Tai lieu ky thuat lap trinh
•Download as DOC, PDF•
0 likes•456 views
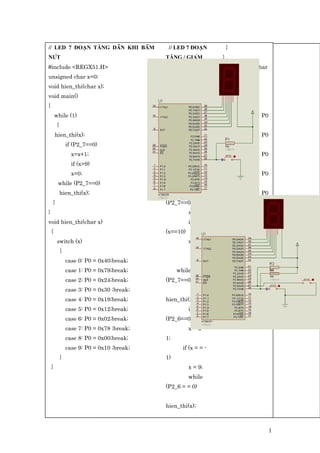
#include <regx51.h> unsigned char x=0; void hien_thi(char x); void main() { while (1) { hien_thi(x); if (P2_7==0) x=x+1; if (x>9) x=0; while (P2_7==0) hien_thi(x); } } void hien_thi(char x) { switch (x) { case 0: P0 = 0x40;break; case 1: P0 = 0x79;break; case 2: P0 = 0x24;break; case 3: P0 = 0x30 ;break; case 4: P0 = 0x19;break; case 5: P0 = 0x12;break; case 6: P0 = 0x02;break; case 7: P0 = 0x78 ;break; case 8: P0 = 0x00;break; case 9: P0 = 0x10 ;break; } }
Report
Share
Report
Share
Recommended
Cn os-lp lab manual k.roshan

1. The document provides a lab manual for computer networks and operating systems labs containing 8 programs to implement various networking and security algorithms.
2. The programs include implementing data link layer framing methods, CRC polynomials, Dijkstra's shortest path algorithm, distance vector routing, DES encryption, breaking the DES code, and RSA encryption/decryption.
3. The document contains instructions for 8 programs to implement computer network and security algorithms as part of a lab course covering topics like data link layer, routing, encryption, and public key cryptography.
Ejercicios de programacion

The document contains multiple C++ code examples for programming exercises. It includes code to generate and output matrices, sort vectors, loop through ranges printing values, and calculate averages of two digit numbers. Jefferson Caiza is listed as the student name for the programming course. The code examples demonstrate basic programming concepts like loops, arrays, conditionals, and math operations.
Asssignment2 

This document contains C++ code that implements various classical ciphers including Caesar cipher, Playfair cipher, Affine cipher, Autokey cipher, and Vigenere cipher. The code provides functions for encrypting and decrypting messages with each cipher. The main function allows a user to select which cipher to use and whether to encrypt or decrypt a message by entering inputs. It then calls the relevant encryption or decryption functions and displays the output.
C++ Lambda and concurrency

The document summarizes lambda expressions and concurrency APIs in C++. It provides examples of lambda expressions with different capture modes. It also discusses features of concurrency APIs like std::future, std::promise, std::packaged_task and how to use them to asynchronously execute tasks and retrieve/propagate results and exceptions.
computer graphics practicals

The document contains 10 programs for computer graphics operations including drawing graphics objects, 2D bars, pattern fills, pie charts, boundary fills, flood fills, translation, scaling, rotation, and window to viewport transformation. For each program, the code is provided to implement the specified graphics operation through functions like line(), circle(), rectangle(), bar(), pieslice(), bfill(), etc.
Os lab file c programs

This document contains 8 C programming code examples demonstrating various scheduling algorithms:
1. First Come First Serve scheduling
2. Non-preemptive Shortest Job First scheduling
3. Round Robin scheduling
4. Priority scheduling
5. Banker's algorithm for deadlock avoidance
6. Producer-consumer problem synchronization
7. Dekker's algorithm for mutual exclusion
Each program example includes comments explaining the algorithm and includes functions to calculate waiting times, turnaround times, and other metrics.
Потоки в перле изнутри

This document discusses Perl streams and provides code examples from Perl source code files. It contains code snippets from files related to process forking on Windows, thread handling, and cloning the Perl interpreter for new processes. The document also describes the structure of Perl source code directories and files.
R tist

The document describes several Arduino sketches. The first sketch uses an array of pin numbers to light up LEDs in sequence using a for loop. The second sketch uses an LM35 sensor to read temperature values from analog pin A0 and print them to the serial monitor. The third sketch stores the on/off patterns for the segments of a 7-segment display in an array and uses it to display counting from 10 to 0 on the display. The fourth sketch reads an analog temperature sensor value and writes it simultaneously to three PWM pins to control the brightness of three LEDs based on the temperature.
Recommended
Cn os-lp lab manual k.roshan

1. The document provides a lab manual for computer networks and operating systems labs containing 8 programs to implement various networking and security algorithms.
2. The programs include implementing data link layer framing methods, CRC polynomials, Dijkstra's shortest path algorithm, distance vector routing, DES encryption, breaking the DES code, and RSA encryption/decryption.
3. The document contains instructions for 8 programs to implement computer network and security algorithms as part of a lab course covering topics like data link layer, routing, encryption, and public key cryptography.
Ejercicios de programacion

The document contains multiple C++ code examples for programming exercises. It includes code to generate and output matrices, sort vectors, loop through ranges printing values, and calculate averages of two digit numbers. Jefferson Caiza is listed as the student name for the programming course. The code examples demonstrate basic programming concepts like loops, arrays, conditionals, and math operations.
Asssignment2 

This document contains C++ code that implements various classical ciphers including Caesar cipher, Playfair cipher, Affine cipher, Autokey cipher, and Vigenere cipher. The code provides functions for encrypting and decrypting messages with each cipher. The main function allows a user to select which cipher to use and whether to encrypt or decrypt a message by entering inputs. It then calls the relevant encryption or decryption functions and displays the output.
C++ Lambda and concurrency

The document summarizes lambda expressions and concurrency APIs in C++. It provides examples of lambda expressions with different capture modes. It also discusses features of concurrency APIs like std::future, std::promise, std::packaged_task and how to use them to asynchronously execute tasks and retrieve/propagate results and exceptions.
computer graphics practicals

The document contains 10 programs for computer graphics operations including drawing graphics objects, 2D bars, pattern fills, pie charts, boundary fills, flood fills, translation, scaling, rotation, and window to viewport transformation. For each program, the code is provided to implement the specified graphics operation through functions like line(), circle(), rectangle(), bar(), pieslice(), bfill(), etc.
Os lab file c programs

This document contains 8 C programming code examples demonstrating various scheduling algorithms:
1. First Come First Serve scheduling
2. Non-preemptive Shortest Job First scheduling
3. Round Robin scheduling
4. Priority scheduling
5. Banker's algorithm for deadlock avoidance
6. Producer-consumer problem synchronization
7. Dekker's algorithm for mutual exclusion
Each program example includes comments explaining the algorithm and includes functions to calculate waiting times, turnaround times, and other metrics.
Потоки в перле изнутри

This document discusses Perl streams and provides code examples from Perl source code files. It contains code snippets from files related to process forking on Windows, thread handling, and cloning the Perl interpreter for new processes. The document also describes the structure of Perl source code directories and files.
R tist

The document describes several Arduino sketches. The first sketch uses an array of pin numbers to light up LEDs in sequence using a for loop. The second sketch uses an LM35 sensor to read temperature values from analog pin A0 and print them to the serial monitor. The third sketch stores the on/off patterns for the segments of a 7-segment display in an array and uses it to display counting from 10 to 0 on the display. The fourth sketch reads an analog temperature sensor value and writes it simultaneously to three PWM pins to control the brightness of three LEDs based on the temperature.
Operating system and embedded systems

operating system is same as ARM controller.but, here we learn about optimization in terms of time,memory,size of the code.reducing one of these will be our main moto
3

This document discusses binary vulnerabilities and methods for identifying and exploiting them. It covers topics like stack overflows, heap overflows, integer overflows, and pointer vulnerabilities. It also discusses vulnerability metrics, identifiers, and tools that can be used for analysis like fuzzers, symbolic execution, and decompilers. Exploitation techniques like bypassing protections and transferring control are also mentioned.
Как работает LLVM бэкенд в C#. Егор Богатов ➠ CoreHard Autumn 2019

LLVM содержит огромное количество оптимизаций и подходит в качестве бэкенда для многих языков программирования. Но все немного усложняется для Managed языков и JIT сценариев. В этом докладе Егор расскажет о трудностях, с которыми столкнулись в C# при реализации LLVM бэкенда.
Алексей Кутумов, Coroutines everywhere

Не так давно Гор Нишанов представил свой доклад: C++ Coroutines a negative overhead abstraction. В этом докладе Гор упомянул, что предложенный дизайн корутин позволяет их использовать практически в любых окружениях, в том числе и с "бедным" C++ рантаймом.
Я решил попробовать запустить корутины в следующих окружениях: обычное приложение, драйвер ОС Windows, EFI приложение. Только в одном из этих окружений есть полноценный C++ рантайм и поддержка исключений, в остальных ничего этого нет. Более того, EFI приложение вообще выполняется до старта ОС.
Я хочу рассказать о том, как мне удалось запустить корутины в этих окружениях, поговорим о том, какие проблемы существуют в асинхронном системном программировании и как их можно обойти.
Nested micro

This document discusses macro nesting in C programming. It defines several macros, including nested macros where a macro name is used within the definition of another macro. It then shows an example program that defines macros, reads a text file containing additional macro definitions, builds a linked list of the macros, replaces nested macro names within values, and prints the final macro table.
Main Form Number To Word

This document contains C# code for a program that converts numbers to words. It includes a MainForm class with a button click event that calls the ConvertToWord class. The ConvertToWord class contains two methods: Convert, which takes a numeric string as input and returns the equivalent word string, and CharToWord and DigitToWord, which return the word representations of individual characters and digits based on their position in the number. The code uses arrays, loops, and switch statements to iterate through the input and build up the word string by concatenating the outputs of the character and digit conversion methods.
Go vs C++ - CppRussia 2019 Piter BoF

This document compares and contrasts various features of C++ and Go, including:
- Error handling approaches like exceptions in C++ vs explicit error checking in Go.
- Class/struct definitions and how they compare between the languages.
- Common data structures like vectors, maps, and how they are implemented in each language.
- Benchmark results that show Go outperforming C++ in some cases but C++ performing better in others, depending on optimizations and data structure choices.
- Interfacing Go with C via Cgo and the performance overhead of marshalling between the languages.
- Concurrency primitives available in each language like mutexes, channels, atomics.
C++の話(本当にあった怖い話)

The document discusses C++ and its history and features. It describes C++ as an extension of C with object-oriented features like classes. It provides information on the creator of C++, Bjarne Stroustrup, and the evolution of C++ since its introduction as a way to add object-oriented programming to C. It also includes sample C++ code demonstrating the use of arrays and includes from the Boost library.
Computer Programming- Lecture 4

The document discusses procedural abstraction and predefined functions in computer programming. It provides examples of for loops and nested for loops to iterate through ranges of values. The for loop examples demonstrate how the initialization, boolean expression, and update components work together to execute the loop body. Tracing is used to step through multiple iterations of the for loops.
Voce Tem Orgulho Do Seu Codigo

O quanto você está satisfeito com o código que produz? Mais ainda: o quanto você está satisfeito como profissional? Na busca pela melhoria de nossas aplicações, caímos num grande desafio: melhorar a nós mesmos!
Numa conversa franca e descontraída, Samuel e Victor tentarão apresentar idéias sobre como você pode melhorar seu próprio trabalho e sentir orgulho do que faz.
Java, Up to Date Sources

Source codes of the Presentation "Java, Up to Date", http://www.slideshare.net/akirakoyasu/java-up-to-date
Some examples of the 64-bit code errors

While porting 32-bit software to 64-bit systems there may appear some errors in the code of applications which were written in C++ language. The cause for these hides in the alteration of the base data types (to be more exact, in the relations between them) with the new hardware platform.
Percobaan 1

This program uses an ATmega8535 microcontroller to light up LEDs connected to port A in sequence when button 0 on port B is pressed and turn them off in reverse order when button 1 is pressed. It initializes ports A, B, C and D, sets port A pins as outputs and lights up each pin on port A for 50ms when button 0 is pressed, then turns them all off when button 1 is pressed also with a 50ms delay between each pin.
project3

The document contains code for an employee management system program written in C++. It defines structures to store employee data and functions to build, list, insert, delete, edit, search, and sort employee records. The main function calls these functions and includes a menu loop to allow the user to select different options for managing the employee database.
Bai Giang 11

The document discusses various ways to redefine operators and functions in C++. It covers redefining functions with the same name but different parameters, redefining operators for a class using member and non-member functions, converting between types when redefining operators, and redefining stream insertion and extraction operators.
TMPA-2017: Predicate Abstraction Based Configurable Method for Data Race Dete...

TMPA-2017: Tools and Methods of Program Analysis
3-4 March, 2017, Hotel Holiday Inn Moscow Vinogradovo, Moscow
Predicate Abstraction Based Configurable Method for Data Race Detection in Linux Kernel
Pavel Andrianov, Vadim Mutilin,Alexey Khoroshilov, Institute for System Programming
For video follow the link: https://youtu.be/SxDVQ7lSTqc
Would like to know more?
Visit our website:
www.tmpaconf.org
www.exactprosystems.com/events/tmpa
Follow us:
https://www.linkedin.com/company/exactpro-systems-llc?trk=biz-companies-cym
https://twitter.com/exactpro
Gaurav Jatav , BCA Third Year

This is a work by the student of BCA Department student from Third Year studying at Dezyne E'cole College,Ajmer
Breaking the wall

The document discusses different approaches tried to switch device certificates programmatically on iOS, including using NSURLConnection, GTMHTTPFetcher, and ASIHTTPRequest. It also describes some hacks that worked like using the IP address instead of the hostname and adding a period to the hostname. The document appears to be technical notes on trying to authenticate and switch certificates during an HTTPS connection on iOS.
Server

This document contains C code for creating a basic TCP server socket that listens for connections from clients and allows for bidirectional communication by reading from and writing to the client socket file descriptor. The code binds the server socket to port 4020 on IP address 10.180.5.196, accepts an incoming connection, and then enters a loop to continuously read messages from the client and write responses until the client sends the string "bye".
Tere 

The document discusses the benefits of exercise for mental health. Regular physical activity can help reduce anxiety and depression and improve mood and cognitive functioning. Exercise causes chemical changes in the brain that may help boost feelings of calmness, happiness and focus.
CEIP Alcalde Rafael Cedrés - Día de La Infancia

El documento describe el programa de la semana del Día de la Infancia en el colegio Ceip Alcalde Rafael Cedrés. Los estudiantes debatieron sobre los derechos y deberes de los niños, crearon sus propias versiones de los deberes basados en los derechos, y plasmaron cada derecho a través de dibujos y historias. Finalmente, celebraron el Día de la Infancia jugando en las colchonetas.
More Related Content
What's hot
Operating system and embedded systems

operating system is same as ARM controller.but, here we learn about optimization in terms of time,memory,size of the code.reducing one of these will be our main moto
3

This document discusses binary vulnerabilities and methods for identifying and exploiting them. It covers topics like stack overflows, heap overflows, integer overflows, and pointer vulnerabilities. It also discusses vulnerability metrics, identifiers, and tools that can be used for analysis like fuzzers, symbolic execution, and decompilers. Exploitation techniques like bypassing protections and transferring control are also mentioned.
Как работает LLVM бэкенд в C#. Егор Богатов ➠ CoreHard Autumn 2019

LLVM содержит огромное количество оптимизаций и подходит в качестве бэкенда для многих языков программирования. Но все немного усложняется для Managed языков и JIT сценариев. В этом докладе Егор расскажет о трудностях, с которыми столкнулись в C# при реализации LLVM бэкенда.
Алексей Кутумов, Coroutines everywhere

Не так давно Гор Нишанов представил свой доклад: C++ Coroutines a negative overhead abstraction. В этом докладе Гор упомянул, что предложенный дизайн корутин позволяет их использовать практически в любых окружениях, в том числе и с "бедным" C++ рантаймом.
Я решил попробовать запустить корутины в следующих окружениях: обычное приложение, драйвер ОС Windows, EFI приложение. Только в одном из этих окружений есть полноценный C++ рантайм и поддержка исключений, в остальных ничего этого нет. Более того, EFI приложение вообще выполняется до старта ОС.
Я хочу рассказать о том, как мне удалось запустить корутины в этих окружениях, поговорим о том, какие проблемы существуют в асинхронном системном программировании и как их можно обойти.
Nested micro

This document discusses macro nesting in C programming. It defines several macros, including nested macros where a macro name is used within the definition of another macro. It then shows an example program that defines macros, reads a text file containing additional macro definitions, builds a linked list of the macros, replaces nested macro names within values, and prints the final macro table.
Main Form Number To Word

This document contains C# code for a program that converts numbers to words. It includes a MainForm class with a button click event that calls the ConvertToWord class. The ConvertToWord class contains two methods: Convert, which takes a numeric string as input and returns the equivalent word string, and CharToWord and DigitToWord, which return the word representations of individual characters and digits based on their position in the number. The code uses arrays, loops, and switch statements to iterate through the input and build up the word string by concatenating the outputs of the character and digit conversion methods.
Go vs C++ - CppRussia 2019 Piter BoF

This document compares and contrasts various features of C++ and Go, including:
- Error handling approaches like exceptions in C++ vs explicit error checking in Go.
- Class/struct definitions and how they compare between the languages.
- Common data structures like vectors, maps, and how they are implemented in each language.
- Benchmark results that show Go outperforming C++ in some cases but C++ performing better in others, depending on optimizations and data structure choices.
- Interfacing Go with C via Cgo and the performance overhead of marshalling between the languages.
- Concurrency primitives available in each language like mutexes, channels, atomics.
C++の話(本当にあった怖い話)

The document discusses C++ and its history and features. It describes C++ as an extension of C with object-oriented features like classes. It provides information on the creator of C++, Bjarne Stroustrup, and the evolution of C++ since its introduction as a way to add object-oriented programming to C. It also includes sample C++ code demonstrating the use of arrays and includes from the Boost library.
Computer Programming- Lecture 4

The document discusses procedural abstraction and predefined functions in computer programming. It provides examples of for loops and nested for loops to iterate through ranges of values. The for loop examples demonstrate how the initialization, boolean expression, and update components work together to execute the loop body. Tracing is used to step through multiple iterations of the for loops.
Voce Tem Orgulho Do Seu Codigo

O quanto você está satisfeito com o código que produz? Mais ainda: o quanto você está satisfeito como profissional? Na busca pela melhoria de nossas aplicações, caímos num grande desafio: melhorar a nós mesmos!
Numa conversa franca e descontraída, Samuel e Victor tentarão apresentar idéias sobre como você pode melhorar seu próprio trabalho e sentir orgulho do que faz.
Java, Up to Date Sources

Source codes of the Presentation "Java, Up to Date", http://www.slideshare.net/akirakoyasu/java-up-to-date
Some examples of the 64-bit code errors

While porting 32-bit software to 64-bit systems there may appear some errors in the code of applications which were written in C++ language. The cause for these hides in the alteration of the base data types (to be more exact, in the relations between them) with the new hardware platform.
Percobaan 1

This program uses an ATmega8535 microcontroller to light up LEDs connected to port A in sequence when button 0 on port B is pressed and turn them off in reverse order when button 1 is pressed. It initializes ports A, B, C and D, sets port A pins as outputs and lights up each pin on port A for 50ms when button 0 is pressed, then turns them all off when button 1 is pressed also with a 50ms delay between each pin.
project3

The document contains code for an employee management system program written in C++. It defines structures to store employee data and functions to build, list, insert, delete, edit, search, and sort employee records. The main function calls these functions and includes a menu loop to allow the user to select different options for managing the employee database.
Bai Giang 11

The document discusses various ways to redefine operators and functions in C++. It covers redefining functions with the same name but different parameters, redefining operators for a class using member and non-member functions, converting between types when redefining operators, and redefining stream insertion and extraction operators.
TMPA-2017: Predicate Abstraction Based Configurable Method for Data Race Dete...

TMPA-2017: Tools and Methods of Program Analysis
3-4 March, 2017, Hotel Holiday Inn Moscow Vinogradovo, Moscow
Predicate Abstraction Based Configurable Method for Data Race Detection in Linux Kernel
Pavel Andrianov, Vadim Mutilin,Alexey Khoroshilov, Institute for System Programming
For video follow the link: https://youtu.be/SxDVQ7lSTqc
Would like to know more?
Visit our website:
www.tmpaconf.org
www.exactprosystems.com/events/tmpa
Follow us:
https://www.linkedin.com/company/exactpro-systems-llc?trk=biz-companies-cym
https://twitter.com/exactpro
Gaurav Jatav , BCA Third Year

This is a work by the student of BCA Department student from Third Year studying at Dezyne E'cole College,Ajmer
Breaking the wall

The document discusses different approaches tried to switch device certificates programmatically on iOS, including using NSURLConnection, GTMHTTPFetcher, and ASIHTTPRequest. It also describes some hacks that worked like using the IP address instead of the hostname and adding a period to the hostname. The document appears to be technical notes on trying to authenticate and switch certificates during an HTTPS connection on iOS.
Server

This document contains C code for creating a basic TCP server socket that listens for connections from clients and allows for bidirectional communication by reading from and writing to the client socket file descriptor. The code binds the server socket to port 4020 on IP address 10.180.5.196, accepts an incoming connection, and then enters a loop to continuously read messages from the client and write responses until the client sends the string "bye".
What's hot (19)
Как работает LLVM бэкенд в C#. Егор Богатов ➠ CoreHard Autumn 2019

Как работает LLVM бэкенд в C#. Егор Богатов ➠ CoreHard Autumn 2019
TMPA-2017: Predicate Abstraction Based Configurable Method for Data Race Dete...

TMPA-2017: Predicate Abstraction Based Configurable Method for Data Race Dete...
Viewers also liked
Tere 

The document discusses the benefits of exercise for mental health. Regular physical activity can help reduce anxiety and depression and improve mood and cognitive functioning. Exercise causes chemical changes in the brain that may help boost feelings of calmness, happiness and focus.
CEIP Alcalde Rafael Cedrés - Día de La Infancia

El documento describe el programa de la semana del Día de la Infancia en el colegio Ceip Alcalde Rafael Cedrés. Los estudiantes debatieron sobre los derechos y deberes de los niños, crearon sus propias versiones de los deberes basados en los derechos, y plasmaron cada derecho a través de dibujos y historias. Finalmente, celebraron el Día de la Infancia jugando en las colchonetas.
SGQ in Anatomia Patologica

Il Sistma Gestione Qualità secondo le ISO 9000:2015 applicate al laboratorio di Isto-Citopatologia
Felicitación Navideña 2015 - CEIP La Cerruda

El documento desea a la comunidad educativa del CEIP La Cerruda unas felices fiestas y un próspero año 2016. Incluye trabajos realizados por el alumnado y familias sobre la Navidad, y hace referencia a cambiar actitudes y compromiso tendiendo una mano para ayudar.
What are kpi targets

This document discusses key performance indicators (KPIs) and how to develop them. It provides information on defining objectives and key result areas, identifying tasks and work procedures, and determining how to measure results for KPIs. The document outlines common mistakes to avoid when creating KPIs, such as having too many, and notes that KPIs should be linked to strategy and empower employees. It also describes different types of KPIs, including process, input, output, leading, lagging, outcome, qualitative and quantitative.
CERTIFICATE

Rationel oven Aegean region of educator
1995 Tudem (Tourism and Hotel)
Training course has been taken on F&B department.
2003 Kitchen Arts Center RATIONAL
The usage of the ovens training has been by Mesut ERDOĞAN
2004 Wine and grape’s vineyard
Wine and grapes training has been taken by Mehmet YALÇIN
Bread production training and fermentation training has been taken by Hasan ZEKİ ŞEKER
CERTIFICATES
Basic Food Hygiene, HACCP, Chemical Safety, Breakage&loss” trainings (ECOLAB)
Pest Prevention
FAQ PAU - IES Lomo Apolinario

Este documento proporciona información sobre el acceso a la universidad desde los ciclos formativos de grado superior. Indica que los titulados en ciclos formativos pueden acceder a cualquier grado sin pruebas adicionales, aunque pueden mejorar su nota de admisión presentándose voluntariamente a la fase específica de la prueba de acceso a la universidad. También explica la diferencia entre la nota de acceso y la nota de admisión, que es la que se usa para adjudicar plazas cuando hay límite.
Gioco Vase - Vase Erasmus +

The document describes a game that presents moral dilemmas in various situations and tests the player's ability to choose ethical responses. It includes scenarios about witnessing bullying, completing an assignment honestly, finding a lost phone, trying to get into a selective school, facing rejection at an audition, attending a new class, and more. For each scenario, the player must select between 3 response options, with only one response considered correct by the game.
Presentación red ecos IES Lomo Apolinario

La RedECOS es una iniciativa para desarrollar la educación ambiental en los centros educativos de Canarias. Está compuesta por 161 centros que participan compartiendo recursos y realizando ecoauditorías escolares, que implican evaluar la calidad ambiental del centro e implementar acciones de mejora con la participación de la comunidad escolar. El proceso de ecoauditoría sigue las etapas de organización, diagnóstico, plan de acción, acción, evaluación y difusión.
Sales kpi dashboard

This document discusses key performance indicators (KPIs) for sales dashboards. It provides information on common KPI metrics, how to create KPIs, common mistakes in KPI development, and different types of KPIs such as leading vs lagging. The document recommends visiting an external website for additional free resources on KPIs, including ebooks, lists of sample KPIs, performance appraisal forms and methods. It also outlines a step-by-step process for developing KPIs for a specific position.
A.Yasser ( Mechatronics Engineer ) CV

This document contains a summary of Ahmed Yasser Saad Qaitbay's personal and professional experience. It includes his contact information, date of birth, nationality, education history, and work experience in various engineering roles at companies like MCS Free Zone and NAFFCO MISR. His experience involves tasks like operating technical software for pipeline inspection, AutoCAD design, fire safety system installation, and machinery maintenance. He has skills in areas such as AutoCAD, Microsoft Office, PLC programming, and troubleshooting.
Viewers also liked (13)
Similar to Tai lieu ky thuat lap trinh
8051 -5

The document contains several 8051 microcontroller C programs that demonstrate different applications including:
1) Sending ASCII character values to a port, generating square waves, and step waveforms.
2) Generating a 100ms time delay using a timer, toggling an LED using a timer, and implementing a down counter on a 7-segment display.
3) Controlling a stepper motor, displaying "HELLO" on an LCD, and generating a triangular wave.
Snake.c

This C program implements a snake game using graphics. It initializes a linked list to represent the snake and randomly generates food on the screen. It uses functions to check for collisions with food/body, move the snake according to key presses, and draw the snake/food each frame. The main game loop runs continuously, checking for input, calling functions to update the snake's position and check for collisions, drawing the updated scene, and exiting if the snake collides with itself or the edge of the screen.
ARM 7 LPC 2148 lecture

This document provides C code solutions to interface four 7-segment displays on an ARM7 microcontroller and display counts from 0000 to 9999. The code defines arrays to store the digit values for the displays and uses conditions to extract the digits from the count value to display on the individual segments. Delay functions are used to control the timing of digit updates on the displays.
REPORT

This project report describes a treadmill simulation project using an 8052 microcontroller. The hardware components included an 8052 microcontroller, LCD display, numeric keypad, DC motor, and other components. The code was written to control the keypad, LCD display, motor and calculate calories burned based on speed, time, weight and gender of the user. The project was simulated using Proteus and results matched the expected functionality.
Microsoft Word Hw#1

This document contains programs written in C++ to perform encryption and decryption using Caesar cipher, Vigenere cipher, and Playfair cipher. It includes the code for encrypting and decrypting text using Caesar cipher. It also includes code for encrypting and decrypting text using Vigenere cipher's autokey method. There is incomplete code provided for Playfair cipher that distributes the alphabet and key into a 5x5 matrix but does not include the encryption logic.
codings related to avr micro controller

This article is related to codings of different types of applications which is taken from engineersgarage.com
Aodv routing protocol code in ns2

Implementation coding AODV coding of NS2 simulator, and aodv routing protocol implementation design source code in ns2 ThesisScientist.com aodv routing protocol in wireless sensor networks
Lab programs FOR 8TH SEM EC SUBJECT BY LOHITH KUMAR |11GUEE6018

The document contains code snippets for several microcontroller programs including a buzzer, LCD display, down counter, up counter, left shift, right shift, and voltage converter/ADC. The code defines pin configurations, registers, and functions for delay, counting, shifting bits, and reading analog voltage values from an ADC converter.
Microcontroladores: programas de CCS Compiler.docx

This document contains programs for a PIC microcontroller that implement various functions including:
1) Scanning a 4x4 keypad and displaying the pressed number on a 7-segment display.
2) Using an ADC to read pressure sensor data and transmit it via RS-232.
3) Transmitting and receiving data between two PICs via RS-232.
4) Blinking LEDs on ports and driving a buzzer.
5) Reading an ADC and displaying the value on an LCD.
6) Implementing a timer and counting seconds on an LCD.
7) Using I2C to communicate with a device.
8) Scanning a keypad and unlock
Program interfacing lab

This document contains code snippets for several programs:
1) A program to toggle an LED on and off using delays.
2) A program to control the direction and speed of a stepper motor using interrupts and delays.
3) A program to generate a square wave by alternating the port between high and low using delays.
4) A program to control traffic lights by sequentially turning on different LED patterns on two ports using repeated delays.
5) A program to generate a rectangular wave by setting the port high for one delay then low for a longer delay in a loop.
6) A program to generate a triangular wave by incrementing then decrementing a counter to set the port value in a continuous loop
Computer Graphics Lab File C Programs

This program writes a C code to shear a cuboid. It includes graphics header files and uses the Bresenham's line algorithm to draw lines. The program defines a function called 'bress' to draw lines using the Bresenham algorithm. It takes coordinates of two points as input and uses conditions on the slope to determine the increment, endpoint and direction of line drawing. This function is used to draw the individual lines of the cuboid before and after shearing.
Jamming attack in wireless network

This document contains code for implementing a jamming attack in a mobile ad hoc network (MANET). It includes code for functions related to sending and processing Hello messages used for neighbor discovery and route maintenance. It also includes code for functions related to creating, sending, forwarding, and processing route reply (RREP) messages used for route discovery and maintenance in the ad hoc on-demand distance vector (AODV) routing protocol. The code implements optimizations for dealing with unidirectional links and extensions for including additional information in messages.
ANS#include iostream int Rn_get(int low, int high); int cva.pdf

ANS:
#include
int Rn_get(int low, int high);
int cvalue(int card);
int toca(int deck[]);
int handva(const int hand[]);
bool pla_hand(char&);
bool draw_u(char&);
void inti(int deck[]);
void d_deck(int deck[], int size);
void dhudd(int deck[], int size);
void show_card(int card);
void card_s(const int cards[], int numCards, bool hideFirstCard);
void wiwh(const int pHand[], const int dHand[]);
void cbust(const int pHand[], const int dHand[], char p1);
void bbjack(const int pHand[], const int dHand[], char p1);
void nbjack(const int pHand[], const int dHand[], char p1);
void play_one();
void scboard(const int pHand[], const int dHand[]);
void bakkdor(const int hand[]);
void sffot(int pHand[]);
void go_to(int dHand[], int pHand[]);
void choo_def();
void sh_rules();
void add_hand(int hand[], int cardToAdd);
void stand_hit(int dHand[], int deck[], int pHand[]);
int tcard = 0;
float wi = 1.00;
int l_1;
int main()
{
sh_rules();
choo_def();
play_one();
return 1;
}
void sh_rules()
{
}
void choo_def()
{
cout << \"\ \";
cout << \"Level of Difficulty: Beginner (1), Expert (2). \";
cin >> l_1;
cout << \"\ \";
if(l_1 != 1)
{
if(l_1 != 2)
{
cin.clear();
cin.ignore(numeric_limits::max(), \'\ \');
cout << \"Please enter your l_1 of difficulty using the number 1 or 2.\" << endl;
choo_def();
}
}
}
void play_one()
{
char p1 = \'N\';
do
{
char dr = \'H\';
int deck[52];
inti(deck);
dhudd(deck, 51);
int pHand[10] = {0};
int dHand[10] = {0};
add_hand(pHand, toca(deck));
add_hand(dHand, toca(deck));
add_hand(pHand, toca(deck));
add_hand(dHand, toca(deck));
cout << \"The Dealer dhuddd and dealt you each your cards. \";
nbjack(pHand, dHand, \'y\');
bbjack(pHand, dHand, \'Y\');
cout << \"Your hand:\" << endl;
card_s(pHand, 10, false);
cout << \"\ \ Dealer\'s hand:\" << endl;
card_s(dHand, 10, true);
sffot(pHand);
while (draw_u(dr))
{
add_hand(pHand, toca(deck));
cout << \"The Dealer dealt you another card.\ \" << endl;
cout << \"Your hand:\" << endl;
card_s(pHand, 10, false);
sffot(pHand);
cbust(pHand, dHand, \'y\');
bbjack(pHand, dHand, \'Y\');
}
stand_hit(dHand, deck, pHand);
cout << endl;
cbust(pHand, dHand, \'Y\');
bbjack(pHand, dHand, \'Y\');
wiwh(pHand, dHand);
cout << endl;
cout << \"Winnings multiplier: \" << wi << endl;
}
while (pla_hand(p1));
}
void inti(int deck[])
{
int Rank = 101;
int i = 0;
for (i = 0 ; i<=13; i++)
{
deck[i] = Rank++;
}
for (i = 13 ; i<=26; i++)
{
deck[i] = Rank++ + 100 - 14;
}
for (i = 26 ; i<=39; i++)
{
deck[i] = Rank++ + 200 - 28;
}
for (i = 39 ; i<=51; i++)
{
deck[i] = Rank++ + 300 - 42;
}
}
void dhudd(int deck[], int size)
{
for(int i = 0; i < 500; i++)
{
int T1 = 0;
int R1 = Rn_get(0, size);
int R2 = Rn_get(0, size);
T1 = deck[R1];
deck[R1] = deck[R2];
deck[R2] = T1;
}
}
void show_card(int card)
{
if(card == 0)
{
cout << \"\";
}
else
{
switch(card % 100)
{
case 1:
cout << \"A\";
break;
case 11:
cout << \"J\";
break;
case 12:
cout << \"K\";
break;
case 13:
cout << \"Q\";
break;
case 14:
cout << \"A\";
break;
default:
cout << card % 100;.
Ds 2 cycle

The document discusses the implementation of a binary search tree (BST) using both recursive and non-recursive traversal methods. It defines a BST node structure with left and right child pointers. Functions are included to insert nodes, perform inorder, preorder and postorder traversals recursively and non-recursively using stacks. Main inserts sample nodes into the tree and calls the various traversal functions to output the node values in the specified orders.
Senior design project code for PPG

Program to display heart rate and heart beat waveform based on photoplethysmography (PPG). It reads values from a sensor made of photodiode and LED and displays the corresponding heart rate and waveform on an LCD screen
A scrupulous code review - 15 bugs in C++ code

A close look at 15 problems one can find when reviewing C++ code.
Offers code examples.
Covers indexed loops, tainted data, copy and paste errors, problems with comparisons, exceptions, etc.
You can use static code analysis tools to make code review easier. Code analyzers find errors and potential vulnerabilities in code, while saving the developers' time and the companies' money.
Manual code review is expensive - a group of programmers get together regularly to review the code.
One can run static analysis tools regularly to find mistakes and vulnerabilities early.
C# Assignmet Help

Random speed program in CPP
This program is calculating the random speed explicitly and implementing the concept of matrix.
programminghomeworkhelp.com is the leading online solution provider for C++ Programming assignments. If you are struggling with your scoring in C++ Programming Assignments, Homework or Projects then email your requirements at info@programminghomeworkhelp.com and we will ensure excellent grades. Email your C++ assignment to info@programminghomeworkhelp.com and distress yourself from the complex C++ Programming Assignments.
From clever code to better code

Part of the software developer job is to find new and better ways to solve problems. Writing code using his/her wits, intelligent and creativity.
However, sometimes being too clever can lead to hard to track bugs, maintainability issues and impossible to understand code. Is all cleverly written code good code, or is it a problem just waiting to happen?
In this session, I will show you real world examples of cleverly written code. And show you how we can use clean code principles, refactoring and design patterns, to transform that code from clever code to good code, code one that your peers - and future self - would thank you for writing.
Questions has 4 parts.1st part Program to implement sorting algor.pdf

The document contains a C++ program that implements several sorting algorithms including bubble sort, selection sort, insertion sort, merge sort, quick sort, and radix sort. The program defines functions for each sorting algorithm and includes a main method that tests each algorithm by sorting sample data arrays and printing the results.
7segment scetch

This document defines functions for displaying numeric values on a 7-segment display using an Arduino. It sets latch, clock, and data pins as outputs to control the display. The disNum() function takes in a numeric value, position, and decimal flag and outputs the corresponding 7-segment display value. The showNum() function takes a double value, converts it to long, extracts each digit, and calls disNum() to display the number on the 7-segment display one position at a time.
Similar to Tai lieu ky thuat lap trinh (20)
Lab programs FOR 8TH SEM EC SUBJECT BY LOHITH KUMAR |11GUEE6018

Lab programs FOR 8TH SEM EC SUBJECT BY LOHITH KUMAR |11GUEE6018
Microcontroladores: programas de CCS Compiler.docx

Microcontroladores: programas de CCS Compiler.docx
ANS#include iostream int Rn_get(int low, int high); int cva.pdf

ANS#include iostream int Rn_get(int low, int high); int cva.pdf
Questions has 4 parts.1st part Program to implement sorting algor.pdf

Questions has 4 parts.1st part Program to implement sorting algor.pdf
Recently uploaded
Monitoring and Managing Anomaly Detection on OpenShift.pdf

Monitoring and Managing Anomaly Detection on OpenShift
Overview
Dive into the world of anomaly detection on edge devices with our comprehensive hands-on tutorial. This SlideShare presentation will guide you through the entire process, from data collection and model training to edge deployment and real-time monitoring. Perfect for those looking to implement robust anomaly detection systems on resource-constrained IoT/edge devices.
Key Topics Covered
1. Introduction to Anomaly Detection
- Understand the fundamentals of anomaly detection and its importance in identifying unusual behavior or failures in systems.
2. Understanding Edge (IoT)
- Learn about edge computing and IoT, and how they enable real-time data processing and decision-making at the source.
3. What is ArgoCD?
- Discover ArgoCD, a declarative, GitOps continuous delivery tool for Kubernetes, and its role in deploying applications on edge devices.
4. Deployment Using ArgoCD for Edge Devices
- Step-by-step guide on deploying anomaly detection models on edge devices using ArgoCD.
5. Introduction to Apache Kafka and S3
- Explore Apache Kafka for real-time data streaming and Amazon S3 for scalable storage solutions.
6. Viewing Kafka Messages in the Data Lake
- Learn how to view and analyze Kafka messages stored in a data lake for better insights.
7. What is Prometheus?
- Get to know Prometheus, an open-source monitoring and alerting toolkit, and its application in monitoring edge devices.
8. Monitoring Application Metrics with Prometheus
- Detailed instructions on setting up Prometheus to monitor the performance and health of your anomaly detection system.
9. What is Camel K?
- Introduction to Camel K, a lightweight integration framework built on Apache Camel, designed for Kubernetes.
10. Configuring Camel K Integrations for Data Pipelines
- Learn how to configure Camel K for seamless data pipeline integrations in your anomaly detection workflow.
11. What is a Jupyter Notebook?
- Overview of Jupyter Notebooks, an open-source web application for creating and sharing documents with live code, equations, visualizations, and narrative text.
12. Jupyter Notebooks with Code Examples
- Hands-on examples and code snippets in Jupyter Notebooks to help you implement and test anomaly detection models.
Generating privacy-protected synthetic data using Secludy and Milvus

During this demo, the founders of Secludy will demonstrate how their system utilizes Milvus to store and manipulate embeddings for generating privacy-protected synthetic data. Their approach not only maintains the confidentiality of the original data but also enhances the utility and scalability of LLMs under privacy constraints. Attendees, including machine learning engineers, data scientists, and data managers, will witness first-hand how Secludy's integration with Milvus empowers organizations to harness the power of LLMs securely and efficiently.
GraphRAG for Life Science to increase LLM accuracy

GraphRAG for life science domain, where you retriever information from biomedical knowledge graphs using LLMs to increase the accuracy and performance of generated answers
Programming Foundation Models with DSPy - Meetup Slides

Prompting language models is hard, while programming language models is easy. In this talk, I will discuss the state-of-the-art framework DSPy for programming foundation models with its powerful optimizers and runtime constraint system.
Presentation of the OECD Artificial Intelligence Review of Germany

Consult the full report at https://www.oecd.org/digital/oecd-artificial-intelligence-review-of-germany-609808d6-en.htm
5th LF Energy Power Grid Model Meet-up Slides

5th Power Grid Model Meet-up
It is with great pleasure that we extend to you an invitation to the 5th Power Grid Model Meet-up, scheduled for 6th June 2024. This event will adopt a hybrid format, allowing participants to join us either through an online Mircosoft Teams session or in person at TU/e located at Den Dolech 2, Eindhoven, Netherlands. The meet-up will be hosted by Eindhoven University of Technology (TU/e), a research university specializing in engineering science & technology.
Power Grid Model
The global energy transition is placing new and unprecedented demands on Distribution System Operators (DSOs). Alongside upgrades to grid capacity, processes such as digitization, capacity optimization, and congestion management are becoming vital for delivering reliable services.
Power Grid Model is an open source project from Linux Foundation Energy and provides a calculation engine that is increasingly essential for DSOs. It offers a standards-based foundation enabling real-time power systems analysis, simulations of electrical power grids, and sophisticated what-if analysis. In addition, it enables in-depth studies and analysis of the electrical power grid’s behavior and performance. This comprehensive model incorporates essential factors such as power generation capacity, electrical losses, voltage levels, power flows, and system stability.
Power Grid Model is currently being applied in a wide variety of use cases, including grid planning, expansion, reliability, and congestion studies. It can also help in analyzing the impact of renewable energy integration, assessing the effects of disturbances or faults, and developing strategies for grid control and optimization.
What to expect
For the upcoming meetup we are organizing, we have an exciting lineup of activities planned:
-Insightful presentations covering two practical applications of the Power Grid Model.
-An update on the latest advancements in Power Grid -Model technology during the first and second quarters of 2024.
-An interactive brainstorming session to discuss and propose new feature requests.
-An opportunity to connect with fellow Power Grid Model enthusiasts and users.
AI 101: An Introduction to the Basics and Impact of Artificial Intelligence

Imagine a world where machines not only perform tasks but also learn, adapt, and make decisions. This is the promise of Artificial Intelligence (AI), a technology that's not just enhancing our lives but revolutionizing entire industries.
Webinar: Designing a schema for a Data Warehouse

Are you new to data warehouses (DWH)? Do you need to check whether your data warehouse follows the best practices for a good design? In both cases, this webinar is for you.
A data warehouse is a central relational database that contains all measurements about a business or an organisation. This data comes from a variety of heterogeneous data sources, which includes databases of any type that back the applications used by the company, data files exported by some applications, or APIs provided by internal or external services.
But designing a data warehouse correctly is a hard task, which requires gathering information about the business processes that need to be analysed in the first place. These processes must be translated into so-called star schemas, which means, denormalised databases where each table represents a dimension or facts.
We will discuss these topics:
- How to gather information about a business;
- Understanding dictionaries and how to identify business entities;
- Dimensions and facts;
- Setting a table granularity;
- Types of facts;
- Types of dimensions;
- Snowflakes and how to avoid them;
- Expanding existing dimensions and facts.
Salesforce Integration for Bonterra Impact Management (fka Social Solutions A...

Sidekick Solutions uses Bonterra Impact Management (fka Social Solutions Apricot) and automation solutions to integrate data for business workflows.
We believe integration and automation are essential to user experience and the promise of efficient work through technology. Automation is the critical ingredient to realizing that full vision. We develop integration products and services for Bonterra Case Management software to support the deployment of automations for a variety of use cases.
This video focuses on integration of Salesforce with Bonterra Impact Management.
Interested in deploying an integration with Salesforce for Bonterra Impact Management? Contact us at sales@sidekicksolutionsllc.com to discuss next steps.
Driving Business Innovation: Latest Generative AI Advancements & Success Story

Are you ready to revolutionize how you handle data? Join us for a webinar where we’ll bring you up to speed with the latest advancements in Generative AI technology and discover how leveraging FME with tools from giants like Google Gemini, Amazon, and Microsoft OpenAI can supercharge your workflow efficiency.
During the hour, we’ll take you through:
Guest Speaker Segment with Hannah Barrington: Dive into the world of dynamic real estate marketing with Hannah, the Marketing Manager at Workspace Group. Hear firsthand how their team generates engaging descriptions for thousands of office units by integrating diverse data sources—from PDF floorplans to web pages—using FME transformers, like OpenAIVisionConnector and AnthropicVisionConnector. This use case will show you how GenAI can streamline content creation for marketing across the board.
Ollama Use Case: Learn how Scenario Specialist Dmitri Bagh has utilized Ollama within FME to input data, create custom models, and enhance security protocols. This segment will include demos to illustrate the full capabilities of FME in AI-driven processes.
Custom AI Models: Discover how to leverage FME to build personalized AI models using your data. Whether it’s populating a model with local data for added security or integrating public AI tools, find out how FME facilitates a versatile and secure approach to AI.
We’ll wrap up with a live Q&A session where you can engage with our experts on your specific use cases, and learn more about optimizing your data workflows with AI.
This webinar is ideal for professionals seeking to harness the power of AI within their data management systems while ensuring high levels of customization and security. Whether you're a novice or an expert, gain actionable insights and strategies to elevate your data processes. Join us to see how FME and AI can revolutionize how you work with data!
Building Production Ready Search Pipelines with Spark and Milvus

Spark is the widely used ETL tool for processing, indexing and ingesting data to serving stack for search. Milvus is the production-ready open-source vector database. In this talk we will show how to use Spark to process unstructured data to extract vector representations, and push the vectors to Milvus vector database for search serving.
Fueling AI with Great Data with Airbyte Webinar

This talk will focus on how to collect data from a variety of sources, leveraging this data for RAG and other GenAI use cases, and finally charting your course to productionalization.
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Discover how MongoDB Atlas and vector search technology can revolutionize your application's search capabilities. This comprehensive presentation covers:
* What is Vector Search?
* Importance and benefits of vector search
* Practical use cases across various industries
* Step-by-step implementation guide
* Live demos with code snippets
* Enhancing LLM capabilities with vector search
* Best practices and optimization strategies
Perfect for developers, AI enthusiasts, and tech leaders. Learn how to leverage MongoDB Atlas to deliver highly relevant, context-aware search results, transforming your data retrieval process. Stay ahead in tech innovation and maximize the potential of your applications.
#MongoDB #VectorSearch #AI #SemanticSearch #TechInnovation #DataScience #LLM #MachineLearning #SearchTechnology
Introduction of Cybersecurity with OSS at Code Europe 2024

I develop the Ruby programming language, RubyGems, and Bundler, which are package managers for Ruby. Today, I will introduce how to enhance the security of your application using open-source software (OSS) examples from Ruby and RubyGems.
The first topic is CVE (Common Vulnerabilities and Exposures). I have published CVEs many times. But what exactly is a CVE? I'll provide a basic understanding of CVEs and explain how to detect and handle vulnerabilities in OSS.
Next, let's discuss package managers. Package managers play a critical role in the OSS ecosystem. I'll explain how to manage library dependencies in your application.
I'll share insights into how the Ruby and RubyGems core team works to keep our ecosystem safe. By the end of this talk, you'll have a better understanding of how to safeguard your code.
UiPath Test Automation using UiPath Test Suite series, part 6

Welcome to UiPath Test Automation using UiPath Test Suite series part 6. In this session, we will cover Test Automation with generative AI and Open AI.
UiPath Test Automation with generative AI and Open AI webinar offers an in-depth exploration of leveraging cutting-edge technologies for test automation within the UiPath platform. Attendees will delve into the integration of generative AI, a test automation solution, with Open AI advanced natural language processing capabilities.
Throughout the session, participants will discover how this synergy empowers testers to automate repetitive tasks, enhance testing accuracy, and expedite the software testing life cycle. Topics covered include the seamless integration process, practical use cases, and the benefits of harnessing AI-driven automation for UiPath testing initiatives. By attending this webinar, testers, and automation professionals can gain valuable insights into harnessing the power of AI to optimize their test automation workflows within the UiPath ecosystem, ultimately driving efficiency and quality in software development processes.
What will you get from this session?
1. Insights into integrating generative AI.
2. Understanding how this integration enhances test automation within the UiPath platform
3. Practical demonstrations
4. Exploration of real-world use cases illustrating the benefits of AI-driven test automation for UiPath
Topics covered:
What is generative AI
Test Automation with generative AI and Open AI.
UiPath integration with generative AI
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
Columbus Data & Analytics Wednesdays - June 2024

Columbus Data & Analytics Wednesdays, June 2024 with Maria Copot 20
National Security Agency - NSA mobile device best practices

Threats to mobile devices are more prevalent and increasing in scope and complexity. Users of mobile devices desire to take full advantage of the features
available on those devices, but many of the features provide convenience and capability but sacrifice security. This best practices guide outlines steps the users can take to better protect personal devices and information.
Recently uploaded (20)
Monitoring and Managing Anomaly Detection on OpenShift.pdf

Monitoring and Managing Anomaly Detection on OpenShift.pdf
Generating privacy-protected synthetic data using Secludy and Milvus

Generating privacy-protected synthetic data using Secludy and Milvus
GraphRAG for Life Science to increase LLM accuracy

GraphRAG for Life Science to increase LLM accuracy
Programming Foundation Models with DSPy - Meetup Slides

Programming Foundation Models with DSPy - Meetup Slides
Presentation of the OECD Artificial Intelligence Review of Germany

Presentation of the OECD Artificial Intelligence Review of Germany
AI 101: An Introduction to the Basics and Impact of Artificial Intelligence

AI 101: An Introduction to the Basics and Impact of Artificial Intelligence
Salesforce Integration for Bonterra Impact Management (fka Social Solutions A...

Salesforce Integration for Bonterra Impact Management (fka Social Solutions A...
Driving Business Innovation: Latest Generative AI Advancements & Success Story

Driving Business Innovation: Latest Generative AI Advancements & Success Story
Building Production Ready Search Pipelines with Spark and Milvus

Building Production Ready Search Pipelines with Spark and Milvus
Deep Dive: AI-Powered Marketing to Get More Leads and Customers with HyperGro...

Deep Dive: AI-Powered Marketing to Get More Leads and Customers with HyperGro...
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf
Introduction of Cybersecurity with OSS at Code Europe 2024

Introduction of Cybersecurity with OSS at Code Europe 2024
UiPath Test Automation using UiPath Test Suite series, part 6

UiPath Test Automation using UiPath Test Suite series, part 6
National Security Agency - NSA mobile device best practices

National Security Agency - NSA mobile device best practices
Tai lieu ky thuat lap trinh
- 1. // LED 7 ĐOẠN TĂNG DẦN KHI BẤM NÚT #include <REGX51.H> unsigned char x=0; void hien_thi(char x); void main() { while (1) { hien_thi(x); if (P2_7==0) x=x+1; if (x>9) x=0; while (P2_7==0) hien_thi(x); } } void hien_thi(char x) { switch (x) { case 0: P0 = 0x40;break; case 1: P0 = 0x79;break; case 2: P0 = 0x24;break; case 3: P0 = 0x30 ;break; case 4: P0 = 0x19;break; case 5: P0 = 0x12;break; case 6: P0 = 0x02;break; case 7: P0 = 0x78 ;break; case 8: P0 = 0x00;break; case 9: P0 = 0x10 ;break; } } // LED 7 ĐOẠN TĂNG / GIẢM DẦN KHI BẤM NÚT #include <REGX51.H> unsigned char x=0; void hien_thi(char x); void main() { while (1) { hien_thi(x); if (P2_7==0) x=x+1; if (x==10) x=0; while (P2_7==0) hien_thi(x); if (P2_6==0) x = x - 1; if (x = = - 1) x = 9; while (P2_6 = = 0) hien_thi(x); } } void hien_thi(char x) { switch (x) { case 0: P0 = 0x40;break; case 1: P0 = 0x79;break; case 2: P0 = 0x24;break; case 3: P0 = 0x30 ;break; case 4: P0 = 0x19;break; case 5: P0 = 0x12;break; case 6: P0 = 0x02;break; case 7: P0 = 0x78 ;break; case 8: P0 = 0x00;break; case 9: P0 = 0x10 ;break; } } 1
- 2. // ĐẾM TIẾN LÙI TỪ 00 ĐẾN 99 #include <reg52x2.h> #define DVI P3_1 #define CHUC P3_0 #define tang P1_1 #define giam P1_0 delay(int time); hien_thi(int number); void main(void) { int phim_tang, phim_giam,sodem, d_vi,hang_chuc,i; sodem = 0; while(1) { phim_tang = tang; if(phim_tan g = = 0) { sode m++; if (sodem = =100) sodem=0; while (phim_tang = = 0) phim_tang = tang; } phim_giam = giam; if(phim_giam = = 0) { sode m--; if (sodem<0) sodem=0; while (phim_giam = = 0) phim_giam = giam; } hang_chuc = sodem/10; d_vi = sodem - (hang_chuc*10); for (i=1;i<30;i++) { DVI = 1; CHUC = 0; hien_thi(d_vi); } for (i=1;i<30;i++) { CHUC = 1; DVI = 0; hien_thi(hang_chuc); }}} hien_thi (int number) { switch (number) { case 0: P2 = 0x40;break; case 1: P2 = 0x79;break; case 2: P2 = 0x24;break; case 3: P2 = 0x30 ;break; case 4: P2 = 0x19;break; case 5: P2 = 0x12;break; case 6: P2 = 0x02;break; case 7: P2 = 0x78 ;break; case 8: P2 = 0x00;break; case 9: P2 = 0x10 ;break; } P2 = 0xff; } delay(int time) { int k,l; for(k=1;k<time; k++) for(l=1;l<time;l+ +); }} #include <reg52x2.h> unsigned char i; void sangdan(); void tatdan(); void delay(long time); void 2
- 3. sang_theo_tung_cap (); void main() { while(1) { P2=0x00; delay(2000); sangdan(); delay(2000); tatdan(); delay(2000); sang_theo_tung_c ap(); delay(2000); } } void delay(long time) { long t; for (t=0;t<=time;t++) { } } void sangdan( ) { unsigned char sangdan[ ] = {0x01,0x03,0x07,0x0 f,0x1f,0x3f,0x7f,0xff} ; for (i=0;i<=7;i++) { P2=sangdan[i ]; delay(2000); } } void tatdan() { unsigned char sangdan[ ] = {0x01,0x03,0x07,0 x0f,0x1f,0x3f,0x7f, 0xff}; for (i=0;i<=7;i++) { P2 = ~ sangdan[i]; delay(2000); } } void sang_theo_tung_ca p( ) { unsigned char sang_theo_tung_ca p[ ] = {0x81,0xc3,0xe7,0x ff}; for (i=0;i<=3;i+ +) { P2=sang_theo_tun g_cap[i]; delay(2000); } } // BÁO ĐỘNG #include <reg52x2.h> #define hoatdong P1_0 #define n1 P0_0 #define n2 P0_1 #define n3 P0_2 #define n4 P0_3 #define button P3_7 #define baodong P3_0 void main(void) { int phim_hd, nut_n1,nut_n2,nut_n3, nut_n4, nut_button; int dem1,temp; baodong = 0; while (1) { temp = 0; phim_hd = hoatdong; if ( phim_hd = = 0 ) { temp = 1; baodong = 0; while ( phim_hd = = 0 ) phim_hd = hoatdong; } while (temp= =1) { nut_button = button; if (nut_button = = 1) baodong = 1; nut_n1 = n1; nut_n2 = n2; nut_n3 = n3; nut_n4 = n4; if (nut_n1 == 0) { if (dem1= =0) dem1 = 1; else dem1=0; while (nut_n1 = = 0) nut_n1 = n1; } if (nut_n2 = = 0) { 3
- 4. if (dem1= =1) dem1 = 2; else dem1=0; while (nut_n2 == 0) nut_n2 = n2; } if (nut_n3 = = 0) { if (dem1= =2) dem1 = 3; else dem1=0; while (nut_n3 == 0) nut_n3 = n3; } if (nut_n4 = = 0) { if (dem1= =3) dem1 = 4; else dem1=0; while (nut_n4 = = 0) nut_n4 = n4; } if (dem1 = =4) {baodong = 0; temp=0; dem1=0;} }}} // CHẠY XUỐNG / LÊN #include <reg52x2.h> int luythua (a,b); void delay (int time); void main ( ) { //HIỂN THỊ CHỮ “T” #include <reg52x2.h> #define hang P2 #define cot P3 void main(void) { int i,k; int i,x,t; t = 1000; while(1) { P2 = 0; for (i=0; i<8; i++) {P2 = luythua (2, i); delay (t);} for (i=7; i>0; i - -) {P2 = luythua (2, i); delay (t);}}} void delay(int time) { int i; for(i=0;i<time;i++); } int luythua(a,b) { int x,k; x = 1; for(k=0;k<b;k++) x=x*a; return(x); } int gt_hang[8], gt_cot[8]; for(i = 1;i<9;i++) gt_cot[i] = 2^(i-1); gt_cot[1] = 1; gt_cot[2] = 2; gt_cot[3] = 4; gt_cot[4] = 8; gt_cot[5] = 16; gt_cot[6] = 32; gt_cot[7] = 64; gt_cot[8] = 128; gt_hang[1]= 0xfc; gt_hang[2]= 0xfc; gt_hang[3]= 0xfc; gt_hang[4]= 0x00; gt_hang[5]= 0x00; gt_hang[6]= 0xfc; gt_hang[7]= 0xfc; gt_hang[8]= 0xfc; while(1) { for (i=1;i<9;i++) { for(k=0;k<10;k++) { cot = gt_cot[i]; hang = gt_hang[i]; } } } } // ĐẾM TỪ 00 ĐẾN 99 RỒI LẶP LẠI, 12MHz #include"regx51.h" #define Led_dv P3_0 #define Led_chuc P3_1 unsigned char Ma[10]={0xc0,0xf9,0xa4,0xb0,0x99,0x92,0x8 2,0xf8,0x80,0x90}; int a, b, c, d, k; void delay(unsigned long int t) { unsigned long int l; 4
- 5. for(l=0;l<t;l++); } void main() { int i; while(1) { for(k=0;k<=99;k++) { a=k/10; b=k%10; for(i=0;i<20;i++) { Led_dv=1; P2=Ma[a]; delay(400); Led_dv=0; P2=0xff;//xoa data Led_chuc=1; P2=Ma[b]; delay(400); Led_chuc=0; P2=0xff; } } } } // ĐẾM TỪ 0000 ĐẾN 9999 RỒI LẶP LẠI, 12MHz #include<reg51.h> unsigned char Ma[10]={0xc0,0xf9,0xa4,0xb0, 0x99,0x92,0x82,0xf8,0x80,0x9 0}; unsigned char num=0,donvi,chuc,tram,nghin; void delay(unsig ned long int t) { unsigne d long int l; for(l=0;l <t;l++); } void DCB(void) { nghin=num/1000; tram=(num%1000)/100; chuc=(num%100)/10; donvi=num%10; } void HIEN_THI(void) { P0=Ma[nghin]; P2=0x1; delay(130); P2=0; P0=0xFF; P0=Ma[tram]; P2=0x2; delay(130); P2=0; P0=0xFF; P0=Ma[chuc]; P2=0x4; delay(130); P2=0; P0=0xFF; P0=Ma[donvi]; P2=0x8; delay(130); P2=0; P0=0xFF; } void main(void) { while(1) { unsigned a; for(a=0;a<30;a++) { DCB(); HIEN_THI( ); } num=num+ 1; if (num= =10000)nu m=0; } } Đề năm 2013/06/15 5
- 6. #include <REGX51.H> unsigned char x=0,y; void hien_thi_chu(char y); void hien_thi_so(char x); void main() { while (1) { hien_thi_so (x); if (P3_0==0) x=x+1; if (x==10) x=9; while (P3_0==0) { while (P3_1==0) { hien_thi_chu(1); } hien_thi_so (x); } if (P3_1==0) x=x-1; if (x == - 1) x=0; while (P3_1 == 0) { while (P3_0==0) { hien_thi_chu(2); } hien_thi_so (x); } } } void hien_thi_so (char x) { switch (x) { case 0: P2 = 0x40;break; case 1: P2 = 0x79;break; case 2: P2 = 0x24;break; case 3: P2 = 0x30 ;break; case 4: P2 = 0x19;break; case 5: P2 = 0x12;break; case 6: P2 = 0x02;break; case 7: P2 = 0x78 ;break; case 8: P2 = 0x00;break; case 9: P2 = 0x10 ;break; } } void hien_thi_chu (char y) { switch (y) { case 1: P2 = 0x08;break; case 2: P2 = 0x03;break; } } 6
- 7. #include <REGX51.H> unsigned char x=0,y; void hien_thi_chu(char y); void hien_thi_so(char x); void main() { while (1) { hien_thi_so (x); if (P3_0==0) x=x+1; if (x==10) x=9; while (P3_0==0) { while (P3_1==0) { hien_thi_chu(1); } hien_thi_so (x); } if (P3_1==0) x=x-1; if (x == - 1) x=0; while (P3_1 == 0) { while (P3_0==0) { hien_thi_chu(2); } hien_thi_so (x); } } } void hien_thi_so (char x) { switch (x) { case 0: P2 = 0x40;break; case 1: P2 = 0x79;break; case 2: P2 = 0x24;break; case 3: P2 = 0x30 ;break; case 4: P2 = 0x19;break; case 5: P2 = 0x12;break; case 6: P2 = 0x02;break; case 7: P2 = 0x78 ;break; case 8: P2 = 0x00;break; case 9: P2 = 0x10 ;break; } } void hien_thi_chu (char y) { switch (y) { case 1: P2 = 0x08;break; case 2: P2 = 0x03;break; } } 6