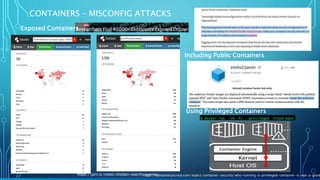
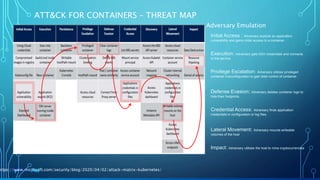
The document evaluates container security through the lens of the ATT&CK framework, highlighting current technology trends, vulnerability timelines, and misconfiguration attack strategies. It discusses various vulnerabilities and challenges faced in container runtime, orchestration, and response practices. The conclusion emphasizes understanding adversary behavior to improve defenses and mitigate risks effectively.