Embed presentation
Downloaded 13 times

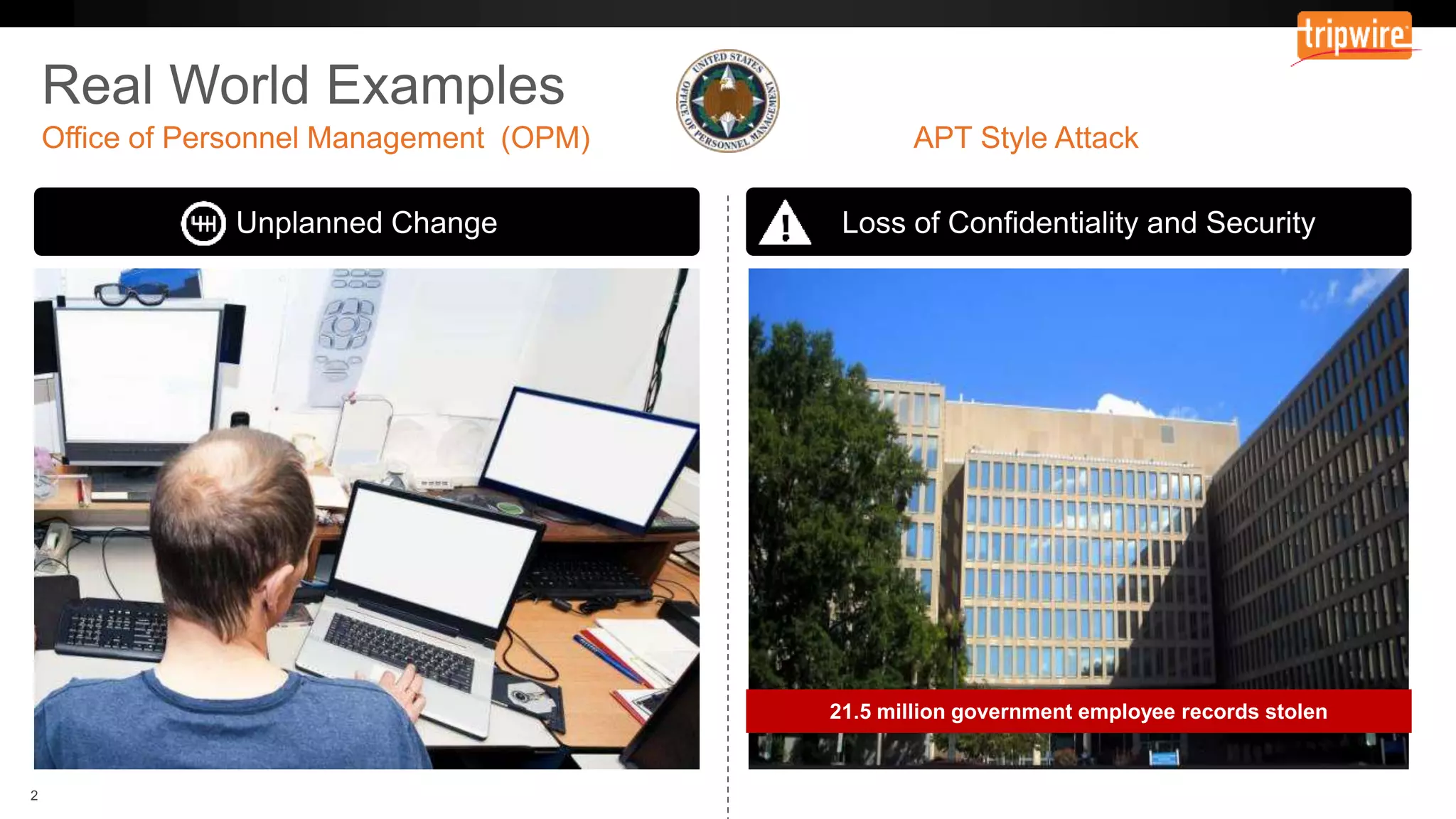
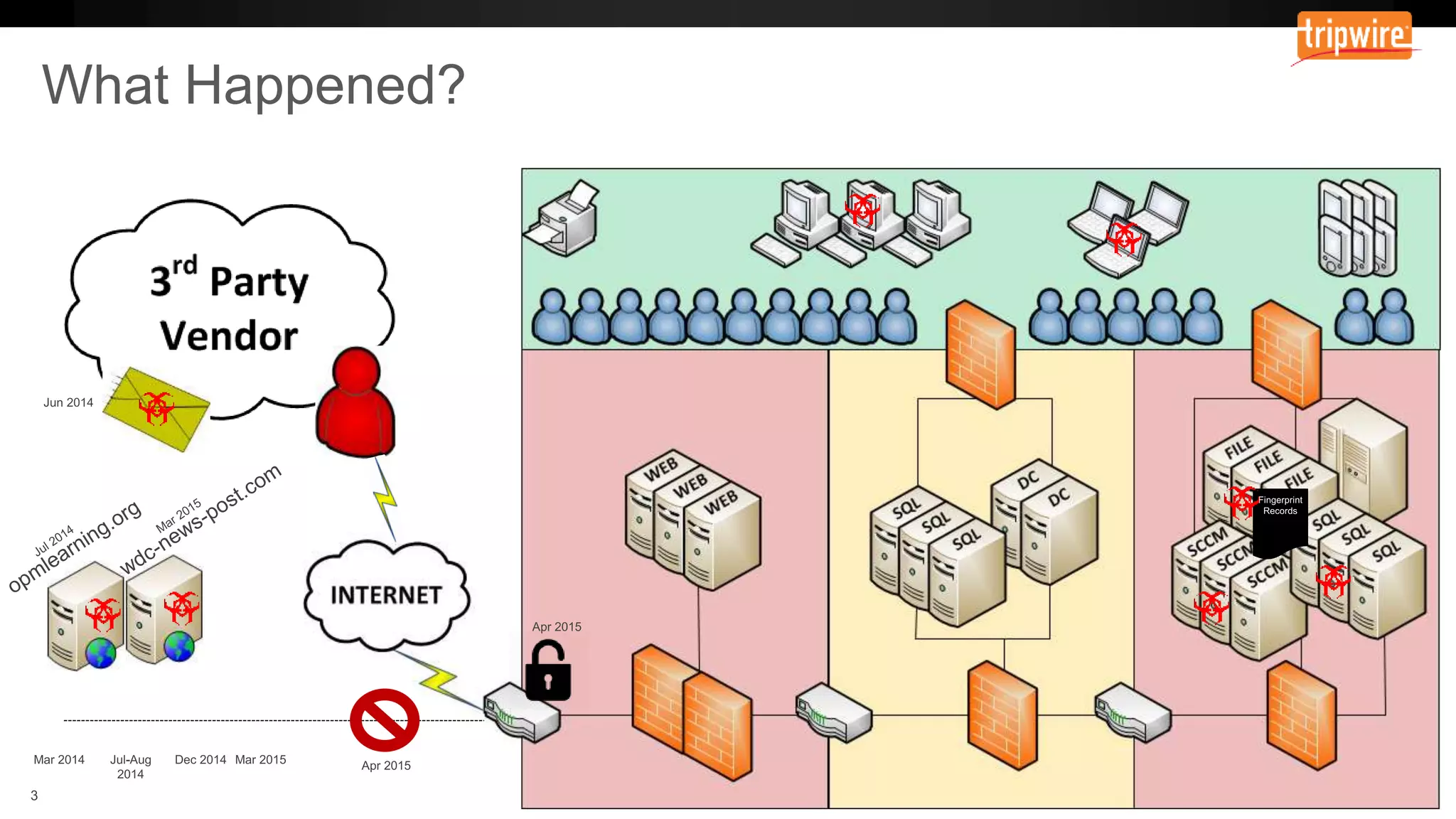
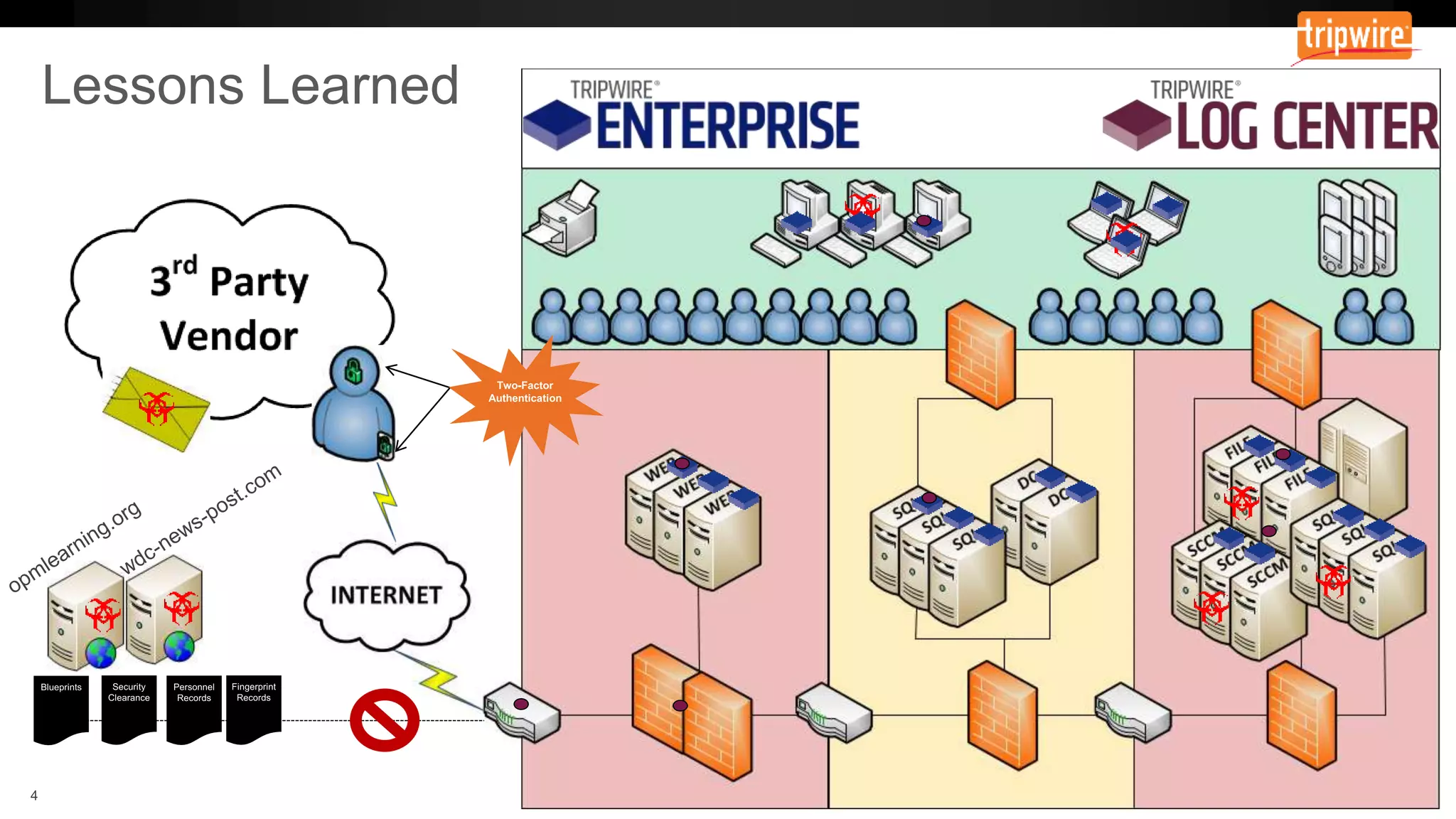
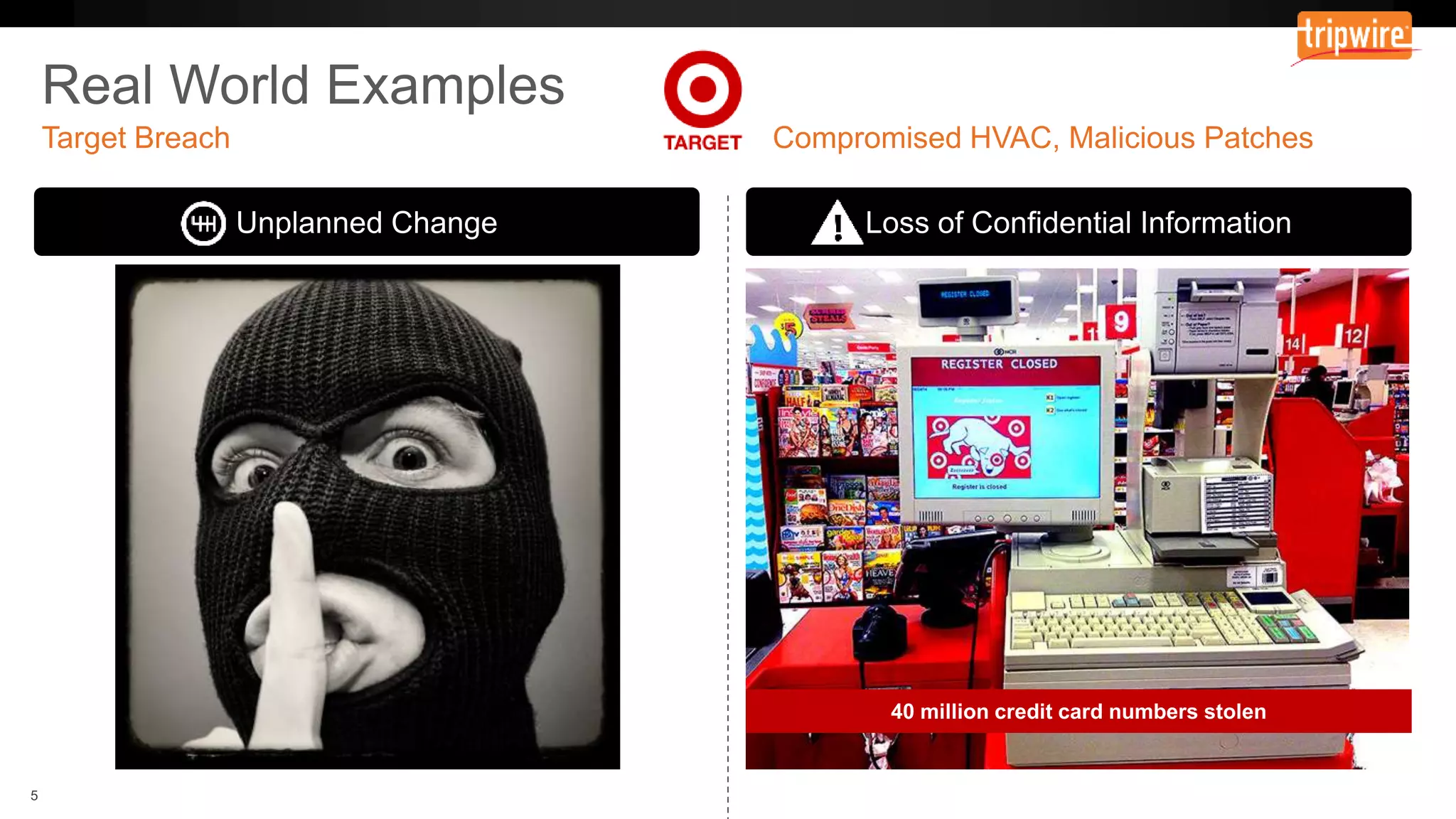
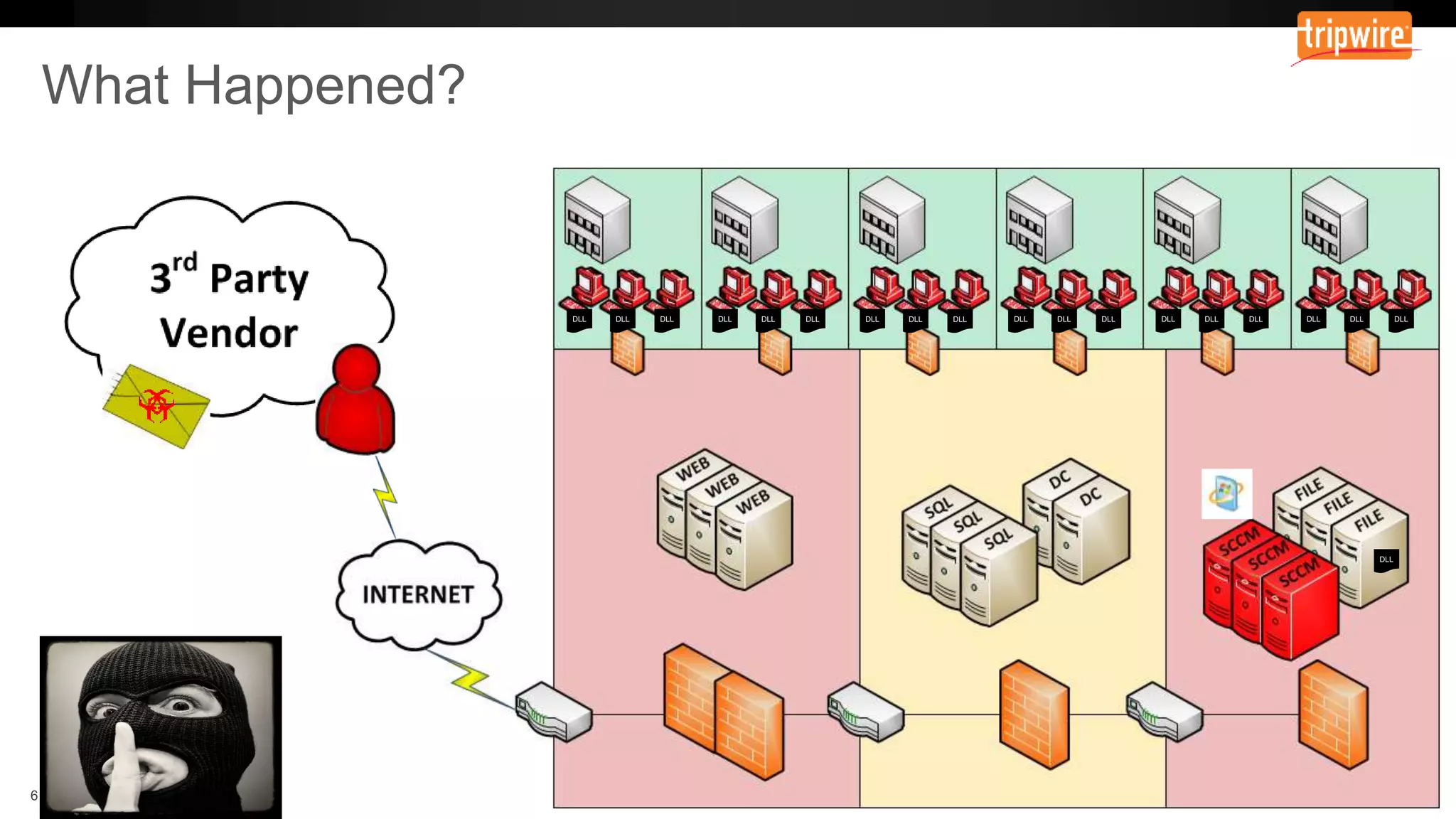
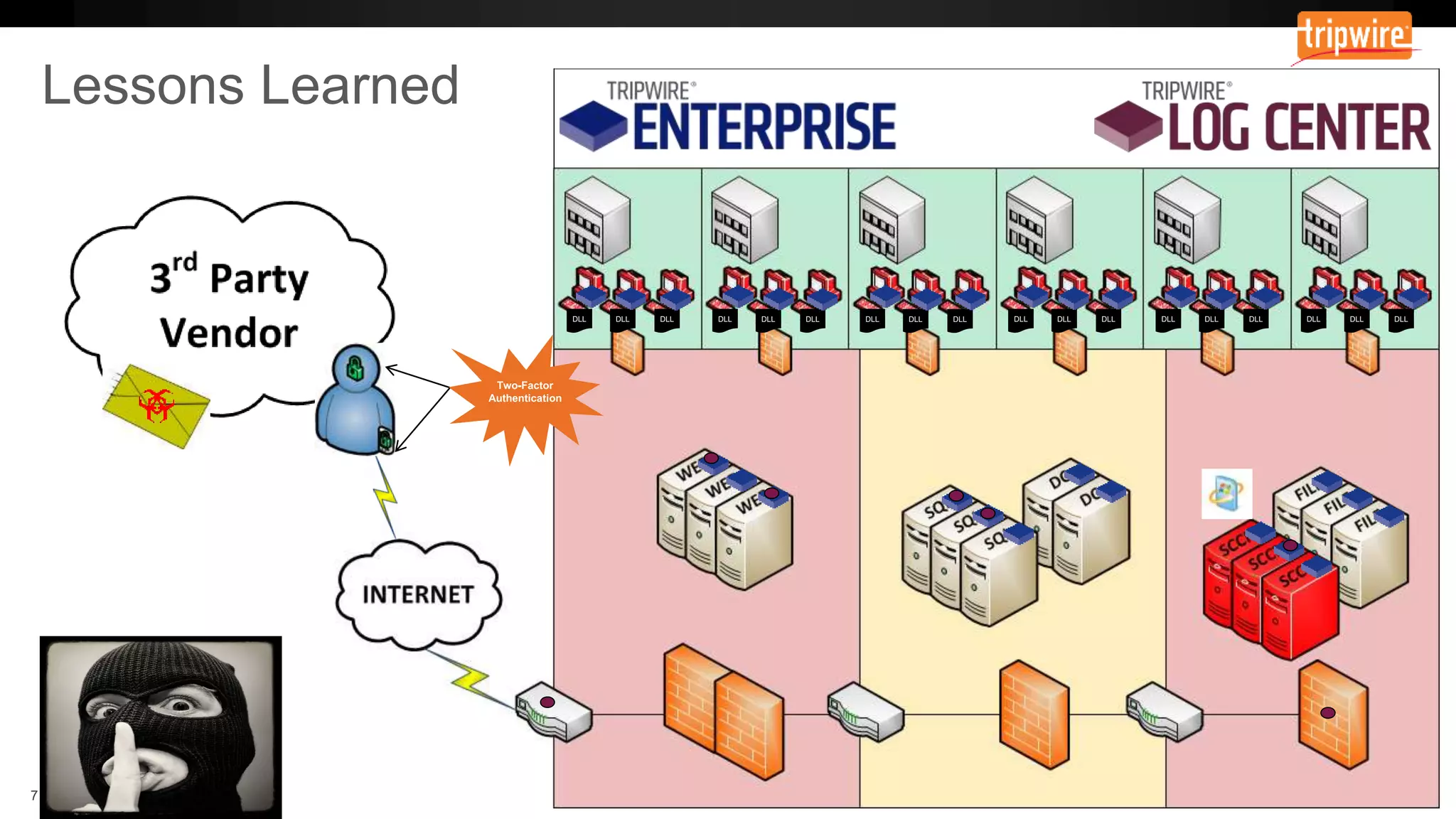
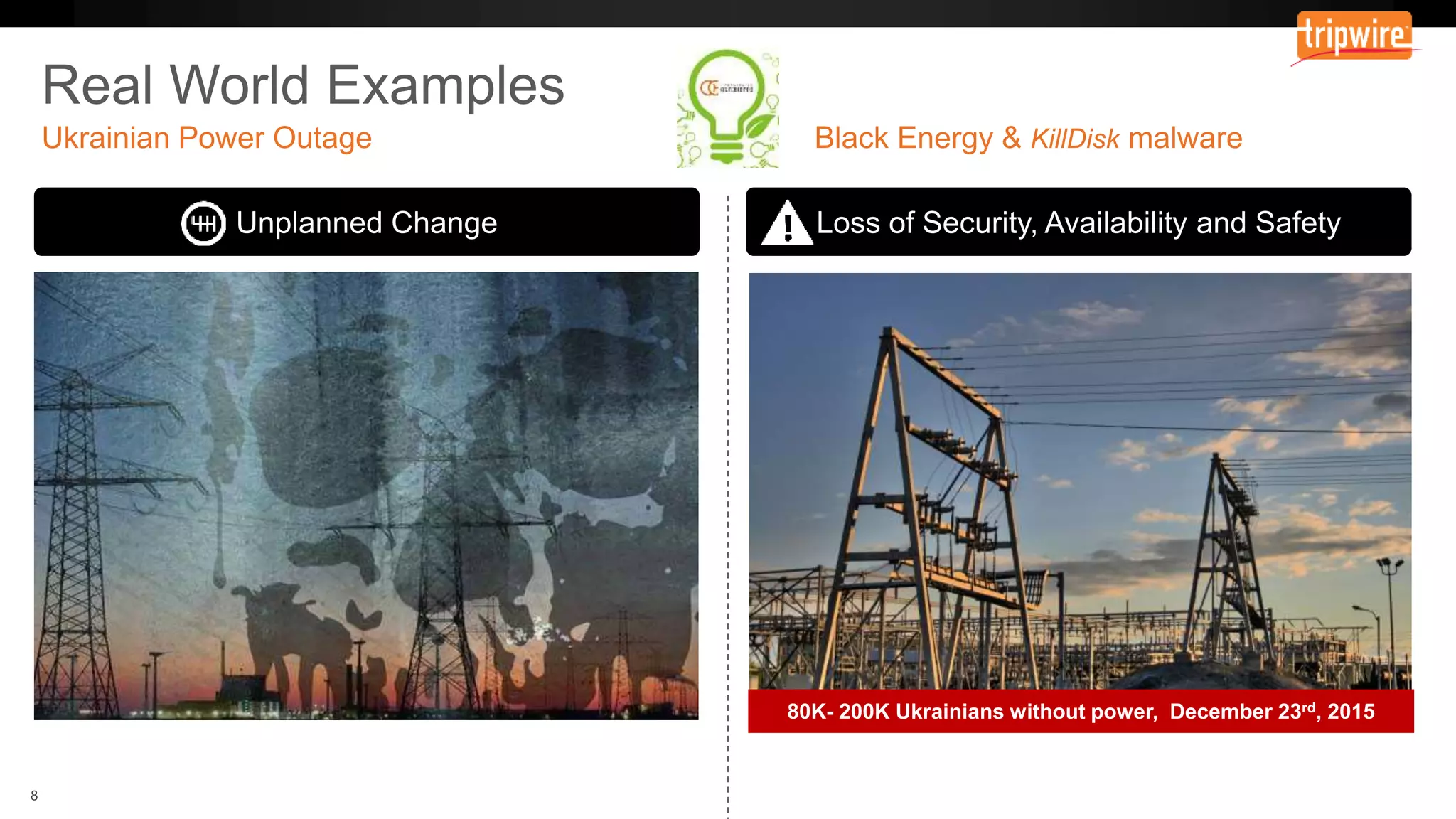
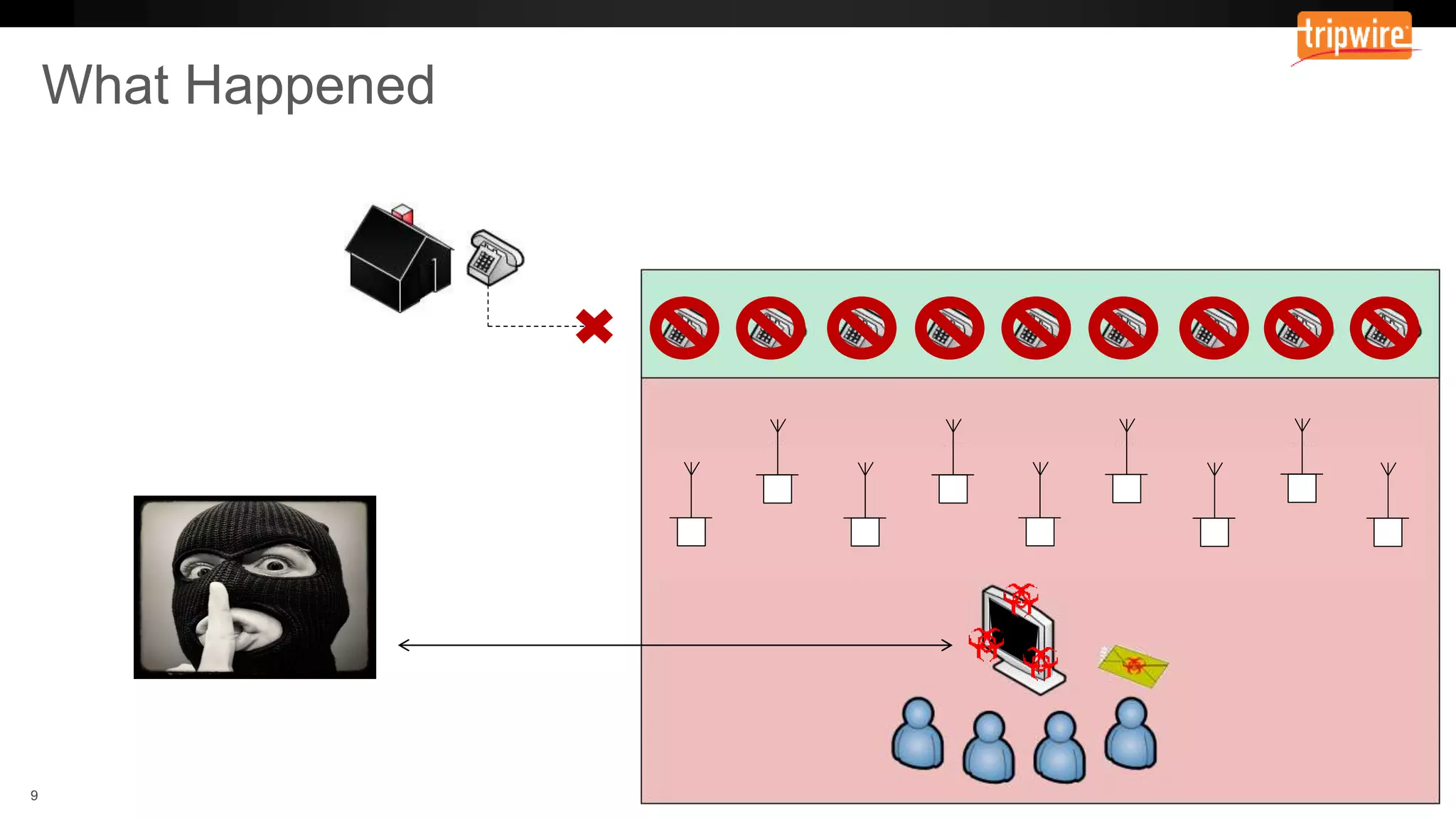
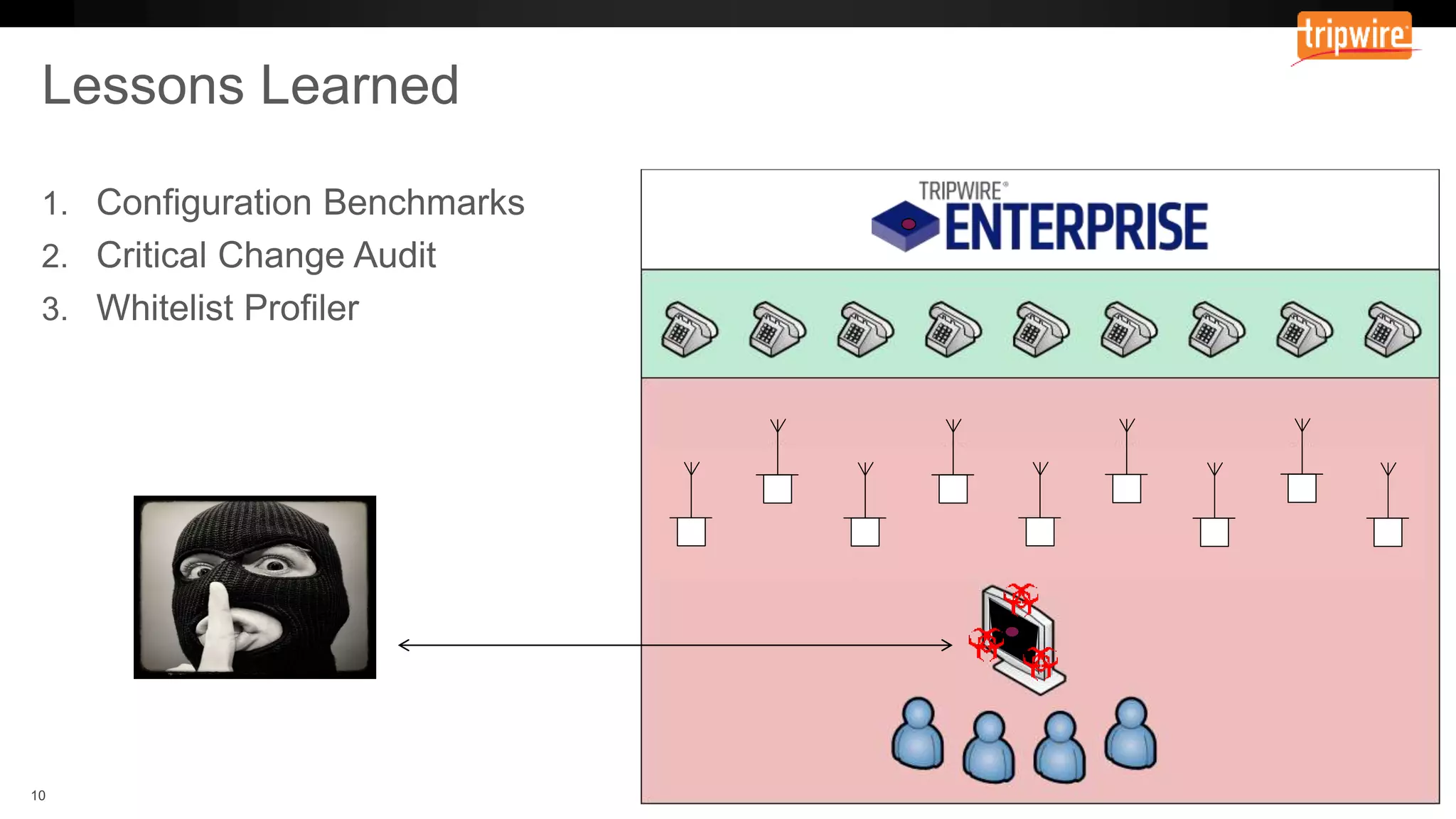

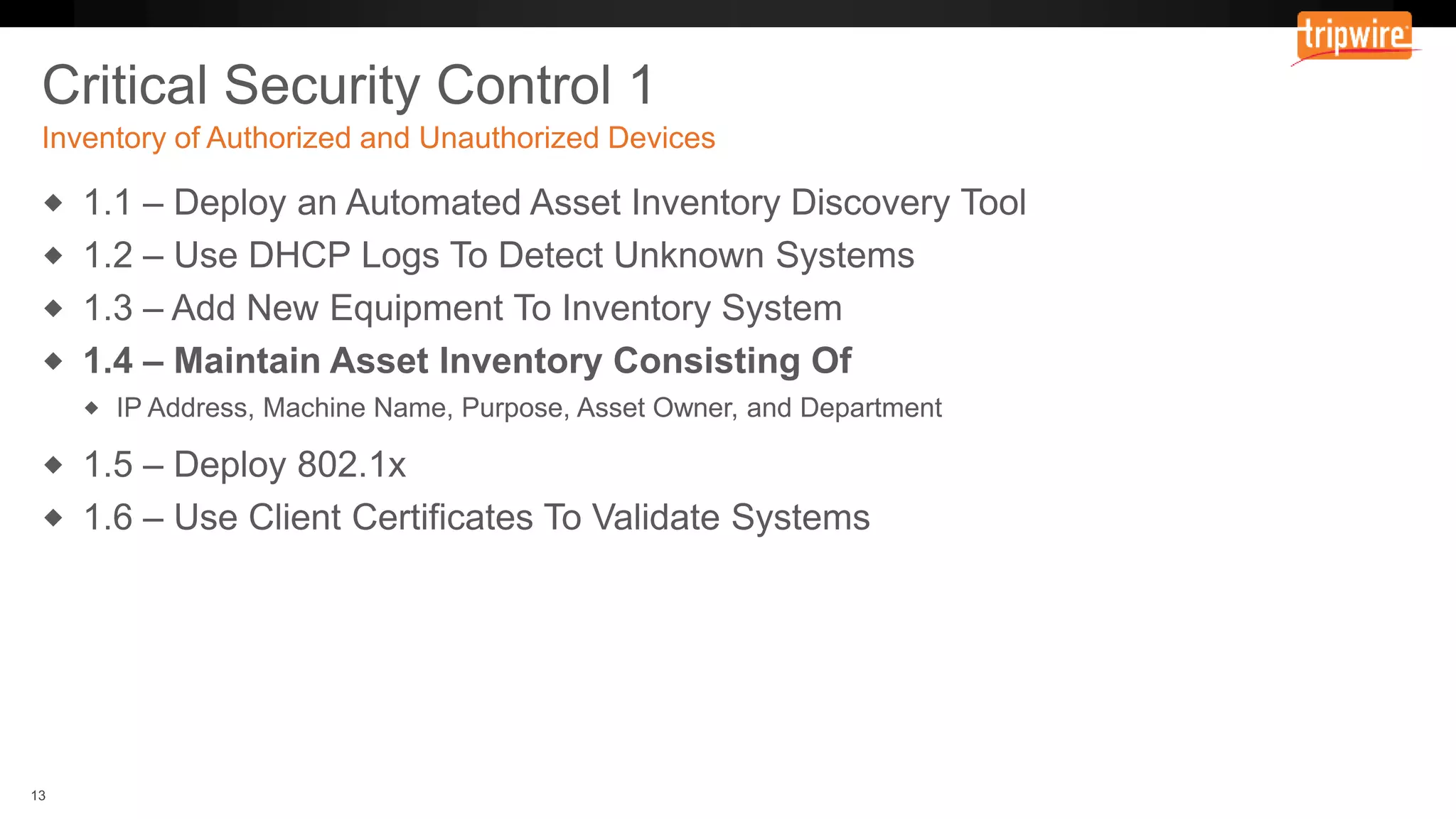
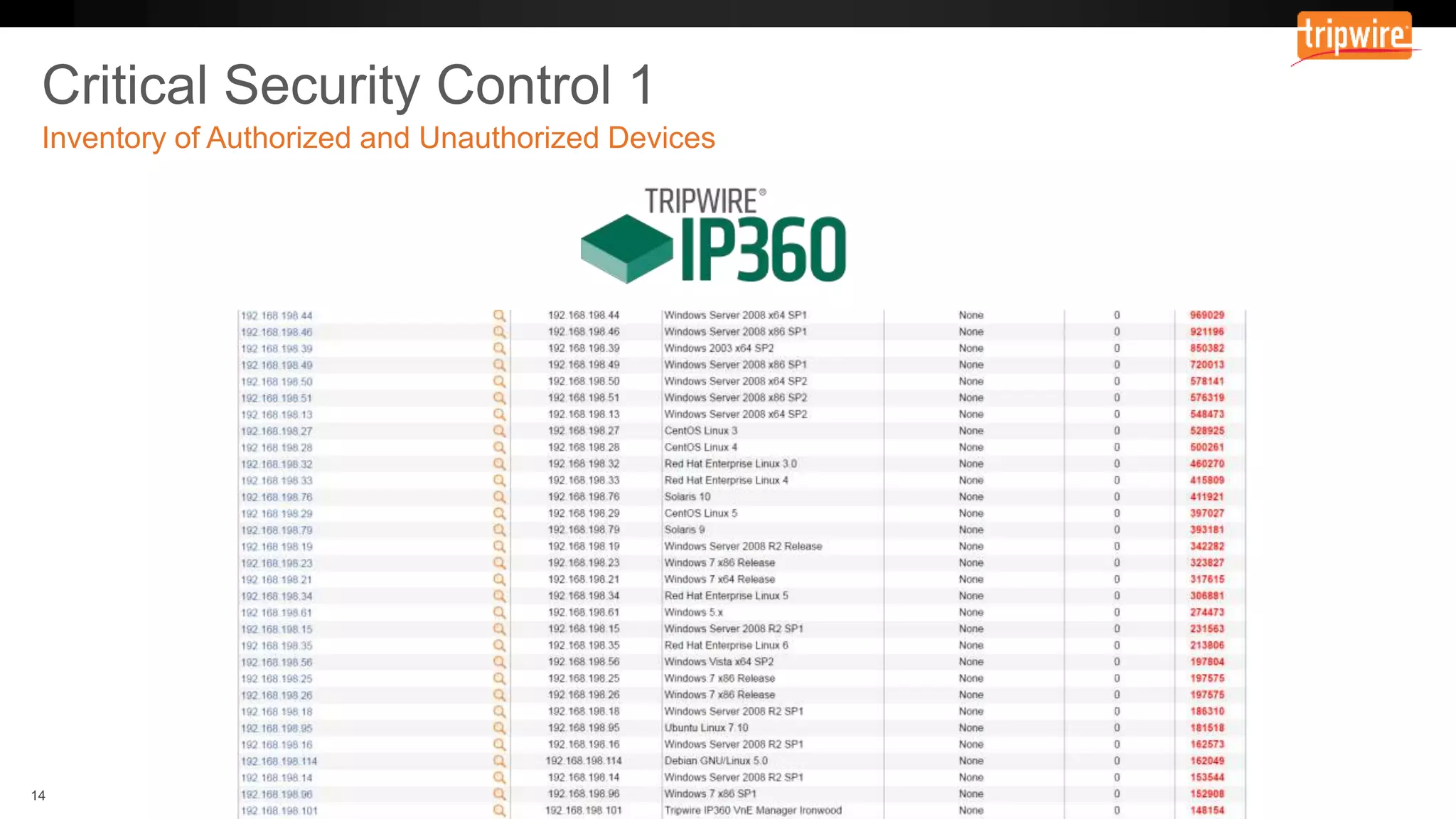
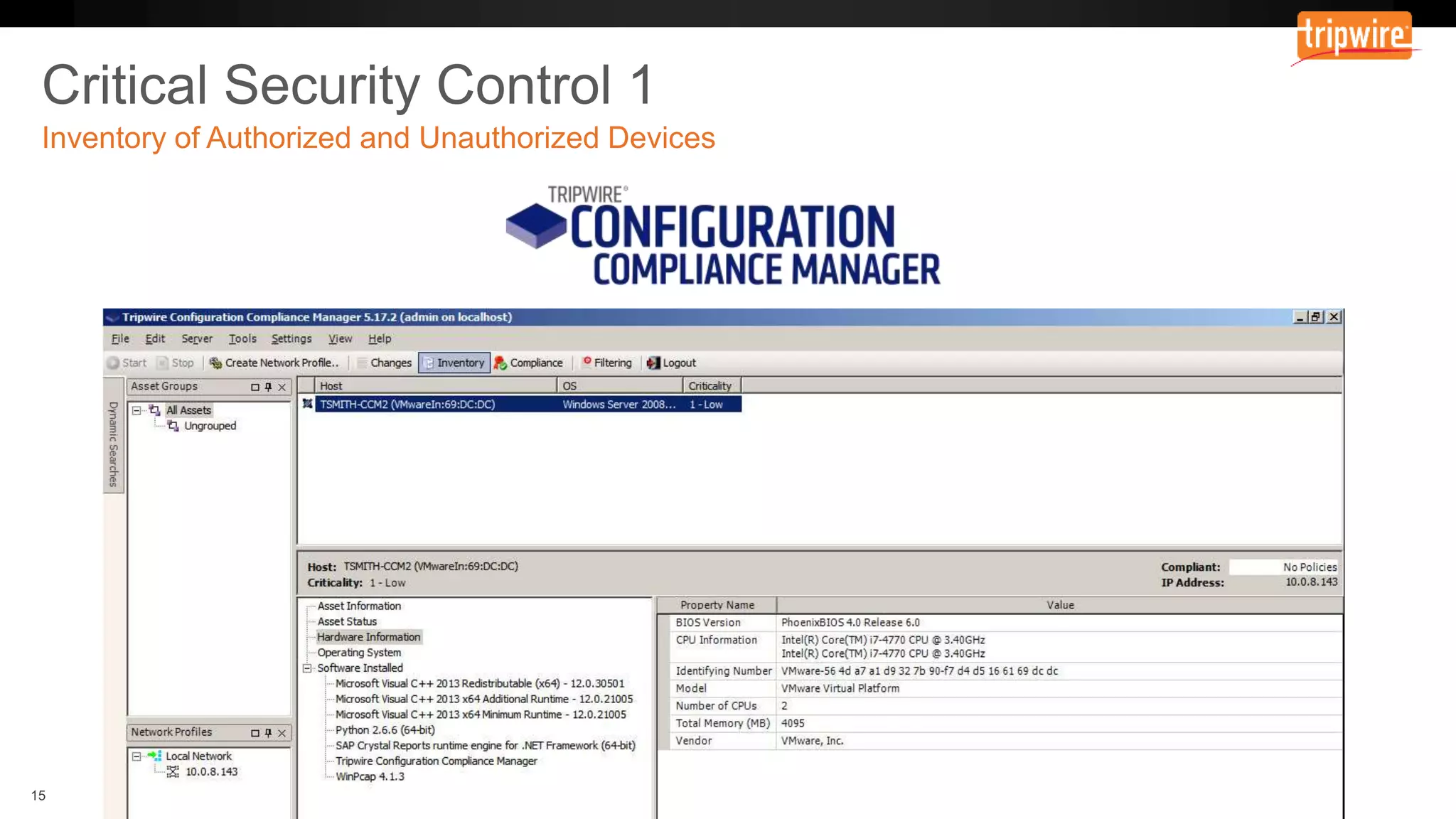
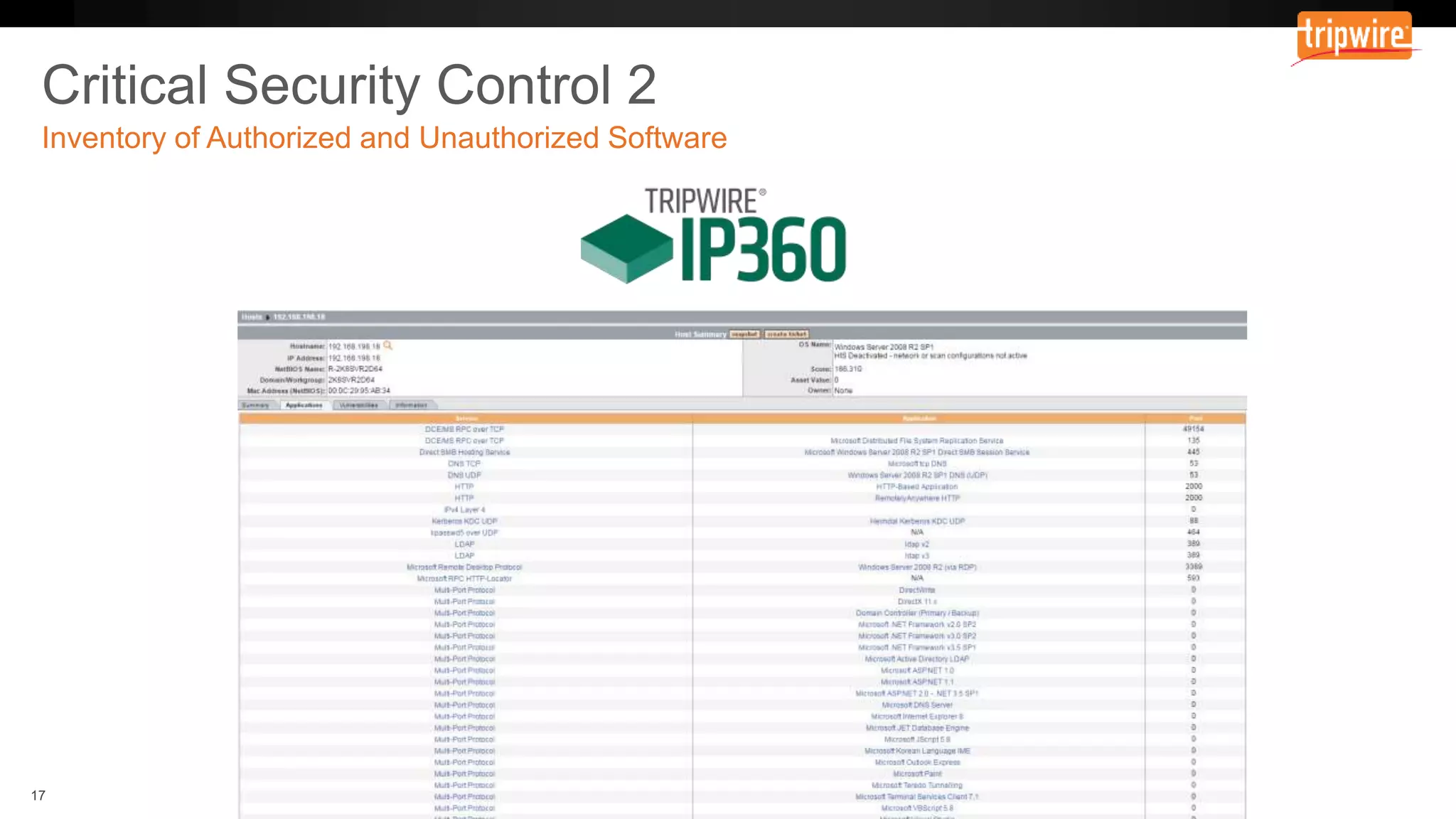
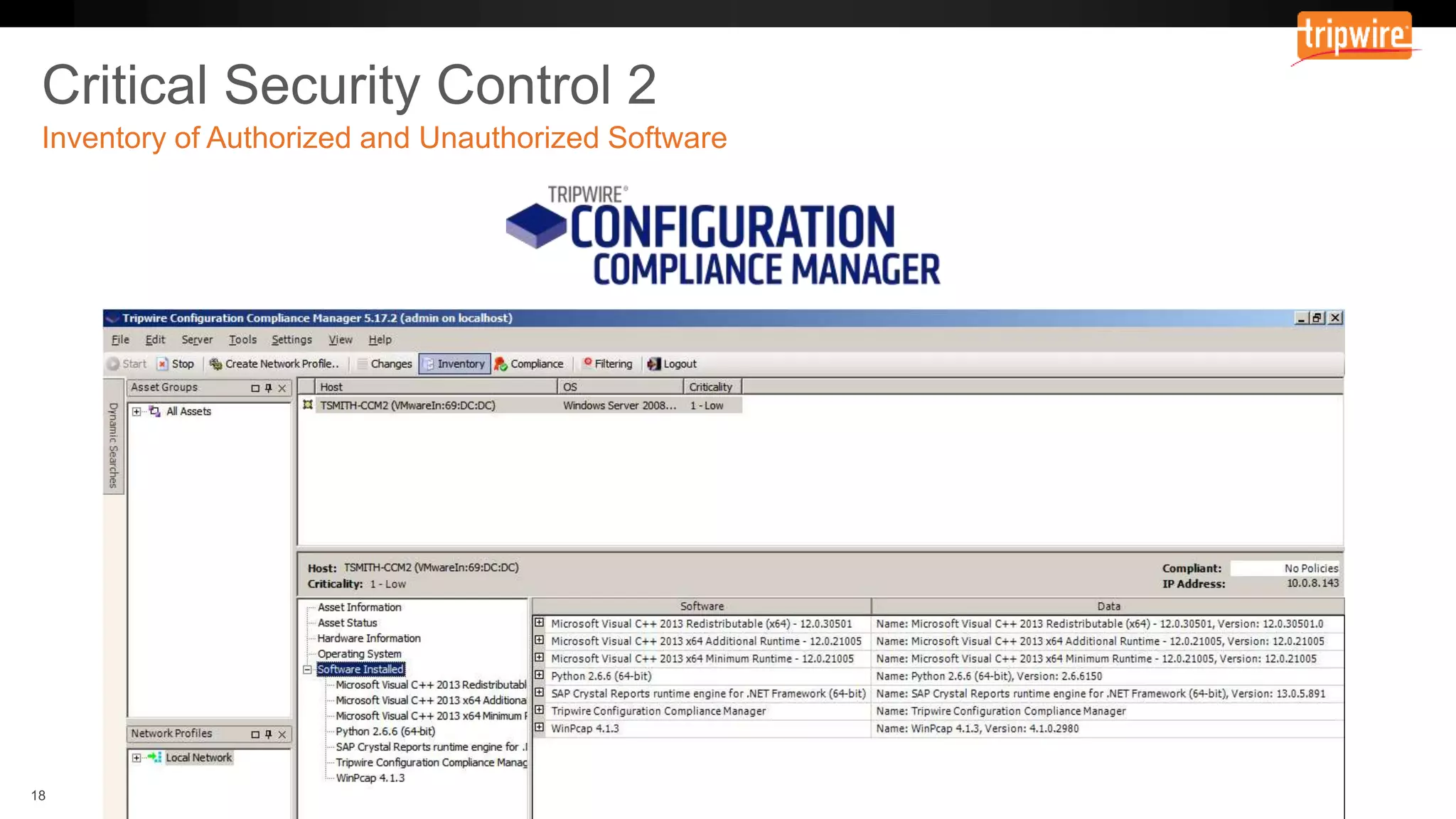
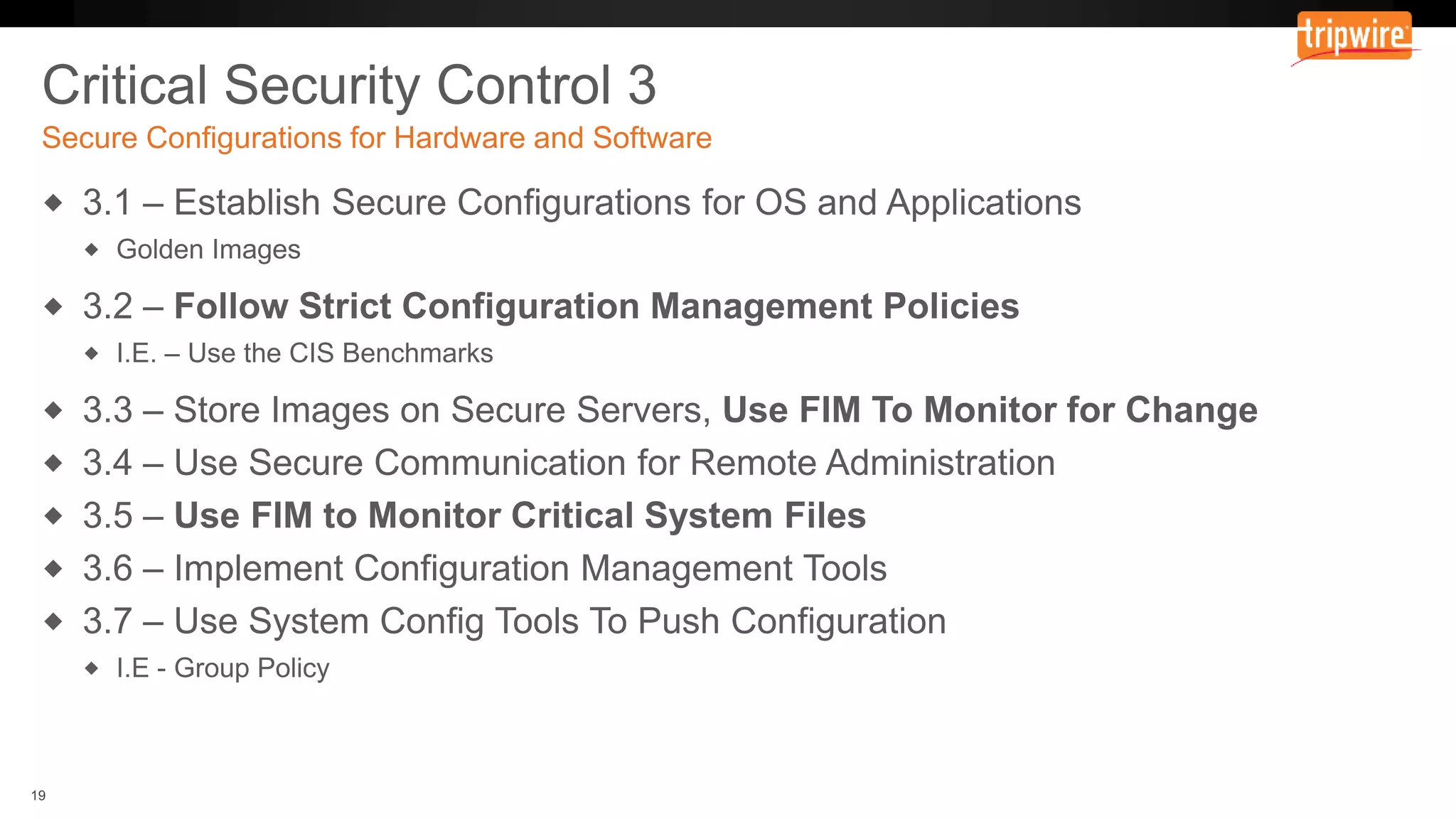
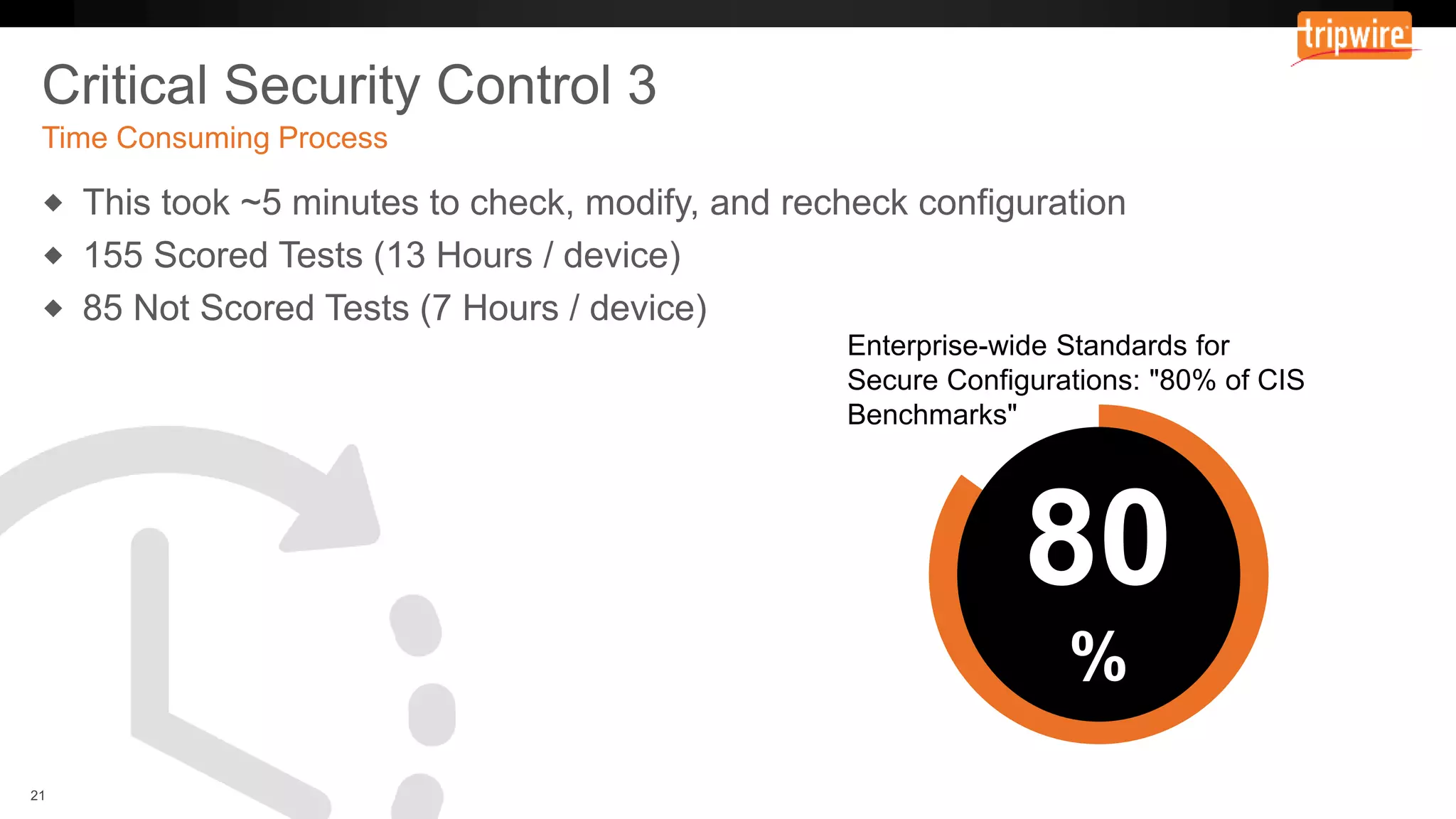
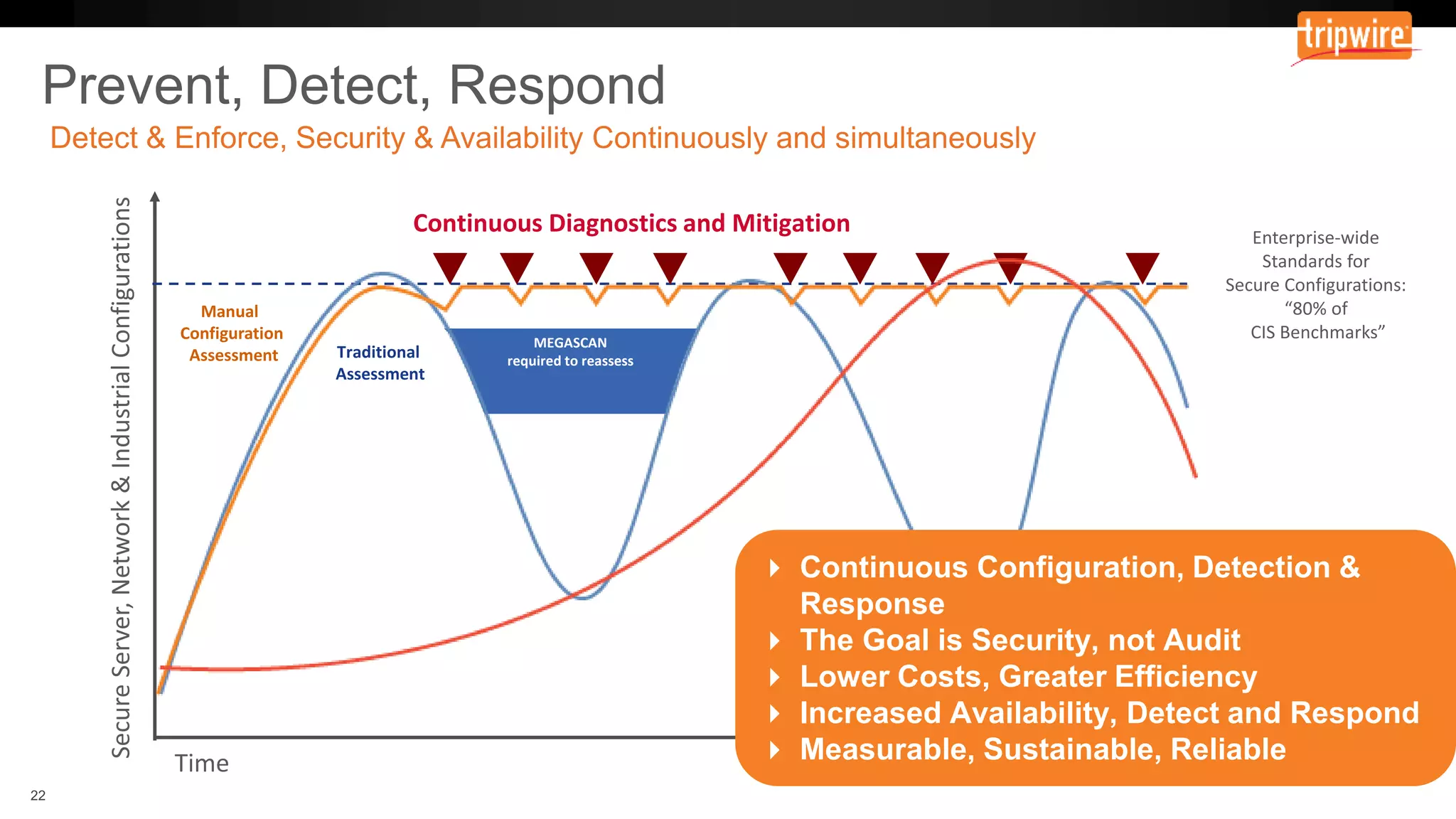
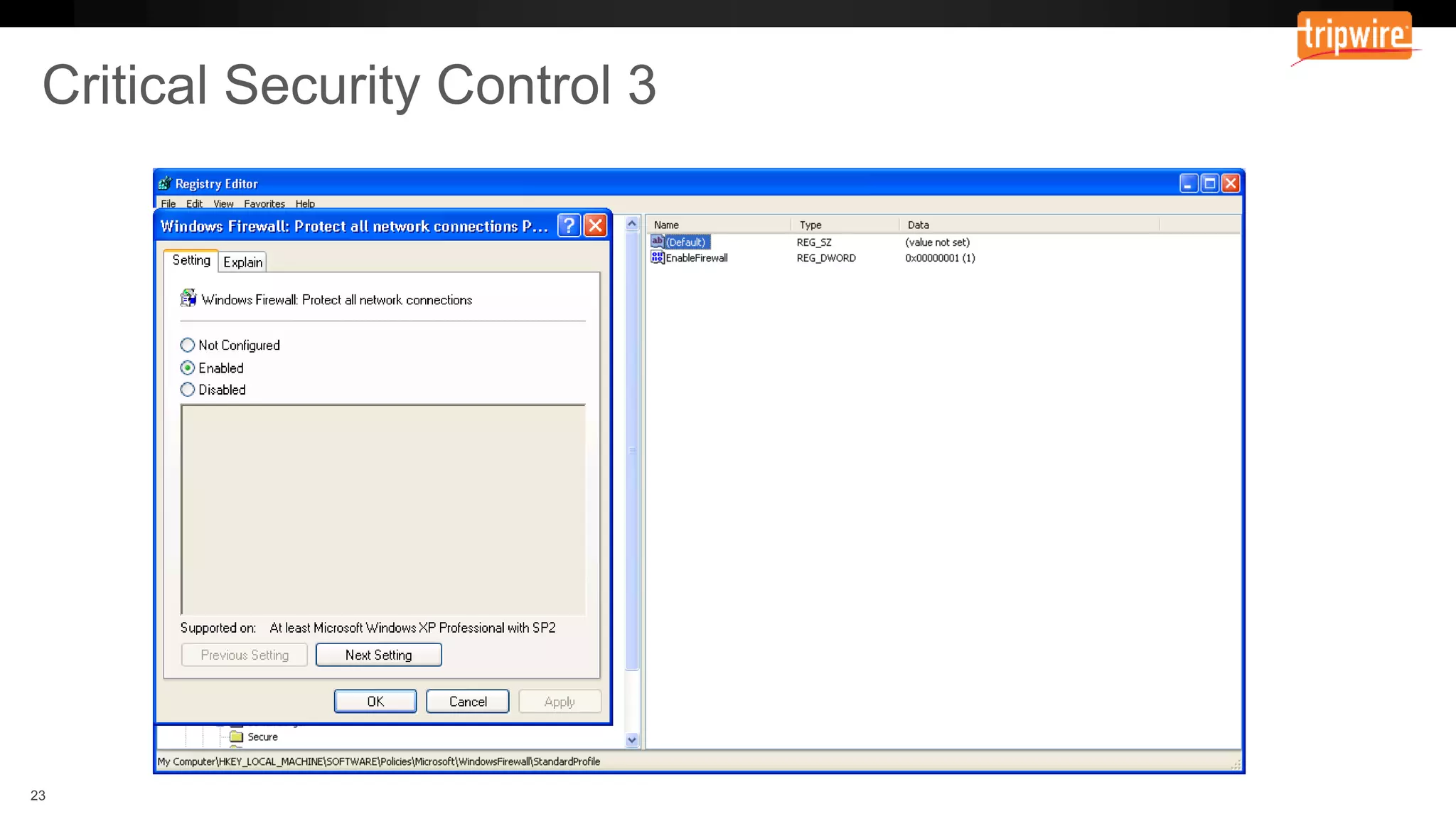
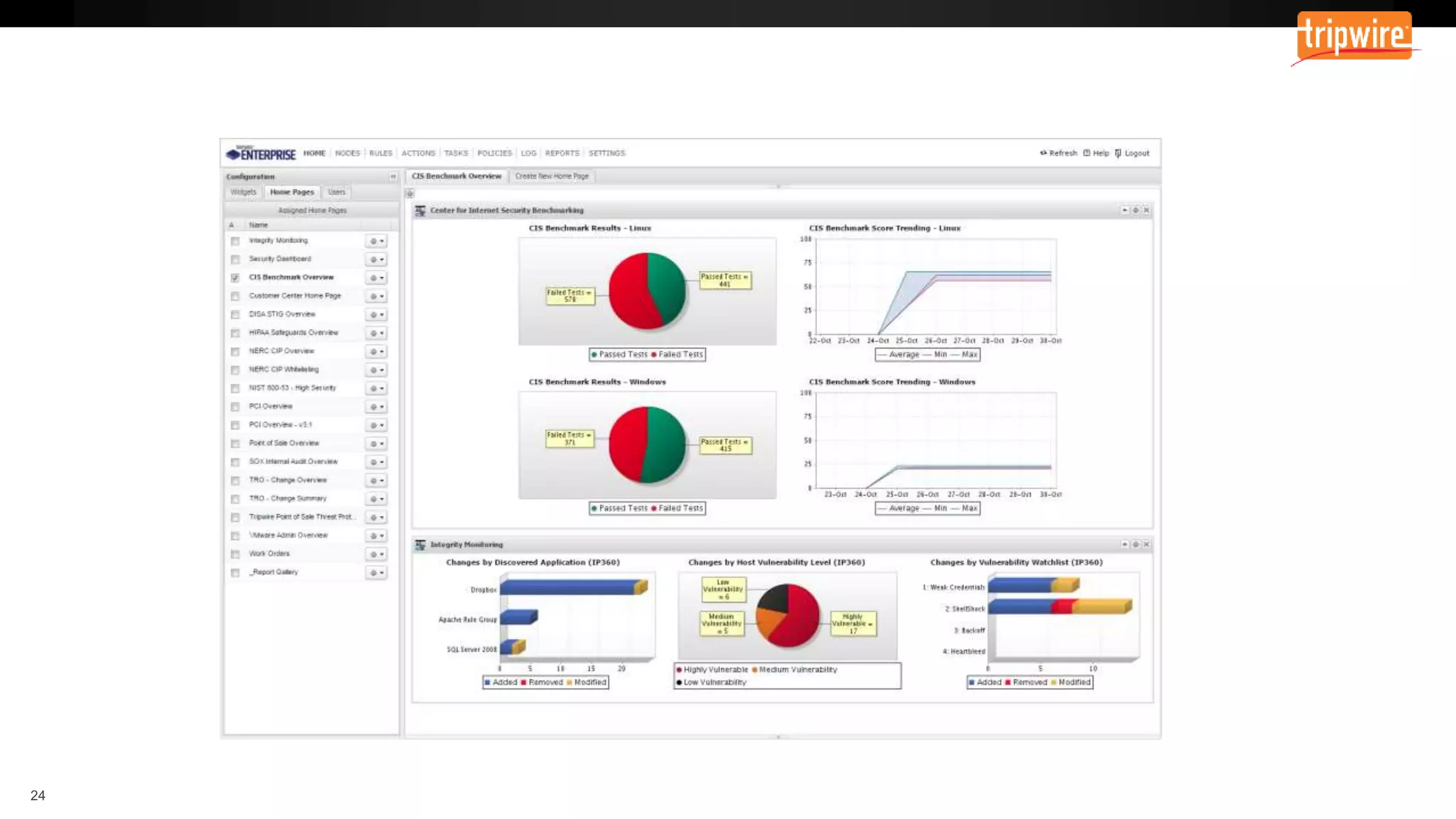
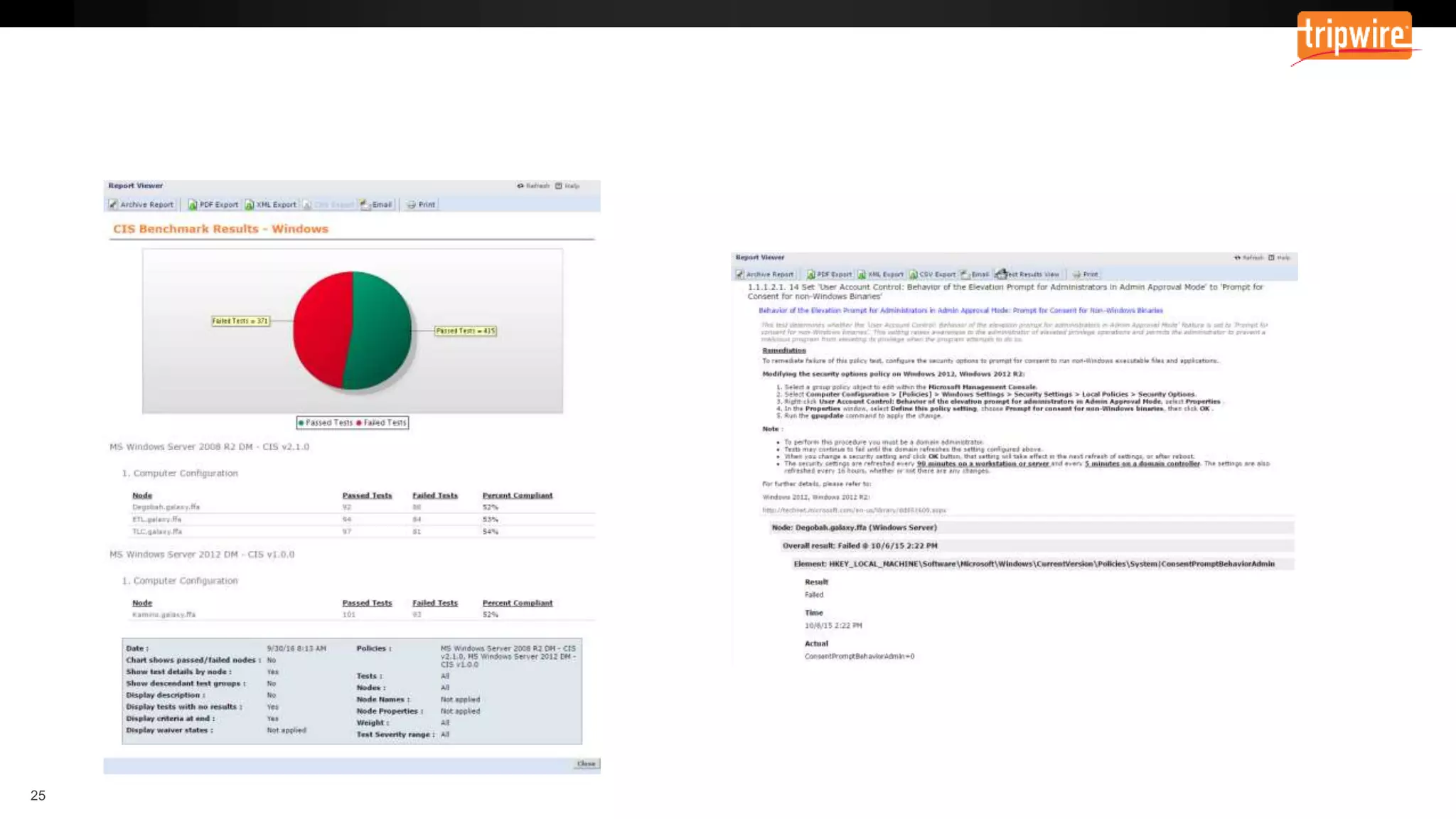
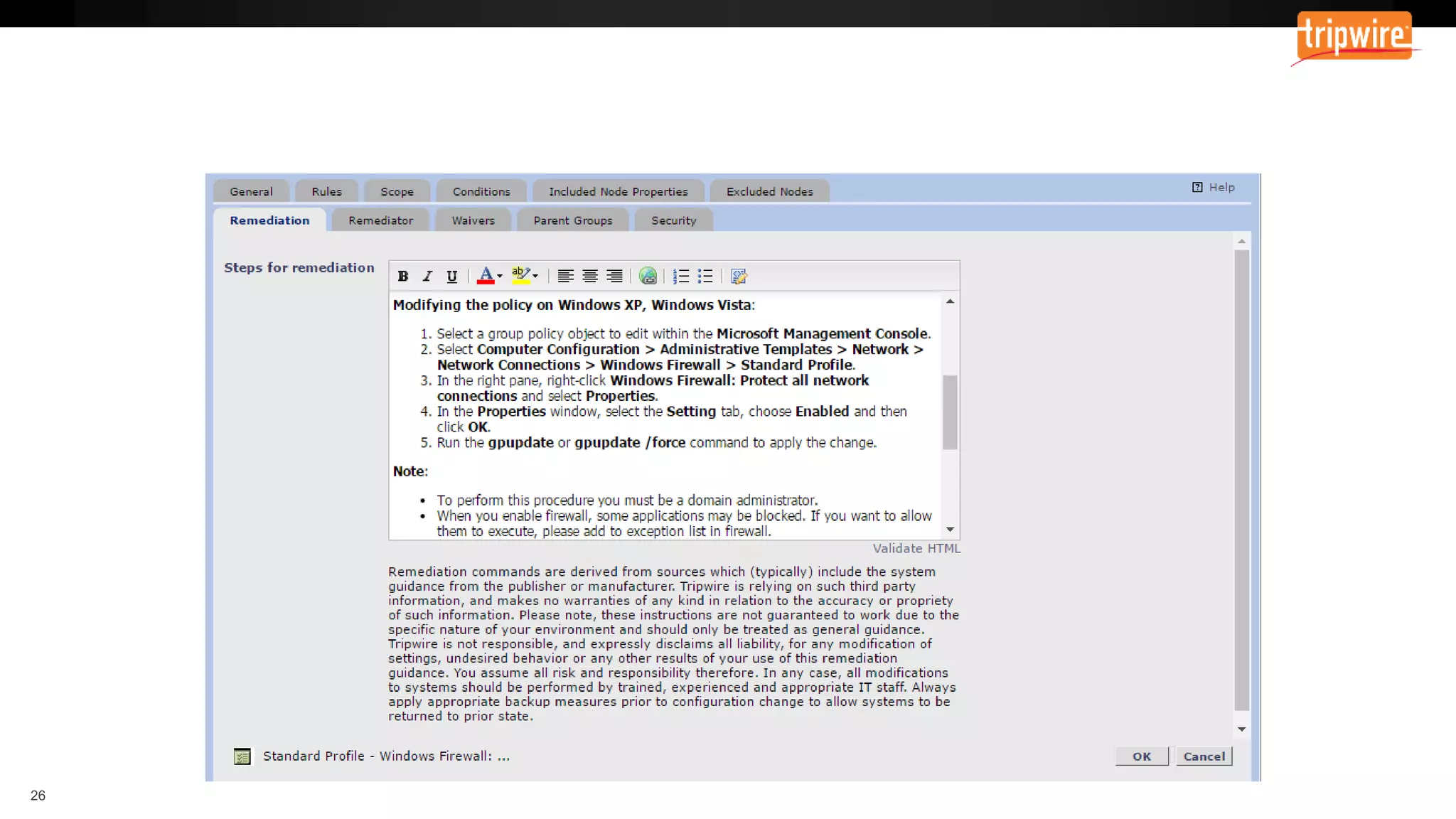
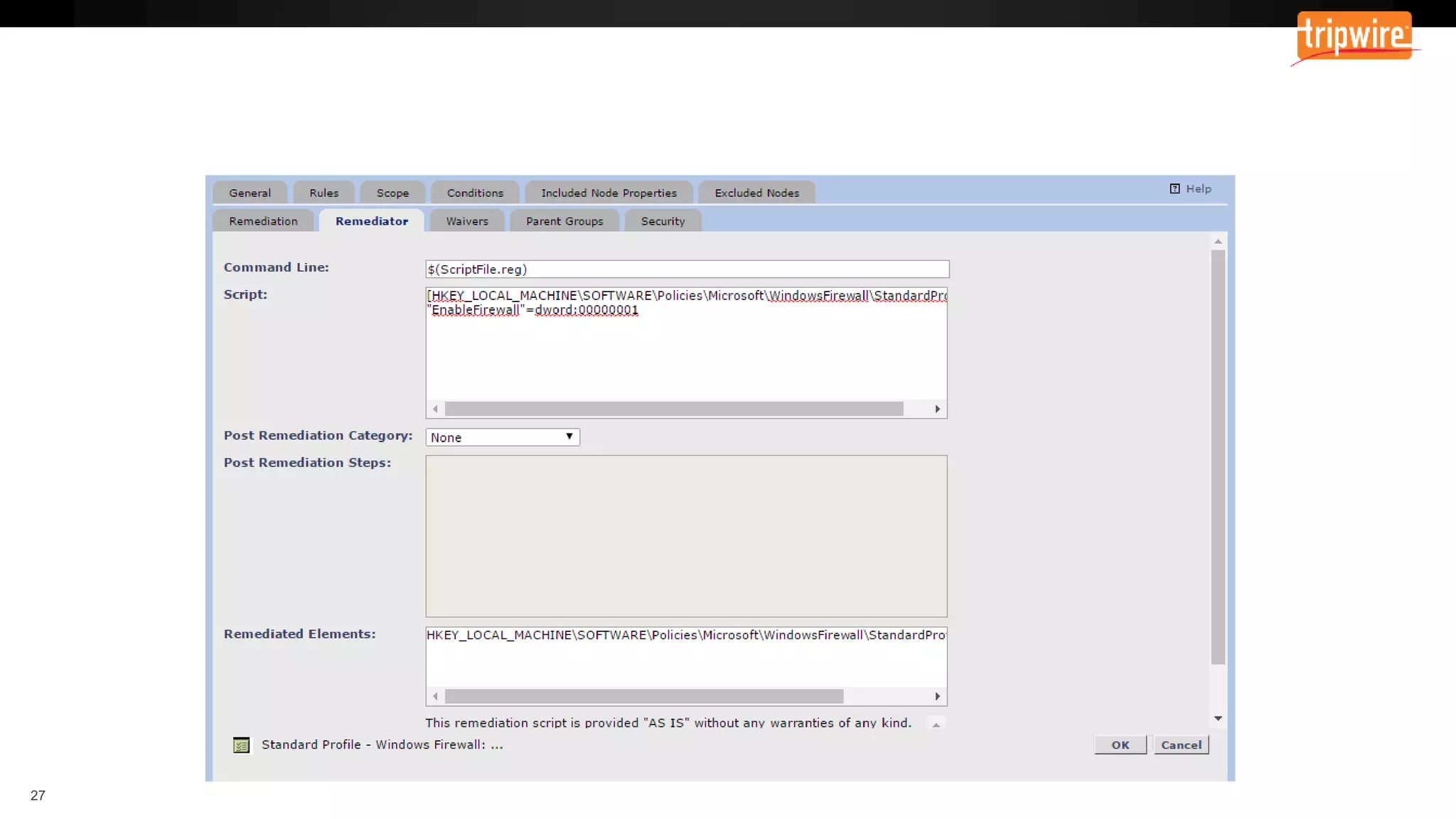
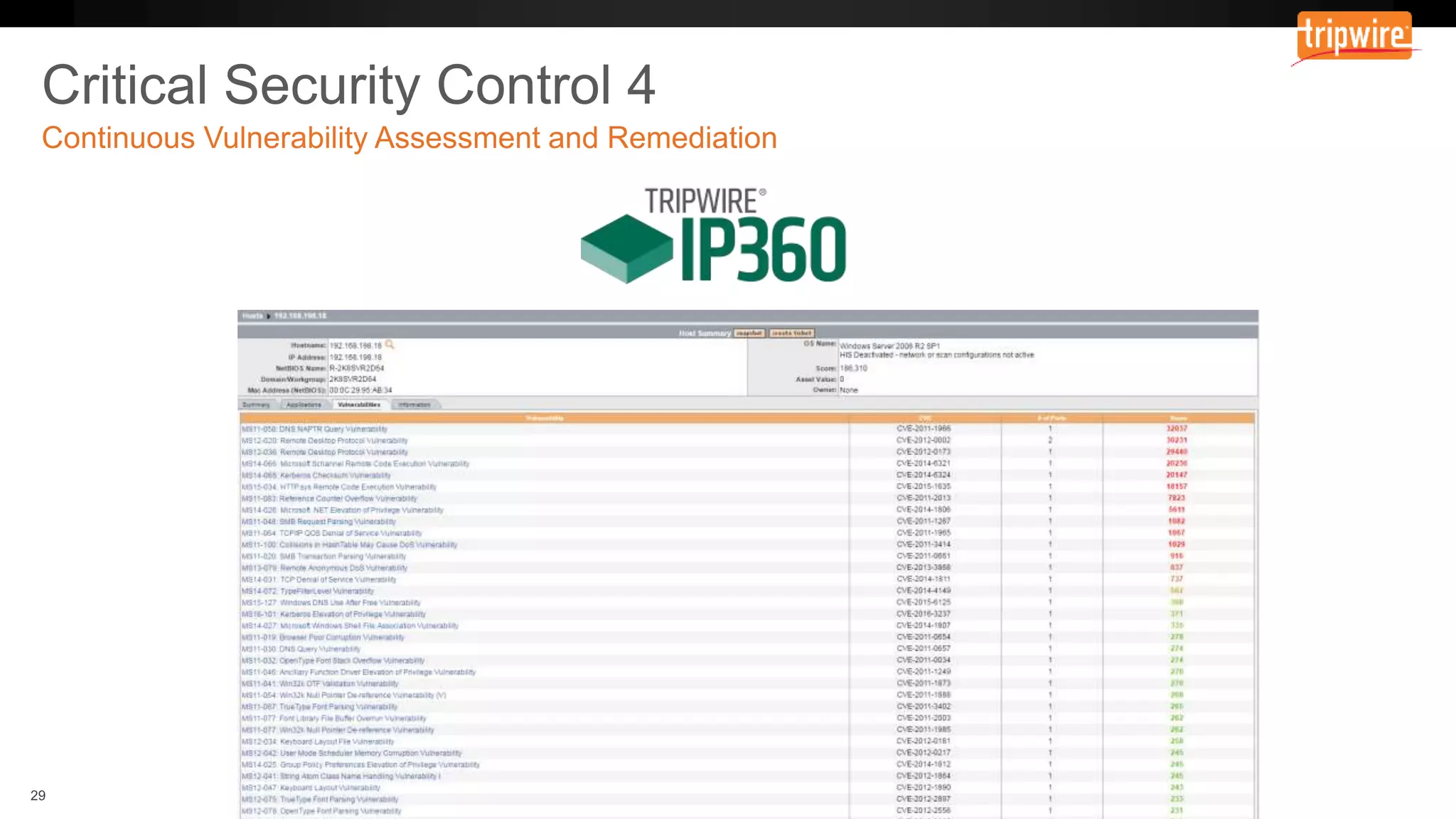
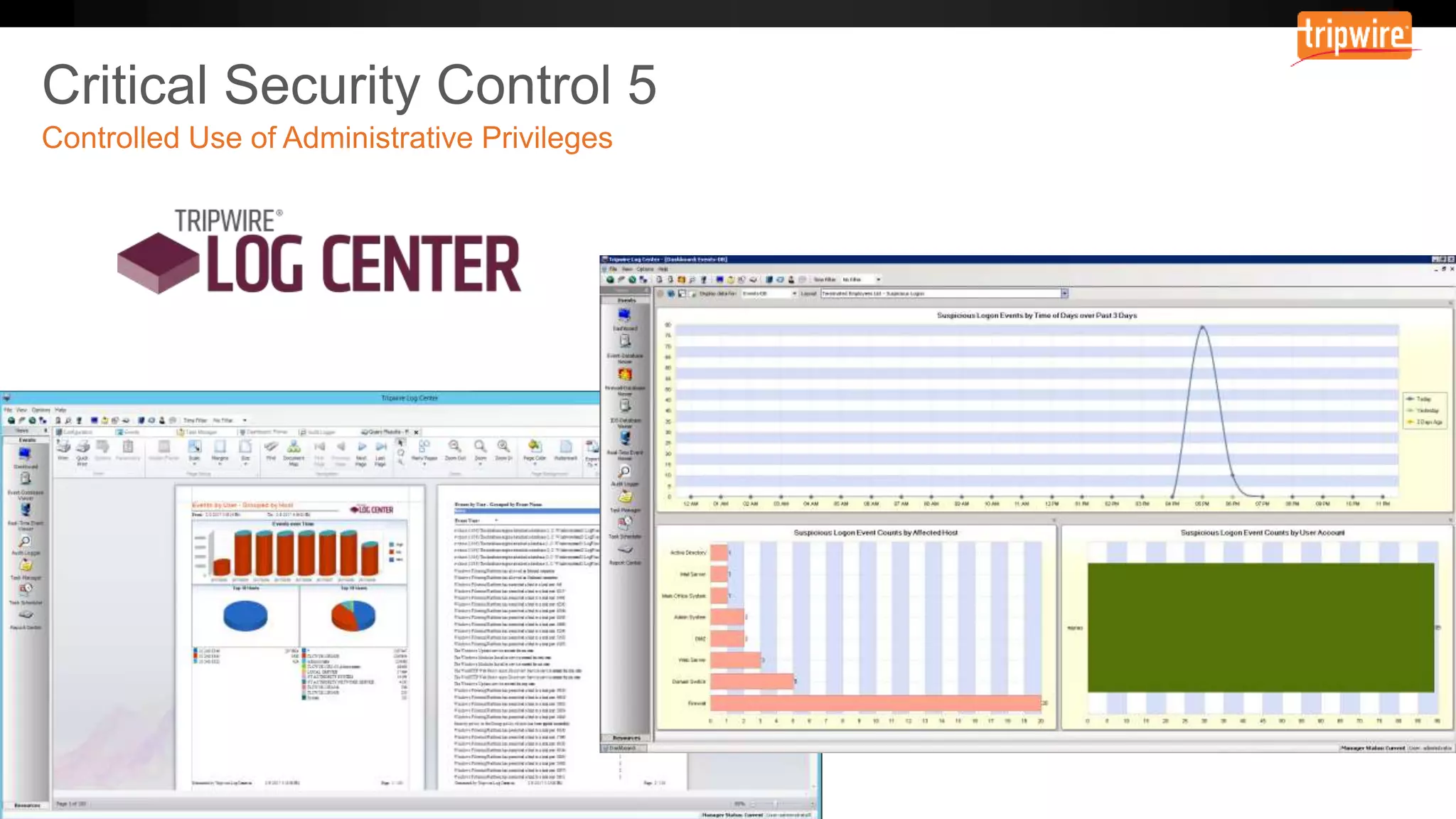
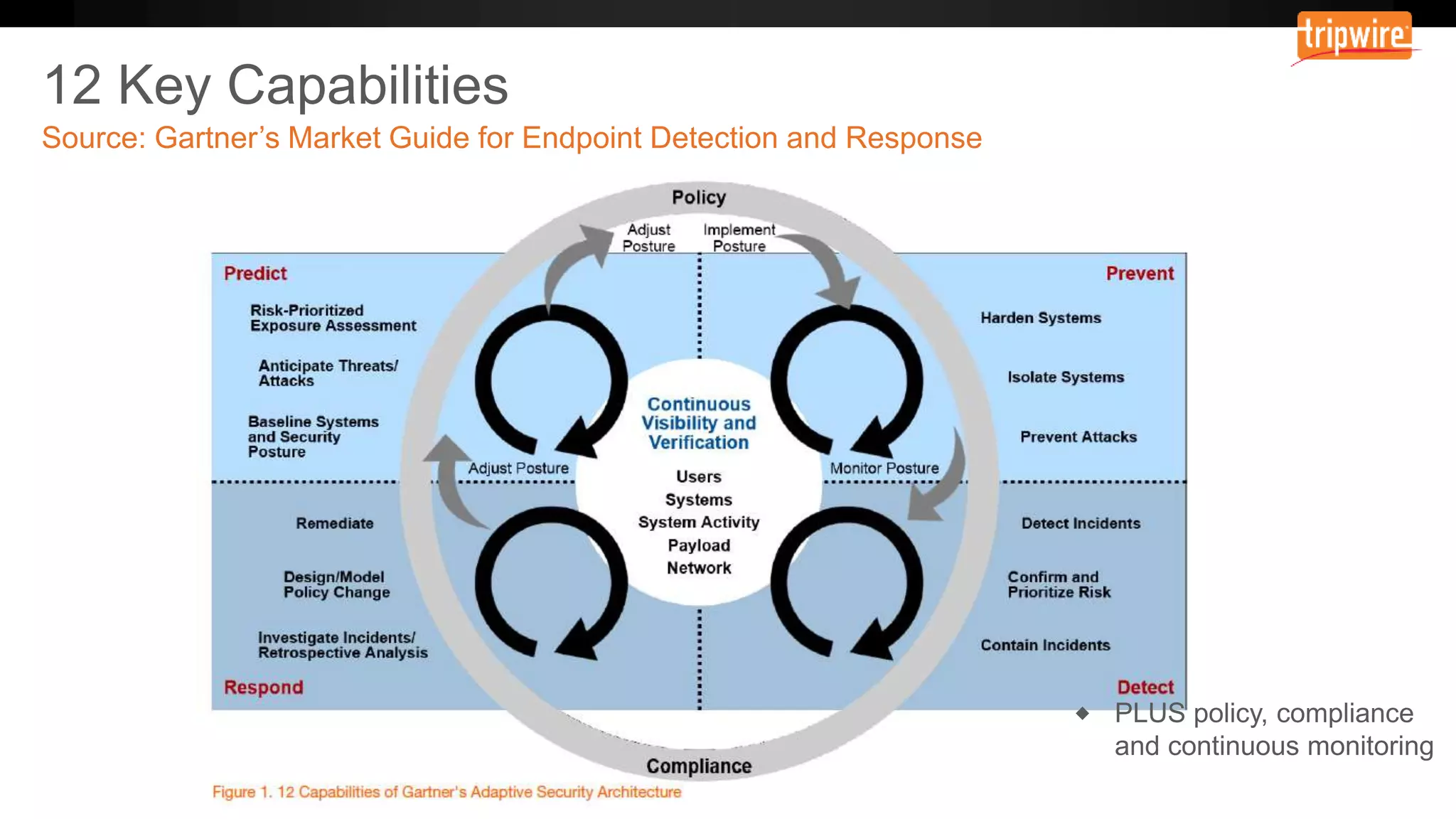
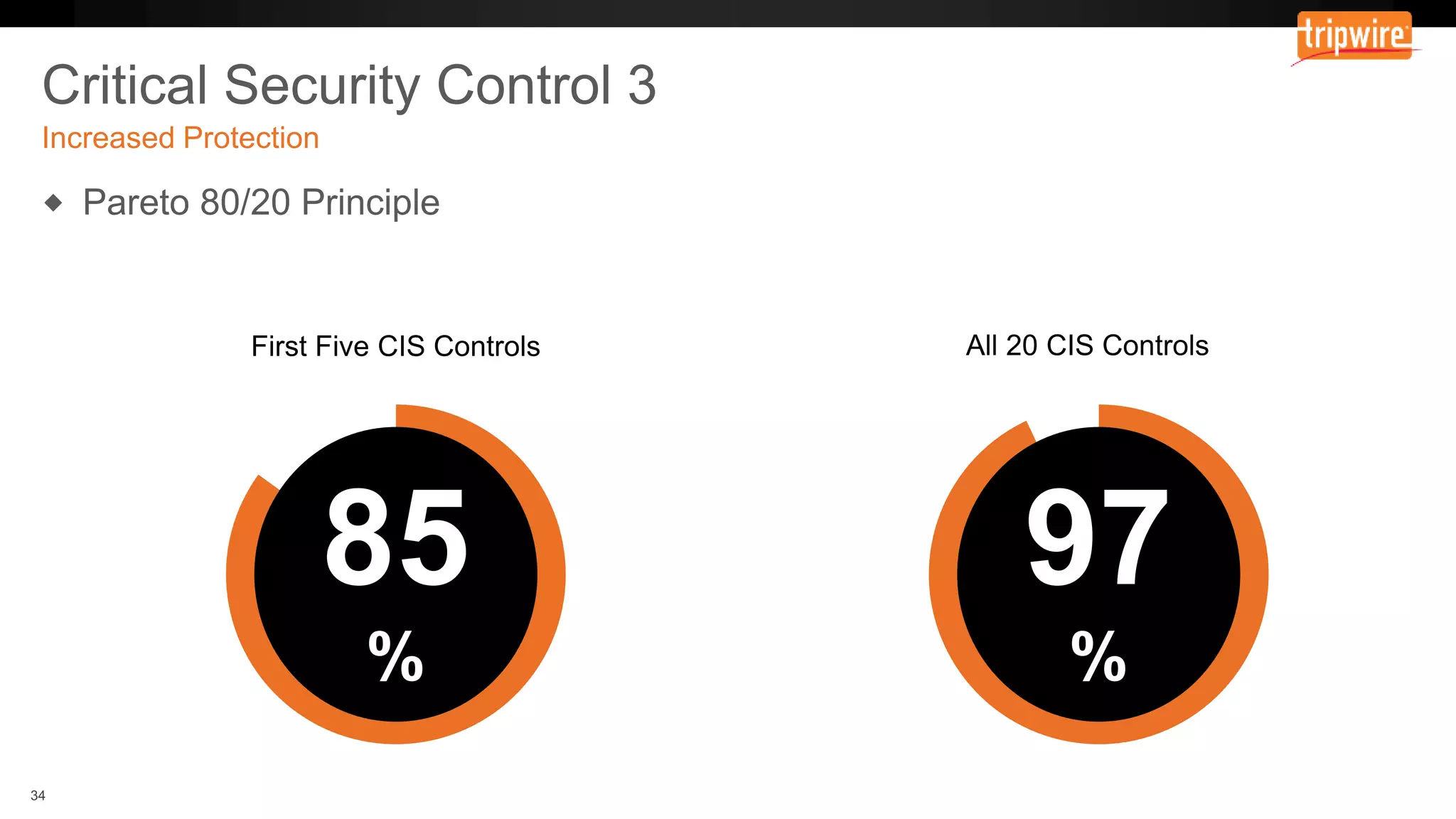
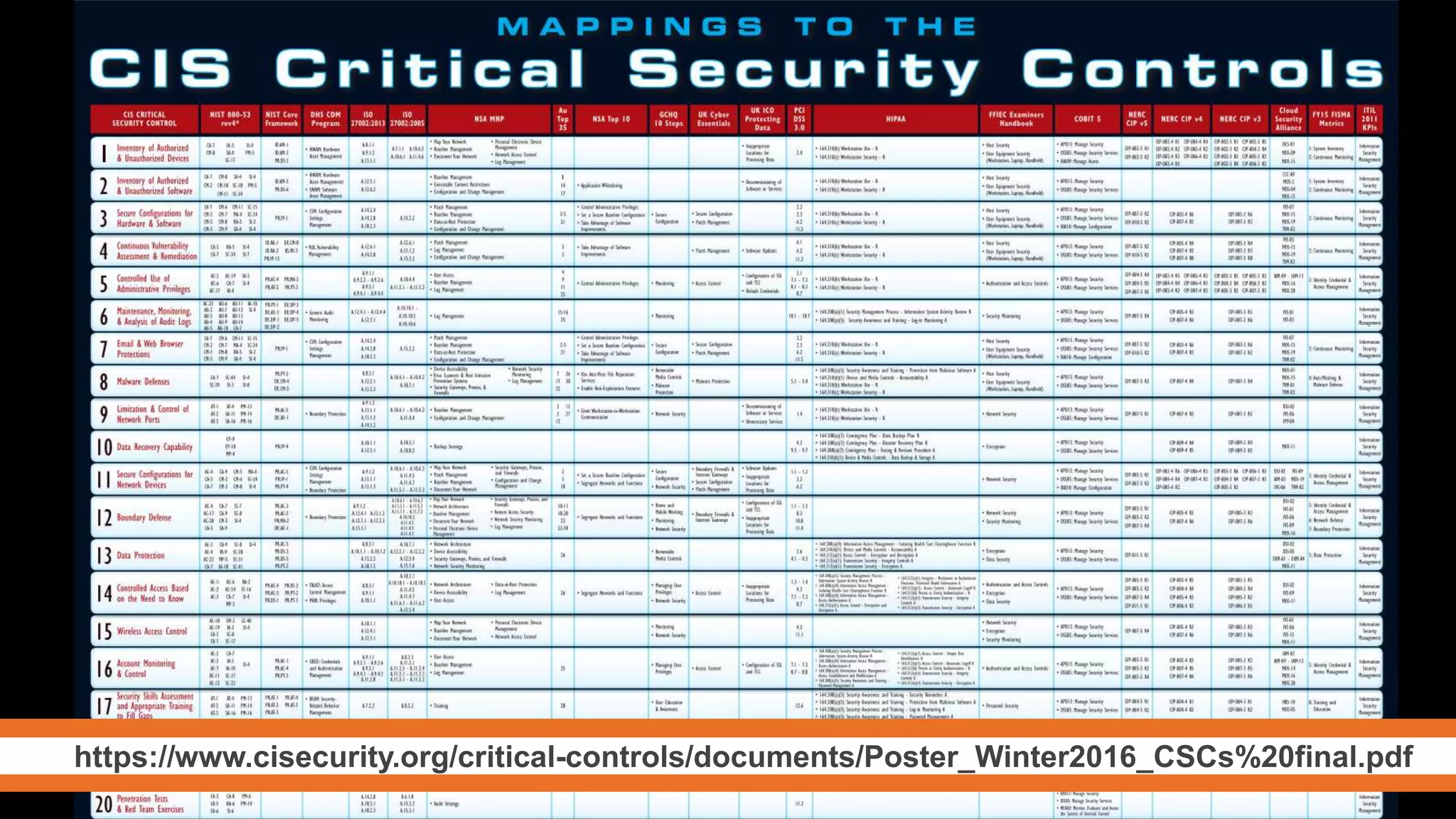
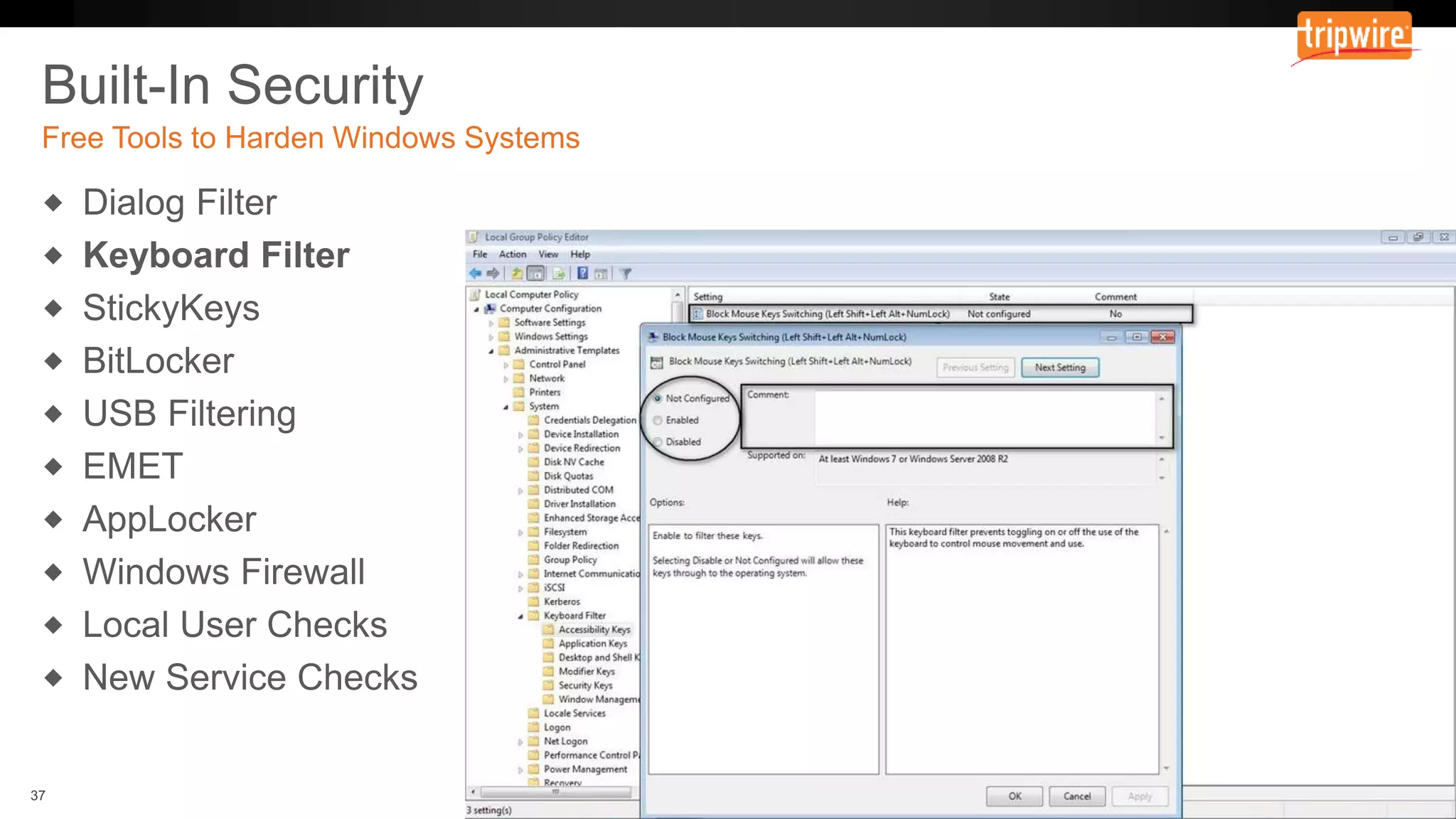

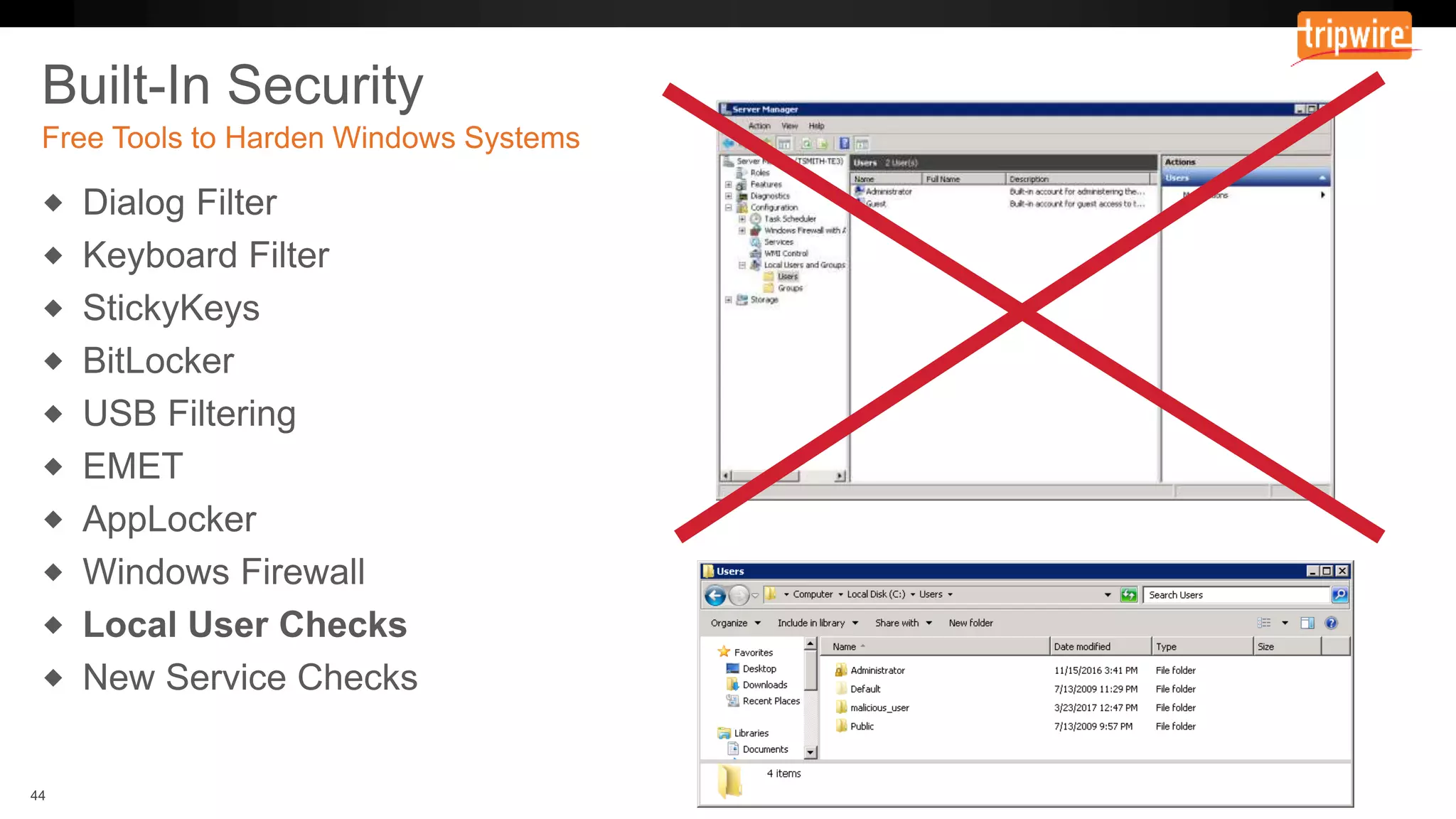
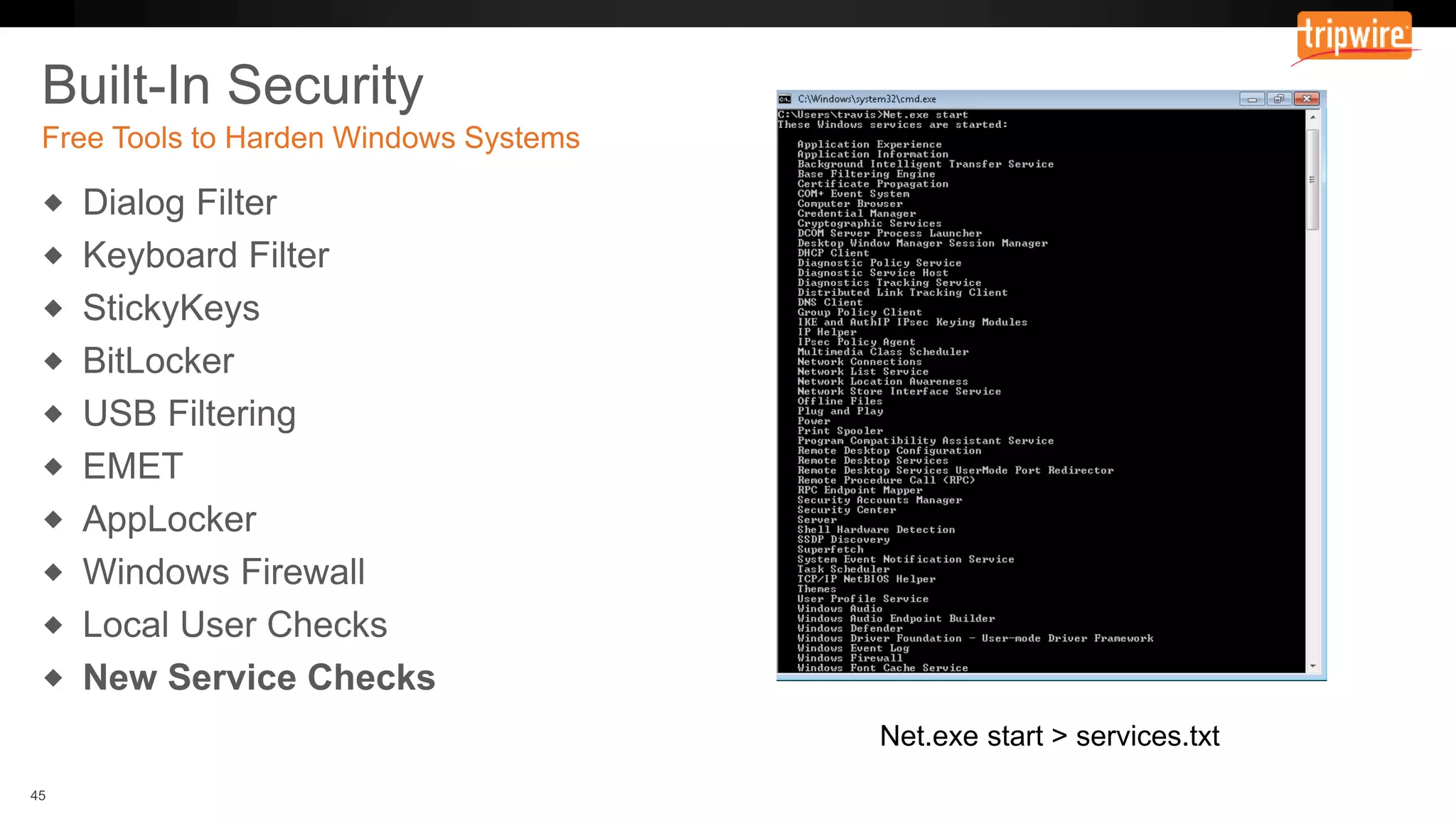
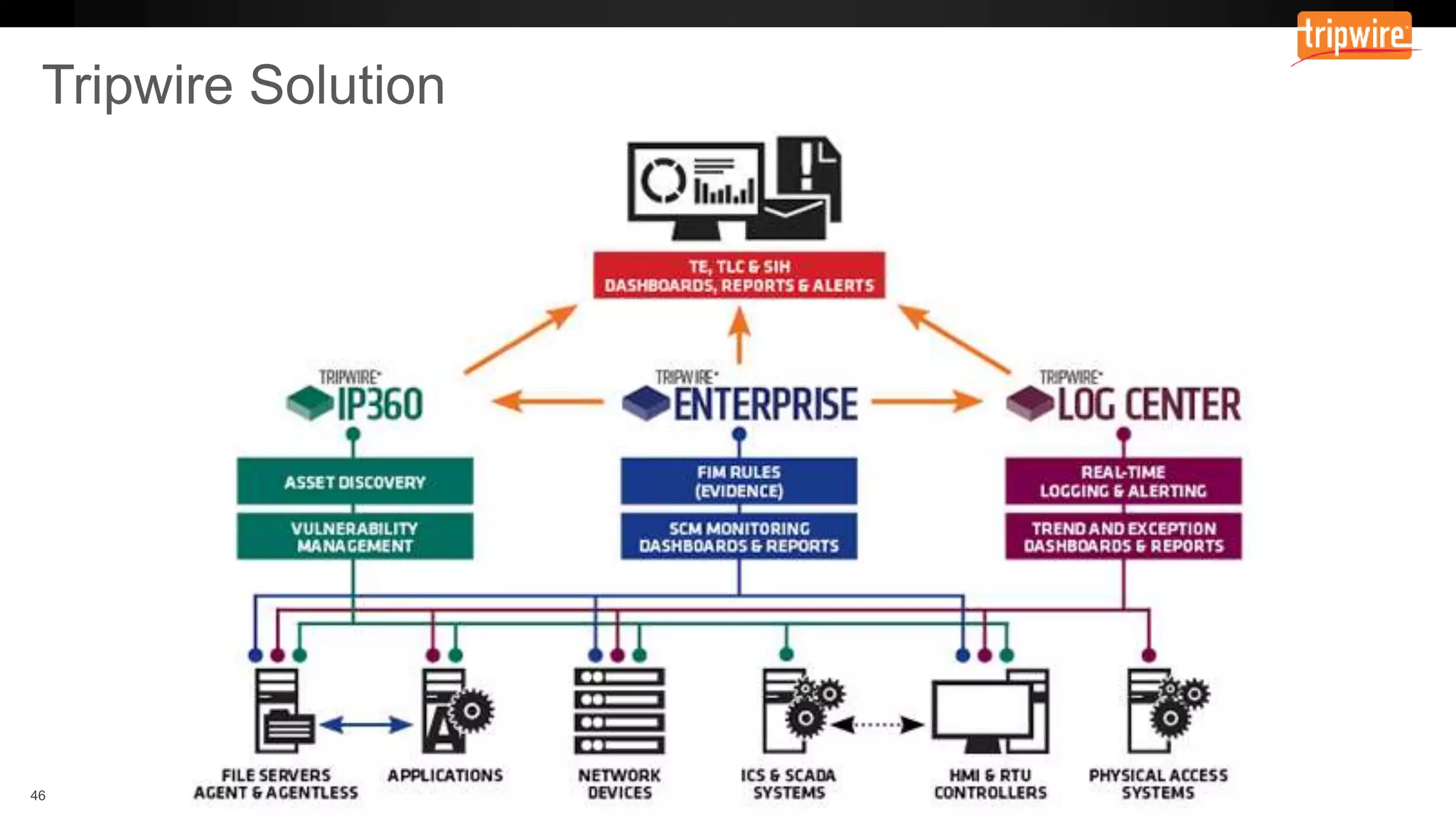



The document emphasizes the need to reassess traditional assessment methods by focusing on continuous configuration, detection, and response to achieve security goals. It highlights measuring and maintaining a sustainable system state through baselining, comparison of actual and desired configurations, and automation for remediation. Key features include deep change inspection, change management processes, and the ability to track and respond to changes effectively.















































