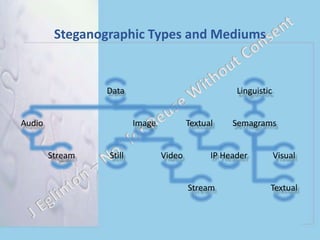
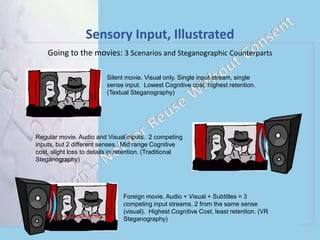
Digital Steganography and Virtual Environments discusses steganography techniques for hiding secret messages. It defines steganography and its constraints. Examples are given of real-world uses of steganography in photos and malware. Applications in virtual environments like gaming are discussed, but limitations exist due to human cognitive abilities. While virtual reality could theoretically hide large amounts of data, the fast streaming of multiple inputs exceeds human processing and would result in low integrity of decrypted messages. Traditional steganography techniques remain most effective currently.