A Rise of Citizen Application Developers
•
0 likes•316 views
A rise of citizen application developers poses data, security and integration challenges. Additionally, three out of four IT decision makers believe an enterprise low-code platform is the solution to mitigate risks. Learn more about empowering Citizen Developers with low-code: http://ap.pn/2lbSmVF
Report
Share
Report
Share
Download to read offline
Recommended
Infographic 2014 smart_grid_cybersecurity_survey_smart_modular_technologies_z...

Infographic 2014 smart_grid_cybersecurity_survey_smart_modular_technologies_z...Massimiliano Mandolini
Recommended
Infographic 2014 smart_grid_cybersecurity_survey_smart_modular_technologies_z...

Infographic 2014 smart_grid_cybersecurity_survey_smart_modular_technologies_z...Massimiliano Mandolini
More Related Content
What's hot
What's hot (20)
The Challenge of Managing & Securing Data in the Mobile World. By Stuart Chev...

The Challenge of Managing & Securing Data in the Mobile World. By Stuart Chev...
The Stand Against Cyber Criminals Lawyers, Take The Stand Against Cyber Crimi...

The Stand Against Cyber Criminals Lawyers, Take The Stand Against Cyber Crimi...
Realizing the Promise of the Mobile Workforce through a Mobile Device Platfor...

Realizing the Promise of the Mobile Workforce through a Mobile Device Platfor...
Infographic: Mobile is growing and so are security threats

Infographic: Mobile is growing and so are security threats
Retail Industry Application Security Survey Insights

Retail Industry Application Security Survey Insights
The Internet of Security Things (A Story about Change) 

The Internet of Security Things (A Story about Change)
Similar to A Rise of Citizen Application Developers
Similar to A Rise of Citizen Application Developers (20)
Nube, Cumplimiento y Amenazas avanzadas: Consideraciones de Seguridad para la...

Nube, Cumplimiento y Amenazas avanzadas: Consideraciones de Seguridad para la...
Perception Gaps in Cyber Resilience: What Are Your Blind Spots?

Perception Gaps in Cyber Resilience: What Are Your Blind Spots?
Federal Webinar: Leverage IT Operations Monitoring and Log Data to Reduce Ins...

Federal Webinar: Leverage IT Operations Monitoring and Log Data to Reduce Ins...
application-security-fallacies-and-realities-veracode

application-security-fallacies-and-realities-veracode
Cloud Security - What you Should Be Concerned About

Cloud Security - What you Should Be Concerned About
The top challenges to expect in network security in 2019 survey report 

The top challenges to expect in network security in 2019 survey report
Apperian 2015 Executive Enterprise Mobility Survey

Apperian 2015 Executive Enterprise Mobility Survey
More from Appian
More from Appian (20)
How to Transform Contact Centers into Profit Centers

How to Transform Contact Centers into Profit Centers
Modernize Your Acquisition Platform Through Digital Transformation

Modernize Your Acquisition Platform Through Digital Transformation
How Manufacturers Can Drive Efficiency With Interconnected Processes

How Manufacturers Can Drive Efficiency With Interconnected Processes
The Key to Successful Digital Transformation in Life Sciences

The Key to Successful Digital Transformation in Life Sciences
Why Contact Center Operators Need to Take Advantage of Intelligent Automation

Why Contact Center Operators Need to Take Advantage of Intelligent Automation
How Digital Will Impact the Federal Government this Year

How Digital Will Impact the Federal Government this Year
5 Questions Financial Institutions Should Ask About GDPR Readiness

5 Questions Financial Institutions Should Ask About GDPR Readiness
How to Simplify and Streamline Process Improvement with BPM

How to Simplify and Streamline Process Improvement with BPM
Keeping the Banking Customer at the Center of the Transformation Journey

Keeping the Banking Customer at the Center of the Transformation Journey
Process Excellence Essential as Business Face Unrelenting Technological Change

Process Excellence Essential as Business Face Unrelenting Technological Change
Digital Transformation in Retail - How Brands are Preparing for the Holidays

Digital Transformation in Retail - How Brands are Preparing for the Holidays
Recently uploaded
Steps To Getting Up And Running Quickly With MyTimeClock Employee Scheduling ...

Steps To Getting Up And Running Quickly With MyTimeClock Employee Scheduling ...MyIntelliSource, Inc.
Try MyIntelliAccount Cloud Accounting Software As A Service Solution Risk Fre...

Try MyIntelliAccount Cloud Accounting Software As A Service Solution Risk Fre...MyIntelliSource, Inc.
Recently uploaded (20)
Steps To Getting Up And Running Quickly With MyTimeClock Employee Scheduling ...

Steps To Getting Up And Running Quickly With MyTimeClock Employee Scheduling ...
Building Real-Time Data Pipelines: Stream & Batch Processing workshop Slide

Building Real-Time Data Pipelines: Stream & Batch Processing workshop Slide
Adobe Marketo Engage Deep Dives: Using Webhooks to Transfer Data

Adobe Marketo Engage Deep Dives: Using Webhooks to Transfer Data
Automate your Kamailio Test Calls - Kamailio World 2024

Automate your Kamailio Test Calls - Kamailio World 2024
Alluxio Monthly Webinar | Cloud-Native Model Training on Distributed Data

Alluxio Monthly Webinar | Cloud-Native Model Training on Distributed Data
Try MyIntelliAccount Cloud Accounting Software As A Service Solution Risk Fre...

Try MyIntelliAccount Cloud Accounting Software As A Service Solution Risk Fre...
BATTLEFIELD ORM: TIPS, TACTICS AND STRATEGIES FOR CONQUERING YOUR DATABASE

BATTLEFIELD ORM: TIPS, TACTICS AND STRATEGIES FOR CONQUERING YOUR DATABASE
Professional Resume Template for Software Developers

Professional Resume Template for Software Developers
Building a General PDE Solving Framework with Symbolic-Numeric Scientific Mac...

Building a General PDE Solving Framework with Symbolic-Numeric Scientific Mac...
Advancing Engineering with AI through the Next Generation of Strategic Projec...

Advancing Engineering with AI through the Next Generation of Strategic Projec...
Short Story: Unveiling the Reasoning Abilities of Large Language Models by Ke...

Short Story: Unveiling the Reasoning Abilities of Large Language Models by Ke...
A Rise of Citizen Application Developers
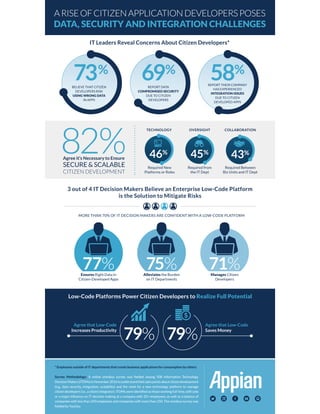
- 1. ARISEOFCITIZENAPPLICATIONDEVELOPERSPOSES DATA, SECURITY AND INTEGRATION CHALLENGES IT Leaders Reveal Concerns About Citizen Developers* 3 out of 4 IT Decision Makers Believe an Enterprise Low-Code Platform is the Solution to Mitigate Risks Agree it’s Necessary to Ensure SECURE & SCALABLE CITIZEN DEVELOPMENT 82% 73% 69% 58% REPORT THEIR COMPANY HAS EXPERIENCED INTEGRATION ISSUES DUE TO CITIZEN DEVELOPED APPS REPORT DATA COMPROMISED SECURITY DUE TO CITIZEN DEVELOPERS BELIEVE THAT CITIZEN DEVELOPERS RISK USING WRONG DATA IN APPS Required New Platforms or Roles TECHNOLOGY Required from the IT Dept OVERSIGHT Required Between Biz Units and IT Dept COLLABORATION 46% 45% 43% MORE THAN 70% OF IT DECISION MAKERS ARE CONFIDENT WITH A LOW-CODE PLATFORM Ensures Right Data in Citizen-Developed Apps 77% Alleviates the Burden on IT Departments 75% Manages Citizen Developers 71% Low-Code Platforms Power Citizen Developers to Realize Full Potential Agree that Low-Code Increases Productivity Agree that Low-Code Saves Money 79% 79% * Employees outside of IT departments that create business applications for consumption by others. Survey Methodology: A online omnibus survey was fielded among 508 Information Technology DecisionMakers(ITDMs)inNovember2016tounderstandtheirpainpointsaboutcitizendevelopment (e.g., data security, integration, scalability) and the need for a new technology platform to manage citizen developers (i.e., a citizen integrator). ITDMs were identified as those working full-time, with sole or a major influence on IT decision-making at a company with 20+ employees, as well as a balance of companies with less than 250 employees and companies with more than 250. The omnibus survey was fielded by YouGov.
