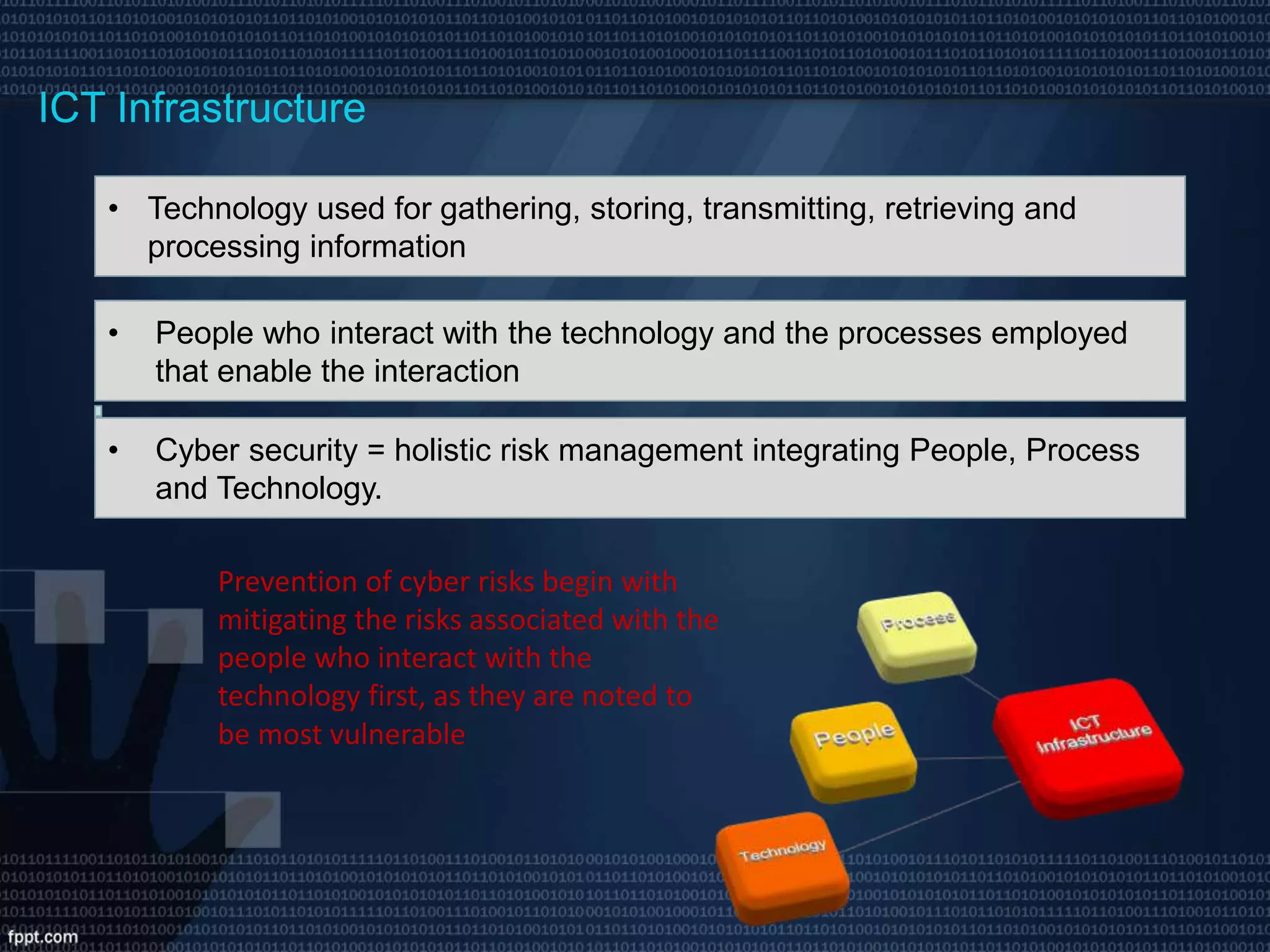
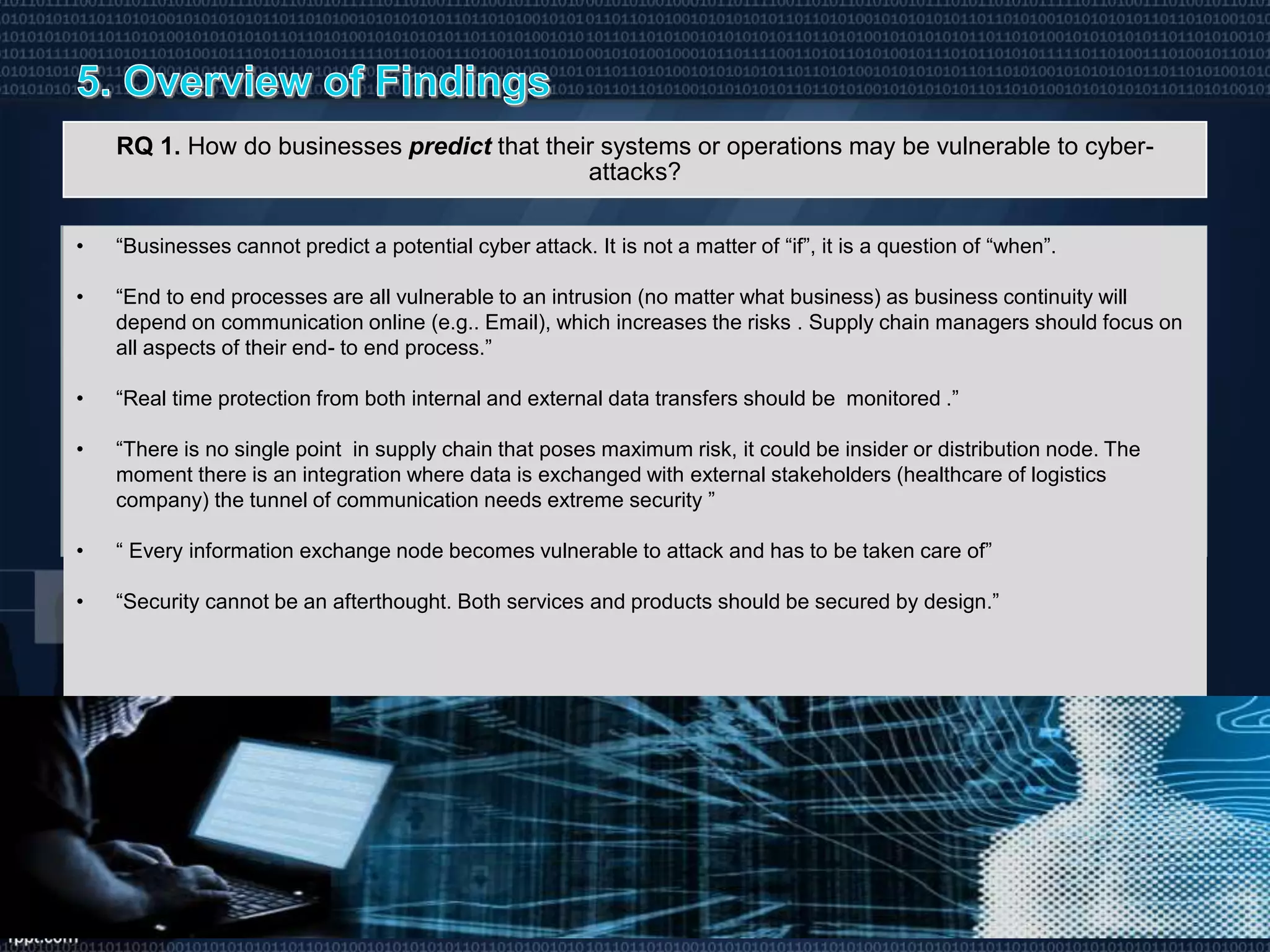
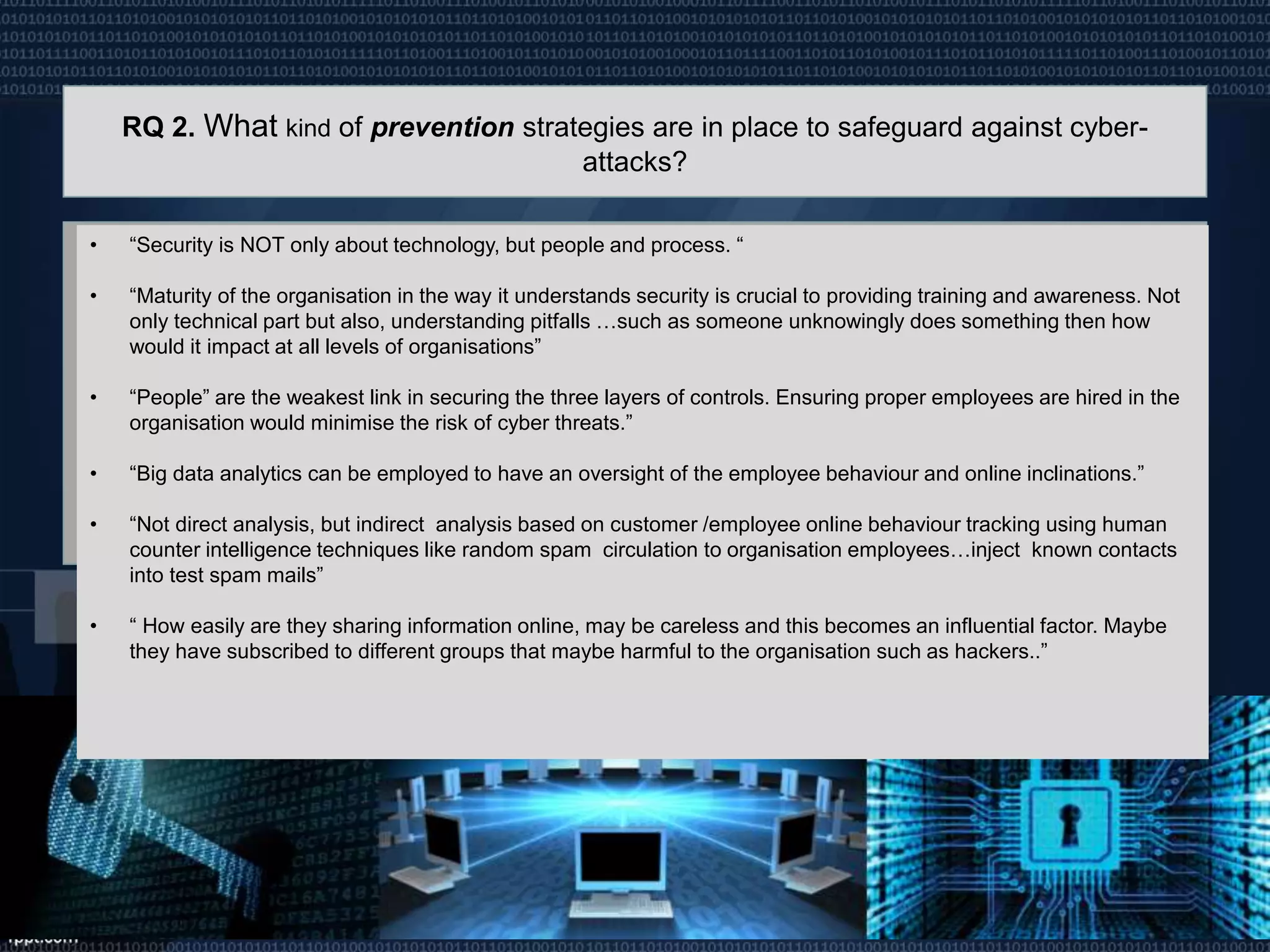
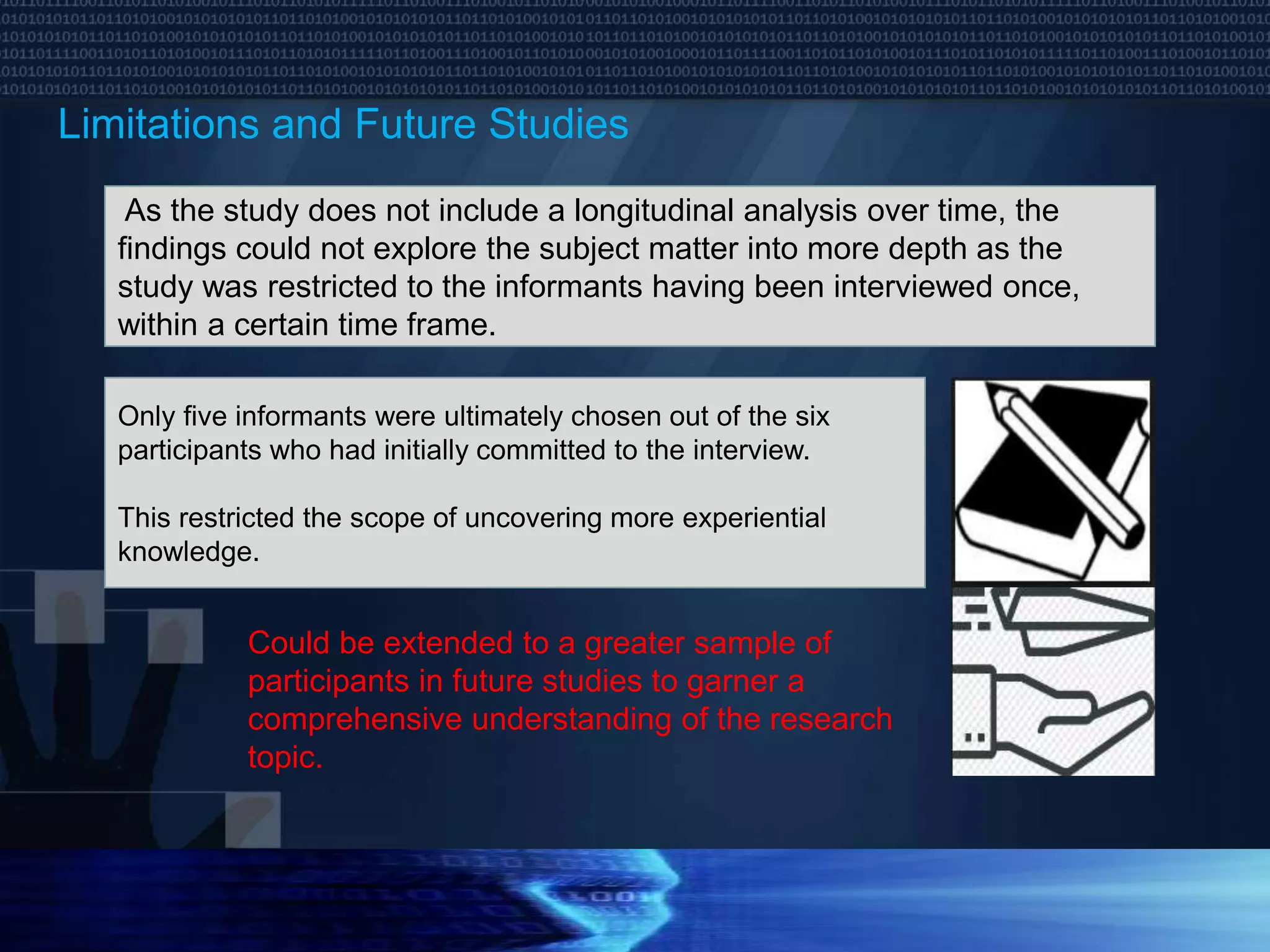
The document discusses the rise of cyber-attacks related to information theft and online fraud due to increased technology integration across organizations, highlighting that people are often the most vulnerable point of compromise. It emphasizes that cybersecurity involves a holistic approach of managing risks related to people, processes, and technology, and outlines various prevention, detection, and response strategies required for effective risk management in ICT infrastructure, especially within supply chains. The document concludes that a continuous improvement capability in cybersecurity is essential for ensuring business continuity amidst evolving threats.





















![• Shackleford, D., 2015. Combatting Cyber Risks in the Supply Chain. SANS Institute InfoSec Reading Room, [Online]. 1, 1-17. Available
at: https://www.sans.org/reading-room/whitepapers/analyst/combatting-cyber-risks-supply-chain-36252 [Accessed 21 August 2016].
•
• Urciuoli, L. 2015. Cyber-Resilience: A Strategic Approach for Supply Chain Management.Technology Innovation Management Review,
5(4): 13-18. http://timreview.ca/article/886
•
• Khan, O., & Estay, D. A. Sepúlv. 2015. Supply Chain Cyber-Resilience: Creating an Agenda for Future Research. Technology Innovation
Management Review, 5(4): 6-12. http://timreview.ca/article/885
•
•
• PwC . 2016. The Global State of Information Security® Survey 2016. [ONLINE] Available at:http://www.pwc.com/gx/en/issues/cyber-
security/information-security-survey.html. [Accessed 24 August 2016].
•
• Lane, D., 2011. The Chief Information Officer's Body of Knowledge: People, Process, and Technology. 1st ed. New Jersey: John Wiley &
Sons.
•
•
• Business Security Insider. 2016. THE 360 DEGREE APPROACH TO CYBER SECURITY. [ONLINE] Available at: https://business.f-
secure.com/cyber-security-is-not-a-solution-but-a-process/. [Accessed 25 August 2016].
•
• Juneja , N., Tuli, K., 2016. CYBER SECURITY CHALLENGES & ONLINE FRAUDS ON INTERNET.International Journal of Advanced
Research in IT and Engineering , [Online]. 5, 1-12. Available at:http://garph.co.uk/IJARIE/Feb2016/1.pdf [Accessed 21 August 2016].
•
•
• Booz Allen Hamilton, Booz Allen Hamilton, 2012. Managing Risks in Global ICT Supply Chains. Booz Allen Hamilton Report, 1-12.(
https://www.boozallen.com/content/dam/boozallen/media/file/managing-risk-in-global-ict-supply-chains-vp.pdf)
•
• Chacko, A., (2015). Cybersecurity - Integrating People, Process and Technology. In IASA 87TH ANNUAL EDUCATIONAL
CONFERENCE & BUSINESS SHOW. Las Vegas, June 7-10. Las Vegas: IASA. 1-37.
•
•
• Humphreys, E., 2008. Information security management standards: Compliance, governance and risk management. Information Security
Technical Report, 13, 247-255.
•](https://image.slidesharecdn.com/cyberrisksinsupplychains1-171204115019/75/Cyber-risks-in-supply-chains-26-2048.jpg)

![• Masvosvere, D.J.E. and Venter, H.S., 2015, August. A model for the design of next generation e-supply chain digital forensic readiness
tools. InInformation Security for South Africa (ISSA), 2015 (pp. 1-9). IEEE.
•
•
• Gartner. 2014. Designing an Adaptive Security Architecture for Protection From Advanced Attacks. [ONLINE] Available
at: https://www.gartner.com/doc/2665515/designing-adaptive-security-architecture-protection. [Accessed 24 August 2016].
•
• Elsbach, K.D. and Kramer, R.M., 2003. Assessing creativity in Hollywood pitch meetings: Evidence for a dual-process model of creativity
judgments.Academy of Management journal, 46(3), pp.283-301.
•
•
• Meredith, J., 1998. Building operations management theory through case and field research. Journal of operations management, 16(4),
pp.441-454.
•
• Marshall, M.N., 1996. Sampling for qualitative research. Family practice,13(6), pp.522-526.
•
•
• Marshall, C. and Rossman, G.B., 2014. Designing qualitative research.Sage publications.
•
• Narasimhan, R., 2014. Theory development in operations management: Extending the frontiers of a mature discipline via qualitative
research.Decision Sciences, 45(2), pp.209-227.
•
•
• Guercini, S., 2014.New qualitative research methodologies in management.Management Decision, 52(4), pp.662-674.
•
• Forza, C., 2002. Survey research in operations management: a process-based perspective. International journal of operations &
production management, 22(2), pp.152-194.
•
• Bowen, G.A., 2009. Document analysis as a qualitative research method.Qualitative research journal, 9(2), pp.27-40.
•](https://image.slidesharecdn.com/cyberrisksinsupplychains1-171204115019/75/Cyber-risks-in-supply-chains-28-2048.jpg)