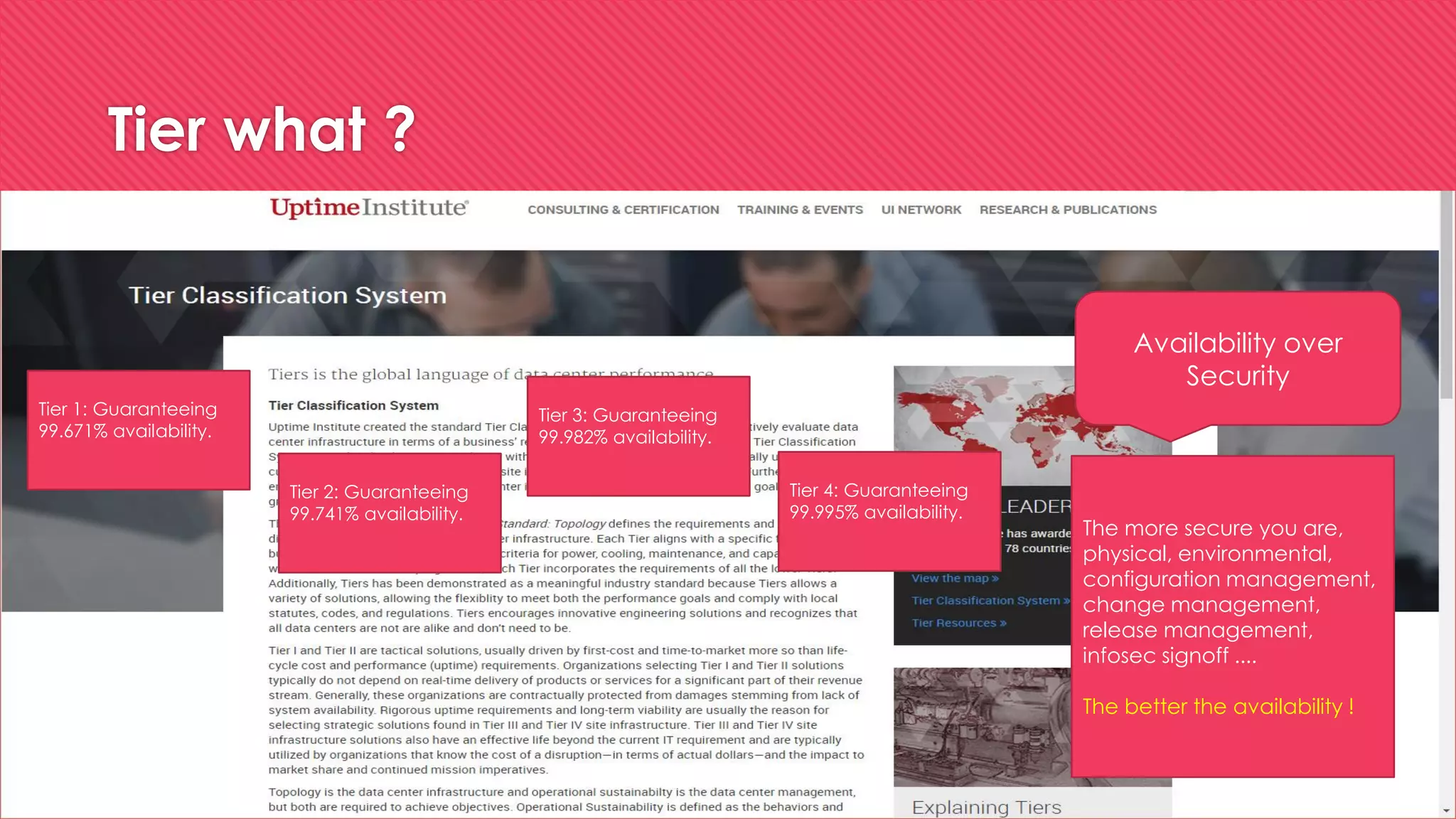
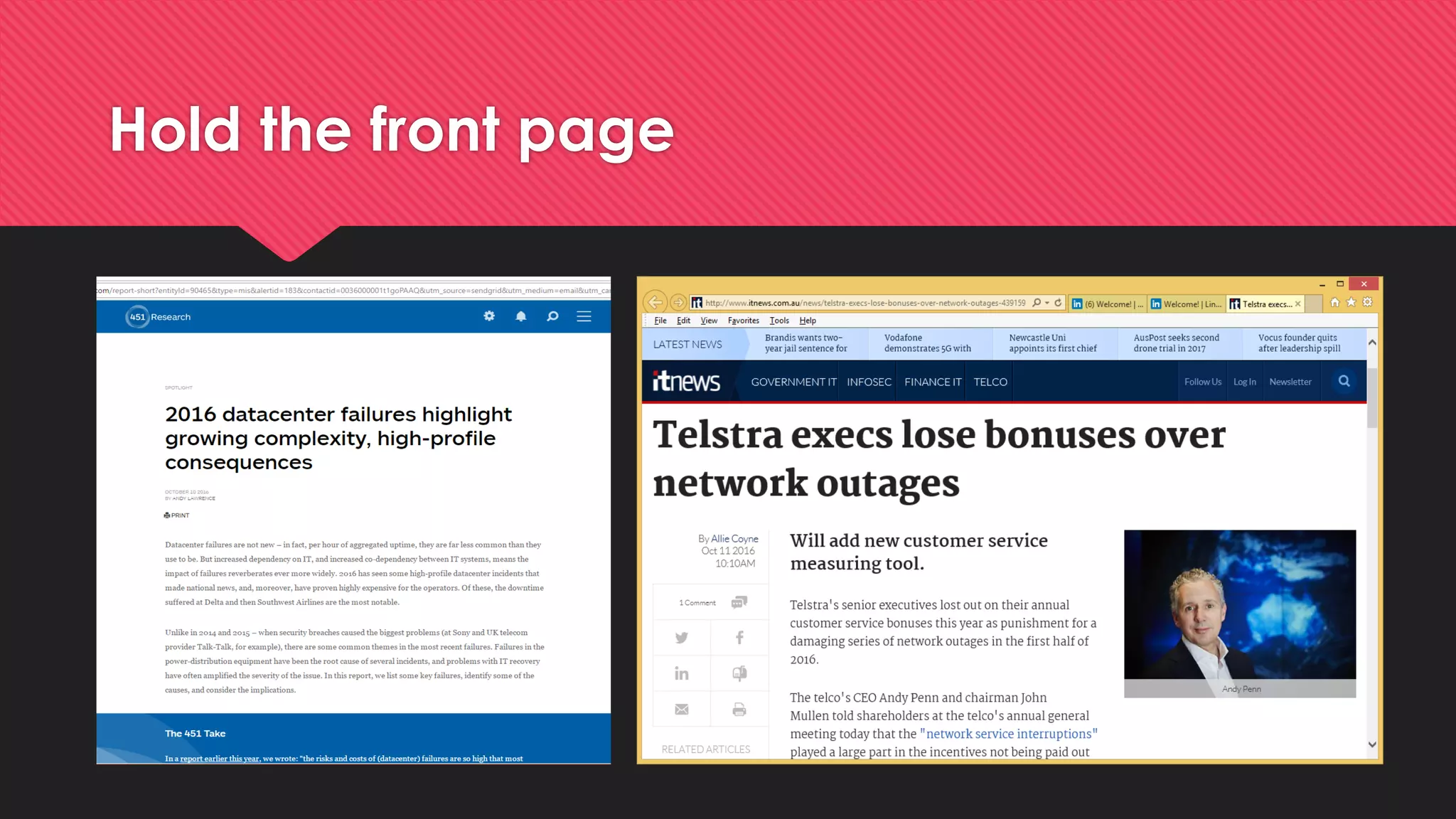
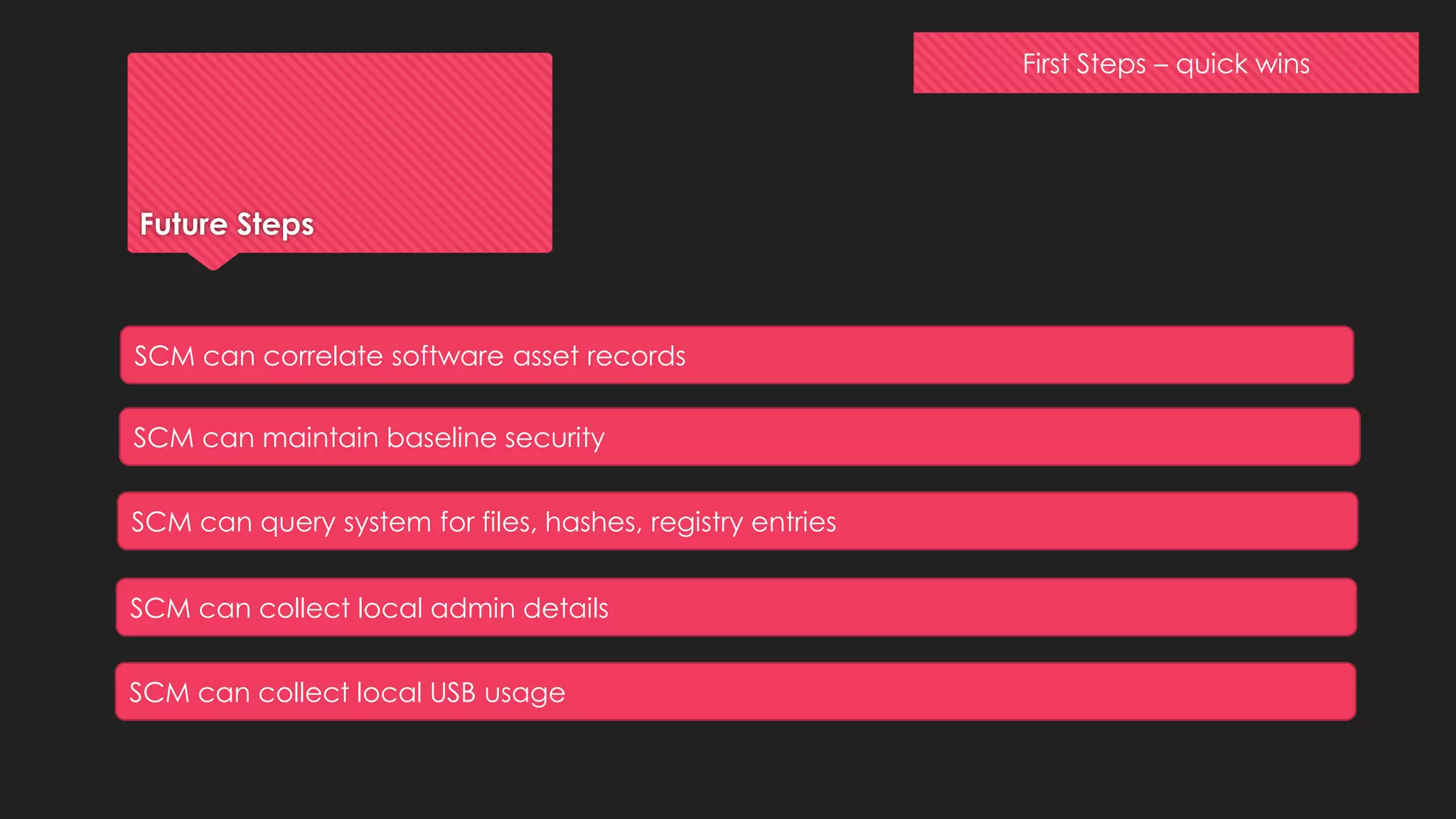
This document summarizes James McKinlay's presentation on "Cyber Hygiene at speed and scale - How to Clean a Datacenter". The presentation discusses the benefits of implementing vulnerability assessment and management (VMaaS) in managed datacenters to improve security. It recommends starting with quick wins like installing VMaaS agents, building a knowledgebase of patches, and linking VMaaS to configuration management databases. Long-term, security automation could be expanded to correlate software assets, maintain baselines, query systems, and collect security details. The takeaway is that datacenter operators should prioritize basic security hygiene and work with managed service providers to integrate more proactive security measures.