Report
Share
Download to read offline
Recommended
More Related Content
What's hot
What's hot (17)
Are You Finding Out About Application Performance Problems From Your Users?

Are You Finding Out About Application Performance Problems From Your Users?
Quantitative Data-Driven Risk Management and Internal Audit

Quantitative Data-Driven Risk Management and Internal Audit
Outsourcing Email Management? Companies are getting the Message

Outsourcing Email Management? Companies are getting the Message
TrustedAgent GRC for Vulnerability Management and Continuous Monitoring

TrustedAgent GRC for Vulnerability Management and Continuous Monitoring
Best Practices and ROI for Risk-based Vulnerability Management

Best Practices and ROI for Risk-based Vulnerability Management
Viewers also liked
Viewers also liked (19)
Think Energy Ambassador Training at Wood Quay Venue - March 2014

Think Energy Ambassador Training at Wood Quay Venue - March 2014
Бизнес-мастерская "ТОП-10" - лучшие бизнес-книги по мнению экспертов

Бизнес-мастерская "ТОП-10" - лучшие бизнес-книги по мнению экспертов
Лицензирование управляющих компаний: Стандарт раскрытия информации

Лицензирование управляющих компаний: Стандарт раскрытия информации
Similar to Symantec Infographic
Similar to Symantec Infographic (20)
International Technology Adoption & Workforce Issues Study - Canadian Summary

International Technology Adoption & Workforce Issues Study - Canadian Summary
International Technology Adoption & Workforce Issues Study - Middle East Summary

International Technology Adoption & Workforce Issues Study - Middle East Summary
International Technology Adoption & Workforce Issues Study - German Summary

International Technology Adoption & Workforce Issues Study - German Summary
3 Considerations for IT Teams at Small-Midsized Firms

3 Considerations for IT Teams at Small-Midsized Firms
5 Reasons Why IT Managed Services in Washington, DC, Are the Best.pdf

5 Reasons Why IT Managed Services in Washington, DC, Are the Best.pdf
How to assess your Cybersecurity Vulnerability_.pdf

How to assess your Cybersecurity Vulnerability_.pdf
How to assess your Cybersecurity Vulnerability_.pptx

How to assess your Cybersecurity Vulnerability_.pptx
Module 8 - External Crisis – Changing Technology.pptx

Module 8 - External Crisis – Changing Technology.pptx
[Infographic] Are Data Center Demons Keeping You Up at Night?![[Infographic] Are Data Center Demons Keeping You Up at Night?](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] Are Data Center Demons Keeping You Up at Night?](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] Are Data Center Demons Keeping You Up at Night?
More from Sandra Augustin
More from Sandra Augustin (7)
Recently uploaded
Booking open Available Pune Call Girls Nanded City 6297143586 Call Hot India...

Booking open Available Pune Call Girls Nanded City 6297143586 Call Hot India...Call Girls in Nagpur High Profile
Captivating Charm: Exploring Marseille's Hillside Villas with Our 3D Architec...

Captivating Charm: Exploring Marseille's Hillside Villas with Our 3D Architec...Yantram Animation Studio Corporation
Recently uploaded (20)
VIP Russian Call Girls in Gorakhpur Deepika 8250192130 Independent Escort Ser...

VIP Russian Call Girls in Gorakhpur Deepika 8250192130 Independent Escort Ser...
CBD Belapur Individual Call Girls In 08976425520 Panvel Only Genuine Call Girls

CBD Belapur Individual Call Girls In 08976425520 Panvel Only Genuine Call Girls
Cheap Rate ➥8448380779 ▻Call Girls In Huda City Centre Gurgaon

Cheap Rate ➥8448380779 ▻Call Girls In Huda City Centre Gurgaon
Booking open Available Pune Call Girls Nanded City 6297143586 Call Hot India...

Booking open Available Pune Call Girls Nanded City 6297143586 Call Hot India...
The_Canvas_of_Creative_Mastery_Newsletter_April_2024_Version.pdf

The_Canvas_of_Creative_Mastery_Newsletter_April_2024_Version.pdf
VIP Call Girls Service Kukatpally Hyderabad Call +91-8250192130

VIP Call Girls Service Kukatpally Hyderabad Call +91-8250192130
Best VIP Call Girls Noida Sector 44 Call Me: 8448380779

Best VIP Call Girls Noida Sector 44 Call Me: 8448380779
AMBER GRAIN EMBROIDERY | Growing folklore elements | Root-based materials, w...

AMBER GRAIN EMBROIDERY | Growing folklore elements | Root-based materials, w...
CALL ON ➥8923113531 🔝Call Girls Kalyanpur Lucknow best Female service 🧵

CALL ON ➥8923113531 🔝Call Girls Kalyanpur Lucknow best Female service 🧵
Dubai Call Girls Pro Domain O525547819 Call Girls Dubai Doux

Dubai Call Girls Pro Domain O525547819 Call Girls Dubai Doux
VIP Call Girl Amravati Aashi 8250192130 Independent Escort Service Amravati

VIP Call Girl Amravati Aashi 8250192130 Independent Escort Service Amravati
Verified Trusted Call Girls Adugodi💘 9352852248 Good Looking standard Profil...

Verified Trusted Call Girls Adugodi💘 9352852248 Good Looking standard Profil...
Captivating Charm: Exploring Marseille's Hillside Villas with Our 3D Architec...

Captivating Charm: Exploring Marseille's Hillside Villas with Our 3D Architec...
Kala jadu for love marriage | Real amil baba | Famous amil baba | kala jadu n...

Kala jadu for love marriage | Real amil baba | Famous amil baba | kala jadu n...
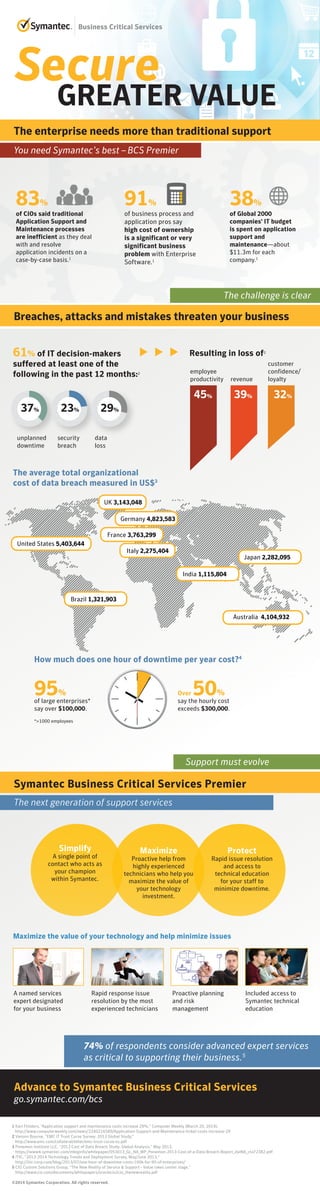
Symantec Infographic
- 1. The enterprise needs more than traditional support 83% of CIOs said traditional Application Support and Maintenance processes are inefficient as they deal with and resolve application incidents on a case-by-case basis.1 38% of Global 2000 companies’ IT budget is spent on application support and maintenance—about $11.3m for each company.1 91% of business process and application pros say high cost of ownership is a significant or very significant business problem with Enterprise Software.1 Simplify A single point of contact who acts as your champion within Symantec. Maximize Proactive help from highly experienced technicians who help you maximize the value of your technology investment. Protect Rapid issue resolution and access to technical education for your staff to minimize downtime. You need Symantec’s best –BCS Premier Breaches, attacks and mistakes threaten your business Symantec Business Critical Services Premier The next generation of support services The average total organizational cost of data breach measured in US$3 Advance to Symantec Business Critical Services go.symantec.com/bcs 61% of IT decision-makers suffered at least one of the following in the past 12 months:2 Resulting in loss of2 45% 39% 32% employee productivity unplanned downtime security breach data loss revenue customer confidence/ loyalty 37% 23% 29% United States 5,403,644 France 3,763,299 Italy 2,275,404 Japan 2,282,095 India 1,115,804 Brazil 1,321,903 Germany 4,823,583 Australia 4,104,932 UK 3,143,048 Support must evolve The challenge is clear 95% of large enterprises* say over $100,000. How much does one hour of downtime per year cost?4 Over 50% say the hourly cost exceeds $300,000. *>1000 employees Maximize the value of your technology and help minimize issues A named services expert designated for your business Rapid response issue resolution by the most experienced technicians Proactive planning and risk management Included access to Symantec technical education 74% of respondents consider advanced expert services as critical to supporting their business.5 Secure GREATER VALUE 1 Karl Flinders, "Application support and maintenance costs increase 29%,” Computer Weekly (March 20, 2014), http://www.computerweekly.com/news/2240216589/Application-Support-and-Maintenance-ticket-costs-increase-29 2 Vanson Bourne, "EMC IT Trust Curve Survey: 2013 Global Study," http://www.emc.com/collateral/other/emc-trust-curve-es.pdf 3 Ponemon Institute LLC, "2013 Cost of Data Breach Study: Global Analysis," May 2013, https://www4.symantec.com/mktginfo/whitepaper/053013_GL_NA_WP_Ponemon-2013-Cost-of-a-Data-Breach-Report_daiNA_cta72382.pdf 4 ITIC, "2013-2014 Technology Trends and Deployment Survey, May/June 2013," http://itic-corp.com/blog/2013/07/one-hour-of-downtime-costs-100k-for-95-of-enterprises/ 5 CIO Custom Solutions Group, “The New Reality of Service & Support - Value takes center stage,” http://www.cio.com/documents/whitepapers/oraclecio2cio_thenewreality.pdf ©2014 Symantec Corporation. All rights reserved.
