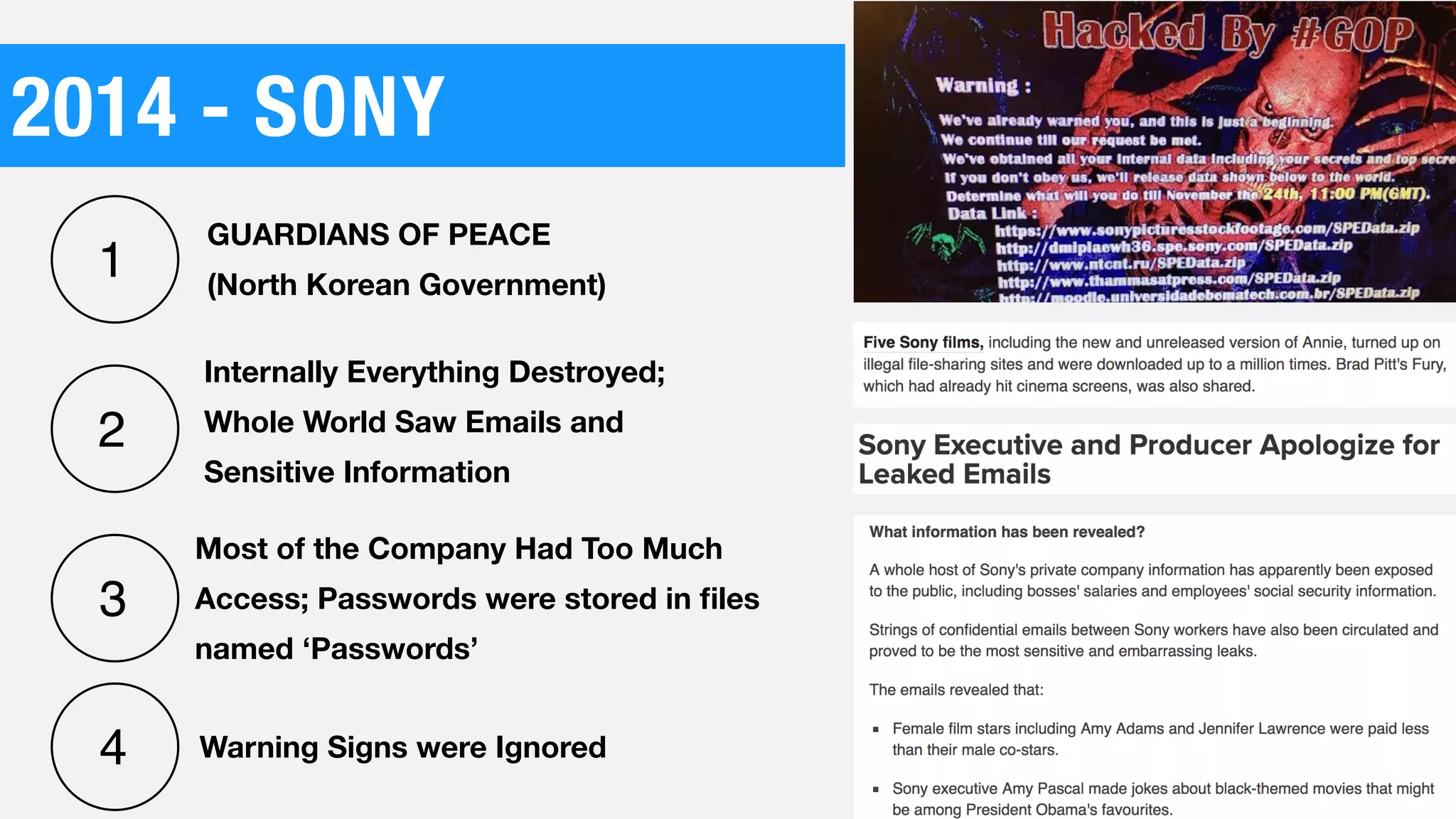
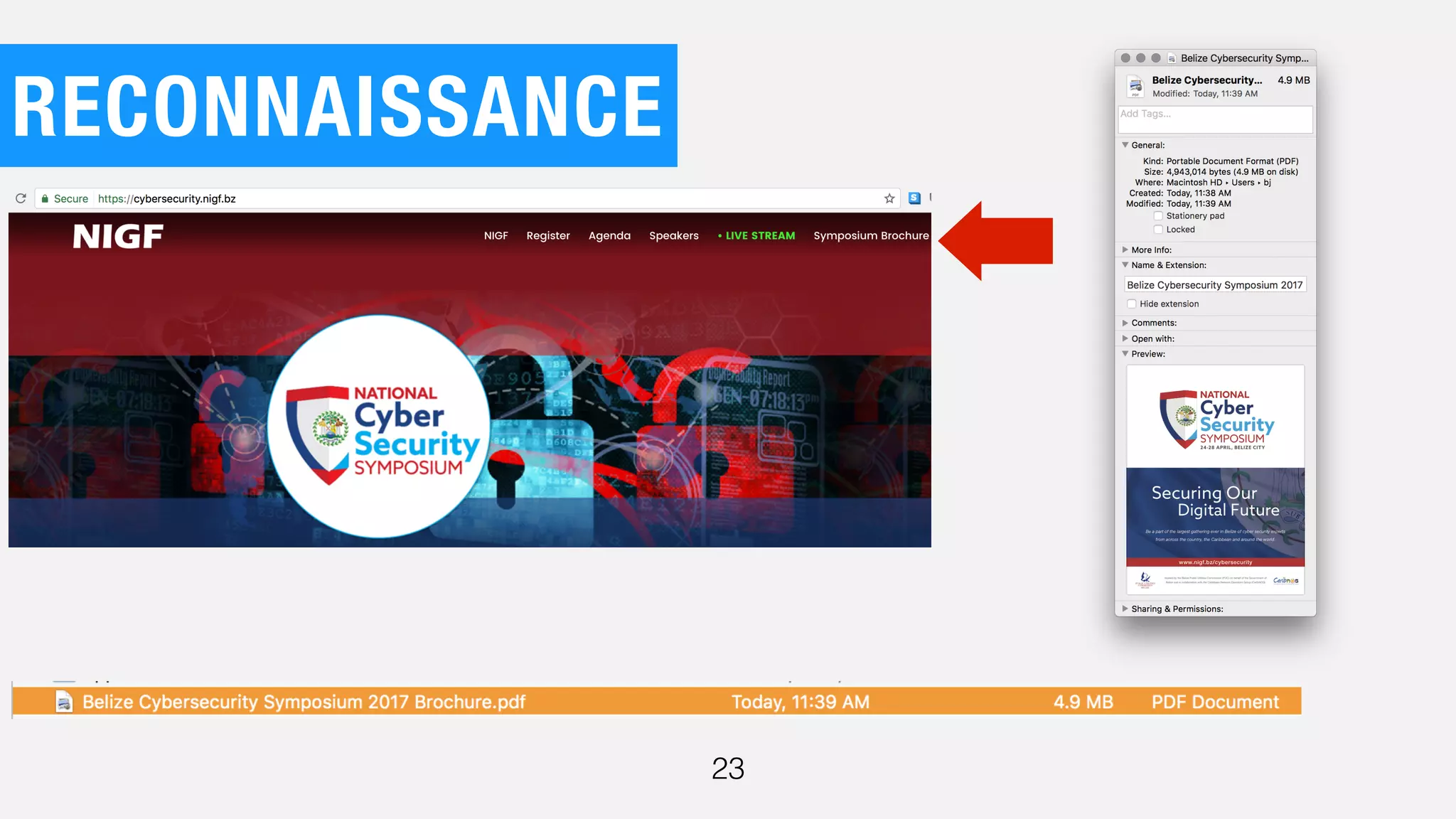
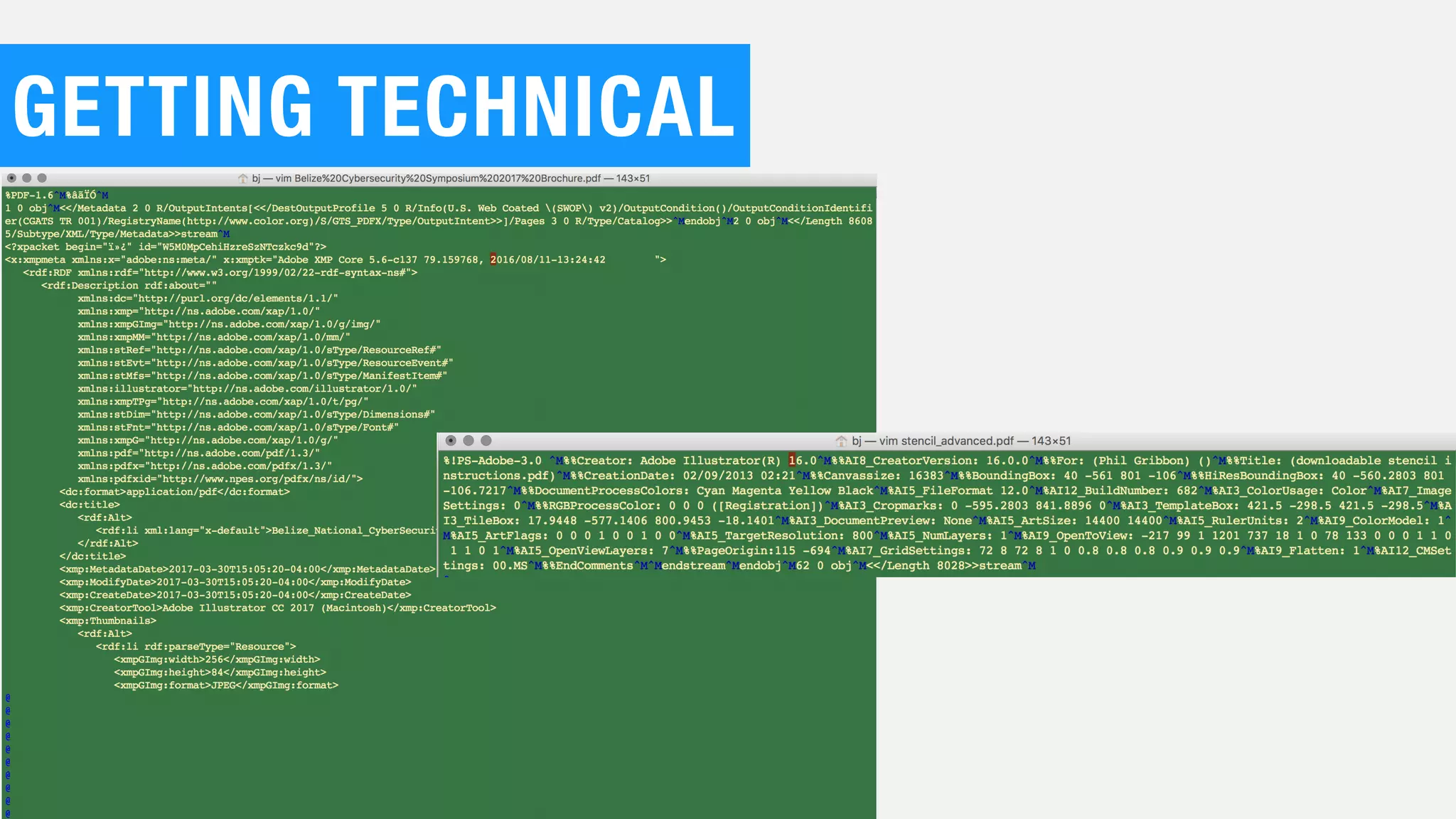
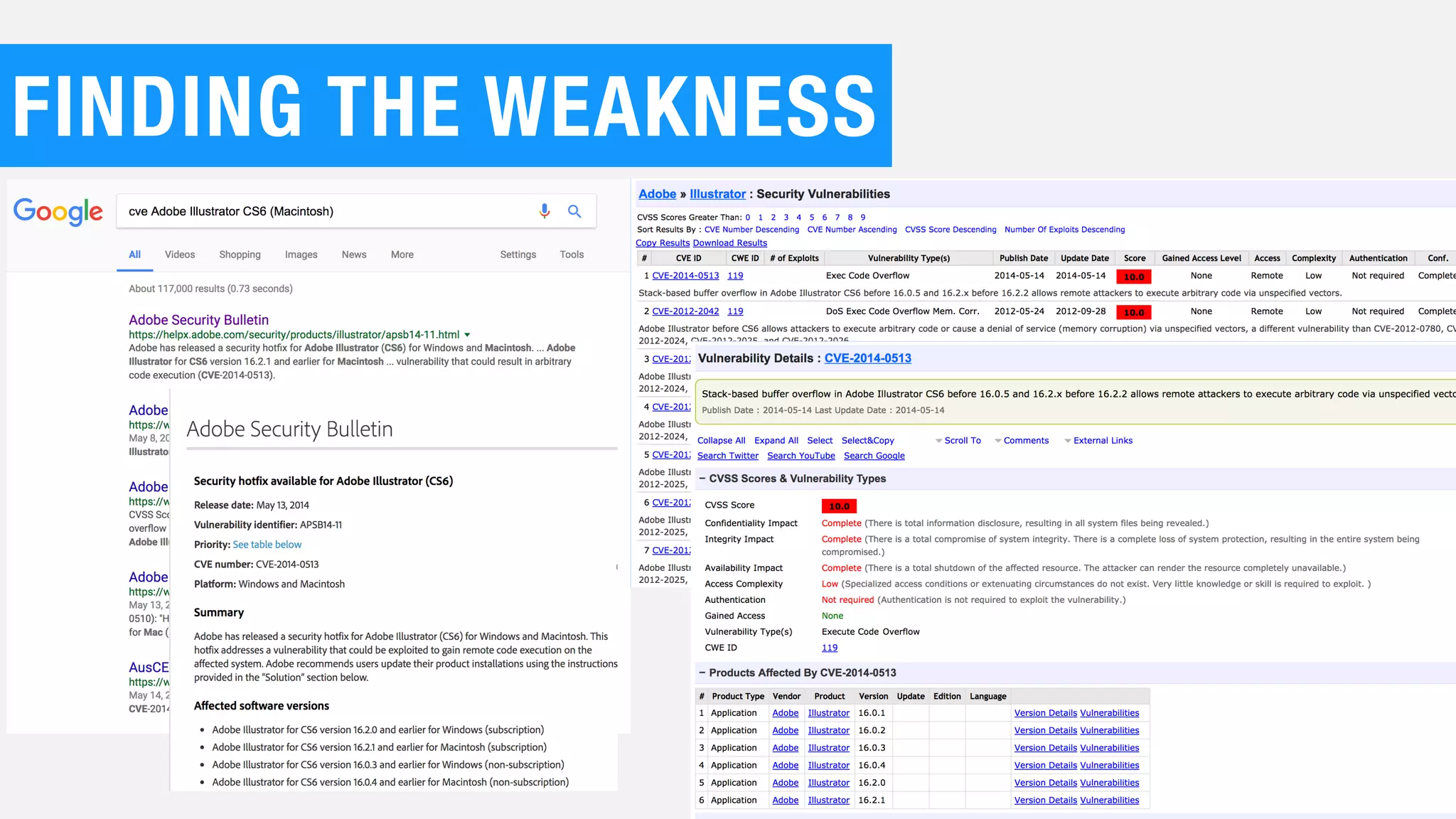
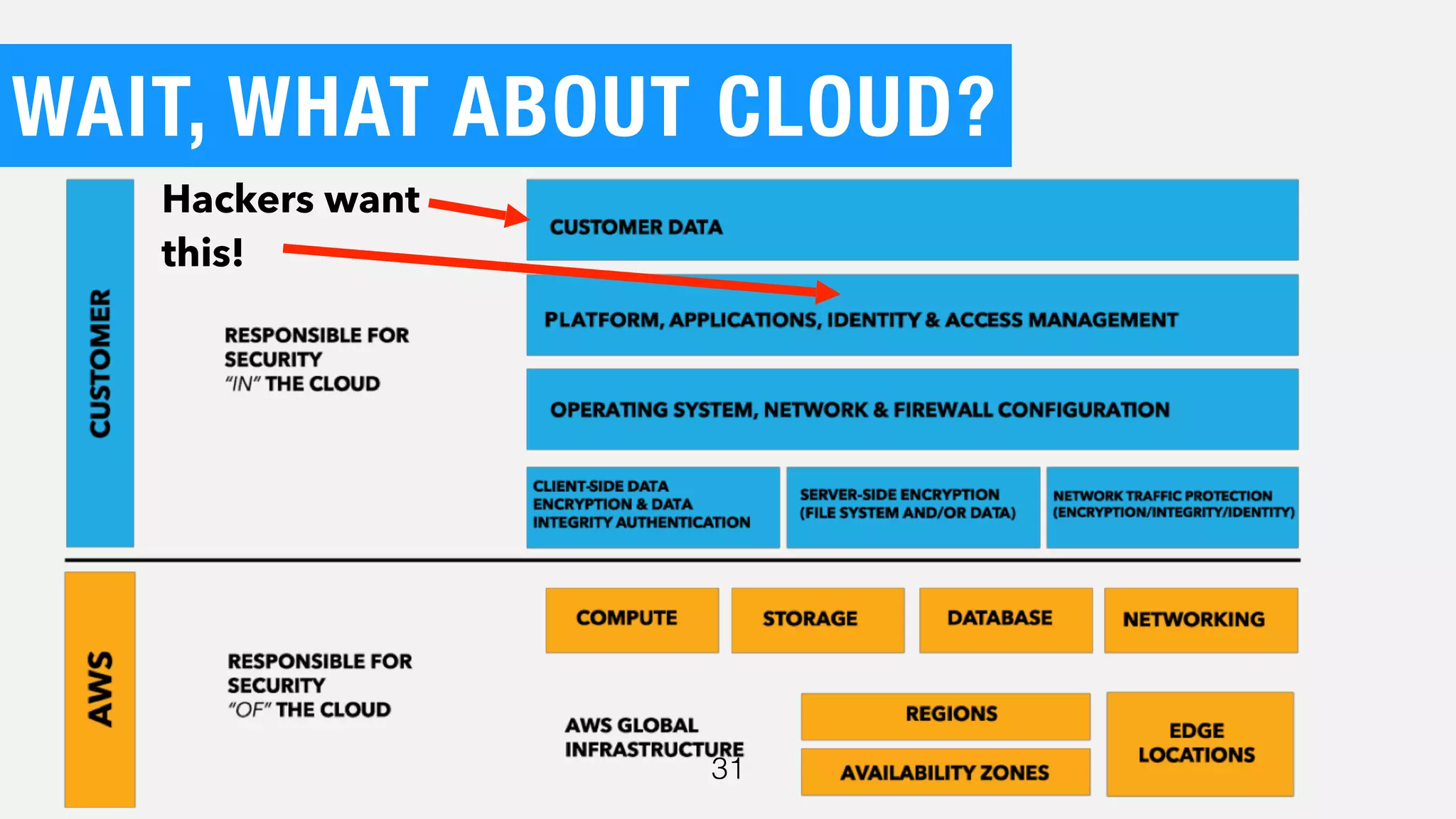
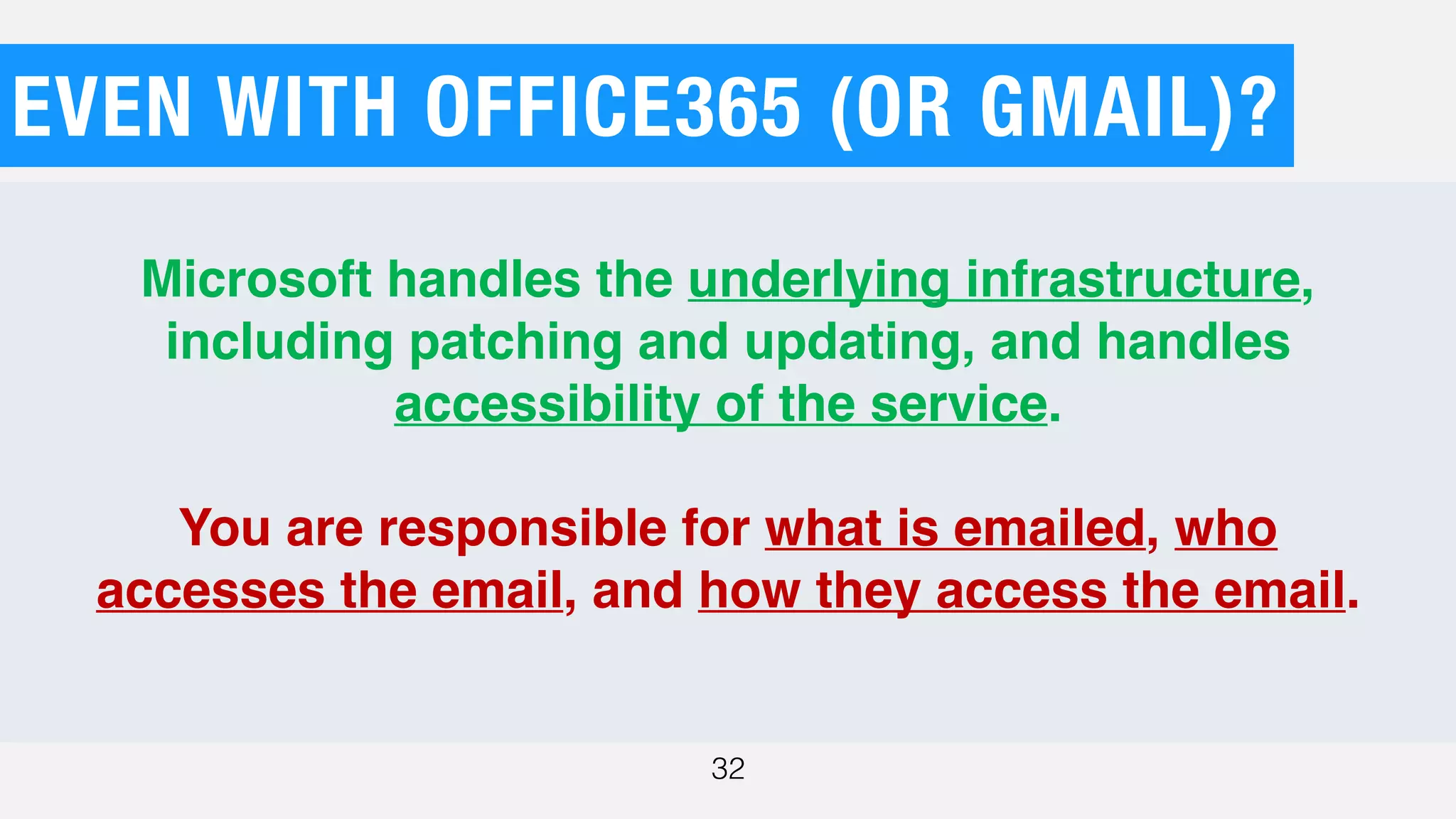
The document discusses the current state of cybersecurity, highlighting a significant talent shortage and the challenges posed by outdated technology. It emphasizes the complexity of cyber threats from various actors, including cybercriminals, hacktivists, and nation-states, and urges the need for increased awareness and better collaboration to combat these threats. The author, Ben Johnson, offers actionable steps for organizations and individuals to improve their security posture, such as updating systems, promoting cybersecurity awareness, and integrating security into software development.