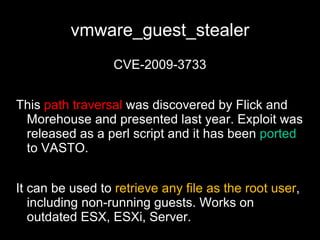
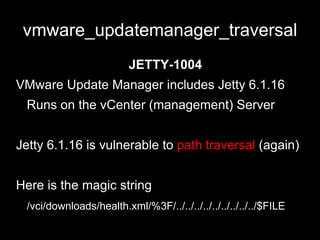
The document discusses attacking virtualization infrastructure through various exploits. It presents the Virtualization ASsessment TOolkit (VASTO) which is an exploit pack focusing on virtualization and cloud security. It then demonstrates several exploits against VMware virtualization software, including path traversal exploits, session hijacking, and code execution exploits affecting the vCenter management console, ESXi hypervisor, and supporting services. The talk encourages testing these attacks to better understand vulnerabilities in virtualization platforms.













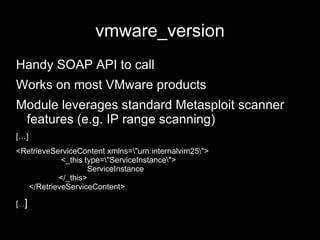

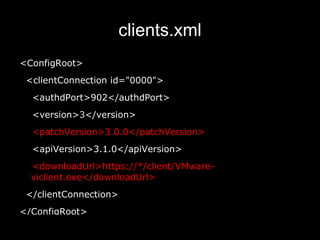
![vmware_version Handy SOAP API to call Works on most VMware products Module leverages standard Metasploit scanner features (e.g. IP range scanning) […] <RetrieveServiceContent xmlns=\"urn:internalvim25\"> <_this type=\"ServiceInstance\"> ServiceInstance </_this> </RetrieveServiceContent> [ … ]](https://image.slidesharecdn.com/bh10-virtuallypwnedlast-100817040936-phpapp01/85/Virtually-Pwned-20-320.jpg)








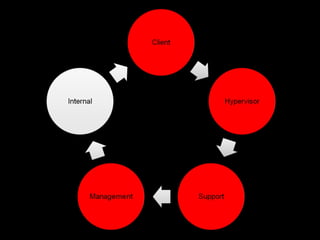




![Management is not just interface vCenter connects to ESX server via SSL [SOAP] Certificates are usually not trusted, but stored. MITM Connection Broken On reconnection, the vCenter will check for the certificate CN Spoof the CN Admin gets usual warning Admin agrees password sniffed](https://image.slidesharecdn.com/bh10-virtuallypwnedlast-100817040936-phpapp01/85/Virtually-Pwned-44-320.jpg)