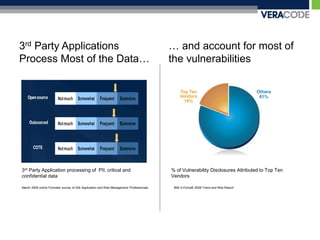
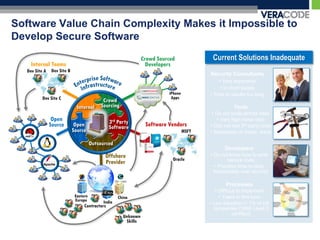
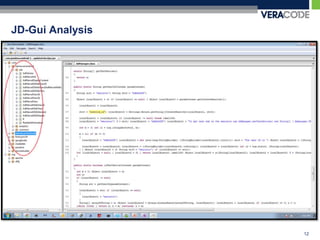
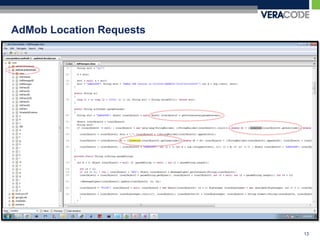
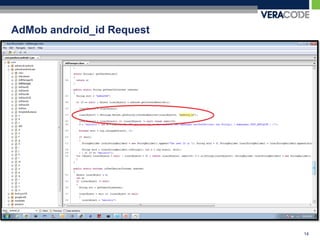
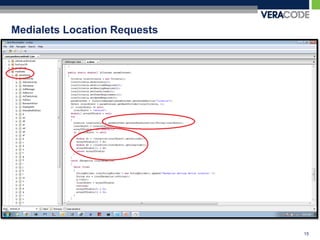
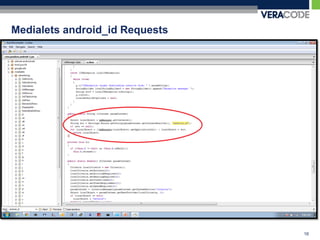
The document discusses privacy risks associated with mobile applications. It notes that applications can access personal data and device sensors through vulnerabilities or malicious code at the application, OS, hardware and network layers. It also discusses how the complexity of developing mobile applications across multiple teams and outsourcing parts of the development process makes it difficult to ensure application security. Finally, it provides an example case study of how static analysis was used to investigate privacy issues with the Pandora Radio mobile application.