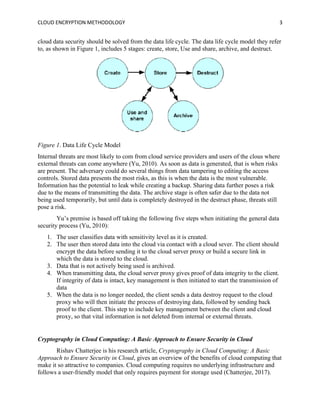
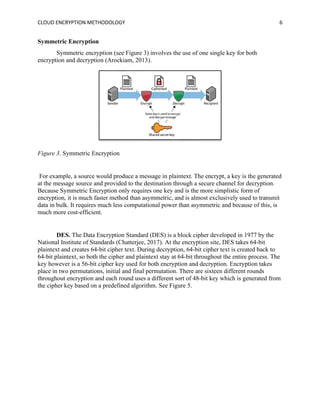
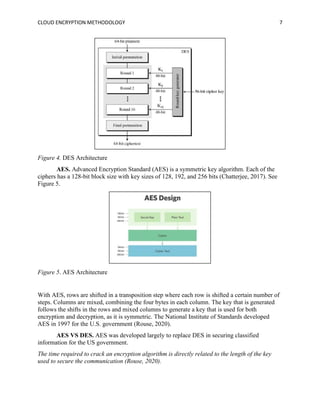
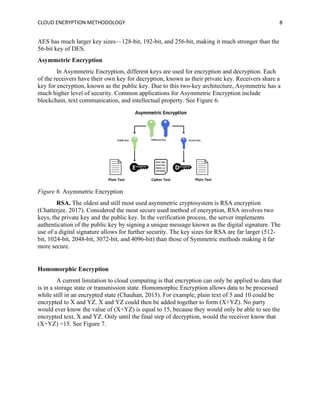
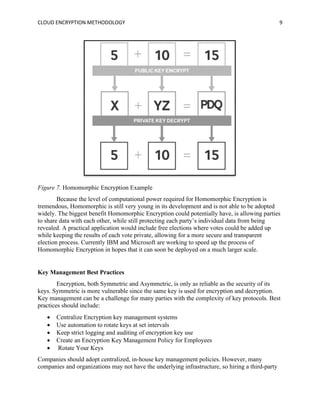
The document discusses the importance of cloud encryption methodologies in securing data within cloud computing, including a review of various encryption techniques such as symmetric, asymmetric, and homomorphic encryption. It highlights the challenges organizations face regarding data security due to cyber threats and emphasizes the need for effective key management practices. Additionally, the paper suggests that the future of cloud encryption may lie in advancing homomorphic encryption to allow data processing while keeping information encrypted.