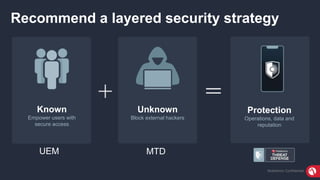
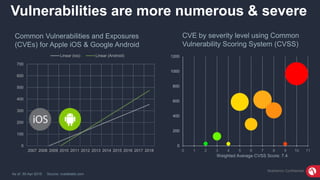
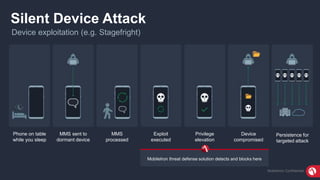
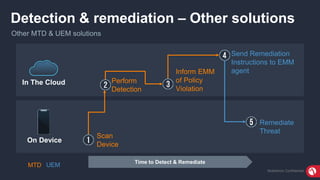
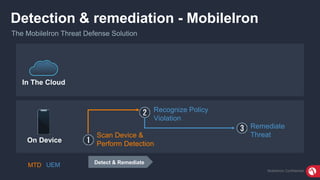
The document discusses the importance of mobile security, highlighting that many organizations are unprotected due to inadequate policies and understanding of threats. It introduces the MobileIron Threat Defense solution, which provides a layered security strategy to detect and block various threats, including device, network, and application vulnerabilities. The solution aims to minimize data loss risk and enhance visibility into mobile threats while ensuring compliance with security regulations.