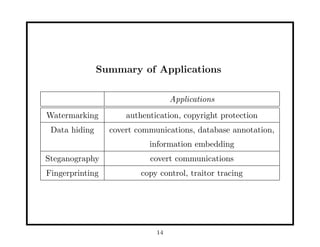
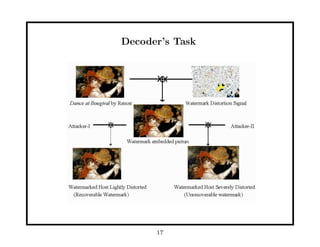
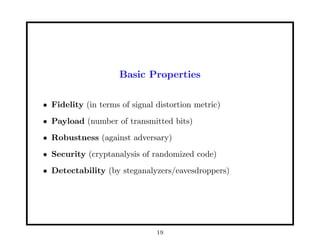
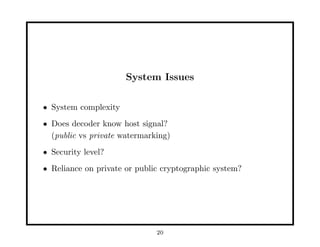
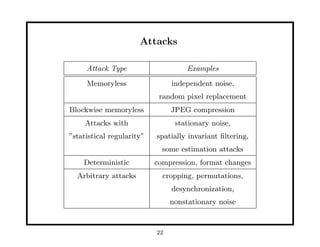
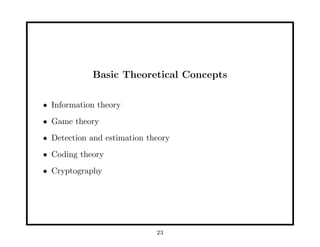
This document provides an overview of fundamentals of watermarking and data hiding. It discusses basic techniques, performance analysis in terms of error probabilities and capacity, and applications to images and advanced topics. The document outlines the tutorial, which covers data hiding, watermarking and steganography applications, embedding data in images, attacks on watermarked images, and basic theoretical concepts from information theory, game theory, coding theory and cryptography that are relevant to understanding fundamental limits of information hiding.