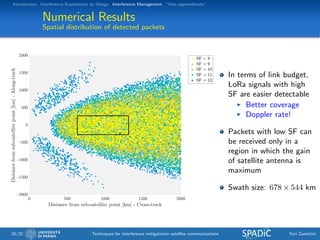
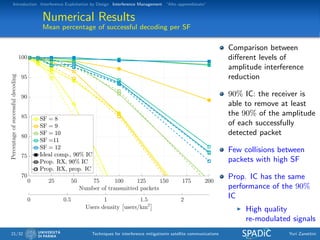
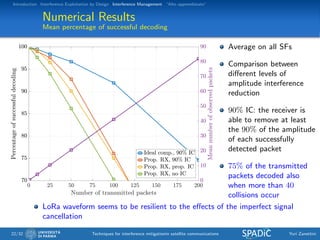
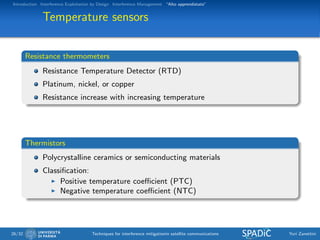
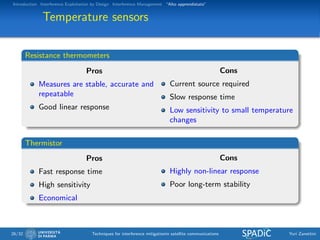
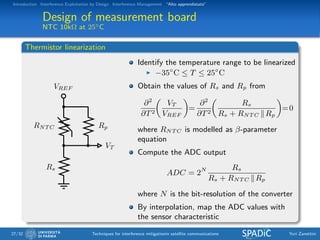
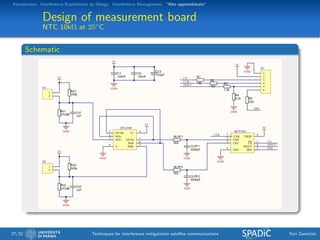
This document discusses techniques for interference mitigation in satellite communications. It begins with an introduction discussing the problem of interference and the need to move from interference avoidance to interference management and exploitation. It then outlines the rest of the document which will cover interference exploitation by design, interference management, and "Alto apprendistato". Numerical results are presented evaluating various interference mitigation techniques including interference cancellation detectors and a multicarrier predistortion technique.


![Introduction Interference Exploitation by Design Interference Management “Alto apprendistato”
Two-carrier Scenario
Channel model
Satellite transponder
IMUX OMUXTWTA
x(t) s(t)
w(t)
y(t)
Symbols from QPSK to 64APSK, possibly predistorted
x(t) =
k
x
(1)
k p(t − kTs)e−j2πF t
+
k
x
(2)
k p(t − kTs)ej2πF t
p(t) RRC with roll-off α = 10%
DVB-S2 channel model
[1] ETSI EN 302 307-2 Digital Video Broadcasting (DVB),“Second generation framing structure, channel coding and modulation systems
for Broadcasting, Interactive Services, News Gathering and other broadband satellite applications, Part II: S2-Extensions (DVB-S2X),”
Available on ETSI web site (http://www.etsi.org).
5/32 Techniques for interference mitigationin satellite communications Yuri Zanettini](https://image.slidesharecdn.com/presentazione-181130014057/85/Techniques-for-interference-mitigation-in-satellite-communications-5-320.jpg)
![Introduction Interference Exploitation by Design Interference Management “Alto apprendistato”
Applied Techniques
Frequency packing
F
Rs
BOMUX
Two carriers per transponder
BOMUX = 500 MHz
We optimize the symbol rate Rs and the frequency spacing F
Figure of merit
Achievable spectral efficiency
ASE =
IR
TsBOMUX
[bit/s/Hz]
[2] D. M. Arnold, H. A. Loeliger, P. O. Vontobel, A. Kavˇci´c and W. Zeng, “Simulation-Based Computation of Information Rates for
Channels With Memory,” IEEE Trans. Inform. Theory, vol. 52, pp. 3498–3508, Aug. 2006.
6/32 Techniques for interference mitigationin satellite communications Yuri Zanettini](https://image.slidesharecdn.com/presentazione-181130014057/85/Techniques-for-interference-mitigation-in-satellite-communications-6-320.jpg)
![Introduction Interference Exploitation by Design Interference Management “Alto apprendistato”
Applied Techniques
Transmitter side
Multicarrier data predistorter
Mitigation of the non-linear intermodulation distortion
Iterative processing
Time-varying constellations
Stage 1 Stage 2
a1
aU
a
(0)
1
a
(0)
U
a
(2)
1
a
(2)
U
a
(S)
1
a
(S)
U
a
(1)
1
a
(1)
U
a
(S-1)
1
a
(S-1)
U
Stage S
[3] B. F. Beidas, R. I. Shesadri and N. Becker, “Multicarrier Successive Predistortion for Nonlinear Satellite Systems,” IEEE Trans.
Commun., vol. 63, pp. 1373–1382, Apr. 2015
7/32 Techniques for interference mitigationin satellite communications Yuri Zanettini](https://image.slidesharecdn.com/presentazione-181130014057/85/Techniques-for-interference-mitigation-in-satellite-communications-7-320.jpg)
![Introduction Interference Exploitation by Design Interference Management “Alto apprendistato”
Applied Techniques
Transmitter side
Predistorted constellations
Computed for each carrier
Minimizing error between undistorted symbols and estimator output
a(s+1)
u = ˆa(s)
u − µ(s)
au − ˆa(s)
u
a1
aU
a
(s)
1
a
(s)
U
a
(s+1)
1
a
(s+1)
U
µ(s)
ˆa
(s)
1
ˆa
(s)
U
Channel
Output
Estimator
−
−
Stage s
[3] B. F. Beidas, R. I. Shesadri and N. Becker, “Multicarrier Successive Predistortion for Nonlinear Satellite Systems,” IEEE Trans.
Commun., vol. 63, pp. 1373–1382, Apr. 2015
7/32 Techniques for interference mitigationin satellite communications Yuri Zanettini](https://image.slidesharecdn.com/presentazione-181130014057/85/Techniques-for-interference-mitigation-in-satellite-communications-8-320.jpg)
![Introduction Interference Exploitation by Design Interference Management “Alto apprendistato”
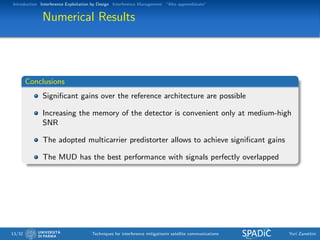
Numerical Results
SUD detector
0
1
2
3
4
5
6
−10 −5 0 5 10 15 20 25
ASE[bit/s/Hz]
Psat/N [dB]
Ref., no pred.
Ref., pred.
L = 0, no pred.
L = 0, pred.
L = 1, no pred.
L = 1, pred.
Memory L = 0 and
L = 1
Symbols up to 64APSK
Optimization:
Symbol rate
Frequency spacing
IBO
Comparison with and
without the predistorter
Maximum ASE when
signals slightly overlapped
SUD L = 1 – pred. SUD L = 1 – no pred.
Psat/N0 [dB] M Rs [Mbaud] F [MHz] IBO [dB] M Rs [Mbaud] F [MHz] IBO [dB]
15 64 250 275 3 64 275 275 6
20 64 275 275 6 64 275 275 9
25 64 325 325 6 64 325 350 12
9/32 Techniques for interference mitigationin satellite communications Yuri Zanettini](https://image.slidesharecdn.com/presentazione-181130014057/85/Techniques-for-interference-mitigation-in-satellite-communications-11-320.jpg)
![Introduction Interference Exploitation by Design Interference Management “Alto apprendistato”
Numerical Results
MUD detector
0
1
2
3
4
5
6
−10 −5 0 5 10 15 20 25
ASE[bit/s/Hz]
Psat/N [dB]
Ref., no pred.
Ref., pred.
L = 0, no pred.
L = 0, pred.
L = 1, no pred.
L = 1, pred.
Memory L = 0 and
L = 1
Symbols up to 16APSK
Optimization:
Symbol rate
Frequency spacing
IBO
Comparison with and
without the predistorter
Maximum ASE when
signals perfectly
overlapped
MUD L = 0 – pred. MUD L = 0 – no pred.
Psat/N0 [dB] M Rs [Mbaud] F [MHz] IBO [dB] M Rs [Mbaud] F [MHz] IBO [dB]
15 16 525 0 0 8 525 0 6
20 16 525 0 3 16 525 0 9
25 16 525 0 3 16 525 0 12
10/32 Techniques for interference mitigationin satellite communications Yuri Zanettini](https://image.slidesharecdn.com/presentazione-181130014057/85/Techniques-for-interference-mitigation-in-satellite-communications-12-320.jpg)
![Introduction Interference Exploitation by Design Interference Management “Alto apprendistato”
Numerical Results
SUD and MUD detectors with memory L = 0
0
1
2
3
4
5
6
−10 −5 0 5 10 15 20 25
ASE[bit/s/Hz]
Psat/N [dB]
Ref., no pred.
Ref., pred.
SUD, no pred.
SUD, pred.
MUD, no pred.
MUD, pred.
Comparison between
SUD and MUD
Memory L = 0
SUD: symbols up to
64APSK
MUD: symbols up to
16APSK
Gains of 2.5 ÷ 4 dB over
reference scheme
11/32 Techniques for interference mitigationin satellite communications Yuri Zanettini](https://image.slidesharecdn.com/presentazione-181130014057/85/Techniques-for-interference-mitigation-in-satellite-communications-13-320.jpg)
![Introduction Interference Exploitation by Design Interference Management “Alto apprendistato”
Numerical Results
SUD and MUD detectors with memory L = 1
0
1
2
3
4
5
6
−10 −5 0 5 10 15 20 25
ASE[bit/s/Hz]
Psat/N [dB]
Ref., no pred.
Ref., pred.
SUD, no pred.
SUD, pred.
MUD, no pred.
MUD, pred.
Comparison between
SUD and MUD
Memory L = 1
SUD: symbols up to
64APSK
MUD: symbols up to
16APSK
Gains of 1 bit/s/Hz over
reference scheme
12/32 Techniques for interference mitigationin satellite communications Yuri Zanettini](https://image.slidesharecdn.com/presentazione-181130014057/85/Techniques-for-interference-mitigation-in-satellite-communications-14-320.jpg)

![Introduction Interference Exploitation by Design Interference Management “Alto apprendistato”
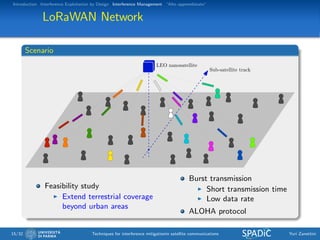
LoRaWAN Network
Channel model
The complex envelope of the received signal at the Cubesat is
r(t) = ejθ(t)
N
i=1
γi(t)si(t − τi)ej[2π(νi+αit/2)t+φi(t)]
+ w(t)
where
N is the number of active transmitters on a given frequency band
and on a given swath,
si(t − τi) is the message transmitted by the i-th active user,
γi(t) its complex gain/attenuation,
νi its Doppler shift,
αi its Doppler rate,
θ(t) the receive phase noise,
φi(t) the corrisponding phase noise at the transmitter (indipendent
of the phase noise process θ(t)),
τi the relative delays of packets transmitted by different users,
w(t) the additive white Gaussian noise.
16/32 Techniques for interference mitigationin satellite communications Yuri Zanettini](https://image.slidesharecdn.com/presentazione-181130014057/85/Techniques-for-interference-mitigation-in-satellite-communications-18-320.jpg)
![Introduction Interference Exploitation by Design Interference Management “Alto apprendistato”
LoRaWAN Network
Doppler effect
The Doppler shift and Doppler rate are computed as
ν(t) = −f0
c
REd sin(∆ψ(t)) cos cos−1 RE
d
cos(θ) −θ
vsat
d
R2
E+d2−2REd cos(∆ψ(t)) cos cos−1 RE
d
cos(θ) −θ
α(t) = d
dt
ν(t)
Doppler shift has to be cumulated with oscillator frequency instability
Doppler rate comparable to the frequency separation between symbols
[4] I. Ali, N. Al-Dhahir, J. E. Hershey, “Doppler characterization for LEO satellites”, IEEE Trans. Commun., vol. 46, pp. 309–313, Mar. 1998.
16/32 Techniques for interference mitigationin satellite communications Yuri Zanettini](https://image.slidesharecdn.com/presentazione-181130014057/85/Techniques-for-interference-mitigation-in-satellite-communications-20-320.jpg)
![Introduction Interference Exploitation by Design Interference Management “Alto apprendistato”
Receiver
Cubesat
Expandable modular
architecture
1U: 10 × 10 × 10 cm
Proposed receiver
Directional antennas (helical, G ≈ 12.4 dB)
Different swaths
[5] G. Colavolpe, T. Foggi, M. Ricciulli, Y. Zanettini, “Reception of LoRa signals from LEO satellites”, patent assigned to Inmarsat, sent
to the patent attorney for further processing.
18/32 Techniques for interference mitigationin satellite communications Yuri Zanettini](https://image.slidesharecdn.com/presentazione-181130014057/85/Techniques-for-interference-mitigation-in-satellite-communications-22-320.jpg)
![Introduction Interference Exploitation by Design Interference Management “Alto apprendistato”
Numerical Results
Assumptions
All users are uniformly distributed within the entire FoV
No interference coming from other services in the same unlicensed
bandwidth is considered
Link budget
CNR values required to achieve a BER = 10−5
over AWGN channel and
in absence of interfering signals and packet collisions
PFSK
b ≈ 2SF −1
Q
C
N
2SF
rc
SF 7 8 9 10 11 12
C/N [dB] −6.9 −9.7 −12.5 −15.3 −18.1 −20.9
Distribution of SFs
SF 7 8 9 10 11 12
p 0 16/31 8/31 4/31 2/31 1/31
19/32 Techniques for interference mitigationin satellite communications Yuri Zanettini](https://image.slidesharecdn.com/presentazione-181130014057/85/Techniques-for-interference-mitigation-in-satellite-communications-23-320.jpg)