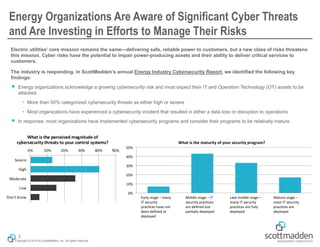
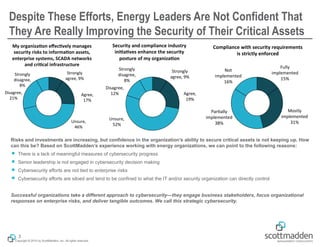
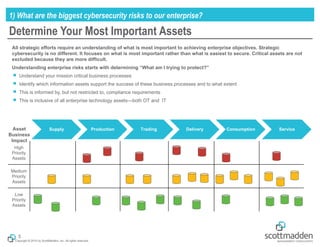
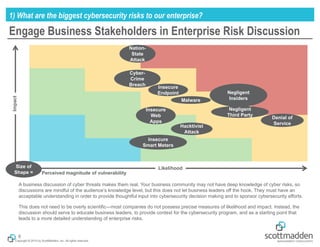
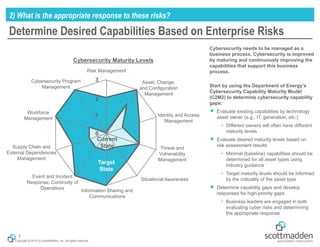
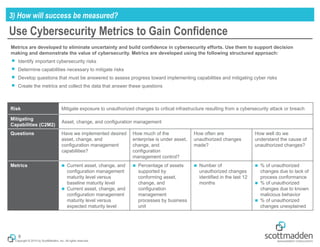
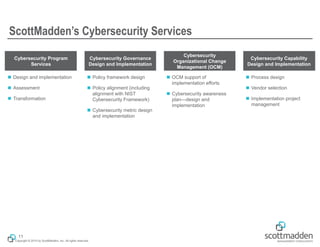
The document outlines a strategic approach to cybersecurity for energy organizations, emphasizing the need for engagement from senior leadership and alignment with enterprise risks. It identifies critical questions for guiding cybersecurity efforts, including assessing risks, defining desired capabilities, and measuring success using structured metrics. The goal is to enhance cybersecurity programs by prioritizing risks, improving capabilities, and maintaining continuous improvement while ensuring business objectives are met.