Security and Your Business
•
1 like•239 views
Don’t be next! More and more security breaches are happening every day. Regardless if you are a small, medium, or large company, the risk is always there. Don’t believe us? Take a look at our infographic and check out some of the eye-opening stats!
Report
Share
Report
Share
Download to read offline
Recommended
Palo Alto Networks 2016 Cybersecurity Predictions

Palo Alto Networks experts make their predictions for cybersecurity trends in 2016.
How to Gather Global Mobile Threat Intelligence

Zimperium's Tuesday presentation at Deutsche Telekom's Magenta Security Summit. To gather mobile threat intelligence you must enable your mobile devices with mobile threat sensors.
Is the financial services industry vulnerable to constant cyber attacks

S21sec is a leading company in services and technology of Cybersecurity, shared the trends that are experienced in terms of cyber attacks, which suffers almost all over the world. These trends are the result of updating your annual predictions, which are accurate. This sets off the alarm to be alert to new and more advanced attacks, especially in the banking and retail industries.
Mobile Protect Pro - Powered by Zimperium

Zimperium's Mobile Protect Pro presentation at Deutsche Telekom's Magenta Security Summit in Frankfurt, Germany.
Mobile Security: Perceptions vs Device-harvested Reality

Research results from a 2017 mobile security study of over 1,900 cybersecurity professionals on their perceptions of mobile risks and threats. In contrast, Zimperium provides data from its Global Threat Intelligence on the realities of mobile risks and threats seen on mobile devices.
Four Network Security Challenges for the Cloud Generation

Users are everywhere and need quick access to data and cloud applications around the clock. Your network protection must balance security, performance, complexity, and cost. Symantec Web Security Services protects you with uncompromised network security, delivered from the cloud.
Recommended
Palo Alto Networks 2016 Cybersecurity Predictions

Palo Alto Networks experts make their predictions for cybersecurity trends in 2016.
How to Gather Global Mobile Threat Intelligence

Zimperium's Tuesday presentation at Deutsche Telekom's Magenta Security Summit. To gather mobile threat intelligence you must enable your mobile devices with mobile threat sensors.
Is the financial services industry vulnerable to constant cyber attacks

S21sec is a leading company in services and technology of Cybersecurity, shared the trends that are experienced in terms of cyber attacks, which suffers almost all over the world. These trends are the result of updating your annual predictions, which are accurate. This sets off the alarm to be alert to new and more advanced attacks, especially in the banking and retail industries.
Mobile Protect Pro - Powered by Zimperium

Zimperium's Mobile Protect Pro presentation at Deutsche Telekom's Magenta Security Summit in Frankfurt, Germany.
Mobile Security: Perceptions vs Device-harvested Reality

Research results from a 2017 mobile security study of over 1,900 cybersecurity professionals on their perceptions of mobile risks and threats. In contrast, Zimperium provides data from its Global Threat Intelligence on the realities of mobile risks and threats seen on mobile devices.
Four Network Security Challenges for the Cloud Generation

Users are everywhere and need quick access to data and cloud applications around the clock. Your network protection must balance security, performance, complexity, and cost. Symantec Web Security Services protects you with uncompromised network security, delivered from the cloud.
Why Your Mobile Device Isn’t As Secure As You Think

Most people have the illusion that phones are somehow impervious to viruses and that you are safe browsing virtually anything online. Not so. Mobile usage is growing fast, and it is only going to get bigger in 2014 and beyond.
Top Seven Risks of Enterprise Mobility - How to protect your business

Learn about the top risks associated with mobile devices in the enterprise environment and the steps you can take to mitigate these risks and protect your business
Cybersecurity threats you should know about in 2018

To keep up with the always evolving landscape, the
Security Intelligence Report provides a thorough analysis of security threats and how to best mitigate the top attack types.
Deutsche Telekom Partnering Operating Alliance Summit - Zimperium

Zimperium's presentation at Deutsche Telekom's Operator Partner Summit at Hub:Raum in Berlin, Germany.
Protecting Americas Next Generation Networks

The wireless industry has baked security into our networks since the beginning, and works diligently to continually update and build on our security capabilities with every generation of wireless. Today’s 4G LTE networks have the most advanced security features to date, and 5G will further improve upon them.
The Seven Kinds of Security

Enterprises are constantly working to implement new, faster, better technology to run their businesses. In turn, cyberattackers are working equally as hard to find ways to breach that technology, and security professionals are churning out solutions to thwart attacks. This cycle of activity leads to today’s layered, complex enterprise security ecosystems. These ecosystems are like any ecosystem in the natural world, with interdependencies, limited resources, and a need for balance to make them run smoothly. If one layer falters, the whole ecosystem can become unstable.
With the recent introduction of applications as a business driver, the security ecosystem needs to adapt. The application layer is now a critical player, and requires a reworking of the ecosystem to restore balance and security. However, this reworking has yet to happen in many cases, leading to the surge of breaches we’ve seen lately. End-point and network security tend to garner the lion’s share of IT attention – leading to an unbalanced security ecosystem, an exposed application layer, and serious breaches.
It is important to understand all the layers of security and how they work together to secure your enterprise. Start by getting the facts and stats with our new gbook, The Seven Kinds of Security.
Cyber security threats for 2017

The current presentation is based on different Cyber Security Threats for 2017 published in Internet. All threats are explained at a high level but at the end of this presentation all references URL are present if you want to investigate deeply any threat.
Symantec Internet Security Threat Report 2014 - Volume 19

The 2014 Internet Security Threat Report gives an overview of global threat activity for the past year based on data from Symantec’s Global Intelligence Network.
The state of mobile app security 

This infographic talks about the latest in mobile app security, the challenges and the best practices to tackle them by building secure mobile apps.
Cybersecurity

this is simple cybersecurity presentation. the template is from templatewise.com website
Cyber Security Analytics – The Weapon to Fight Cyber Crime 

Cyber security is utmost essential for corporates to function without any hassle and obstacles. One by one all corporates have begun to realize the importance of security from attacks and what makes the situation even worse is the increase in network world. Unfortunately, some companies do not realize the grievant nature of cyber-attacks and the unquestioned importance of Cyber Security.
The Internet of things paradox

The Home Security: Internet of Things Paradox. Is home security really secure?
Securing data flow to and from organizations

Presented by Benny Czarny, OPSWAT CEO, at INSS Workshop 2013
Protecting Your Business - All Covered Security Services

All Covered is a nationwide provider of IT services and security. This presentation highlights the most essential factors that businesses need to be aware of when implementing their security plan. It shows how any company, regardless of size, is at risk with external, and internal, security threats.
Whether you own a small, medium, or large business, IT security should be at the forefront of any discussion. It is better to be proactive and prevent an attack from happening than having to pick up the pieces after the damage has already been done to your business.
More Related Content
What's hot
Why Your Mobile Device Isn’t As Secure As You Think

Most people have the illusion that phones are somehow impervious to viruses and that you are safe browsing virtually anything online. Not so. Mobile usage is growing fast, and it is only going to get bigger in 2014 and beyond.
Top Seven Risks of Enterprise Mobility - How to protect your business

Learn about the top risks associated with mobile devices in the enterprise environment and the steps you can take to mitigate these risks and protect your business
Cybersecurity threats you should know about in 2018

To keep up with the always evolving landscape, the
Security Intelligence Report provides a thorough analysis of security threats and how to best mitigate the top attack types.
Deutsche Telekom Partnering Operating Alliance Summit - Zimperium

Zimperium's presentation at Deutsche Telekom's Operator Partner Summit at Hub:Raum in Berlin, Germany.
Protecting Americas Next Generation Networks

The wireless industry has baked security into our networks since the beginning, and works diligently to continually update and build on our security capabilities with every generation of wireless. Today’s 4G LTE networks have the most advanced security features to date, and 5G will further improve upon them.
The Seven Kinds of Security

Enterprises are constantly working to implement new, faster, better technology to run their businesses. In turn, cyberattackers are working equally as hard to find ways to breach that technology, and security professionals are churning out solutions to thwart attacks. This cycle of activity leads to today’s layered, complex enterprise security ecosystems. These ecosystems are like any ecosystem in the natural world, with interdependencies, limited resources, and a need for balance to make them run smoothly. If one layer falters, the whole ecosystem can become unstable.
With the recent introduction of applications as a business driver, the security ecosystem needs to adapt. The application layer is now a critical player, and requires a reworking of the ecosystem to restore balance and security. However, this reworking has yet to happen in many cases, leading to the surge of breaches we’ve seen lately. End-point and network security tend to garner the lion’s share of IT attention – leading to an unbalanced security ecosystem, an exposed application layer, and serious breaches.
It is important to understand all the layers of security and how they work together to secure your enterprise. Start by getting the facts and stats with our new gbook, The Seven Kinds of Security.
Cyber security threats for 2017

The current presentation is based on different Cyber Security Threats for 2017 published in Internet. All threats are explained at a high level but at the end of this presentation all references URL are present if you want to investigate deeply any threat.
Symantec Internet Security Threat Report 2014 - Volume 19

The 2014 Internet Security Threat Report gives an overview of global threat activity for the past year based on data from Symantec’s Global Intelligence Network.
The state of mobile app security 

This infographic talks about the latest in mobile app security, the challenges and the best practices to tackle them by building secure mobile apps.
Cybersecurity

this is simple cybersecurity presentation. the template is from templatewise.com website
Cyber Security Analytics – The Weapon to Fight Cyber Crime 

Cyber security is utmost essential for corporates to function without any hassle and obstacles. One by one all corporates have begun to realize the importance of security from attacks and what makes the situation even worse is the increase in network world. Unfortunately, some companies do not realize the grievant nature of cyber-attacks and the unquestioned importance of Cyber Security.
The Internet of things paradox

The Home Security: Internet of Things Paradox. Is home security really secure?
Securing data flow to and from organizations

Presented by Benny Czarny, OPSWAT CEO, at INSS Workshop 2013
What's hot (20)
Why Your Mobile Device Isn’t As Secure As You Think

Why Your Mobile Device Isn’t As Secure As You Think
Top Seven Risks of Enterprise Mobility - How to protect your business

Top Seven Risks of Enterprise Mobility - How to protect your business
Cybersecurity threats you should know about in 2018

Cybersecurity threats you should know about in 2018
Deutsche Telekom Partnering Operating Alliance Summit - Zimperium

Deutsche Telekom Partnering Operating Alliance Summit - Zimperium
Ms810 assignment viruses and malware affecting moblie devices

Ms810 assignment viruses and malware affecting moblie devices
Symantec Internet Security Threat Report 2014 - Volume 19

Symantec Internet Security Threat Report 2014 - Volume 19
Lookout Mobile Endpoint Security Datasheet (US - v2.5)

Lookout Mobile Endpoint Security Datasheet (US - v2.5)
Cyber Security Analytics – The Weapon to Fight Cyber Crime 

Cyber Security Analytics – The Weapon to Fight Cyber Crime
Viewers also liked
Protecting Your Business - All Covered Security Services

All Covered is a nationwide provider of IT services and security. This presentation highlights the most essential factors that businesses need to be aware of when implementing their security plan. It shows how any company, regardless of size, is at risk with external, and internal, security threats.
Whether you own a small, medium, or large business, IT security should be at the forefront of any discussion. It is better to be proactive and prevent an attack from happening than having to pick up the pieces after the damage has already been done to your business.
The Cloud Revolution

Did you know that 75% of IT managers report they are currently using or evaluating cloud computing? If you’re still on the fence about having your business join the cloud revolution, check out our infographic to learn what the cloud can do for your bottom line.
Are You Ready To Join The Cloud Revolution?

Here is the deck from All Covered's "Joining The Cloud Revolution" webinar in case you missed it. It discusses what the cloud is, how it works, the benefits of it, how the industry has evolved, success stories, and much much more!
The webinar recording is included at the end of the deck!
Quality manegment

This presentation is based of quality Management with the Productivity of any types of production ( Mobile Manufacturing,Mechanical Parts Manufacturing etc.)
indian railway signal system ppt

it is railway signal and communication system based power point presentation.
Viewers also liked (13)
Protecting Your Business - All Covered Security Services

Protecting Your Business - All Covered Security Services
Similar to Security and Your Business
The Top Five Cybersecurity Trends In 2023

Cybersecurity is a fast-evolving area. Here, we look at the most important trends to watch out for in 2023, including the increased threats from connected IoT devices, hybrid working, and state-sponsored attacks.
5 Cybersecurity threats in Public Sector

This SlideShare takes you through the top 5 cybersecurity threats in Public Sector.
ATS Connection.pdf

ATS Connection
15, Old Printing House Square, Tarrant St, Arundel BN18 9JH, United Kingdom
+441903255159
https://atsconnection.co.uk/
https://www.google.com/maps?cid=6871096897964695418
Microsoft Digital Crimes Unit

A safer digital experience for every person and organization on the planet.
Data security for healthcare industry

This slideshare takes you through the most pertinent risks that plague the healthcare industry.
Top 5 Cybersecurity Threats in Retail Industry

Retail industry is growing at a very fast pace. This slideshare takes you through the security threats in retail industry.
cyber security services | MasGlobal Services

MasGlobal is a one-stop shop for cyber security consulting services in the USA. We provide cyber security services to protect systems, networks, programs, devices, and data from cyberattacks.
For more information: https://www.masglobalservices.com/services/
Top 10 Cybersecurity Trends to Watch Out For in 2022

With the Digital revolution around all businesses, small or large, corporates, organizations and even governments are relying on computerized systems to manage their day-to-day activities and thus making cybersecurity a primary goal to safeguard data from various online attacks or any unauthorized access. Continuous change in technologies also implies a parallel shift in cybersecurity trends as news of data breach, ransomware and hacks become the norms. Here are the top cybersecurity trends for 2022.
IS Decisions Company Overview. Solutions to secure your Windows Network.

IS Decisions address specific but important gaps in managing the security of Microsoft Windows & Active Directory Infrastructures. We are focused on providing solutions to prevent and mitigate insider threat breaches that take security controls beyond what’s available in native Windows functionality.
Our solutions also facilitate/automate many of the often tedious but necessary tasks associated with user access control, access monitoring, file access auditing, server & desktop reporting, patches & remote installations - saving time & money for organizations.
Some figures about IS Decisions. With insider threats emerging as one of the biggest risks to corporate data we’ve seen that more and more organizations are recognizing the need for security solutions to help prevent data breaches from inappropriate user access, intentional or not.
Trust and confidence in IS Decisions solutions has been underlined with several prestigious clients. Customers include some of the most security-sensitive organizations around the world. However our solutions attract any organization that wants to enhance the security of their Windows network.
The 4 key areas where we help organizations are:
1. Prevent Security Breaches
2. Mitigate Insider Threats
3. Get Compliant
4. Quickly Respond in Emergency situations
SMB customers find our solutions to be fast, efficient & affordable. Large Government & Enterprise customers impressed with the ease of use in a high-risk and complex environment.
Find out more at www.isdecisions.com
AI IN CYBERSECURITY: THE NEW FRONTIER OF DIGITAL PROTECTION

Artificial Intelligence (AI) fortifies cybersecurity by dynamically identifying and neutralizing cyber threats. With machine learning algorithms, AI analyzes patterns in real-time data, swiftly detecting anomalies and potential security breaches. This proactive approach enhances the overall defense mechanism, ensuring robust protection against evolving cyber threats in the ever-changing digital landscape.
Why Should A Business Worry about Cyber Attacks?

In May 2017, Cybersecurity Malaysia confirm the "WannaCry" ransom ware attack spread across Malaysia.
The attack, which locks computers and holds users' files for ransom reported to hit 200,000 victims in 150
countries. The National Health Service reported the massive ransom ware attack shut down work at 16
hospitals across the United Kingdom. Hackers threaten to delete patient records and other critical files if
hospitals don’t pay them.
Network Security of Data Protection

Here is some knowledge of Network Security of Data Protection and some application knowledge
Similar to Security and Your Business (20)
Top 10 Cybersecurity Trends to Watch Out For in 2022

Top 10 Cybersecurity Trends to Watch Out For in 2022
IS Decisions Company Overview. Solutions to secure your Windows Network.

IS Decisions Company Overview. Solutions to secure your Windows Network.
AI IN CYBERSECURITY: THE NEW FRONTIER OF DIGITAL PROTECTION

AI IN CYBERSECURITY: THE NEW FRONTIER OF DIGITAL PROTECTION
Securing mobile devices in the business environment

Securing mobile devices in the business environment
What Are Cyber Attacks All About? | Cyberroot Risk Advisory

What Are Cyber Attacks All About? | Cyberroot Risk Advisory
Recently uploaded
Improving profitability for small business

In this comprehensive presentation, we will explore strategies and practical tips for enhancing profitability in small businesses. Tailored to meet the unique challenges faced by small enterprises, this session covers various aspects that directly impact the bottom line. Attendees will learn how to optimize operational efficiency, manage expenses, and increase revenue through innovative marketing and customer engagement techniques.
Lookback Analysis

Explore our most comprehensive guide on lookback analysis at SafePaaS, covering access governance and how it can transform modern ERP audits. Browse now!
Attending a job Interview for B1 and B2 Englsih learners

It is a sample of an interview for a business english class for pre-intermediate and intermediate english students with emphasis on the speking ability.
Accpac to QuickBooks Conversion Navigating the Transition with Online Account...

This article provides a comprehensive guide on how to
effectively manage the convert Accpac to QuickBooks , with a particular focus on utilizing online accounting services to streamline the process.
Global Interconnection Group Joint Venture[960] (1).pdf![Global Interconnection Group Joint Venture[960] (1).pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Global Interconnection Group Joint Venture[960] (1).pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Global Interconnection Group Joint Venture[960] (1).pdf
The Parable of the Pipeline a book every new businessman or business student ...

The-Parable of the Pipeline a book every new businessman or business student must read before diving into real world of business.
RMD24 | Debunking the non-endemic revenue myth Marvin Vacquier Droop | First ...

Marvin neemt je in deze presentatie mee in de voordelen van non-endemic advertising op retail media netwerken. Hij brengt ook de uitdagingen in beeld die de markt op dit moment heeft op het gebied van retail media voor niet-leveranciers.
Retail media wordt gezien als het nieuwe advertising-medium en ook mediabureaus richten massaal retail media-afdelingen op. Merken die niet in de betreffende winkel liggen staan ook nog niet in de rij om op de retail media netwerken te adverteren. Marvin belicht de uitdagingen die er zijn om echt aansluiting te vinden op die markt van non-endemic advertising.
Digital Transformation in PLM - WHAT and HOW - for distribution.pdf

Presentation describing the Digital Transformation for PLM in the context of a Dassault Systemes portfolio.
Taurus Zodiac Sign_ Personality Traits and Sign Dates.pptx

Explore the world of the Taurus zodiac sign. Learn about their stability, determination, and appreciation for beauty. Discover how Taureans' grounded nature and hardworking mindset define their unique personality.
Business Valuation Principles for Entrepreneurs

This insightful presentation is designed to equip entrepreneurs with the essential knowledge and tools needed to accurately value their businesses. Understanding business valuation is crucial for making informed decisions, whether you're seeking investment, planning to sell, or simply want to gauge your company's worth.
falcon-invoice-discounting-a-premier-platform-for-investors-in-india

Falcon stands out as a top-tier P2P Invoice Discounting platform in India, bridging esteemed blue-chip companies and eager investors. Our goal is to transform the investment landscape in India by establishing a comprehensive destination for borrowers and investors with diverse profiles and needs, all while minimizing risk. What sets Falcon apart is the elimination of intermediaries such as commercial banks and depository institutions, allowing investors to enjoy higher yields.
Premium MEAN Stack Development Solutions for Modern Businesses

Stay ahead of the curve with our premium MEAN Stack Development Solutions. Our expert developers utilize MongoDB, Express.js, AngularJS, and Node.js to create modern and responsive web applications. Trust us for cutting-edge solutions that drive your business growth and success.
Know more: https://www.synapseindia.com/technology/mean-stack-development-company.html
3.0 Project 2_ Developing My Brand Identity Kit.pptx

A personal brand exploration presentation summarizes an individual's unique qualities and goals, covering strengths, values, passions, and target audience. It helps individuals understand what makes them stand out, their desired image, and how they aim to achieve it.
Search Disrupted Google’s Leaked Documents Rock the SEO World.pdf

The world of search engine optimization (SEO) is buzzing with discussions after Google confirmed that around 2,500 leaked internal documents related to its Search feature are indeed authentic. The revelation has sparked significant concerns within the SEO community. The leaked documents were initially reported by SEO experts Rand Fishkin and Mike King, igniting widespread analysis and discourse. For More Info:- https://news.arihantwebtech.com/search-disrupted-googles-leaked-documents-rock-the-seo-world/
Pitch Deck Teardown: RAW Dating App's $3M Angel deck

Pitch Deck Teardown: RAW Dating App's $3M Angel deck
India Orthopedic Devices Market: Unlocking Growth Secrets, Trends and Develop...

According to TechSci Research report, “India Orthopedic Devices Market -Industry Size, Share, Trends, Competition Forecast & Opportunities, 2030”, the India Orthopedic Devices Market stood at USD 1,280.54 Million in 2024 and is anticipated to grow with a CAGR of 7.84% in the forecast period, 2026-2030F. The India Orthopedic Devices Market is being driven by several factors. The most prominent ones include an increase in the elderly population, who are more prone to orthopedic conditions such as osteoporosis and arthritis. Moreover, the rise in sports injuries and road accidents are also contributing to the demand for orthopedic devices. Advances in technology and the introduction of innovative implants and prosthetics have further propelled the market growth. Additionally, government initiatives aimed at improving healthcare infrastructure and the increasing prevalence of lifestyle diseases have led to an upward trend in orthopedic surgeries, thereby fueling the market demand for these devices.
Affordable Stationery Printing Services in Jaipur | Navpack n Print

Looking for professional printing services in Jaipur? Navpack n Print offers high-quality and affordable stationery printing for all your business needs. Stand out with custom stationery designs and fast turnaround times. Contact us today for a quote!
Recently uploaded (20)
Set off and carry forward of losses and assessment of individuals.pptx

Set off and carry forward of losses and assessment of individuals.pptx
Attending a job Interview for B1 and B2 Englsih learners

Attending a job Interview for B1 and B2 Englsih learners
Accpac to QuickBooks Conversion Navigating the Transition with Online Account...

Accpac to QuickBooks Conversion Navigating the Transition with Online Account...
Global Interconnection Group Joint Venture[960] (1).pdf![Global Interconnection Group Joint Venture[960] (1).pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Global Interconnection Group Joint Venture[960] (1).pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Global Interconnection Group Joint Venture[960] (1).pdf
The Parable of the Pipeline a book every new businessman or business student ...

The Parable of the Pipeline a book every new businessman or business student ...
RMD24 | Debunking the non-endemic revenue myth Marvin Vacquier Droop | First ...

RMD24 | Debunking the non-endemic revenue myth Marvin Vacquier Droop | First ...
Digital Transformation in PLM - WHAT and HOW - for distribution.pdf

Digital Transformation in PLM - WHAT and HOW - for distribution.pdf
Taurus Zodiac Sign_ Personality Traits and Sign Dates.pptx

Taurus Zodiac Sign_ Personality Traits and Sign Dates.pptx
falcon-invoice-discounting-a-premier-platform-for-investors-in-india

falcon-invoice-discounting-a-premier-platform-for-investors-in-india
Premium MEAN Stack Development Solutions for Modern Businesses

Premium MEAN Stack Development Solutions for Modern Businesses
3.0 Project 2_ Developing My Brand Identity Kit.pptx

3.0 Project 2_ Developing My Brand Identity Kit.pptx
Search Disrupted Google’s Leaked Documents Rock the SEO World.pdf

Search Disrupted Google’s Leaked Documents Rock the SEO World.pdf
Pitch Deck Teardown: RAW Dating App's $3M Angel deck

Pitch Deck Teardown: RAW Dating App's $3M Angel deck
India Orthopedic Devices Market: Unlocking Growth Secrets, Trends and Develop...

India Orthopedic Devices Market: Unlocking Growth Secrets, Trends and Develop...
Affordable Stationery Printing Services in Jaipur | Navpack n Print

Affordable Stationery Printing Services in Jaipur | Navpack n Print
Security and Your Business
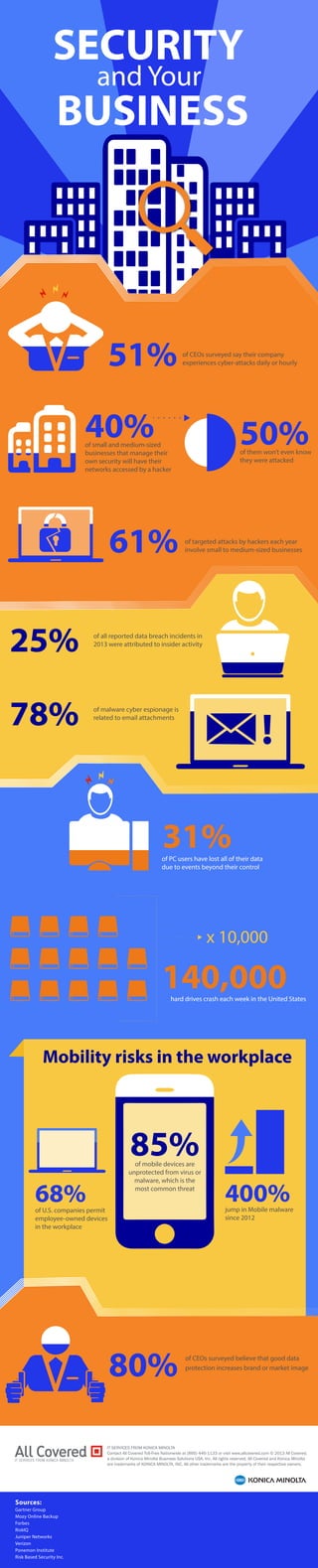
- 1. SECURITY and Your BUSINESS of all reported data breach incidents in 2013 were attributed to insider activity of malware cyber espionage is related to email attachments 31% 50% of them won’t even know they were attacked of PC users have lost all of their data due to events beyond their control x 10,000 40% of small and medium-sized businesses that manage their own security will have their networks accessed by a hacker 140,000 Mobility risks in the workplace IT SERVICES FROM KONICA MINOLTA Contact All Covered Toll-Free Nationwide at (866) 446-1133 or visit www.allcovered.com © 2013 All Covered, a division of Konica Minolta Business Solutions USA, Inc. All rights reserved. All Covered and Konica Minolta are trademarks of KONICA MINOLTA, INC. All other trademarks are the property of their respective owners. Sources: Gartner Group Mozy Online Backup Forbes RiskIQ Juniper Networks Verizon Ponemon Institute Risk Based Security Inc. of targeted attacks by hackers each year involve small to medium-sized businesses 85% of mobile devices are unprotected from virus or malware, which is the 68% most common threat of U.S. companies permit employee-owned devices in the workplace 400% jump in Mobile malware since 2012 51% 61% of CEOs surveyed say their company experiences cyber-attacks daily or hourly hard drives crash each week in the United States 25% 78% 80% of CEOs surveyed believe that good data protection increases brand or market image
