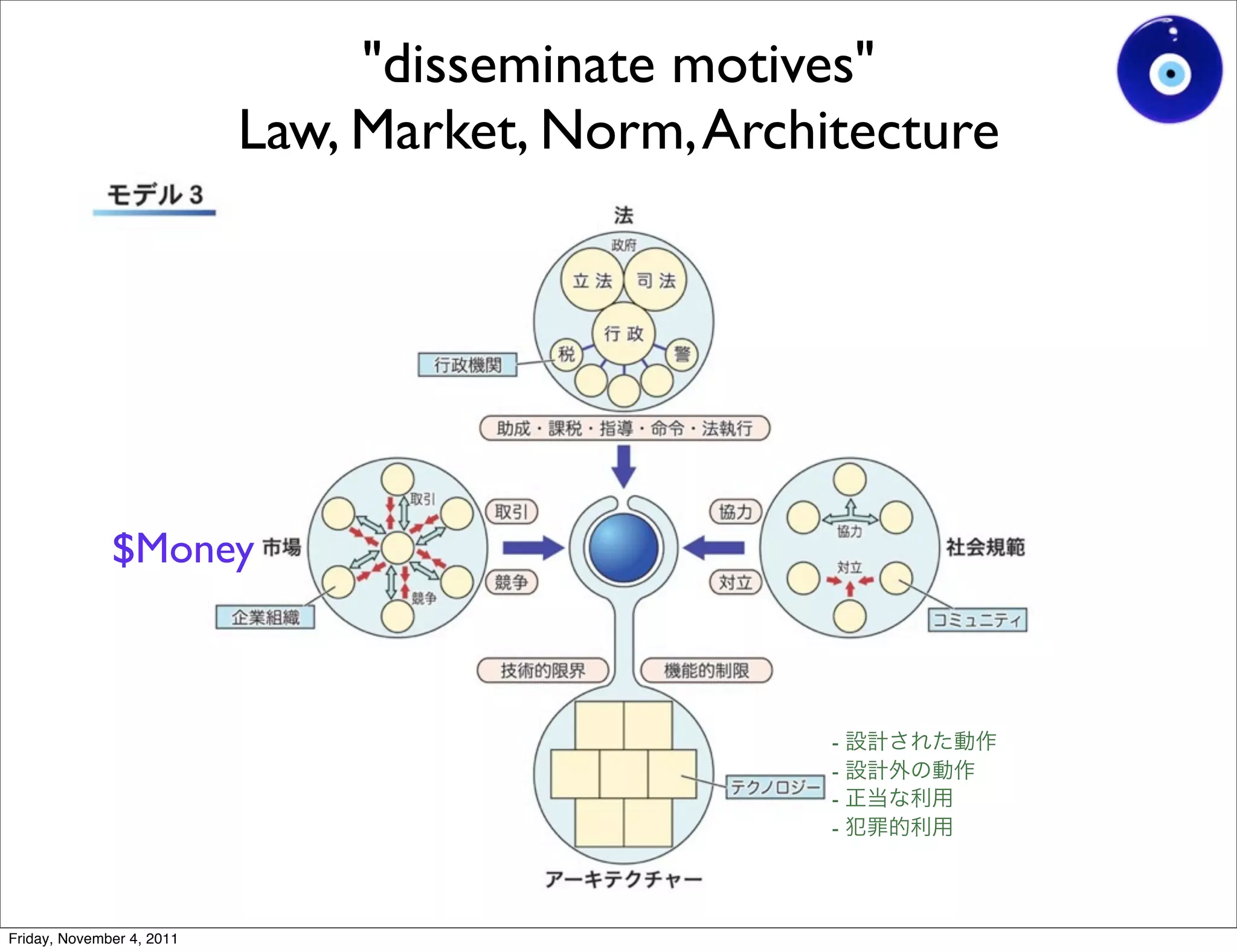
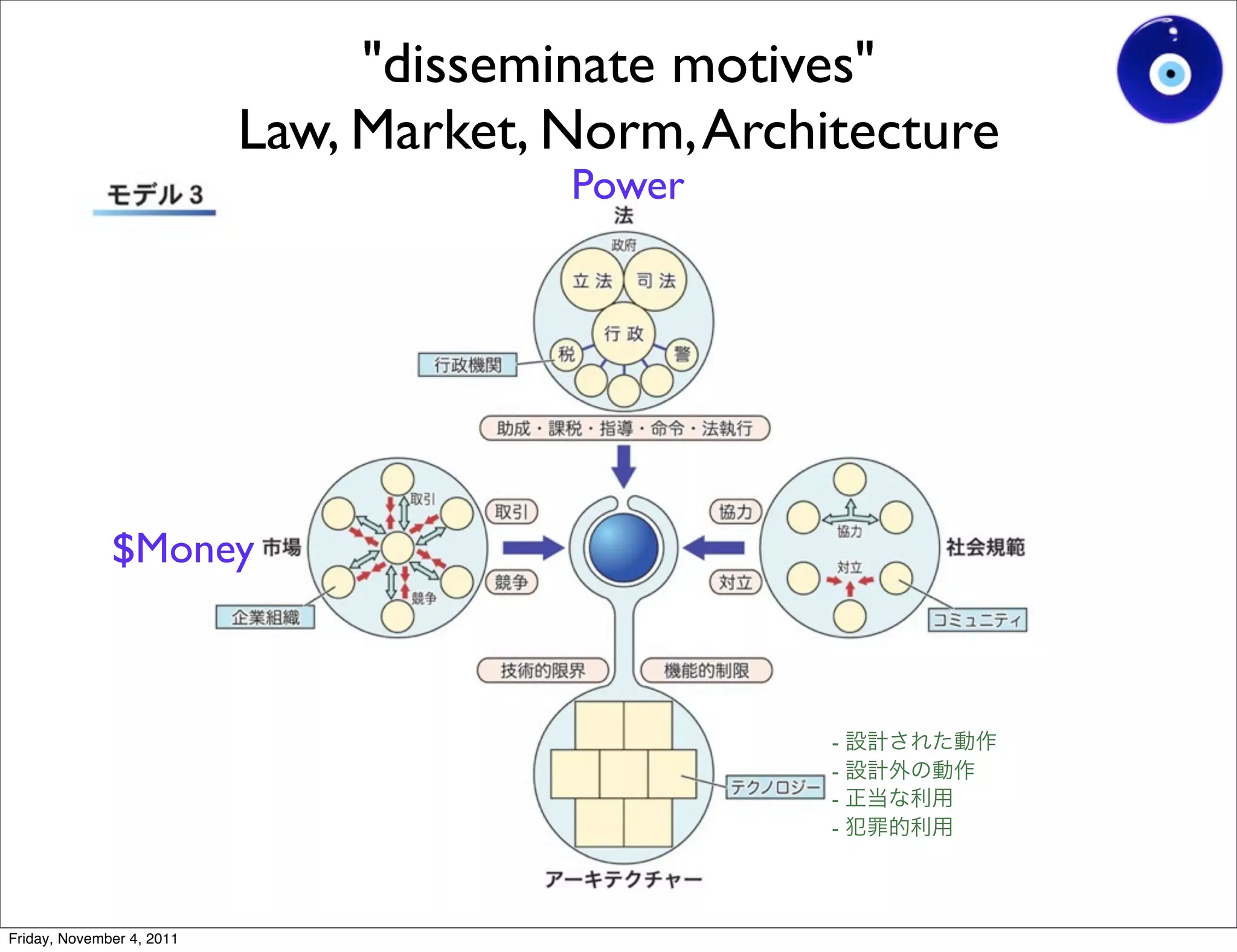
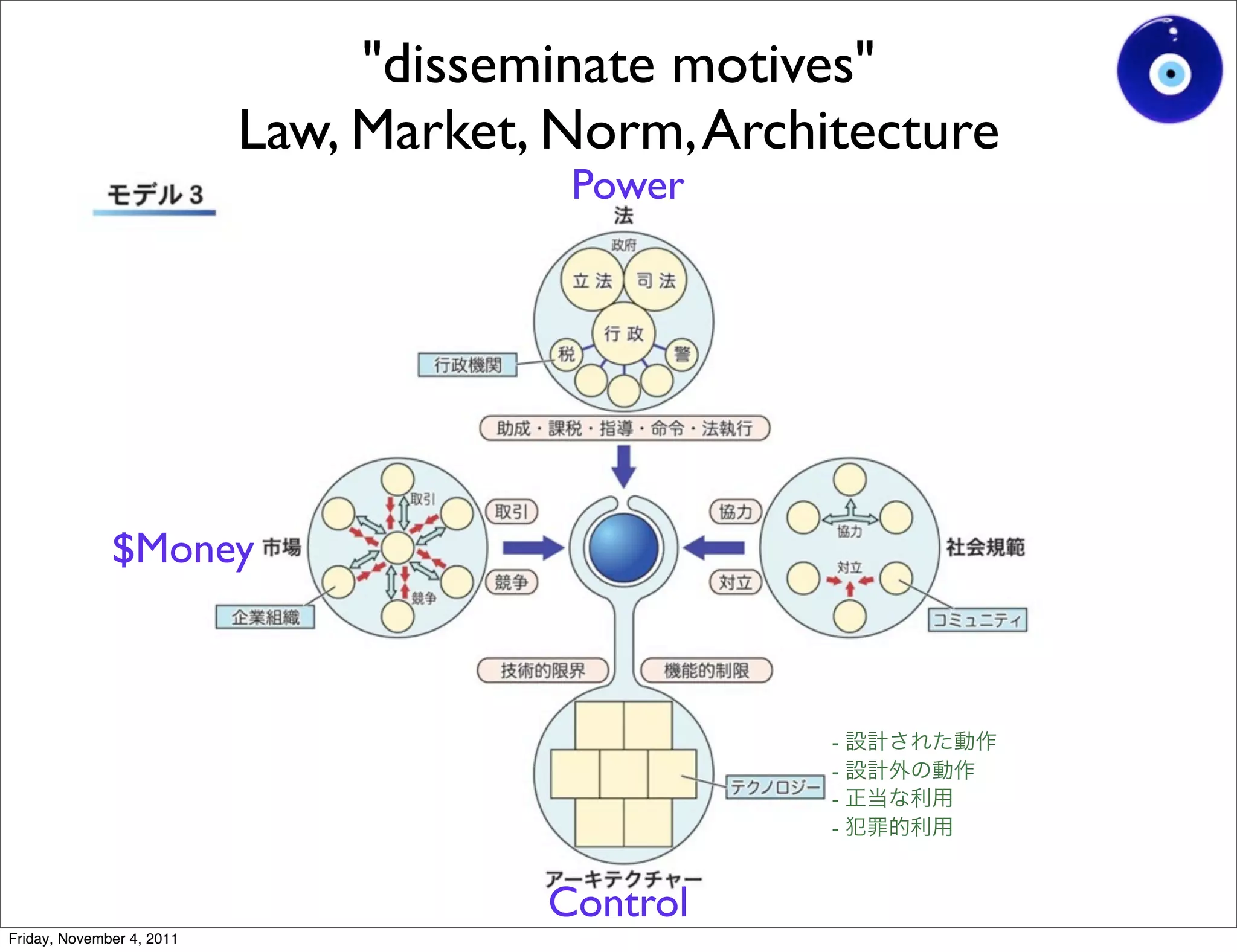
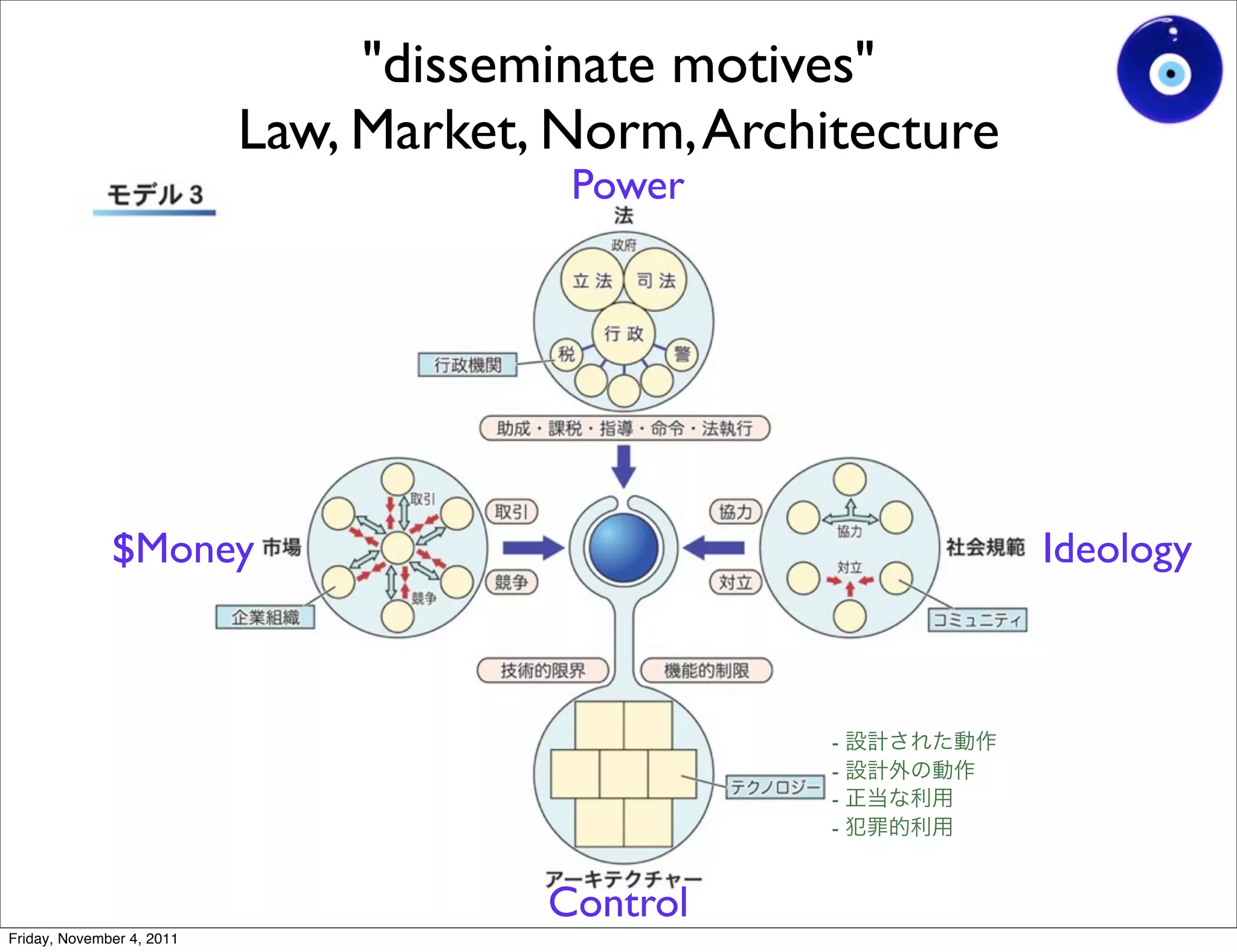
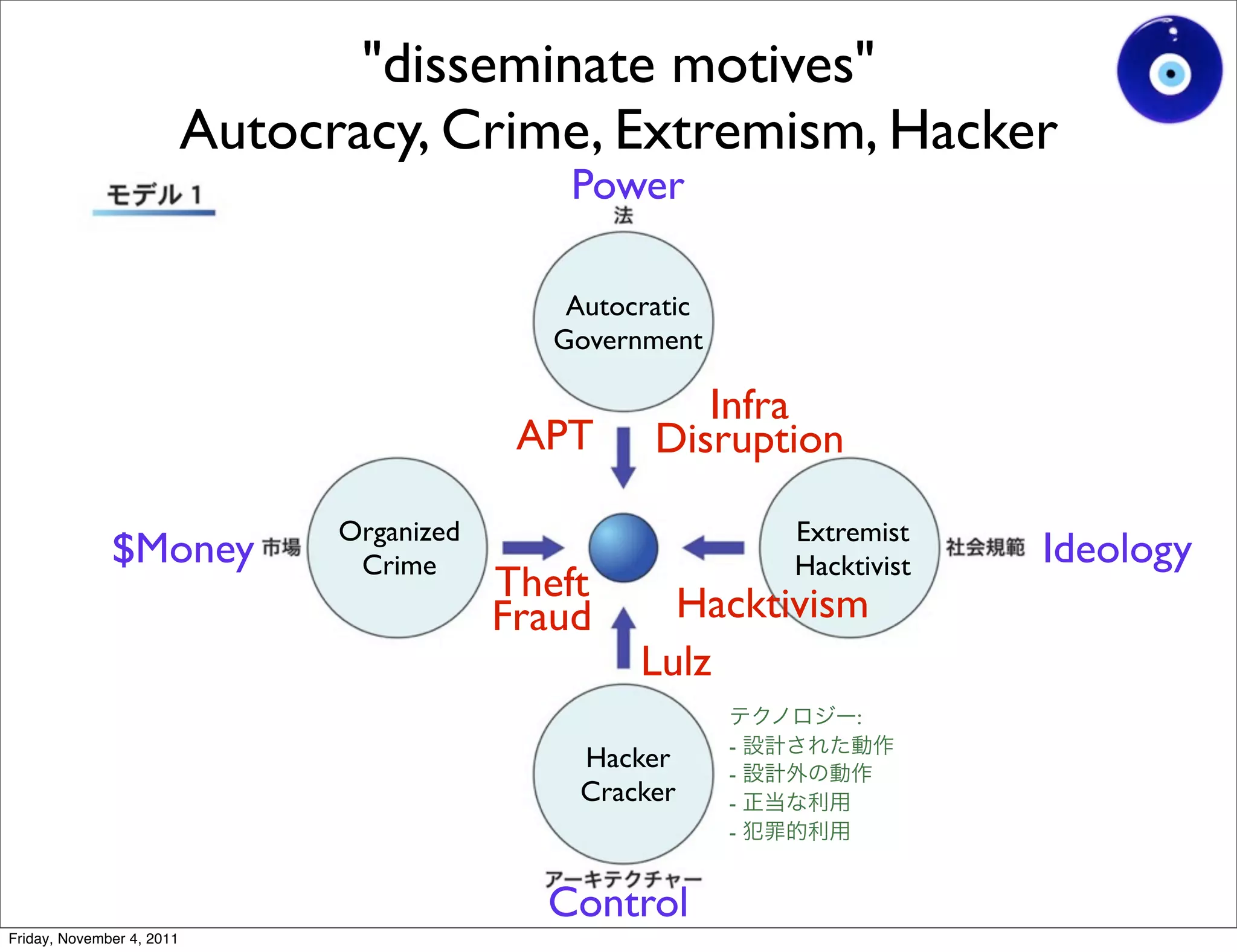
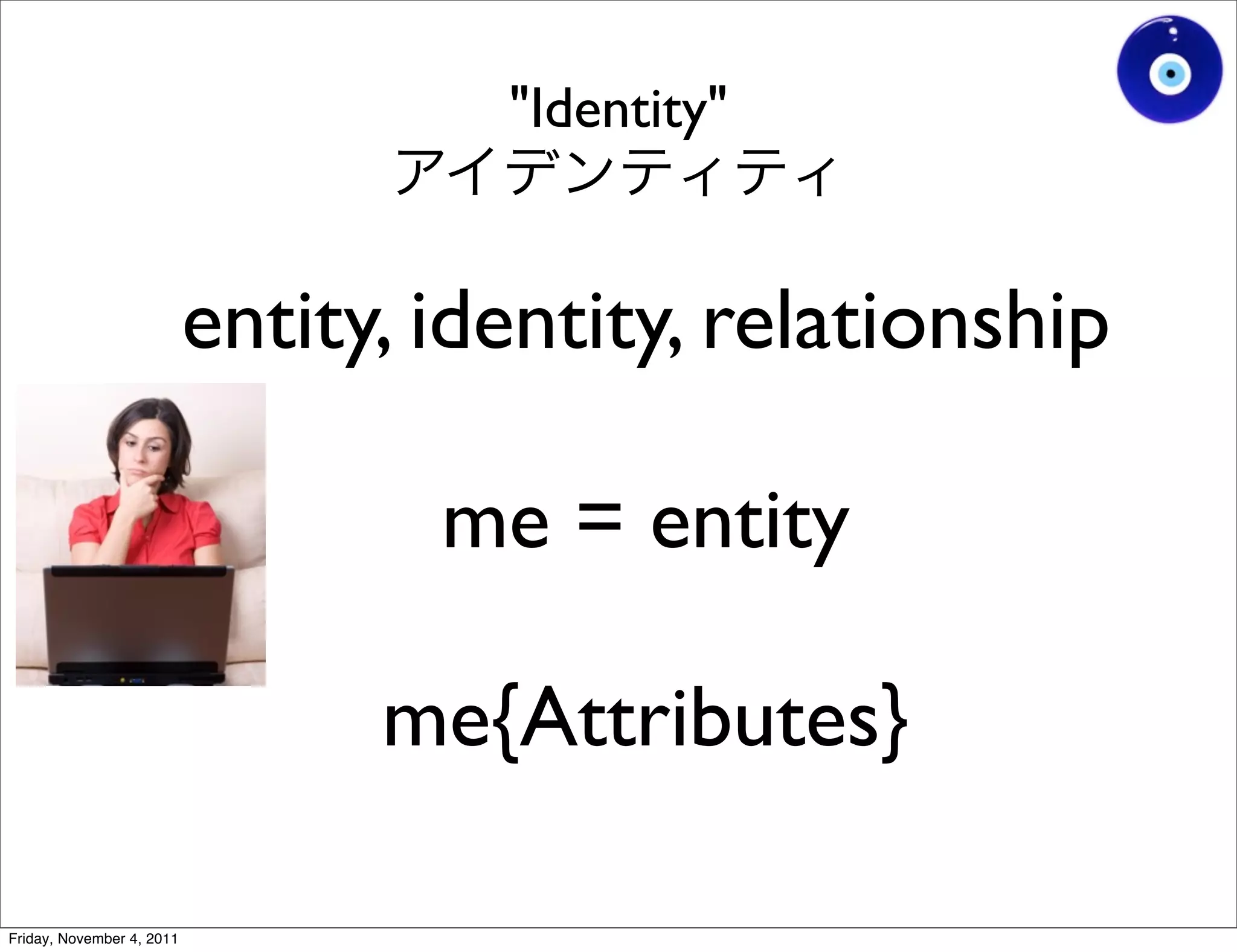
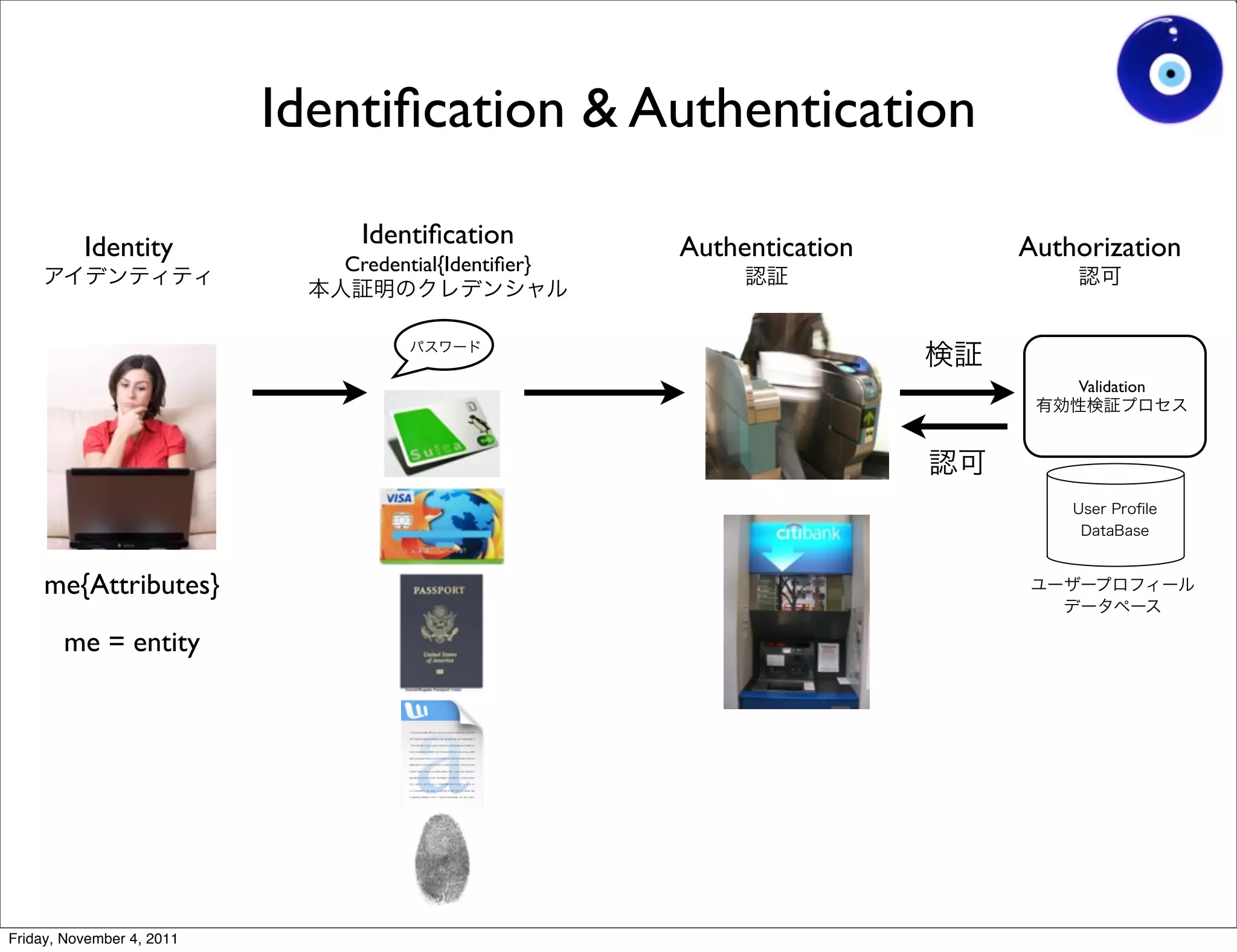
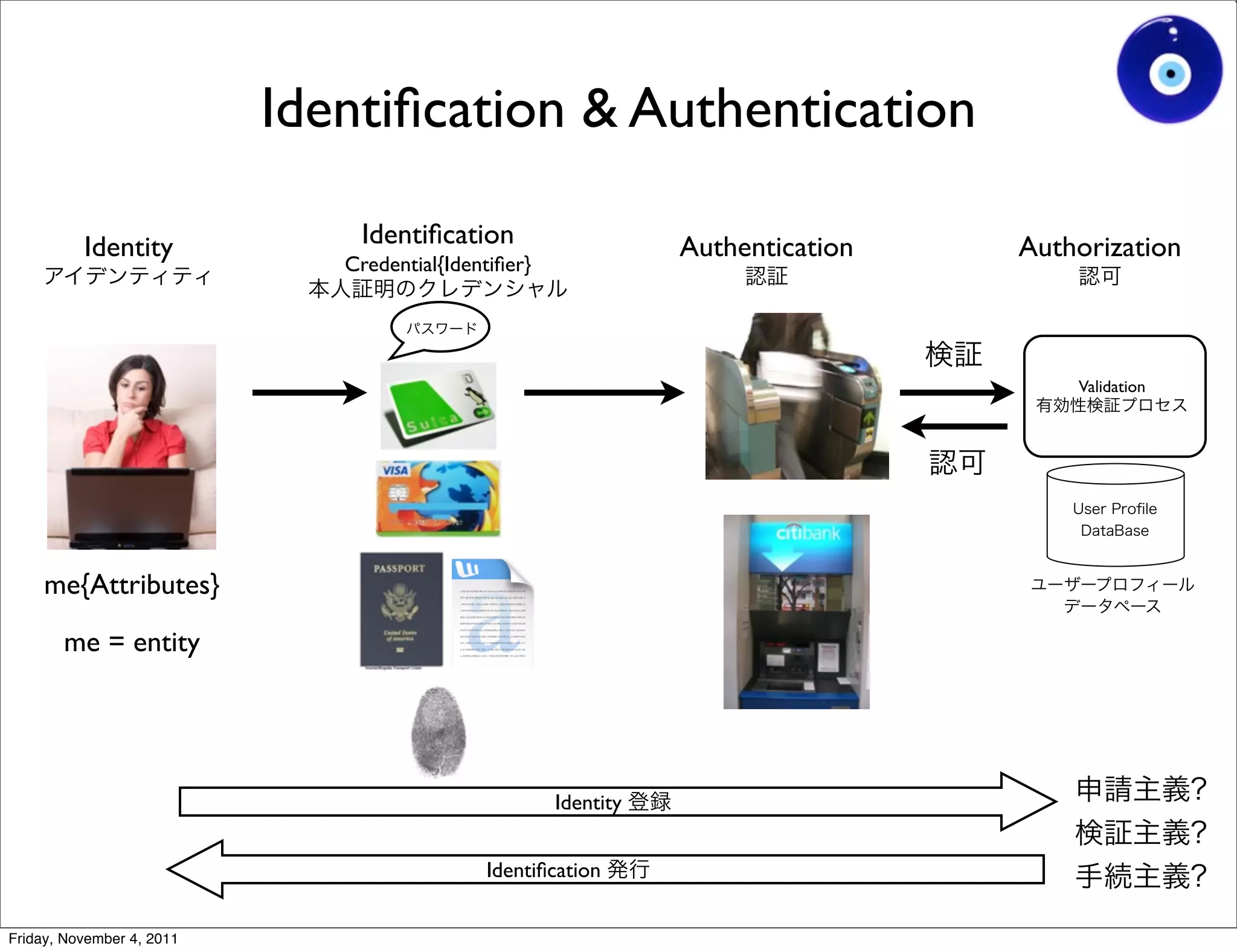
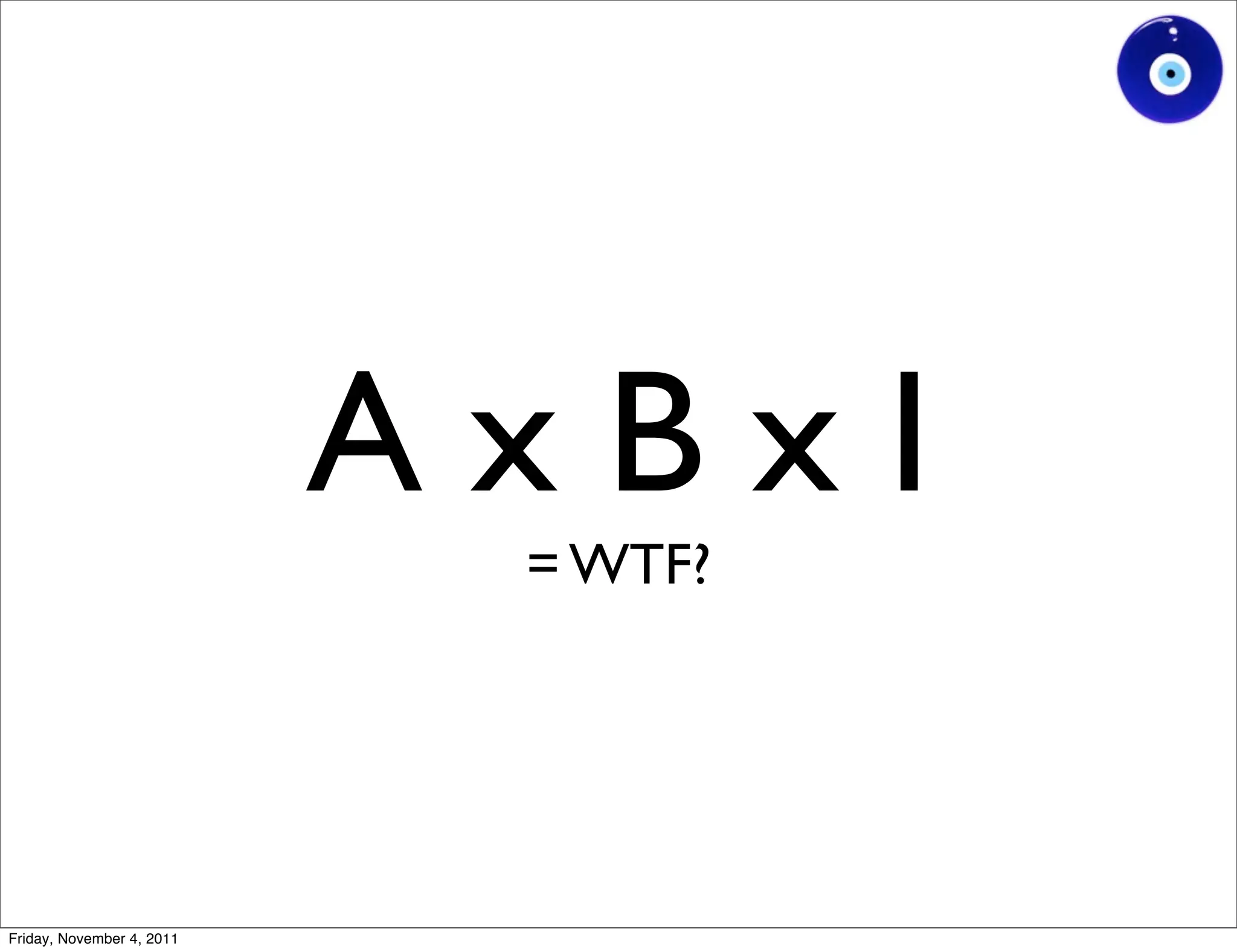The document discusses a presentation given by Gohsuke Takama on November 4, 2011 about cybersecurity topics over the past two years. It covers major cyber attacks like Stuxnet and Operation Aurora, groups like Anonymous and their tactics. It also discusses emerging attack techniques, security defense approaches, and the relationship between online and real-world identities.