Statistics of 2015 Data Breaches
•
1 like•212 views
The document summarizes statistics about data breaches that occurred in 2015 according to a report from Trustwave. The report found that 75% of data breaches in the hospitality industry involved point of sale systems while food and beverage had more even splits between POS and network breaches. Most common types of data compromised across all industries were financial credentials and proprietary data. Breaches were detected internally through self-monitoring more often than being notified by external regulators or law enforcement.
Report
Share
Report
Share
Download to read offline
Recommended
New fraud protection solutions

The document discusses new requirements for fraud prevention across multiple channels as attacks are expanding due to increased mobile and online banking usage. It summarizes a presentation about an omni-channel fraud prevention solution from Guardian Analytics that provides a 360 degree view of customers and activities across channels through integrated data and advanced behavioral analytics. The solution aims to improve fraud detection and reduce customer friction by consolidating risk scoring and providing real-time visibility of customer behaviors and risks across all channels in a single system.
Stop wire fraud aug 2016

The document summarizes Guardian Analytics' wire fraud protection solution. It discusses the rise of business email compromise (BEC) wire fraud, with funds lost increasing over 400% from 2015 to 2016. Guardian Analytics protects customers of the Fiserv wire transfer platform WireXchange through real-time risk scoring of wire transactions. This solution has successfully prevented millions of dollars in fraudulent wires for various banks and credit unions. The document promotes Guardian Analytics' fraud detection capabilities and provides customer testimonials and a diagram of how its real-time wire monitoring works integrated with the WireXchange system.
Guardian analytics vs. actimize 2016

This document summarizes the capabilities of Guardian Analytics' machine learning and behavioral analytics solutions for financial fraud detection compared to Actimize. It states that Guardian Analytics offers omni-channel visibility, behavioral analytics that require no rules, and machine learning that continuously updates models without human intervention. It also provides rapid deployment, flexible hosting options, visual analytics, and integrates risk data from multiple sources. In contrast, it describes Actimize as having poor user interfaces, requiring extensive rule maintenance, long deployments, and high costs.
New! Omni-Channel Fraud Prevention 

The document introduces Guardian Analytics' Omni-Channel Fraud Prevention and Omni-Channel Visual Analytics products. The products provide a 360 degree view of customer risk across channels using behavioral analytics and machine learning. They consolidate customer activity, risk data, and fraud alerts from multiple systems. This allows financial institutions to make faster fraud decisions and gain insights into criminal patterns across payment types and channels.
FinTech Belgium Summit 2018 - Vadis Technologies - Jean-François Heering

Vadis Technologies offers data analytics and risk monitoring services through its Flair platform to help clients gain insights on third parties. The platform matches and links public and private data on over 300 million companies, 200 million individuals, and 215 countries. It provides over 100 predictive indicators to analyze entities' risk of bankruptcy, sales, and other economic factors. The platform aims to help users identify high-risk suppliers, potential conflicts of interest, compliance issues, fast-growing prospects, fraud patterns, and financial stability of partners.
Preventing P2P Fraud with Aite Group

Only real-time fraud detection solutions can prevent Peer-to-Peer fraud. Aite Group and Guardian Analytics show you what to be concerned about and how to detect in real-time evolving attacks from fraudsters.
The Enemy at the Gates: Payments Fraud Is a Symptom

New research from Mercator Advisory Group examines increased global cyber threat, payments fraud, and how to manage the risks.
Cybercrime is a global and growing phenomenon tied to a combination of factors that includes the new era of global economic interdependency along with rapidly changing technology, according to a new research report from Mercator Advisory Group. These factors create opportunities for criminals to find new and often faster ways to defraud businesses of all sizes. Data breaches will inevitably lead to follow-on activities that take advantage of people, holes in processes, and cracks in systems to transfer wealth from legitimate sources to fraudsters across the globe. A range of activities can be undertaken by companies to create better protective cover around organizational data and prevent or limit the damage from payments fraud.
Insurance stream - Marc DonFrancesco slides

This document discusses fraud detection methods used by an online company. It describes how the company uses information from an IP provider like device type, IP address, location, and other evidence to build understanding of potential clients and detect fraud. Rules are used to allow, review, or deny applications, with many sent for human review. Fraud types seen include identity fraud, application fraud, and account takeover. Crime gangs are observed using stolen identities and cloned cards from the dark web along with dynamic IPs to fraudulently apply for loans from PCs. Continual innovation is needed to address evolving fraud risks.
Recommended
New fraud protection solutions

The document discusses new requirements for fraud prevention across multiple channels as attacks are expanding due to increased mobile and online banking usage. It summarizes a presentation about an omni-channel fraud prevention solution from Guardian Analytics that provides a 360 degree view of customers and activities across channels through integrated data and advanced behavioral analytics. The solution aims to improve fraud detection and reduce customer friction by consolidating risk scoring and providing real-time visibility of customer behaviors and risks across all channels in a single system.
Stop wire fraud aug 2016

The document summarizes Guardian Analytics' wire fraud protection solution. It discusses the rise of business email compromise (BEC) wire fraud, with funds lost increasing over 400% from 2015 to 2016. Guardian Analytics protects customers of the Fiserv wire transfer platform WireXchange through real-time risk scoring of wire transactions. This solution has successfully prevented millions of dollars in fraudulent wires for various banks and credit unions. The document promotes Guardian Analytics' fraud detection capabilities and provides customer testimonials and a diagram of how its real-time wire monitoring works integrated with the WireXchange system.
Guardian analytics vs. actimize 2016

This document summarizes the capabilities of Guardian Analytics' machine learning and behavioral analytics solutions for financial fraud detection compared to Actimize. It states that Guardian Analytics offers omni-channel visibility, behavioral analytics that require no rules, and machine learning that continuously updates models without human intervention. It also provides rapid deployment, flexible hosting options, visual analytics, and integrates risk data from multiple sources. In contrast, it describes Actimize as having poor user interfaces, requiring extensive rule maintenance, long deployments, and high costs.
New! Omni-Channel Fraud Prevention 

The document introduces Guardian Analytics' Omni-Channel Fraud Prevention and Omni-Channel Visual Analytics products. The products provide a 360 degree view of customer risk across channels using behavioral analytics and machine learning. They consolidate customer activity, risk data, and fraud alerts from multiple systems. This allows financial institutions to make faster fraud decisions and gain insights into criminal patterns across payment types and channels.
FinTech Belgium Summit 2018 - Vadis Technologies - Jean-François Heering

Vadis Technologies offers data analytics and risk monitoring services through its Flair platform to help clients gain insights on third parties. The platform matches and links public and private data on over 300 million companies, 200 million individuals, and 215 countries. It provides over 100 predictive indicators to analyze entities' risk of bankruptcy, sales, and other economic factors. The platform aims to help users identify high-risk suppliers, potential conflicts of interest, compliance issues, fast-growing prospects, fraud patterns, and financial stability of partners.
Preventing P2P Fraud with Aite Group

Only real-time fraud detection solutions can prevent Peer-to-Peer fraud. Aite Group and Guardian Analytics show you what to be concerned about and how to detect in real-time evolving attacks from fraudsters.
The Enemy at the Gates: Payments Fraud Is a Symptom

New research from Mercator Advisory Group examines increased global cyber threat, payments fraud, and how to manage the risks.
Cybercrime is a global and growing phenomenon tied to a combination of factors that includes the new era of global economic interdependency along with rapidly changing technology, according to a new research report from Mercator Advisory Group. These factors create opportunities for criminals to find new and often faster ways to defraud businesses of all sizes. Data breaches will inevitably lead to follow-on activities that take advantage of people, holes in processes, and cracks in systems to transfer wealth from legitimate sources to fraudsters across the globe. A range of activities can be undertaken by companies to create better protective cover around organizational data and prevent or limit the damage from payments fraud.
Insurance stream - Marc DonFrancesco slides

This document discusses fraud detection methods used by an online company. It describes how the company uses information from an IP provider like device type, IP address, location, and other evidence to build understanding of potential clients and detect fraud. Rules are used to allow, review, or deny applications, with many sent for human review. Fraud types seen include identity fraud, application fraud, and account takeover. Crime gangs are observed using stolen identities and cloned cards from the dark web along with dynamic IPs to fraudulently apply for loans from PCs. Continual innovation is needed to address evolving fraud risks.
ISMG - Fighting Business Email Compromise

The document discusses behavioral analytics for preventing fraud. It summarizes a presentation by Anand Sureka of Guardian Analytics on using behavioral analytics to detect fraud across channels in real-time. It provides examples of how Guardian Analytics' solutions use machine learning on over 100 attributes to generate risk scores for transactions and prevent fraud like business email compromise and account takeover. It highlights case studies where banks saw millions in fraud prevented and significant reductions in manual review volumes and call backs.
IT Trends - Cyber Security

On average, enterprises collaborate with hundreds of other organizations and use public cloud apps, contributing to massive growth in data volumes and connectivity. While only 12% of sensitive data is typically passed internally, 10% is shared with external partners and 2% becomes publicly available. The most common types of sensitive data include intellectual property, personal identification information, medical information, financial information, and internal communications.
AML Penalties Intro Deck 

The Most Extensive Money Laundering Events Based Data Platform, For AML Professionals, Organizations & Regulators. AML, Risk & Banking Professionals have limited access to data, information and tools to combat money laundering risks, effectively.
To add further complexity, the AML & FCC landscape has seen a paradigm shift - both in terms of emerging threats as well as in the complexity of managing compliance & regulatory goals.
Op tijd klaar voor de naderende gdpr avg privacywet - Janus de Visser

GDPR/AVG presentatie gegeven door Janus de Visser bij LevelUp Group op 29 maart 2018 tijdens de LevelUp Group Online Marketing Update
AML Penalties Closed Beta 7 June 2021

The Anti-Money Laundering (AML) and Financial Crimes Compliance (FCC) landscape has radically evolved over the last decade. New areas of risk (Data breaches, Crypto, TBML, etc.) have emerged, compliance costs have jumped (USD 181 Bn in 2020) and most banks (over 60%) expect compliance spends to increase significantly.
Complicating things further, most AML professionals continue to have limited access to tools, data, and resources.
Presenting AML Penalties!
With access to over a million data points and global information, AML professionals may now safeguard their organization's interests while staying up to date on the latest events in the AML space.
To experience AML Penalties, you can set up a free account by visiting https://lnkd.in/e4q4WCm.
{The platform is best experienced on a laptop or computer.}
#amlpenalties #dataassets #zigram #antimoneylaundering #financialcrimecompliance #amlcompliance #amlcft #riskmanagement #data #banking
Affiliate Fraud Trends & the Policies Needed in the Industry

This presentation is from Affiliate Summit East 2015 (August 2-4, 2015 in New York, NY). Session description: The industry needs established policies for monitoring affiliate fraud or identity theft: review online traffic, survey consumers, & implement fraud detection software or affiliate scrubbing service.
An Introduction to GDPR

On the 18th January we attended an interesting event in Lisbon, Portugal. Our goal was to bring together lawyers and engineers, with the aim of providing a wide overview of GDPR from the two different perspectives.
Here's our presentation from that GDPR conference.
Detecting Wire Fraud in Real-Time

Faster payments mean higher risk for fraud, especially through Business Email Compromise (BEC). Learn how to prevent fraudulent Wire transfers from identification to intervention.
The Insurance Digital Revolution Has a Fraud Problem

The rapid digitalization of the Insurance Industry has not only opened up access channels for customers, but also created targets for fraudsters. The time is now to protect your business from fraud as you convert to digital. In this webinar, we’ll analyze the 5 Strategic Approaches to Digital Optimization and Transformation in Insurance that Gartner laid out in their report and explore possible fraud threats that can arise as a result of such transformation.
Register today to learn more from us about:
- Combating fraud threats introduced by the move to digital, such as ghost broking
- Detecting and preventing growing account takeover
- Protecting the entire customer lifecycle
- How to arm your SIU to more effectively fight fraudulent claims
- Improve identity verification to reduce early term losses
Cybersecurity's Impact on Innovation

Most small and mid-sized tech and healthcare companies are maintaining or increasing their cybersecurity resources this year in preparation for inevitable cyber attacks. While half are increasing spending, most are investing in active response capabilities rather than infrastructure. Only a small minority of companies express high confidence in the security of their information, and many see serious business disruption risks from cyber attacks.
2014-15 Cybersecurity Venture Funding and M&A

This document analyzes trends in cybersecurity venture funding and mergers & acquisitions from 2014-2015. It finds that:
1) Endpoint protection companies received a disproportionate amount of funding compared to their representation among funded companies.
2) Round sizes have increased across the board, particularly for Series C rounds. This suggests Series C rounds may be replacing pre-IPO rounds.
3) Cybersecurity mergers and acquisitions deals have significantly decreased in 2015 compared to 2014, possibly due to high valuation scaring away strategic buyers.
More data is needed but the trends show increasing funding amounts coupled with fewer exit opportunities in the cybersecurity industry.
Investing in Cybersecurity, 2020 outlook for Mexico

The document discusses investing in cybersecurity for 2020. It notes that Mexico is the 8th most targeted country by ransomware hackers. Global spending on cybersecurity services exceeds $124 billion annually from 4300 companies. Private capital investment in cybersecurity startups has grown 19% annually in recent years, with some startups raising over $100 million. However, M&A exit activity has not reflected this growth. The document suggests areas Mexico could improve in, such as supporting home-grown cybersecurity and public-private partnerships. It notes that 9 cybersecurity startups currently call Mexico home.
Fraud infographic - Forrester Report

Did you know that global fraud losses predicted by 2020 is $2 trillion? Check out Forrester's fraud report and get more insight about the industry trends.
5 startups using machine learning and behavioral biometrics to fight fraud

This document summarizes 5 startups that are using machine learning and behavioral biometrics to fight fraud. It provides details on each startup such as their funding amounts, investors, and business models. Some key points are that behavioral biometrics can identify users through unconscious behaviors, machine learning is used to analyze vast amounts of user data to detect fraud patterns, and the featured startups provide fraud detection and prevention platforms to help protect companies from online fraud.
IoT Security RoundTable - March 2018

This document summarizes a panel discussion on security for Internet of Things (IoT) devices and secure payment transactions. The panel discussed trends driving the need for improved payment security within IoT, including the evolution of use cases, increased cyberattacks, adoption of digital currencies, and new regulations. Panelists addressed how different players in the IoT payment ecosystem are addressing security challenges, including the roles of devices, semiconductor vendors, platforms, payment vendors, and existing payment networks. The role of new technologies like blockchain was also discussed. The panel provided an opportunity for open discussion between the presenters and audience.
Generali - Fraud Analytics

This document discusses Generali Group, an international insurance company, and its efforts to detect insurance fraud. It provides an overview of Generali Group, describing it as one of the leading insurers in the world with operations in over 60 countries. It then discusses the problem of insurance fraud and some common types. It outlines Generali's solution to fraud detection, which involves using a graph database and applying techniques like rule-based analysis, social network analysis, and machine learning to processed insurance claims data.
Australia part 2

This document lists several locations in South Australia including Victor Harbor, Granite Island, Coolwa, Kangaroo Island, and Flinders Chase National Park. It also mentions seeing Australian Pelicans, kangaroos, seals, and sea lions at some of these locations.
Austraila part 3

This document discusses three locations: Admirals Arch, a natural sea arch on the coast of South Australia; New Zealand fur seal, a species of fur seal; and Remarkable Rocks, unusual granite boulders located in Kangaroo Island, South Australia.
10 IT Security Trends to Watch for in 2016

This brief piece takes a look at what we think will be the top trends to look for (and beware of) in 2016.
More Related Content
What's hot
ISMG - Fighting Business Email Compromise

The document discusses behavioral analytics for preventing fraud. It summarizes a presentation by Anand Sureka of Guardian Analytics on using behavioral analytics to detect fraud across channels in real-time. It provides examples of how Guardian Analytics' solutions use machine learning on over 100 attributes to generate risk scores for transactions and prevent fraud like business email compromise and account takeover. It highlights case studies where banks saw millions in fraud prevented and significant reductions in manual review volumes and call backs.
IT Trends - Cyber Security

On average, enterprises collaborate with hundreds of other organizations and use public cloud apps, contributing to massive growth in data volumes and connectivity. While only 12% of sensitive data is typically passed internally, 10% is shared with external partners and 2% becomes publicly available. The most common types of sensitive data include intellectual property, personal identification information, medical information, financial information, and internal communications.
AML Penalties Intro Deck 

The Most Extensive Money Laundering Events Based Data Platform, For AML Professionals, Organizations & Regulators. AML, Risk & Banking Professionals have limited access to data, information and tools to combat money laundering risks, effectively.
To add further complexity, the AML & FCC landscape has seen a paradigm shift - both in terms of emerging threats as well as in the complexity of managing compliance & regulatory goals.
Op tijd klaar voor de naderende gdpr avg privacywet - Janus de Visser

GDPR/AVG presentatie gegeven door Janus de Visser bij LevelUp Group op 29 maart 2018 tijdens de LevelUp Group Online Marketing Update
AML Penalties Closed Beta 7 June 2021

The Anti-Money Laundering (AML) and Financial Crimes Compliance (FCC) landscape has radically evolved over the last decade. New areas of risk (Data breaches, Crypto, TBML, etc.) have emerged, compliance costs have jumped (USD 181 Bn in 2020) and most banks (over 60%) expect compliance spends to increase significantly.
Complicating things further, most AML professionals continue to have limited access to tools, data, and resources.
Presenting AML Penalties!
With access to over a million data points and global information, AML professionals may now safeguard their organization's interests while staying up to date on the latest events in the AML space.
To experience AML Penalties, you can set up a free account by visiting https://lnkd.in/e4q4WCm.
{The platform is best experienced on a laptop or computer.}
#amlpenalties #dataassets #zigram #antimoneylaundering #financialcrimecompliance #amlcompliance #amlcft #riskmanagement #data #banking
Affiliate Fraud Trends & the Policies Needed in the Industry

This presentation is from Affiliate Summit East 2015 (August 2-4, 2015 in New York, NY). Session description: The industry needs established policies for monitoring affiliate fraud or identity theft: review online traffic, survey consumers, & implement fraud detection software or affiliate scrubbing service.
An Introduction to GDPR

On the 18th January we attended an interesting event in Lisbon, Portugal. Our goal was to bring together lawyers and engineers, with the aim of providing a wide overview of GDPR from the two different perspectives.
Here's our presentation from that GDPR conference.
Detecting Wire Fraud in Real-Time

Faster payments mean higher risk for fraud, especially through Business Email Compromise (BEC). Learn how to prevent fraudulent Wire transfers from identification to intervention.
The Insurance Digital Revolution Has a Fraud Problem

The rapid digitalization of the Insurance Industry has not only opened up access channels for customers, but also created targets for fraudsters. The time is now to protect your business from fraud as you convert to digital. In this webinar, we’ll analyze the 5 Strategic Approaches to Digital Optimization and Transformation in Insurance that Gartner laid out in their report and explore possible fraud threats that can arise as a result of such transformation.
Register today to learn more from us about:
- Combating fraud threats introduced by the move to digital, such as ghost broking
- Detecting and preventing growing account takeover
- Protecting the entire customer lifecycle
- How to arm your SIU to more effectively fight fraudulent claims
- Improve identity verification to reduce early term losses
Cybersecurity's Impact on Innovation

Most small and mid-sized tech and healthcare companies are maintaining or increasing their cybersecurity resources this year in preparation for inevitable cyber attacks. While half are increasing spending, most are investing in active response capabilities rather than infrastructure. Only a small minority of companies express high confidence in the security of their information, and many see serious business disruption risks from cyber attacks.
2014-15 Cybersecurity Venture Funding and M&A

This document analyzes trends in cybersecurity venture funding and mergers & acquisitions from 2014-2015. It finds that:
1) Endpoint protection companies received a disproportionate amount of funding compared to their representation among funded companies.
2) Round sizes have increased across the board, particularly for Series C rounds. This suggests Series C rounds may be replacing pre-IPO rounds.
3) Cybersecurity mergers and acquisitions deals have significantly decreased in 2015 compared to 2014, possibly due to high valuation scaring away strategic buyers.
More data is needed but the trends show increasing funding amounts coupled with fewer exit opportunities in the cybersecurity industry.
Investing in Cybersecurity, 2020 outlook for Mexico

The document discusses investing in cybersecurity for 2020. It notes that Mexico is the 8th most targeted country by ransomware hackers. Global spending on cybersecurity services exceeds $124 billion annually from 4300 companies. Private capital investment in cybersecurity startups has grown 19% annually in recent years, with some startups raising over $100 million. However, M&A exit activity has not reflected this growth. The document suggests areas Mexico could improve in, such as supporting home-grown cybersecurity and public-private partnerships. It notes that 9 cybersecurity startups currently call Mexico home.
Fraud infographic - Forrester Report

Did you know that global fraud losses predicted by 2020 is $2 trillion? Check out Forrester's fraud report and get more insight about the industry trends.
5 startups using machine learning and behavioral biometrics to fight fraud

This document summarizes 5 startups that are using machine learning and behavioral biometrics to fight fraud. It provides details on each startup such as their funding amounts, investors, and business models. Some key points are that behavioral biometrics can identify users through unconscious behaviors, machine learning is used to analyze vast amounts of user data to detect fraud patterns, and the featured startups provide fraud detection and prevention platforms to help protect companies from online fraud.
IoT Security RoundTable - March 2018

This document summarizes a panel discussion on security for Internet of Things (IoT) devices and secure payment transactions. The panel discussed trends driving the need for improved payment security within IoT, including the evolution of use cases, increased cyberattacks, adoption of digital currencies, and new regulations. Panelists addressed how different players in the IoT payment ecosystem are addressing security challenges, including the roles of devices, semiconductor vendors, platforms, payment vendors, and existing payment networks. The role of new technologies like blockchain was also discussed. The panel provided an opportunity for open discussion between the presenters and audience.
Generali - Fraud Analytics

This document discusses Generali Group, an international insurance company, and its efforts to detect insurance fraud. It provides an overview of Generali Group, describing it as one of the leading insurers in the world with operations in over 60 countries. It then discusses the problem of insurance fraud and some common types. It outlines Generali's solution to fraud detection, which involves using a graph database and applying techniques like rule-based analysis, social network analysis, and machine learning to processed insurance claims data.
What's hot (16)
Op tijd klaar voor de naderende gdpr avg privacywet - Janus de Visser

Op tijd klaar voor de naderende gdpr avg privacywet - Janus de Visser
Affiliate Fraud Trends & the Policies Needed in the Industry

Affiliate Fraud Trends & the Policies Needed in the Industry
The Insurance Digital Revolution Has a Fraud Problem

The Insurance Digital Revolution Has a Fraud Problem
Investing in Cybersecurity, 2020 outlook for Mexico

Investing in Cybersecurity, 2020 outlook for Mexico
5 startups using machine learning and behavioral biometrics to fight fraud

5 startups using machine learning and behavioral biometrics to fight fraud
Viewers also liked
Australia part 2

This document lists several locations in South Australia including Victor Harbor, Granite Island, Coolwa, Kangaroo Island, and Flinders Chase National Park. It also mentions seeing Australian Pelicans, kangaroos, seals, and sea lions at some of these locations.
Austraila part 3

This document discusses three locations: Admirals Arch, a natural sea arch on the coast of South Australia; New Zealand fur seal, a species of fur seal; and Remarkable Rocks, unusual granite boulders located in Kangaroo Island, South Australia.
10 IT Security Trends to Watch for in 2016

This brief piece takes a look at what we think will be the top trends to look for (and beware of) in 2016.
sunil_john_sourcing resume (1) (1)

Sunil John has over 5 years of experience in supply chain management, sourcing, procurement, and vendor management. He has worked at multiple companies in various roles, including as a project administrator at Rockwell Automation where he managed inventory, purchasing, and asset evaluation. Previously, he worked at Genpact where he conducted strategic sourcing and procurement. He also has experience working for BA Continuum Solutions and Chadha Sugar and Industry Ltd in supply chain and procurement roles. Sunil John holds an MBA in international business and marketing from Amity University.
Allwyn-PE-CV

Allwyn Leo Stanley is a mechanical engineer with over 9 years of experience in oil and gas projects in Qatar. He is currently a Project Engineer at Doha Petroleum Construction Company Ltd. (DOPET) where he is responsible for project coordination, cost and budget control, subcontractor management, and ensuring adherence to quality and safety standards on projects. Some of the key projects he has worked on involve shutdown maintenance, EPIC projects, and quality assurance. He is proficient in project planning software like Primavera P6.
Data breach presentation

Cyber attacks and data breaches are increasing. Hackers are targeting smaller companies to access personal information like credit cards, social security numbers, and passwords. To reduce risk, companies should implement security measures like firewalls, encryption, training employees on security best practices, and establishing a computer security incident response team to respond effectively to any data breaches. Regular security assessments, software updates, and network monitoring can help organizations strengthen their cyber defenses.
MILAN H. CV 2016-New

This application form summarizes the qualifications and experience of Hajdukovic Milan, who is applying for the position of Chief Officer/Skipper. Some key details include:
- He is a 51-year-old Montenegrin citizen currently residing in Bar, Montenegro.
- He has over 20 years of experience working in various roles such as 2nd Mate, Chief Mate, and Master on tankers, offshore supply vessels, and tugs.
- He holds numerous certifications including a Master's license from Montenegro valid until 2024, Dynamic Positioning certificates, safety training, and flag state endorsements.
- His most recent positions include Chief Mate on tugs serving the oil and gas industry
Viewers also liked (11)
Similar to Statistics of 2015 Data Breaches
wp-analyzing-breaches-by-industry

The document analyzes data breach records from 2005-2015 to examine trends by industry. It finds that healthcare, education, government, retail, and finance were most commonly affected, accounting for over 80% of breaches. Personal information was the most frequently stolen record type, compromised through various methods like device loss, insider leaks, and hacking. The analysis also looks specifically at breach trends in the healthcare industry, where loss of portable devices like laptops was a primary source of compromises.
PCI COMPLIANCE REPORT

Did you suffer a data breach in 2014? Even if you avoided
a breach, it’s likely that you saw an increase in the number
of security incidents — according to PwC research, since
2009 the volume has grown at an average of 66% per
year.1 It seems that it’s only retailers and entertainment
companies that make the headlines, but organizations
of all kinds are affected. In this report we look at how
well prepared companies are to withstand attacks and
mitigate the impact of breaches, and recommend how
you can improve.
Verizon rp pci report-2015-en_xg

In this report, Verizon analyzes payment security and PCI DSS compliance based on assessments of thousands of organizations. The summary is:
- Compliance with PCI DSS requirements increased between 2013-2014 for most requirements, but sustainability of compliance remains low, with less than one-third of organizations maintaining full compliance less than a year after validation.
- While the volume of data breaches continues to rise significantly each year, four out of five organizations still fail interim PCI DSS assessments, indicating ongoing issues with implementing and maintaining adequate security controls.
- Payment card use and transactions continue growing globally each year, increasing the importance of payment security for organizations yet the current state of security is still inadequate to prevent the
IBM X-Force Threat Intelligence Report 2016

Download the latest IBM X-Force Threat Intelligence Report
High-value breaches stole headlines as lackluster security fundamentals left organizations open to attack in 2015.
* The globalization of security incidents is shifting to targets like health-related PII and sensitive personal data
* The growing sophistication and organization of cybercrime rings are helping expand their reach
* New attack techniques like mobile overlay malware are evolving, while classics like DDoS and POS malware remain effective
Fraudsters Hackers & Thieves!

How can we better protect our customers?
It’s official: consumers do not feel their private data is being kept private. Looking around at the headlines, where high profile breach after high-profile breach is documented, the lack of trust in data security is no surprise.
In this graphical report, we delve into the fears surrounding online security and the economic impact of losing your customers’ trust.
Fraudsters Hackers & Thieves

It’s official: your customers do not feel their private data is being kept private. In this graphical report, we delve into the fears surrounding online security and the economic impact of losing your customers’ trust.
Cyber Review_April 2015

Data breaches reached record levels in 2014, with over 5,000 incidents compromising an estimated 675 million records. Healthcare organizations experienced the most breaches at 42.5% of the total. Major breaches impacted Sony, J.P. Morgan, Home Depot, and eBay, compromising millions of customer records. The costs of data breaches for US companies averaged $201 per compromised record, with total costs increasing 15% on average. Looking ahead, healthcare breaches and threats to corporate intellectual property and trade secrets are expected to remain significant risks.
15 Years of Web Security: The Rebellious Teenage Years

This document summarizes Jeremiah Grossman's 15 years of experience in web security and the state of application security. It discusses threat actors targeting websites, the growing costs of data breaches and cyber insurance, challenges with vulnerability remediation, and the need for more effective software development processes and addressing skill shortages. WhiteHat Security helps companies find and fix application vulnerabilities before exploits.
Transport Security 201507 lin

This document discusses developing contingency plans to avoid supply chain disruptions from security breaches. It identifies typical supply chain risks such as natural disasters, cyber attacks, cargo theft, and geopolitical instability. The document examines causes of past disruptions and outlines strategies to mitigate risks like conducting threat assessments, identifying core business functions, analyzing impacts, and implementing prevention measures. Developing contingency plans can help companies effectively protect their supply chains and realize benefits like decreased losses, improved continuity, and competitive advantages over rivals.
wp-follow-the-data

This document analyzes data from the Privacy Rights Clearinghouse database on data breach incidents reported from 2005 to 2015. Some key findings include:
- Hacking or malware were behind 25% of breaches, while insider leaks accounted for 12% and unintended disclosures 17.4%.
- Payment card data breaches increased substantially after 2010 likely due to malware targeting point-of-sale systems.
- The healthcare sector experienced the most breaches followed by government and retail. Personally identifiable information and financial data were the most commonly stolen records.
- While credit card and bank account information is frequently dumped online, accounts for services like Uber, PayPal and poker saw increased dumping.
- Organizations must strengthen
FRISS_Insurance fraud report 2020 

- The document discusses the impacts of COVID-19 on insurance fraud detection. It summarizes the results of a survey of insurance professionals on how the pandemic has affected fraud trends and insurance companies' fraud-fighting efforts.
- Key findings include that over 60% of respondents saw an increased fraud workload due to COVID-19, and the top reported pandemic fraud schemes were staged accidents, procedure billing fraud, and fake home accidents. Nearly two-thirds of insurers increased their focus on digitalization in response.
- Ongoing challenges for insurers in combating fraud effectively include issues with internal data quality, access to external data, and keeping up with changing fraud schemes. Most recognize the benefits of automated fraud detection tools but
deloitte-au-privacy-index-2015

The document provides an overview of the Deloitte Australian Privacy Index 2015, which assessed over 100 leading consumer brands across 11 sectors on their privacy practices. Some key findings include:
1. The Government sector was ranked highest overall, while the Media sector was ranked lowest.
2. Banking/Finance and Government brands tended to have the most transparent online privacy policies and fewer third-party cookies.
3. Consumers trusted Government and Banking/Finance the most with their personal information and complained least about these sectors.
4. Most organizations had internal privacy policies and provided privacy training, but training was often less frequent than annually.
Data Breaches Lead to Identity Fraud, according to Javelin

Contemporary research on the financial impact of data breach events has focused on costs to businesses and institutions, but largely ignored their effect on the consumers whose personally identifiable information (PII) is compromised. Javelin Strategy & Research (@JavelinStrategy) released the firm’s first ever “2013 Data Breach Fraud Impact Report: Mitigating a Rapidly Emerging Driver of Fraud,” which demonstrates the real connection between data breach and consumer fraud. Data breach victimization has been increasingly correlated with fraud over the past three years with over 50% of fraud victims in 2012 were also data breach victims. The Open Security Foundation reports an all-time high of 1,611 breaches in 2012, a 48% increase over 2011.
DATA PROTECTION & BREACH READINESS GUIDE 2014

Company names mentioned herein are the property of, and may be trademarks of, their respective owners and are for educational purposes only.
Chaplygin Roman Cybersecurity challanges in an interconnected world

PwC expert Roman Chaplygin present the key findings of PWC’s Global Information Security Survey 2015 and their implications in the retail and consumer sectors.
BREACH LEVEL INDEX

All information, data, and material contained, presented, or provided on is for educational purposes only.
Company names mentioned herein are the property of, and may be trademarks of, their respective owners.
It is not to be construed or intended as providing legal advice.
Company names mentioned herein are the property of, and may be trademarks of, their respective owners and are for educational purposes only.
17 U.S. Code § 107 - Limitations on exclusive rights: Fair use
Notwithstanding the provisions of sections 106 and 106A, the fair use of a copyrighted work, including such use by reproduction in copies or phonorecords or by any other means specified by that section, for purposes such as criticism, comment, news reporting, teaching (including multiple copies for classroom use), scholarship, or research, is not an infringement of copyright.
2014 ota databreachguide4

This document provides a guide to help organizations prepare for and respond to data breaches and incidents. It discusses the growing risk of data breaches and outlines best practices for data lifecycle management. These include implementing an effective Data Incident Plan, understanding how data flows through an organization from collection to destruction, and designating personnel responsible for data protection. The goal is to help organizations enhance security, respond quickly to incidents, and minimize negative impacts to consumers and business operations.
Main Street vs. Wall Street: Who is to Blame for Data Breaches?

Our analysis of major data breaches at US publicly traded companies offers rare insight into how consumers apportion responsibility for preventing data breaches. Key findings from the survey include:
• Ninety-four percent of consumers surveyed are concerned about retail data breaches.
• Consumers are nearly as likely to hold retailers responsible for data breaches (61 percent) as the criminals themselves (79 percent). Only 34 percent blame the banks that issue debit and credit cards.
• Seventy-five percent believe that retailers are not doing enough to prevent infiltrations into their customer data and payment systems.
• Seventy percent of respondents believe that retailers should be held financially responsible for consumer losses that result from a breach; not banks or card issuers.
• Finally – and most troubling – 34 percent of those surveyed report that they no longer shop at a specific retailer due to a past data breach issue.
2016 trustwave global security report

Trustwave investigated hundreds of data compromise incidents across 17 countries in 2015. Some key findings:
- 45% of incidents were in North America, while 27% were in the Asia-Pacific region and 15% in Europe, Middle East, and Africa.
- The retail industry accounted for 23% of incidents, while hospitality was 14% and food/beverage was 10%.
- 40% of investigations involved corporate/internal network breaches and 38% involved e-commerce breaches.
- 60% of breaches targeted payment card data, with 31% involving card track (magnetic stripe) data from POS terminals.
The report provides insights into trends in compromised industries and regions, attack methods
Transport Forum 201511 lin

Developing a contingency plan and avoiding disruptions from a security breach involves the following steps:
1. Conduct a threat assessment to identify potential risks to the supply chain from security breaches.
2. Identify core business functions and conduct a business impact analysis to understand how disruptions could affect the business.
3. Apply prevention and mitigation measures by researching best practices, utilizing standards for business continuity and supply chain security, implementing supplier oversight and cargo controls, and vetting the supplier base.
4. Implement tests of the contingency plan and maintain the plan to ensure it remains effective over time.
Similar to Statistics of 2015 Data Breaches (20)
15 Years of Web Security: The Rebellious Teenage Years

15 Years of Web Security: The Rebellious Teenage Years
Data Breaches Lead to Identity Fraud, according to Javelin

Data Breaches Lead to Identity Fraud, according to Javelin
Chaplygin Roman Cybersecurity challanges in an interconnected world

Chaplygin Roman Cybersecurity challanges in an interconnected world
Main Street vs. Wall Street: Who is to Blame for Data Breaches?

Main Street vs. Wall Street: Who is to Blame for Data Breaches?
More from HOTEL NEWS NOW (STR)
5 things to know about Easter hotel performance

This document analyzes hotel performance data over the 2016 Easter holiday weekend. It reports that among major global markets, Kyoto, Japan and Macau, China had the highest Easter eve occupancy rates at 98.4% and 98.1% respectively. In the US, New York City and the Florida Keys had the highest Easter eve occupancy rates at 92.2% and 91.5%. Additionally, Easter eve average daily rates in the US have exceeded $100 for the past five years, with only 2008 previously reaching over $100. Globally, hotel occupancy and rates are typically higher on the Saturday before Easter than on Easter Sunday itself.
Consumers Don't Know Much About Cybersecurity

At a time when hotels need to take every precaution to avoid falling victim to a data breach and being branded as insecure, consumers don't seem to know much about the security issues that worry them.
The Biggest Hotel Companies by Market Cap

Marriott International and Hilton clearly lead the way for publicly listed hotel companies in terms of market capitalization, but both lag well behind the largest players in the overall world of travel.
3 Top Tech Trends for 2017

Sabre Labs has identified three emerging technologies that could influence the travel industry this year.
The In-Room Tech Guests Really Want

A recent survey of U.S. guests from Oracle Hospitality and Phocuswright shows that guests have strong opinions about in-room Wi-Fi. temperature and light controls, entertainment and technology-assisted housekeeping.
Jan Freitag’s 5 things to Know U.S. January Performance Data

Luxury and upper upscale hotel chains saw RevPAR growth of 7.1% and 4.3% respectively in January, driven by healthy increases in average daily rates. The inauguration of the US President led to double-digit RevPAR growth in 10 markets including Washington D.C. at 77.1%, boosting occupancy and rates. However, outside the top 25 markets, hotel occupancy remained below 50% for January.
The World's Largest

A glance at the world's largest hotel companies, brands, properties, pipelines and global markets by room count. All figures are as of December 2016, according to STR.
Some guests will share data for rewards

New research from GfK shows roughly a quarter of consumers are willing to be open with companies about their personal data if they're getting something in return.
Jan Freitag’s 5 things to Know U.S. December Performance Data

Closing out a year of both new records and disappointments, U.S. hotel performance in December was decidedly average.
New Year's Eve cocktails from around the world

Looking for a good hotel bar with great cocktails this New Year’s Eve? Look no further. Here are a few favorite cocktail recipes from hoteliers and F&B experts in NYE markets around the world.
How Corporate Travelers Use Mobile

Widespread adoption of smartphones has changed corporate travel habits, but behaviors vary between the U.S. and Europe.
Jan Freitag’s 5 things to Know U.S. October Performance Data

Key performance indicators, as expected, show the hotel industry riding out the curve in October, with RevPAR growing for the 80th straight month, but at the slowest rate this year.
5 things to know about Thanksgiving Travel

Data suggests hoteliers in top markets for Thanksgiving travel should prepare for a record number of guests this holiday weekend.
Defend against these types of data breaches

Hackers take numerous approaches to probe for and exploit weaknesses in corporate computer systems in their hunt for valuable personal and financial information.
The State of Chip and Pin Technology

A year after the launch of chip payment, businesses and consumers are still working to get a handle on the technology, while card processors say they’ve seen improvement.
Jan Freitag’s 5 things to Know U.S. August Performance Data

As supply continues to increase and widen its lead over demand, the U.S. hotel industry reported continued occupancy declines, as occupancy fell 0.4% in August. Jan Freitag, SVP of lodging insights at STR, HNN’s parent company, gives his take on how the chain scales performed, which markets show above-average supply growth and more.
Marriott & Starwood by the numbers

Marriott International’s acquisition of Starwood Hotels & Resorts Worldwide resulted in a behemoth of 27 hotel brands.
Here’s a look at some of the numbers at play in the deal.
Expectations for mobile

A recent survey of executives from Open Mobile Media shows how the business community expects to prioritize mobile development.
Mobile is Everywhere for Hotel Guests

Mobile devices like smartphones are ranked as the most important travel accessory, and potential guests use them to book travel in various situations, according to data from Hotels.com.
Utilities & Labor Costs at a glance

The 2016 HOST Almanac indicates utility costs were down across the country in 2015 and were particularly low in the central regions. Labor costs are poised to increase in many markets over the next few years. Data from the 2016 HOST Almanac shows the regions with the highest labor costs were the Mid-Atlantic, Paci c and East North Central.
More from HOTEL NEWS NOW (STR) (20)
Jan Freitag’s 5 things to Know U.S. January Performance Data

Jan Freitag’s 5 things to Know U.S. January Performance Data
Jan Freitag’s 5 things to Know U.S. December Performance Data

Jan Freitag’s 5 things to Know U.S. December Performance Data
Jan Freitag’s 5 things to Know U.S. October Performance Data

Jan Freitag’s 5 things to Know U.S. October Performance Data
Jan Freitag’s 5 things to Know U.S. August Performance Data

Jan Freitag’s 5 things to Know U.S. August Performance Data
Recently uploaded
一比一原版(UMN文凭证书)明尼苏达大学毕业证如何办理

毕业原版【微信:176555708】【(UMN毕业证书)明尼苏达大学毕业证】【微信:176555708】成绩单、外壳、offer、留信学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
【我们承诺采用的是学校原版纸张(纸质、底色、纹路),我们拥有全套进口原装设备,特殊工艺都是采用不同机器制作,仿真度基本可以达到100%,所有工艺效果都可提前给客户展示,不满意可以根据客户要求进行调整,直到满意为止!】
【业务选择办理准则】
一、工作未确定,回国需先给父母、亲戚朋友看下文凭的情况,办理一份就读学校的毕业证【微信176555708】文凭即可
二、回国进私企、外企、自己做生意的情况,这些单位是不查询毕业证真伪的,而且国内没有渠道去查询国外文凭的真假,也不需要提供真实教育部认证。鉴于此,办理一份毕业证【微信176555708】即可
三、进国企,银行,事业单位,考公务员等等,这些单位是必需要提供真实教育部认证的,办理教育部认证所需资料众多且烦琐,所有材料您都必须提供原件,我们凭借丰富的经验,快捷的绿色通道帮您快速整合材料,让您少走弯路。
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
留信网服务项目:
1、留学生专业人才库服务(留信分析)
2、国(境)学习人员提供就业推荐信服务
3、留学人员区块链存储服务
→ 【关于价格问题(保证一手价格)】
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
选择实体注册公司办理,更放心,更安全!我们的承诺:客户在留信官方认证查询网站查询到认证通过结果后付款,不成功不收费!
My burning issue is homelessness K.C.M.O.

My burning issue is homelessness in Kansas City, MO
To: Tom Tresser
From: Roger Warren
一比一原版(UO毕业证)渥太华大学毕业证如何办理

UO毕业证录取书【微信95270640】购买(渥太华大学毕业证成绩单硕士学历)Q微信95270640代办UO学历认证留信网伪造渥太华大学学位证书精仿渥太华大学本科/硕士文凭证书补办渥太华大学 diplomaoffer,Transcript购买渥太华大学毕业证成绩单购买UO假毕业证学位证书购买伪造渥太华大学文凭证书学位证书,专业办理雅思、托福成绩单,学生ID卡,在读证明,海外各大学offer录取通知书,毕业证书,成绩单,文凭等材料:1:1完美还原毕业证、offer录取通知书、学生卡等各种在读或毕业材料的防伪工艺(包括 烫金、烫银、钢印、底纹、凹凸版、水印、防伪光标、热敏防伪、文字图案浮雕,激光镭射,紫外荧光,温感光标)学校原版上有的工艺我们一样不会少,不论是老版本还是最新版本,都能保证最高程度还原,力争完美以求让所有同学都能享受到完美的品质服务。
文凭办理流程:
1客户提供办理信息:姓名生日专业学位毕业时间等(如信息不确定可以咨询顾问:微信95270640我们有专业老师帮你查询);
2开始安排制作毕业证成绩单电子图;
3毕业证成绩单电子版做好以后发送给您确认;
4毕业证成绩单电子版您确认信息无误之后安排制作成品;
5成品做好拍照或者视频给您确认;
6快递给客户(国内顺丰国外DHLUPS等快读邮寄)。
7完成交易删除客户资料
高精端提供以下服务:
一:渥太华大学渥太华大学毕业证文凭证书全套材料从防伪到印刷水印底纹到钢印烫金
二:真实使馆认证(留学人员回国证明)使馆存档
三:真实教育部认证教育部存档教育部留服网站可查
四:留信认证留学生信息网站可查
五:与学校颁发的相关证件1:1纸质尺寸制定(定期向各大院校毕业生购买最新版本毕,业证成绩单保证您拿到的是鲁昂大学内部最新版本毕业证成绩单微信95270640)
A.为什么留学生需要操作留信认证?
留信认证全称全国留学生信息服务网认证,隶属于北京中科院。①留信认证门槛条件更低,费用更美丽,并且包过,完单周期短,效率高②留信认证虽然不能去国企,但是一般的公司都没有问题,因为国内很多公司连基本的留学生学历认证都不了解。这对于留学生来说,这就比自己光拿一个证书更有说服力,因为留学学历可以在留信网站上进行查询!
B.为什么我们提供的毕业证成绩单具有使用价值?
查询留服认证是国内鉴别留学生海外学历的唯一途径但认证只是个体行为不是所有留学生都操作所以没有办理认证的留学生的学历在国内也是查询不到的他们也仅仅只有一张文凭。所以这时候我们提供的和学校颁发的一模一样的毕业证成绩单就有了使用价值。只硕大的蛇皮袋手里拎着长铁钩正站在门口朝黑色的屋内张望不好坏人小偷山娃一怔却也灵机一动立马仰起头双手拢在嘴边朝楼上大喊:“爸爸爸——有人找——那人一听朝山娃尴尬地笑笑悻悻地走了山娃立马“嘭的一声将铁门锁死心却咚咚地乱跳当山娃跟父亲说起这事时父亲很吃惊抚摸着山娃的头说还好醒得及时要不家早被人掏空了到时连电视也没得看啰不过父亲还是夸山娃能临危不乱随机应变有胆有谋山娃笑笑说那都是书上学的看童话和小说时多
Global Situational Awareness of A.I. and where its headed

You can see the future first in San Francisco.
Over the past year, the talk of the town has shifted from $10 billion compute clusters to $100 billion clusters to trillion-dollar clusters. Every six months another zero is added to the boardroom plans. Behind the scenes, there’s a fierce scramble to secure every power contract still available for the rest of the decade, every voltage transformer that can possibly be procured. American big business is gearing up to pour trillions of dollars into a long-unseen mobilization of American industrial might. By the end of the decade, American electricity production will have grown tens of percent; from the shale fields of Pennsylvania to the solar farms of Nevada, hundreds of millions of GPUs will hum.
The AGI race has begun. We are building machines that can think and reason. By 2025/26, these machines will outpace college graduates. By the end of the decade, they will be smarter than you or I; we will have superintelligence, in the true sense of the word. Along the way, national security forces not seen in half a century will be un-leashed, and before long, The Project will be on. If we’re lucky, we’ll be in an all-out race with the CCP; if we’re unlucky, an all-out war.
Everyone is now talking about AI, but few have the faintest glimmer of what is about to hit them. Nvidia analysts still think 2024 might be close to the peak. Mainstream pundits are stuck on the wilful blindness of “it’s just predicting the next word”. They see only hype and business-as-usual; at most they entertain another internet-scale technological change.
Before long, the world will wake up. But right now, there are perhaps a few hundred people, most of them in San Francisco and the AI labs, that have situational awareness. Through whatever peculiar forces of fate, I have found myself amongst them. A few years ago, these people were derided as crazy—but they trusted the trendlines, which allowed them to correctly predict the AI advances of the past few years. Whether these people are also right about the next few years remains to be seen. But these are very smart people—the smartest people I have ever met—and they are the ones building this technology. Perhaps they will be an odd footnote in history, or perhaps they will go down in history like Szilard and Oppenheimer and Teller. If they are seeing the future even close to correctly, we are in for a wild ride.
Let me tell you what we see.
Predictably Improve Your B2B Tech Company's Performance by Leveraging Data

Harness the power of AI-backed reports, benchmarking and data analysis to predict trends and detect anomalies in your marketing efforts.
Peter Caputa, CEO at Databox, reveals how you can discover the strategies and tools to increase your growth rate (and margins!).
From metrics to track to data habits to pick up, enhance your reporting for powerful insights to improve your B2B tech company's marketing.
- - -
This is the webinar recording from the June 2024 HubSpot User Group (HUG) for B2B Technology USA.
Watch the video recording at https://youtu.be/5vjwGfPN9lw
Sign up for future HUG events at https://events.hubspot.com/b2b-technology-usa/
STATATHON: Unleashing the Power of Statistics in a 48-Hour Knowledge Extravag...

"Join us for STATATHON, a dynamic 2-day event dedicated to exploring statistical knowledge and its real-world applications. From theory to practice, participants engage in intensive learning sessions, workshops, and challenges, fostering a deeper understanding of statistical methodologies and their significance in various fields."
一比一原版(Bradford毕业证书)布拉德福德大学毕业证如何办理

原版定制【微信:41543339】【(Bradford毕业证书)布拉德福德大学毕业证】【微信:41543339】成绩单、外壳、offer、留信学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
【我们承诺采用的是学校原版纸张(纸质、底色、纹路),我们拥有全套进口原装设备,特殊工艺都是采用不同机器制作,仿真度基本可以达到100%,所有工艺效果都可提前给客户展示,不满意可以根据客户要求进行调整,直到满意为止!】
【业务选择办理准则】
一、工作未确定,回国需先给父母、亲戚朋友看下文凭的情况,办理一份就读学校的毕业证【微信41543339】文凭即可
二、回国进私企、外企、自己做生意的情况,这些单位是不查询毕业证真伪的,而且国内没有渠道去查询国外文凭的真假,也不需要提供真实教育部认证。鉴于此,办理一份毕业证【微信41543339】即可
三、进国企,银行,事业单位,考公务员等等,这些单位是必需要提供真实教育部认证的,办理教育部认证所需资料众多且烦琐,所有材料您都必须提供原件,我们凭借丰富的经验,快捷的绿色通道帮您快速整合材料,让您少走弯路。
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
留信网服务项目:
1、留学生专业人才库服务(留信分析)
2、国(境)学习人员提供就业推荐信服务
3、留学人员区块链存储服务
→ 【关于价格问题(保证一手价格)】
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
选择实体注册公司办理,更放心,更安全!我们的承诺:客户在留信官方认证查询网站查询到认证通过结果后付款,不成功不收费!
原版制作(swinburne毕业证书)斯威本科技大学毕业证毕业完成信一模一样

学校原件一模一样【微信:741003700 】《(swinburne毕业证书)斯威本科技大学毕业证》【微信:741003700 】学位证,留信认证(真实可查,永久存档)原件一模一样纸张工艺/offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原。
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
【主营项目】
一.毕业证【q微741003700】成绩单、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理各国各大学文凭(一对一专业服务,可全程监控跟踪进度)
如果您处于以下几种情况:
◇在校期间,因各种原因未能顺利毕业……拿不到官方毕业证【q/微741003700】
◇面对父母的压力,希望尽快拿到;
◇不清楚认证流程以及材料该如何准备;
◇回国时间很长,忘记办理;
◇回国马上就要找工作,办给用人单位看;
◇企事业单位必须要求办理的
◇需要报考公务员、购买免税车、落转户口
◇申请留学生创业基金
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
原版制作(Deakin毕业证书)迪肯大学毕业证学位证一模一样

学校原件一模一样【微信:741003700 】《(Deakin毕业证书)迪肯大学毕业证学位证》【微信:741003700 】学位证,留信认证(真实可查,永久存档)原件一模一样纸张工艺/offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原。
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
【主营项目】
一.毕业证【q微741003700】成绩单、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理各国各大学文凭(一对一专业服务,可全程监控跟踪进度)
如果您处于以下几种情况:
◇在校期间,因各种原因未能顺利毕业……拿不到官方毕业证【q/微741003700】
◇面对父母的压力,希望尽快拿到;
◇不清楚认证流程以及材料该如何准备;
◇回国时间很长,忘记办理;
◇回国马上就要找工作,办给用人单位看;
◇企事业单位必须要求办理的
◇需要报考公务员、购买免税车、落转户口
◇申请留学生创业基金
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
State of Artificial intelligence Report 2023

Artificial intelligence (AI) is a multidisciplinary field of science and engineering whose goal is to create intelligent machines.
We believe that AI will be a force multiplier on technological progress in our increasingly digital, data-driven world. This is because everything around us today, ranging from culture to consumer products, is a product of intelligence.
The State of AI Report is now in its sixth year. Consider this report as a compilation of the most interesting things we’ve seen with a goal of triggering an informed conversation about the state of AI and its implication for the future.
We consider the following key dimensions in our report:
Research: Technology breakthroughs and their capabilities.
Industry: Areas of commercial application for AI and its business impact.
Politics: Regulation of AI, its economic implications and the evolving geopolitics of AI.
Safety: Identifying and mitigating catastrophic risks that highly-capable future AI systems could pose to us.
Predictions: What we believe will happen in the next 12 months and a 2022 performance review to keep us honest.
Enhanced Enterprise Intelligence with your personal AI Data Copilot.pdf

Recently we have observed the rise of open-source Large Language Models (LLMs) that are community-driven or developed by the AI market leaders, such as Meta (Llama3), Databricks (DBRX) and Snowflake (Arctic). On the other hand, there is a growth in interest in specialized, carefully fine-tuned yet relatively small models that can efficiently assist programmers in day-to-day tasks. Finally, Retrieval-Augmented Generation (RAG) architectures have gained a lot of traction as the preferred approach for LLMs context and prompt augmentation for building conversational SQL data copilots, code copilots and chatbots.
In this presentation, we will show how we built upon these three concepts a robust Data Copilot that can help to democratize access to company data assets and boost performance of everyone working with data platforms.
Why do we need yet another (open-source ) Copilot?
How can we build one?
Architecture and evaluation
一比一原版(Glasgow毕业证书)格拉斯哥大学毕业证如何办理

毕业原版【微信:41543339】【(Glasgow毕业证书)格拉斯哥大学毕业证】【微信:41543339】成绩单、外壳、offer、留信学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
【我们承诺采用的是学校原版纸张(纸质、底色、纹路),我们拥有全套进口原装设备,特殊工艺都是采用不同机器制作,仿真度基本可以达到100%,所有工艺效果都可提前给客户展示,不满意可以根据客户要求进行调整,直到满意为止!】
【业务选择办理准则】
一、工作未确定,回国需先给父母、亲戚朋友看下文凭的情况,办理一份就读学校的毕业证【微信41543339】文凭即可
二、回国进私企、外企、自己做生意的情况,这些单位是不查询毕业证真伪的,而且国内没有渠道去查询国外文凭的真假,也不需要提供真实教育部认证。鉴于此,办理一份毕业证【微信41543339】即可
三、进国企,银行,事业单位,考公务员等等,这些单位是必需要提供真实教育部认证的,办理教育部认证所需资料众多且烦琐,所有材料您都必须提供原件,我们凭借丰富的经验,快捷的绿色通道帮您快速整合材料,让您少走弯路。
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
留信网服务项目:
1、留学生专业人才库服务(留信分析)
2、国(境)学习人员提供就业推荐信服务
3、留学人员区块链存储服务
→ 【关于价格问题(保证一手价格)】
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
选择实体注册公司办理,更放心,更安全!我们的承诺:客户在留信官方认证查询网站查询到认证通过结果后付款,不成功不收费!
06-04-2024 - NYC Tech Week - Discussion on Vector Databases, Unstructured Dat...

06-04-2024 - NYC Tech Week - Discussion on Vector Databases, Unstructured Data and AI
Round table discussion of vector databases, unstructured data, ai, big data, real-time, robots and Milvus.
A lively discussion with NJ Gen AI Meetup Lead, Prasad and Procure.FYI's Co-Found
办(uts毕业证书)悉尼科技大学毕业证学历证书原版一模一样

原版一模一样【微信:741003700 】【(uts毕业证书)悉尼科技大学毕业证学历证书】【微信:741003700 】学位证,留信认证(真实可查,永久存档)offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原海外各大学 Bachelor Diploma degree, Master Degree Diploma
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
Analysis insight about a Flyball dog competition team's performance

Insight of my analysis about a Flyball dog competition team's last year performance. Find more: https://github.com/rolandnagy-ds/flyball_race_analysis/tree/main
End-to-end pipeline agility - Berlin Buzzwords 2024

We describe how we achieve high change agility in data engineering by eliminating the fear of breaking downstream data pipelines through end-to-end pipeline testing, and by using schema metaprogramming to safely eliminate boilerplate involved in changes that affect whole pipelines.
A quick poll on agility in changing pipelines from end to end indicated a huge span in capabilities. For the question "How long time does it take for all downstream pipelines to be adapted to an upstream change," the median response was 6 months, but some respondents could do it in less than a day. When quantitative data engineering differences between the best and worst are measured, the span is often 100x-1000x, sometimes even more.
A long time ago, we suffered at Spotify from fear of changing pipelines due to not knowing what the impact might be downstream. We made plans for a technical solution to test pipelines end-to-end to mitigate that fear, but the effort failed for cultural reasons. We eventually solved this challenge, but in a different context. In this presentation we will describe how we test full pipelines effectively by manipulating workflow orchestration, which enables us to make changes in pipelines without fear of breaking downstream.
Making schema changes that affect many jobs also involves a lot of toil and boilerplate. Using schema-on-read mitigates some of it, but has drawbacks since it makes it more difficult to detect errors early. We will describe how we have rejected this tradeoff by applying schema metaprogramming, eliminating boilerplate but keeping the protection of static typing, thereby further improving agility to quickly modify data pipelines without fear.
一比一原版(GWU,GW文凭证书)乔治·华盛顿大学毕业证如何办理

毕业原版【微信:176555708】【(GWU,GW毕业证书)乔治·华盛顿大学毕业证】【微信:176555708】成绩单、外壳、offer、留信学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
【我们承诺采用的是学校原版纸张(纸质、底色、纹路),我们拥有全套进口原装设备,特殊工艺都是采用不同机器制作,仿真度基本可以达到100%,所有工艺效果都可提前给客户展示,不满意可以根据客户要求进行调整,直到满意为止!】
【业务选择办理准则】
一、工作未确定,回国需先给父母、亲戚朋友看下文凭的情况,办理一份就读学校的毕业证【微信176555708】文凭即可
二、回国进私企、外企、自己做生意的情况,这些单位是不查询毕业证真伪的,而且国内没有渠道去查询国外文凭的真假,也不需要提供真实教育部认证。鉴于此,办理一份毕业证【微信176555708】即可
三、进国企,银行,事业单位,考公务员等等,这些单位是必需要提供真实教育部认证的,办理教育部认证所需资料众多且烦琐,所有材料您都必须提供原件,我们凭借丰富的经验,快捷的绿色通道帮您快速整合材料,让您少走弯路。
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
留信网服务项目:
1、留学生专业人才库服务(留信分析)
2、国(境)学习人员提供就业推荐信服务
3、留学人员区块链存储服务
→ 【关于价格问题(保证一手价格)】
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
选择实体注册公司办理,更放心,更安全!我们的承诺:客户在留信官方认证查询网站查询到认证通过结果后付款,不成功不收费!
一比一原版(爱大毕业证书)爱丁堡大学毕业证如何办理

毕业原版【微信:41543339】【(爱大毕业证书)爱丁堡大学毕业证】【微信:41543339】成绩单、外壳、offer、留信学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
【我们承诺采用的是学校原版纸张(纸质、底色、纹路),我们拥有全套进口原装设备,特殊工艺都是采用不同机器制作,仿真度基本可以达到100%,所有工艺效果都可提前给客户展示,不满意可以根据客户要求进行调整,直到满意为止!】
【业务选择办理准则】
一、工作未确定,回国需先给父母、亲戚朋友看下文凭的情况,办理一份就读学校的毕业证【微信41543339】文凭即可
二、回国进私企、外企、自己做生意的情况,这些单位是不查询毕业证真伪的,而且国内没有渠道去查询国外文凭的真假,也不需要提供真实教育部认证。鉴于此,办理一份毕业证【微信41543339】即可
三、进国企,银行,事业单位,考公务员等等,这些单位是必需要提供真实教育部认证的,办理教育部认证所需资料众多且烦琐,所有材料您都必须提供原件,我们凭借丰富的经验,快捷的绿色通道帮您快速整合材料,让您少走弯路。
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
留信网服务项目:
1、留学生专业人才库服务(留信分析)
2、国(境)学习人员提供就业推荐信服务
3、留学人员区块链存储服务
→ 【关于价格问题(保证一手价格)】
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
选择实体注册公司办理,更放心,更安全!我们的承诺:客户在留信官方认证查询网站查询到认证通过结果后付款,不成功不收费!
University of New South Wales degree offer diploma Transcript

澳洲UNSW毕业证书制作新南威尔士大学假文凭定制Q微168899991做UNSW留信网教留服认证海牙认证改UNSW成绩单GPA做UNSW假学位证假文凭高仿毕业证申请新南威尔士大学University of New South Wales degree offer diploma Transcript
Recently uploaded (20)
Global Situational Awareness of A.I. and where its headed

Global Situational Awareness of A.I. and where its headed
Predictably Improve Your B2B Tech Company's Performance by Leveraging Data

Predictably Improve Your B2B Tech Company's Performance by Leveraging Data
STATATHON: Unleashing the Power of Statistics in a 48-Hour Knowledge Extravag...

STATATHON: Unleashing the Power of Statistics in a 48-Hour Knowledge Extravag...
Enhanced Enterprise Intelligence with your personal AI Data Copilot.pdf

Enhanced Enterprise Intelligence with your personal AI Data Copilot.pdf
06-04-2024 - NYC Tech Week - Discussion on Vector Databases, Unstructured Dat...

06-04-2024 - NYC Tech Week - Discussion on Vector Databases, Unstructured Dat...
Analysis insight about a Flyball dog competition team's performance

Analysis insight about a Flyball dog competition team's performance
End-to-end pipeline agility - Berlin Buzzwords 2024

End-to-end pipeline agility - Berlin Buzzwords 2024
University of New South Wales degree offer diploma Transcript

University of New South Wales degree offer diploma Transcript
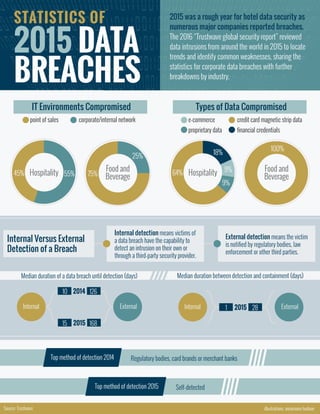
Statistics of 2015 Data Breaches
- 1. 2015 2014 STATISTICS OF 2015 DATA BREACHES 2015 was a rough year for hotel data security as numerous major companies reported breaches. The 2016 “Trustwave global security report” reviewed data intrusions from around the world in 2015 to locate trends and identify common weaknesses, sharing the statistics for corporate data breaches with further breakdowns by industry. External detection means the victim is notified by regulatory bodies, law enforcement or other third parties. Source: Trustwave 18% 9% 9% 100% point of sales corporate/internal network IT Environments Compromised Hospitality 75% 25% 45% 55% Food and Beverage e-commerce credit card magnetic strip data Types of Data Compromised proprietary data financial credentials 64% Internal Versus External Detection of a Breach Median duration of a data breach until detection (days) 126 External 10 Internal 16815 Median duration between detection and containment (days) 28 External1Internal Internal detection means victims of a data breach have the capability to detect an intrusion on their own or through a third-party security provider. Hospitality Food and Beverage illustrations: annamarie hudson 2015 Top method of detection 2014 Regulatory bodies, card brands or merchant banks Top method of detection 2015 Self-detected
