This document discusses the growing use of cloud computing and the critical importance of securing data stored in the cloud through cryptographic techniques. The paper highlights the challenges of data privacy and security, emphasizing the need for robust authentication and encryption methods, particularly the use of the Advanced Encryption Standard (AES) and the Elliptic Curve Digital Signature Algorithm (ECDSA). Furthermore, it presents a model for enhancing data protection through the integration of encryption and steganography to safeguard user information during storage and transmission.


![International Journal of Trend in Scientific Research and Development (IJTSRD) @ www.ijtsrd.com eISSN: 2456-6470
@ IJTSRD | Unique Paper ID – IJTSRD42363 | Volume – 5 | Issue – 4 | May-June 2021 Page 587
key at the same time as in uneven encryption the keys are
distinctive. These days hash function is also being used in
which a hash cost is computedbasedonplaintextual content
to provide a diploma of integrity to the data.
B. Hybrid Symmetric Encryption Algorithm
Symmetric encryption entails the usage of a single mystery
key for both the encryption and decryptionofstatistics.Only
symmetric encryption has the speed and computational
efficiency to deal with encryption of large volumes of data.
This approach emphasizesonimprovingclassical encryption
strategies by using integrating substitution cipher and
transposition cipher. Both substitution and transposition
strategies have used alphabet for cipher text. In the
proposed set of rules, initially the apparent text is converted
into corresponding ASCII code price of each alphabet. In
classical encryption technique, the important thing price
stages among 1 to 26 or key can be string (combination
alphabets). But in proposed set of rules, key cost variety
between 1 to 256. This algorithm is used in an effort to
encrypt the records of the consumer within theclouds.Since
the person has no control over the information after his
session is logged out, the encryption key acts because the
number one authentication for the consumer. N. This set of
rules is used on the way to encrypt the records of the user
inside the cloud. Since the user has no control over the facts
as soon as their consultation is logged out, the encryption
key acts as the number one authentication fortheconsumer.
By making use of this encryption algorithm, consumer
ensures that the records are stored handiest on secured
storage and it cannot be accessed through directors or
intruders.
C. Encryption and Steganography
This version to be presented is primarily based on the
precept of securing information each at some stage in
transmission and even as information-at rest at servers.
The cloud architecture being used is as shown below:
FIG 1: Architectural flow
The operating of this version is as follows:
A] Storing Process
Its working is defined as follows:
1) The person selects the information to be uploaded and
this selected information receives encrypted using a sturdy
set of rules including AES algo.
2) The encrypted facts are then uploaded to server.
3) On receiving facts, one that got here from user aspect a
hiding set of rules is carried out which randomly selects the
bits positions
from snap shots in which statistics is to be stored. The bit
role is either 0th, 1st or 2d position.
4) This hiding set of rules is used to keep the files or records
in the back of the pics. This procedure is known as
steganography using snap shots.
FIG 2: Storing process flowchart
B. Retrieval Process
Its working is as follows:
1) When consumer demands information returned a
retrieval, algorithm extracts picture and separates person
information from them.
2) This extracted information is then sent to consumer.
3) On client aspect, the encrypted data is decrypted and the
unique facts is retrieved.
FIG 3: Retrieval process flowchart
The above version addresses protection of statistics at
stages, one while information is moved to far flung servers
and another whilst it's far being stored and is guarded by
way of the cloud carrier provider officials.
In the above version, two simple methods of encryption and
steganography were done. Now for the success of this
version it's miles essential that images produced after
steganography must be nicely built-in order that it isn't
always viable to differentiate between original and stego pic
and subsequently now not possible to stumble on the
presence of information.
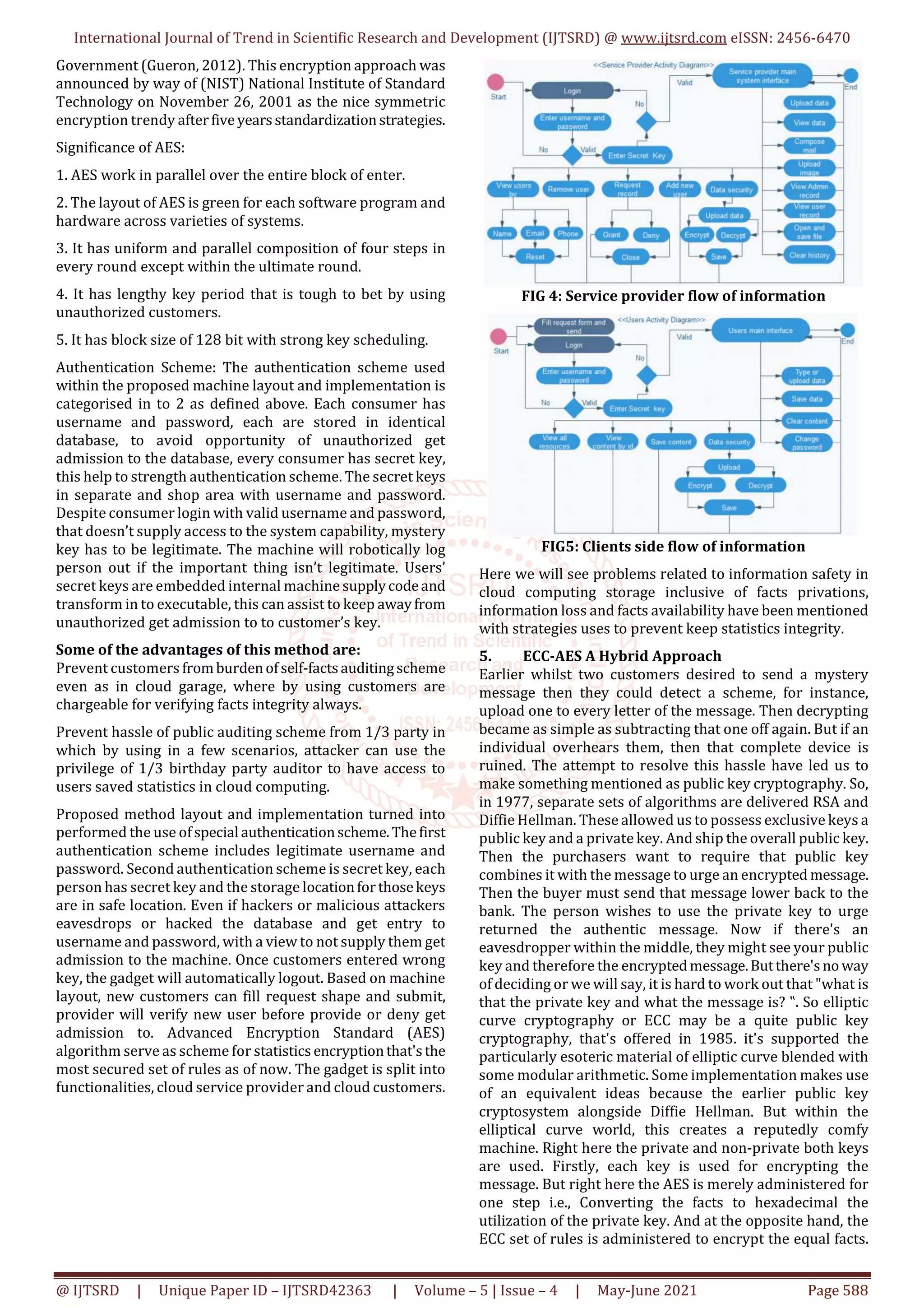
4. Advanced Encryption Standard (AES) And Authentication
Scheme (AS)
Encryption Standard is selected as technique for records
encryption and decryption. The AES served as symmetric
encryption trendy of statistics processing for United State](https://image.slidesharecdn.com/96studyonsecurecryptographictechniquesincloud-210715055946/75/Study-on-Secure-Cryptographic-Techniques-in-Cloud-3-2048.jpg)


![International Journal of Trend in Scientific Research and Development (IJTSRD) @ www.ijtsrd.com eISSN: 2456-6470
@ IJTSRD | Unique Paper ID – IJTSRD42363 | Volume – 5 | Issue – 4 | May-June 2021 Page 591
mean that the facts owner can proportion private data using
a great-grained approach, e.g., adding a unmarried file or a
class of files. The feature of heterogeneity substantially
improves the performance of the algorithm and at the same
time makes it extra handy and like-mindedwiththemachine
advanced based on thetraditional PKEencryptionalgorithm.
An interesting direction for future paintings would be to
make this scheme comfier with the aid of helping different
ciphertext security schemes and addressing different
protection troubles. Wealsoneedtocontinuetooptimize the
performance and make this scheme extra realistic and to
carry out studies into dynamic facts privateness protection
inside the cloud.
Problems associated with statistics protection in cloud
computing storage such as statistics privacy, data loss and
information availabilitywerementionedwithstrategies uses
to prevent shop facts integrity.Reviewedofassociatedwork,
studies truth locating and improvement technique also said
on this paper. Detail descriptionofproposedgadgetchanged
into mentioned with screenshot of a few essential a part of
system interface and functionalities. Additional
functionalities for futures paintings includes Auto
verification of users’ encrypted information while in transit
over internet to make sure that it doesn’t include any
harmful facts. Provide method of secured communique
among cloud customers while tracking their sports and
safety of network layers. Time eager about the resource of
ECC-AES is comparably low. And in determine here bars are
displaying the decryption time concerned about the useful
resource of both the AES set of rules and ECC-AES set of
rules. Here additionally the time eager about the aid of ECC-
AES is comparably low. The ECC encryption scheme may be
very time green and require less computationandmoreover
much less reminiscence place. And alternatively, AES offers
an immoderate protection. So, this hybrid model gives a
higher protection degree by means of combining the
capabilities of both. The use of those two blended strategies
makes the more complex system for an eavesdropper. This
hybrid technique offers a faster manner of each encrypting
and decrypting a document thanthestandaloneAESversion.
For destiny scope, the ECC encryption scheme may be
combine with some different similar encryption set of
guidelines then the AES. Also, we will say that the ECC is the
destiny of cryptography. Its mathematical complexity and
time performance deliver it a completely specific degree.
With the intention to copewiththetroublesproficientmodel
which includes records integrity, data loss and comfortable
information get right of entry to. It isdesignedinsidethe sort
of manner to provide stop – to – cease protection in the
cloud. It allows to guarantee theinformationcorrectnessand
moreover, permits toconcurrentlydiscoverthemisbehaving
servers within the cloud machine. It lets in the statistics
proprietor to have complete control of his very personal
information via tracking the get proper of entry to logs of
information document via allocated auditingmechanism. To
upload extra safety at the get right of entrytolevels,thefacts
has been transformed in a greater bendy and scalable form
with quality grained get right of entry to control. Finally, the
facts have been secured at all the tiers together with at
relaxation, during transit and get properofaccesstoinorder
to provide a whole end to end protection.
References
[1] P. Yang , N. Xiong and J. Ren , "Data Security and
Privacy Protection for Cloud Storage:ASurvey,"IEEE,
vol. 8, 2020.
[2] L. C. J. P. Singh, M. B. Rajshree and S. Ku,ar,
"Authentication and EncryptioninCloudComputing,"
in International ConferenceonSmartTechnologiesand
Management, 2015.
[3] J. Shen, . X. Deng and . Z. Xu , "Multi-security-level
cloud storage system based on improved proxy re-
encryption," EURASIP Journal on Wireless
Communications and Networking, vol. 2, 2019.
[4] A. Kajal and G. , "Enhanced Cloud Storage Security
Using ECC-AES A Hybrid Approach," International
Journal for Research in Engineering Application &
Management (IJREAM) , vol. 04, 2018.
[5] S. Kang, B. Veeravalli and K. M. M. Aung, "ESPRESSO:
An Encryption as a Service for Cloud Storage
Systems," International Federation for Information
Processing, pp. 15-28, 2014.
[6] M. Ismail and B. Yusuf, "ENSURING DATA STORAGE
SECURITY IN CLOUD COMPUTING WITH ADVANCED
ENCRYPTION STANDARD (AES) AND
AUTHENTICATION SCHEME (AS)," International
Journal of Information System and Engineering, vol. 4,
pp. 18-39, 2016.
[7] R. B. Chandar, M. S. Kavitha and K. Seenivasan, "A
PROFICIENT MODEL FOR HIGH END SECURITY IN
CLOUD COMPUTING," ICTACT JOURNAL ON SOFT
COMPUTING, vol. 4, no. 2, pp. 697-702, 2014.
[8] K. Handa and . U. Singh, "Data Security in Cloud
Computing using Encryption and Steganography,"
International Journal of Computer Science and Mobile
Computing, vol. 4, pp. 786-791, 2015.
[9] M. K. Sarkar and T. Chatterjee, "Enhancing Data
Storage Security in Cloud Computing Through
Steganography," ACEEE Int. J. onNetwork, vol.5,2014.
[10] A. Sidhu and . R. Mahajan, "Enhancing security in
cloud computing structure by hybrid encryption,"
International Journal of Recent Scientific, vol. 5, no. 1,
pp. 128-132, 2014.
[11] P. Mukhi and . B. Chauhan, "Survey on triple system
security in cloud computing," IJCSMC, vol. 3, no. 4,
2014.
[12] S. Singla and J. Singh, "Cloud Data Security using
Authentication and Encryption Technique," IJARCET,
vol. 2, no. 7, 2013.
[13] . L. M. K. John Harauz, "Data security in the world of
cloud computing," IEEE Computer and Reliability
society. .
[14] . K. Madhavi, R. Tamilkodi and R. BalaDinakar, "Data
Storage Security in Cloud Computing for Ensuring
Effective and Flexible Distributed System,"
International Journal of Electronics Communication
and Computer Engineering , vol. 3, pp. 133-134, 2012.
[15] N. Zhang, D. Liu and Y.-Y. Zhang, "A ResearchonCloud
Computing Security," IEEE International Conference
on Information Technology and Application, pp. 370-
373, 2013.
[16] V. . R. Pancholi and . B. . P. Patel, "Enhancement of
Cloud Computing Security with Secure Data Storage
using AES," International Journal for Innovative](https://image.slidesharecdn.com/96studyonsecurecryptographictechniquesincloud-210715055946/75/Study-on-Secure-Cryptographic-Techniques-in-Cloud-7-2048.jpg)
![International Journal of Trend in Scientific Research and Development (IJTSRD) @ www.ijtsrd.com eISSN: 2456-6470
@ IJTSRD | Unique Paper ID – IJTSRD42363 | Volume – 5 | Issue – 4 | May-June 2021 Page 592
Research in Science and Technology , vol. 2, no. 9, pp.
18-21, 2016.
[17] P. . M. Pardeshi and D. . R. Borade, "mproving Data
Integrity for Data Storage Security in Cloud
Computing,"InternationalJournalofComputerScience
and Network Security , vol. 15, no. 7, pp. 61-67, 2015.
[18] G. . A. and K. , "A Review on Cloud Storage security,"
International journal of innovation in engineering
research & management, vol. 5, no. 2, 2018.
[19] K. A. Jothy, . K. Sivakumar and . D. M J, "Enhancing the
security of the cloud computing with triple AES, PGP
over SSL algorithms," International Journal of
engineering sciences & research technology, 2018.
[20] K. M. V and . M. Santhanalakshmi, "Remote Data
Integrity Checking inCloudComputing,"International
Journal on Recent and innovation trends in computing
and communication, pp. 426-436, 2017.](https://image.slidesharecdn.com/96studyonsecurecryptographictechniquesincloud-210715055946/75/Study-on-Secure-Cryptographic-Techniques-in-Cloud-8-2048.jpg)