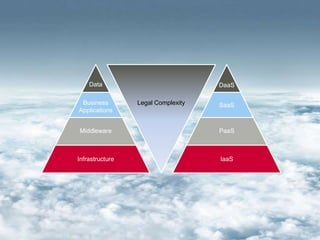
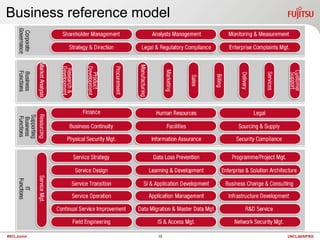
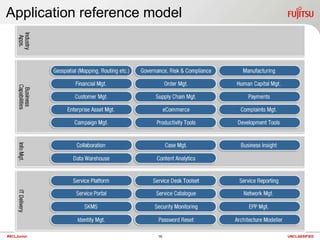
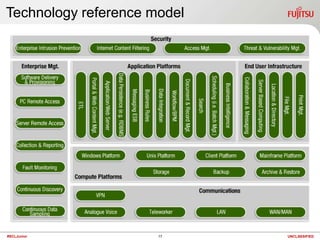
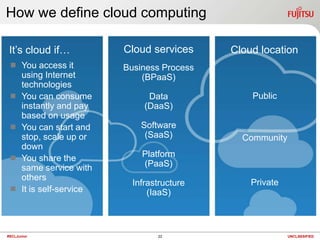
The document discusses technology and summarizes key points from a presentation on the topic. It begins by defining the term "geek" and discussing the need to understand one's audience. It then explains that a "black box" refers to something that can be understood based on its inputs, outputs, and functions without knowing its internal workings. The document summarizes views of business, applications, and technology from both top-down and bottom-up perspectives. It also discusses requirements, service management, cloud computing models, and provides a high-level look at potential future directions for IT.





































![“With about 75,000 people having named Ryan Giggs on Twitter it is obviously impracticable to imprison them all and with reports that Giles Coren also faces imprisonment... the question is what the Government's view is on the enforceability of a law which clearly does not have public consent?”[John Hemming, MP: 23 May 2011]“Super-injunctions” vs. TwitterImage source: Apasciuto on Flickr, via Wikipedia](https://image.slidesharecdn.com/societyforcomputersandlaw-technologyinsidetheblackboxv1-1-110725170756-phpapp01/85/Technology-Inside-the-Black-Box-49-320.jpg)