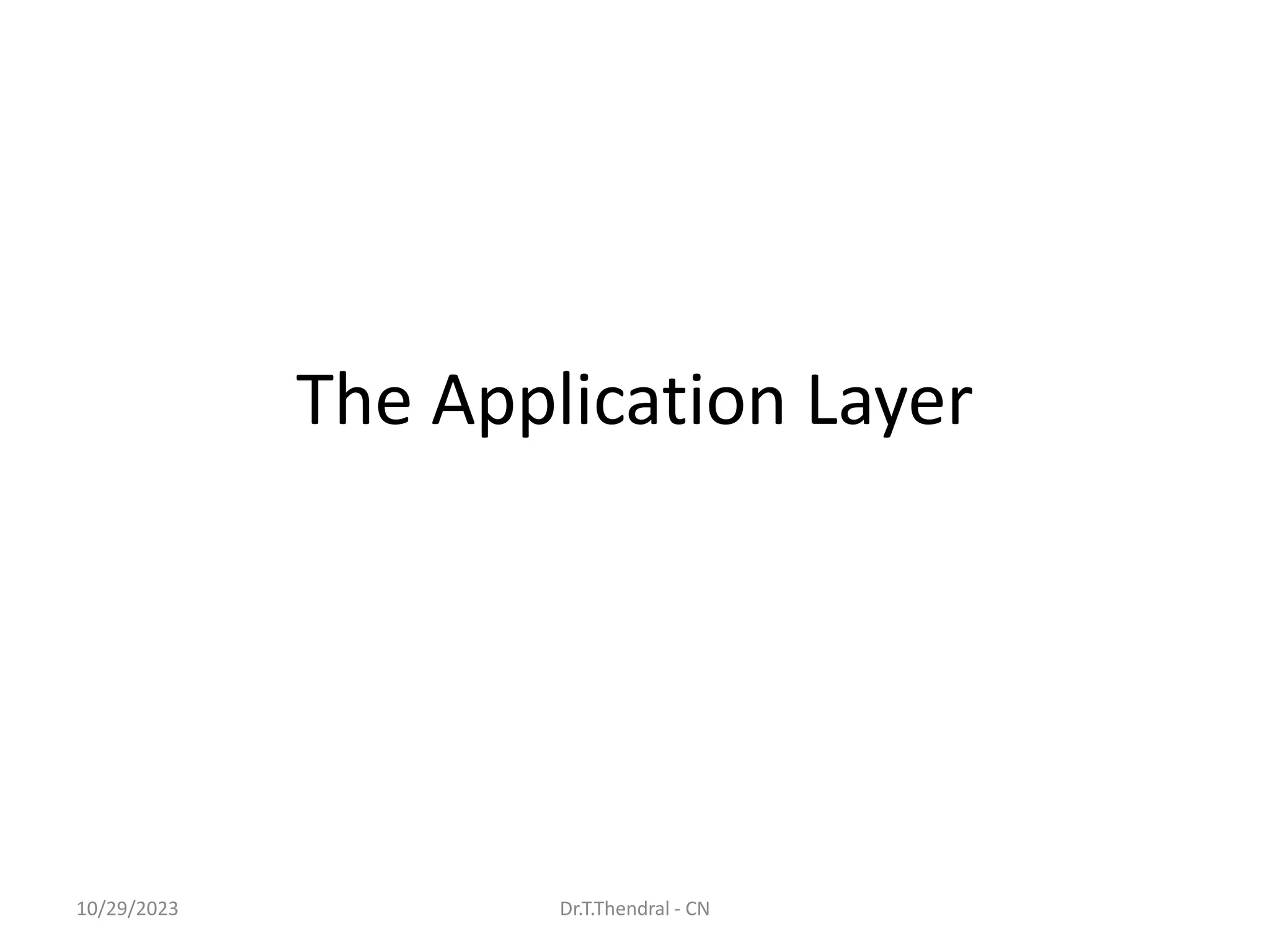
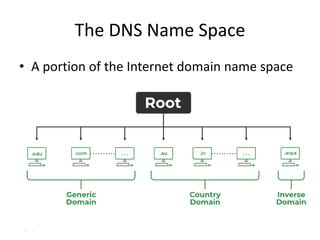
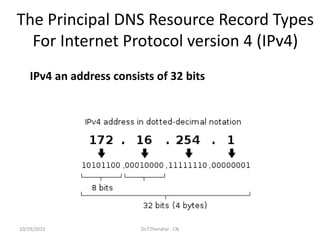
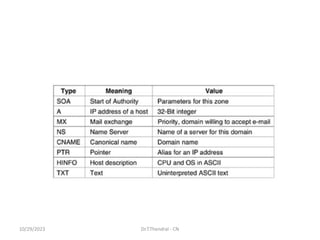
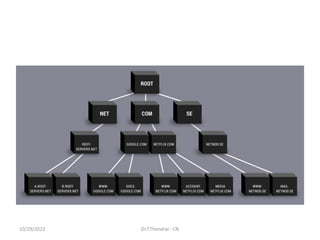
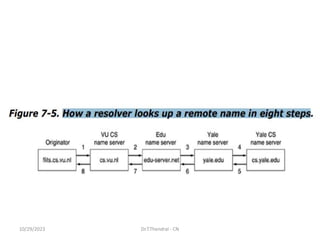
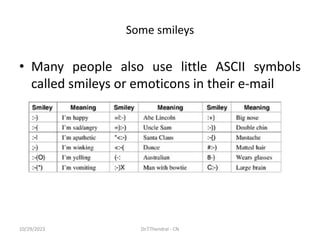
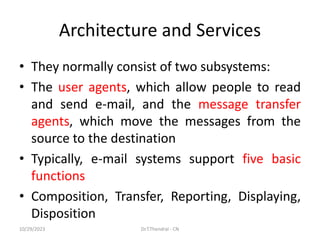
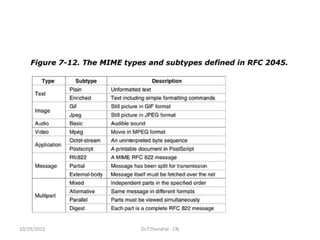
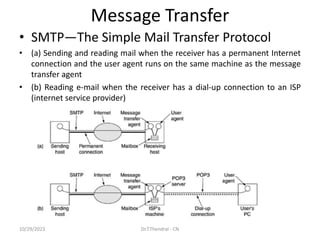
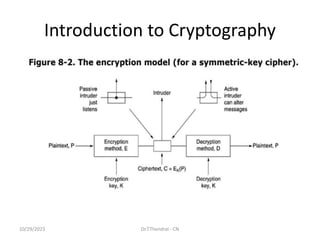
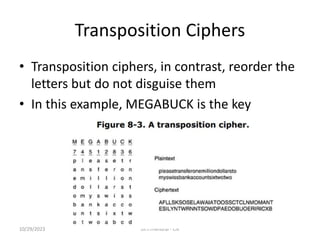
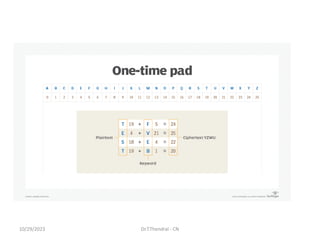
The document discusses the Domain Name System (DNS) which translates domain names to IP addresses, allowing browsers to load internet resources. It describes DNS name space and provides examples of domain names. It also discusses DNS resource records which contain information about a domain, including the domain name, time to live, class, type and value. The principal DNS record types for IPv4 are described, including A, MX, and NS records. The document also discusses DNS name servers which store DNS records and avoid problems with a single information source by dividing the DNS name space into zones.