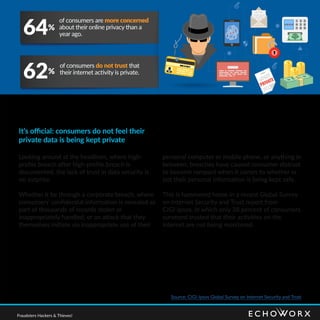
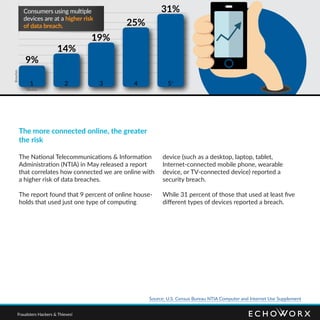
Consumers express significant distrust regarding the security of their personal data online, with only 38% believing their activities are private. The rise in data breaches has led to increased anxiety and altered behaviors, as many individuals refrain from engaging in online financial transactions or sharing personal opinions due to privacy concerns. Businesses must enhance their data protection measures and prioritize user experience to regain consumer trust.