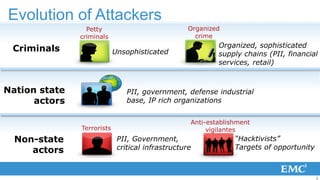
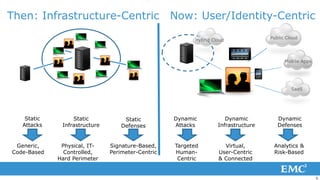
1) The threat landscape has evolved from petty criminals and hackers to sophisticated nation states, organized crime groups, and terrorists targeting personal information, critical infrastructure, and intellectual property.
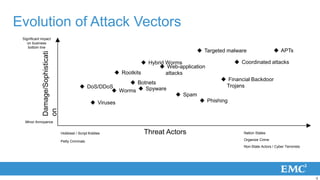
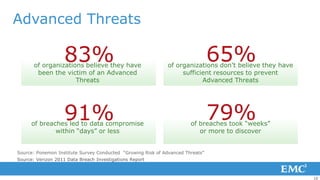
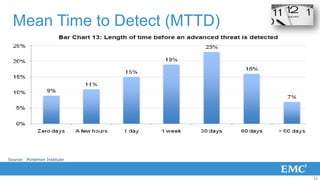
2) Attack vectors have advanced from viruses and malware to targeted attacks using techniques like advanced persistent threats, zero-day exploits, and coordinated multi-vector attacks.
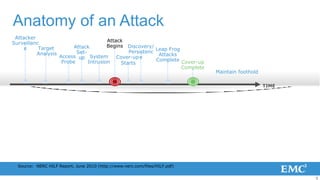
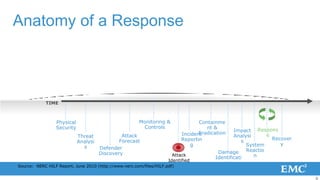
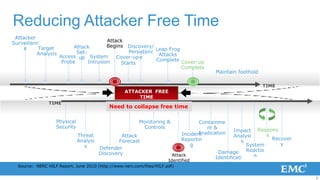
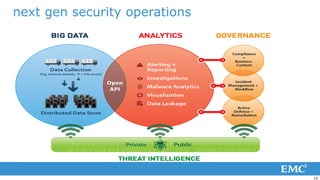
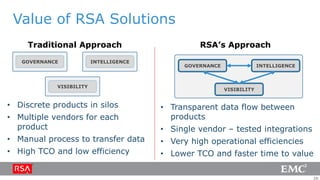
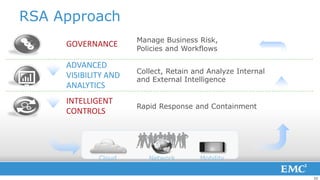
3) To reduce risk, organizations must collapse the time attackers have from initial access to establishing a long-term foothold through improved monitoring, rapid detection and response, and containment of incidents.